Submitted:
14 May 2024
Posted:
16 May 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
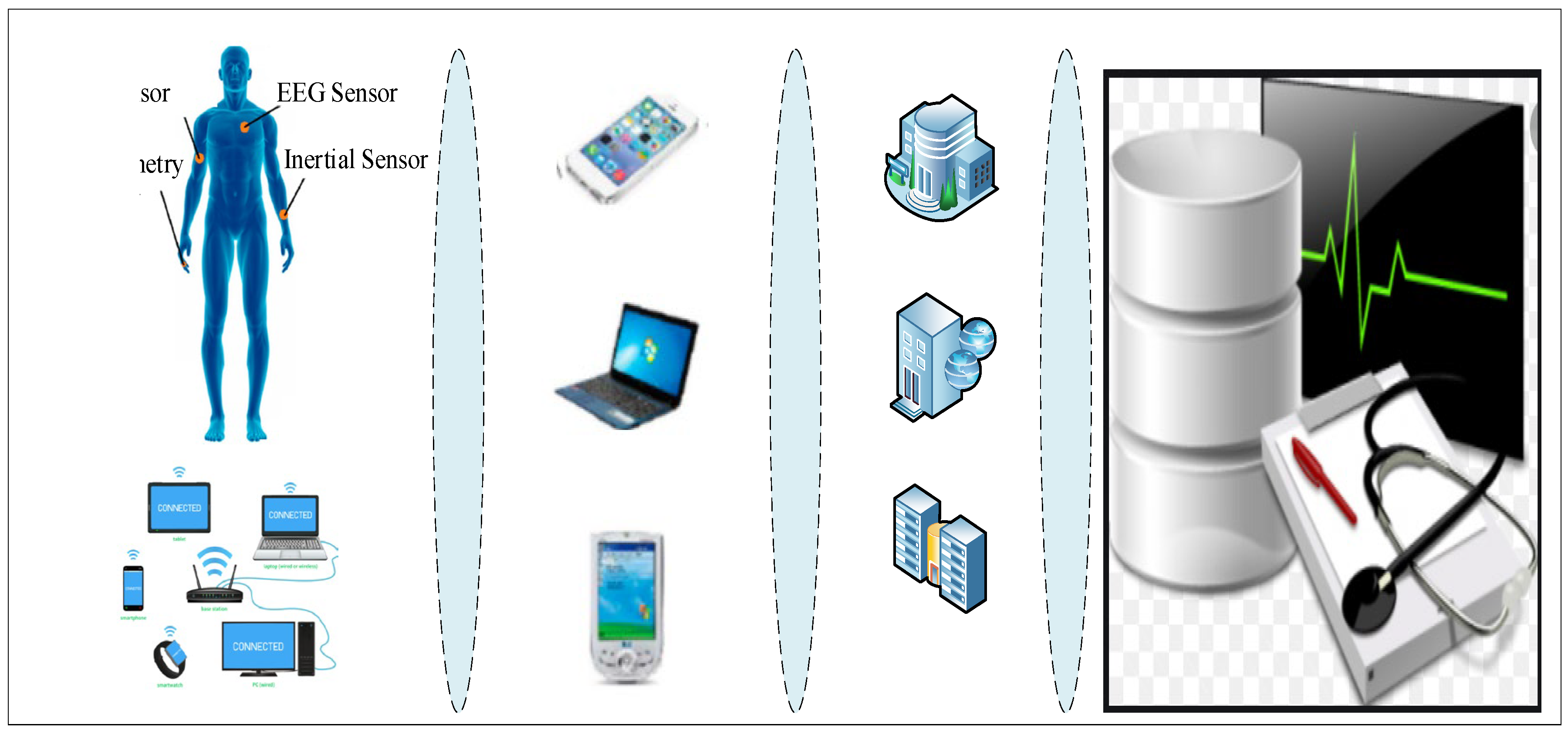
2. The IoMT Structures and Standards
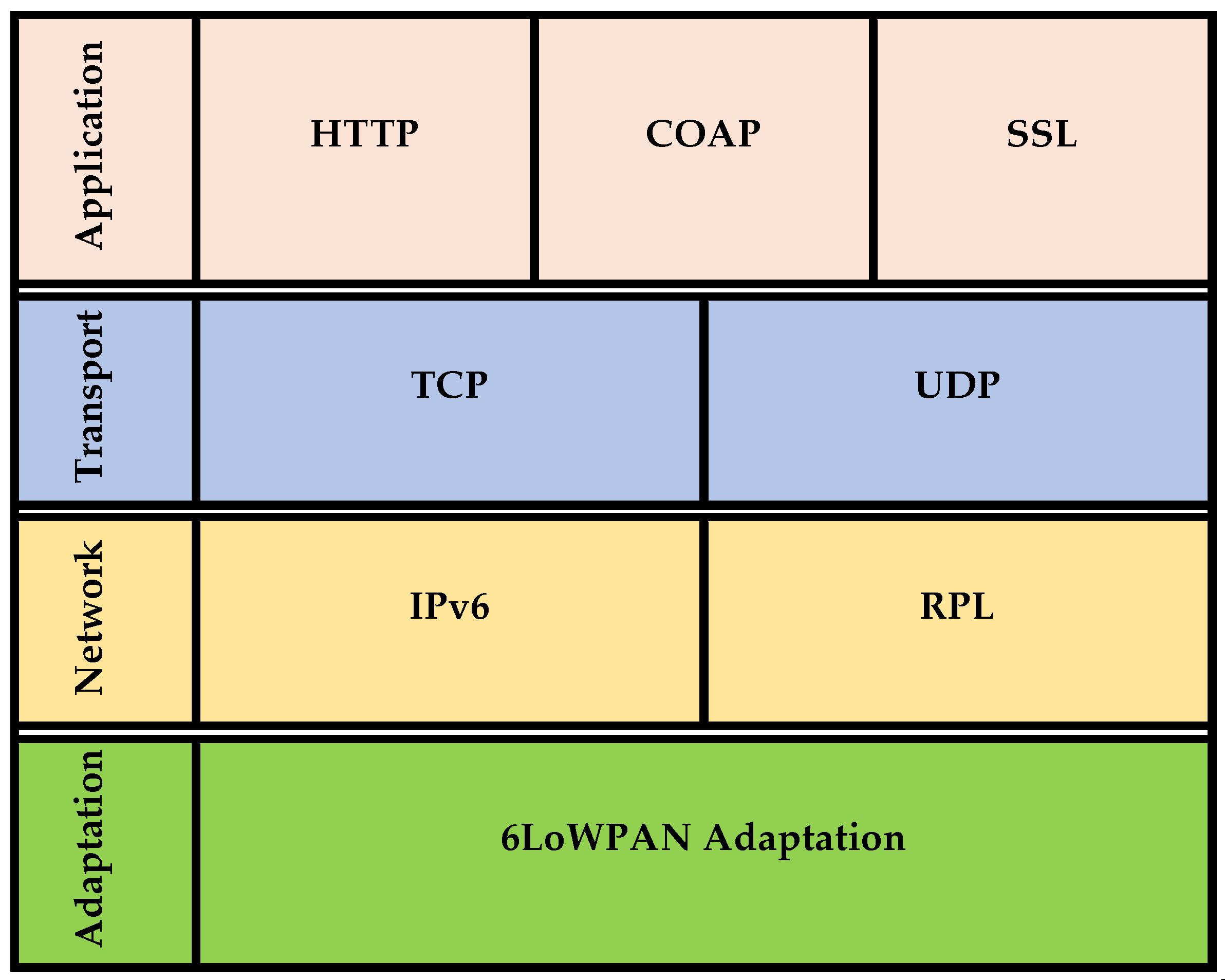
2.1. IoMT Data Types and Protocols
3. Existing Research in IoMT
3.1. Edge Computing
3.1.1. Studies in Edge Computing
3.1.2. Limitations and Research Directions for Edge Computing in IoMT
4. FOG COMPUTING
4.1. Characteristics of Fog Computing
- As fog computing is located at the network's edge, it is closer to the end-user generating data. This indicates that Fog and IoT are on the same LAN, enabling them to exchange data faster. This helps us reduce delays, latency, and jitter, crucial for delay-sensitive applications such as emergency services and healthcare delivery. Dense Geographical Distribution: The fog computing approach of greater geographical distribution has numerous advantages over centralized cloud deployment.
- Support for Mobility: Fog computing supports the mobility of users and provides location awareness. It is made possible by geographical distribution and locating it at the network's edge. This location gives Fog computing network and context information collected by traffic, analytics, and various IoT devices. Location awareness is key to healthcare service providers supporting users' mobility and offering a range of personalized mobile applications.
- These features provide a significant advantage of fog computing compared to the cloud computing approach. Because of geographical distribution and vicinity to end-users, Fog supports users' location awareness and mobility, reduces delay, latency, and jitter, eliminates data transmission in the network's infrastructure, and enhances encrypted data's flexibility, scalability, and security. However, Fog's computing power is limited, and thus, it cannot replace cloud computing. Because of its proximity to the user and geographical distribution, it can support the users' mobility, provide location awareness, and decrease delay, latency, and jitter, eliminating data transmission in the network infrastructure and ensuring enhanced security of encrypted data. As Fog's computing power is limited, it will not replace cloud computing. [26].
4.2. IoMT Fog-Cloud Computing
4.3. Studies in Fog Computing
4.4. Analysis of Existing Techniques and Evaluation Criteria in Fog Computing
4.5. Limitations and Research Directions for Fog Computing in IoMT
5. IoMT PROCESSING
5.1. Distributed Processing
| Ref. | Performance measure | Evaluation Tools | Experimental evaluation | Strength |
|---|---|---|---|---|
| [59] | Energy consumption + Latency | OpenMote-CC2538 platforms provide Contiki-OS with built-in sensors -Raspberry Pi 3 is the gateway. | Results show that the average delay in urgent-high and urgent-medium states is about 90 ms, which is many folds better than the original ones (1000 ms) | For designing fog computing systems that meet the requirements of IoT applications. Device-driven and human-driven intelligence is considered a feasible solution. |
| Energy consumption + Latency | Simulation | The result shows that energy consumption & latency are reduced significantly when the number of nearby fog nodes increases. | ||
| [40] | Energy consumption+ Latency+ Bandwidth expenditure | The application is hosted on the Fog Server and is run using the Raspberry Pi Zero W board. The operating system uses the Python script. The applications support the Message Queuing Telemetry Transport (MQTT) | Local data processing has many advantages, such as reduced latency and low bandwidth costs, affecting the total cost. | The proposed gateway has the main features that help the fog computing system to perform well. |
| [41] | Latency | CloudSim Simulation | The simulation results indicated that the method demonstrated the best cooperation between AET, AWT, and AFT compared to scheduling algorithms such as SJS, FCFS, and MAX-MIN. | The proposed scheduling technique helped in the real-time monitoring of the remote healthcare system. |
| [42] | Latency | Ifogsim simulator +-SPARK | Virtualization and the machine learning approach reduce the network latency between the Fog and cloud for different physical topological arrangements. | A hybrid fuzzy logic and reinforcement learning approach can enhance the current healthcare IoT and cloud-based fog computing. |
| [38] | Energy consumption + Latency | iFogSim | The results were compared to those observed for the existing processes regarding end-to-end delay, throughput, and energy consumption. The proposed methods reduced energy consumption by 30-40%. Simulation results of the FC-IoMT were compared to the earlier techniques. The FC-IoMT was effective as it collected all data from the biosensors and assigned the patient's request to the bio-fog and the bio-cloud-based architecture. | This technique allowed the sensing modes to collect patient data, depending on their health condition. |
| [44] | Number of computing resources Response time | A JMT simulator was installed on the machine with an Intel Core i5 CPU, 2.40 GHz, 4 GB memory, and 250 GB permanent storage. | The study presents the results derived from the simulation & the queuing model for demonstrating how the proposed model displayed effective & dynamic scalability using minimal computing resources (FC nodes, private and public VM nodes) for the incoming workload prompted by the body sensor or IoMT devices for satisfying the imposed SLA response time (2.5 ms) | Analytical and simulation results showed that this model predicted the system's response time based on various workload conditions. It could accurately estimate the number of computing resources required so that the health data services can perform satisfactorily. |
| [40] | Latency | The Kafka cluster, Storm topology, and MongoDB database (or Neo4j graph database) provide a faster query execution time. | N\A | By processing a large amount of the healthcare data streams at the network edge near the data sources, one can decrease the network traffic and increase the latency of the time-sensitive healthcare services & applications. |
| [46] | Bandwidth+ Latency | MATLAB mobile app for transmitting the accelerometer data from the smartphone to a fog node. | They evaluated this model on real-world fall data. It could accurately classify 100% of the falls. The fall detection technique used the fog computing concept, significantly decreasing the data sent to the cloud from 900 values (10,799 bytes) to 5 values (59 bytes) every 6s. | This framework offered real-time fall detection as it analyzed the accelerometer data at the fog node instead of a cloud node. |
| [47] | Latency + Bandwidth efficiency + Classification accuracy of the Fog compared to cloud computing. | The smartphone is equipped with Snapdragon 410 Quad-Core, which is 450 MHz, has 2 GB memory, and a J48Graft classifier. | J48Graft displayed a high classification accuracy of 98.56% compared to other baseline techniques. It utilized fog computing as the intermediary layer, which helped to achieve mobility, local data storage, scalability, and interoperability. Experimental results indicated fog computing had a lower latency, higher bandwidth efficiency, and more classification accuracy than cloud computing. | They effectively predicted the risky blood glucose levels in diabetic patients. |
| [17] | Energy efficient + Latency+ Mobility | The complete system was implemented, from the development of the cloud services to the software-hardware demonstration of the Smart e-Health Gateway prototype. | This concept provided an IoT-based health monitoring system that enhances intelligence, mobility, energy efficiency, interoperability, and security. | The authors evaluated the smart gateways at the network edge for developing high-level services such as real-time local data processing, local storage, and embedded data analysis based on fog computing. They presented different case scenarios that used smart healthcare IoT systems. |
5.2. Limitations and Research Directions for Distributed Processing in IoMT
5.3. Centralized Processing
5.4. Limitations and Research Directions for Centralized Processing in IoMT
5.5. Analysis Techniques
5.6. Limitations and Research Directions for Techniques in IoMT
6. Conclusions
Author Contributions
Competing interest
References
- Al Hamid, H.A., et al., A security model for preserving the privacy of medical big data in a healthcare cloud using a fog computing facility with pairing-based cryptography. IEEE Access, 2017. 5: p. 22313-22328. [CrossRef]
- Zhang, Y., et al., Health-CPS: Healthcare cyber-physical system assisted by cloud and big data. IEEE Systems Journal, 2015. 11(1): p. 88-95. [CrossRef]
- Damar, S., Koksalmis, G.H. A bibliometric analysis of metaverse technologies in healthcare services. Serv Bus (2024). [CrossRef]
- Batra, P. and Dave, D.M., 2024. Revolutionizing Healthcare Platforms: The Impact of AI on Patient Engagement and Treatment Efficacy. International Journal of Science and Research (IJSR), 13(10.21275), pp.613-624. [CrossRef]
- Rauniyar et al., "Federated Learning for Medical Applications: A Taxonomy, Current Trends, Challenges, and Future Research Directions," in IEEE Internet of Things Journal, vol. 11, no. 5, pp. 7374-7398, 1 March 1, 2024. [CrossRef]
- Azizan, A., Ahmed, W. & Razak, A.H.A. Sensing health: a bibliometric analysis of wearable sensors in healthcare. Health Technol. 14, 15–34 (2024). [CrossRef]
- Ali, O., Abdelbaki, W., Shrestha, A., Elbasi, E., Alryalat, M.A.A. and Dwivedi, Y.K., 2023. A systematic literature review of artificial intelligence in the healthcare sector: Benefits, challenges, methodologies, and functionalities. Journal of Innovation & Knowledge, 8(1), p.100333. [CrossRef]
- M. Khalil, Q. Abu Al-Haija, S.Ahmad, "Healthcare IoT networks using LPWAN", Chapter in: Low-Power Wide Area Network for Large Scale Internet of Things, 1st Edition, CRC Press, eBook ISBN9781003426974, 2024.
- Pergolizzi Jr. J, LeQuang J K, Vasiliu-Feltes I, et al. (October 04, 2023) Brave New Healthcare: A Narrative Review of Digital Healthcare in American Medicine. Cureus 15(10): e46489. [CrossRef]
- Osama, M., Ateya, A.A., Sayed, M.S., Hammad, M., Pławiak, P., Abd El-Latif, A.A. and Elsayed, R.A., 2023. Internet of medical things and healthcare 4.0: Trends, requirements, challenges, and research directions. Sensors, 23(17), p.7435. [CrossRef]
- Ahmed, S.F., Alam, M.S.B., Afrin, S., Rafa, S.J., Rafa, N. and Gandomi, A.H., 2024. Insights into the Internet of Medical Things (IoMT): Data fusion, security issues, and potential solutions. Information Fusion, 102, p.102060. [CrossRef]
- Aski, V.J., Dhaka, V.S., Parashar, A. and Rida, I., 2023. Internet of Things in Healthcare: A survey on protocol standards, enabling technologies, WBAN architectures, and open issues. Physical Communication, p.102103. [CrossRef]
- Kamalov, F., Pourghebleh, B., Gheisari, M., Liu, Y. and Moussa, S., 2023. Internet of medical things privacy and security: Challenges, solutions, and future trends from a new perspective. Sustainability, 15(4), p.3317. [CrossRef]
- 14. K. T. Putra et al., "A Review on the Application of Internet of Medical Things in Wearable Personal Health Monitoring: A Cloud-Edge Artificial Intelligence Approach," in IEEE Access, vol. 12, pp. 21437-21452, 2024. [CrossRef]
- Yu, X., et al., An adaptive method based on contextual anomaly detection in Internet of Things through wireless sensor networks. International Journal of Distributed Sensor Networks, 2020. 16(5): p. 1550147720920478. [CrossRef]
- Azimi, I., et al., Hich: Hierarchical fog-assisted computing architecture for healthcare IoT. ACM Transactions on Embedded Computing Systems (TECS), 2017. 16(5s): p. 1-20. [CrossRef]
- Rahmani, A.M., et al., Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Future Generation Computer Systems, 2018. 78: p. 641-658. [CrossRef]
- Alabdulatif, A., et al., Secure Edge of Things for Smart Healthcare Surveillance Framework. IEEE Access, 2019. 7: p. 31010-31021. [CrossRef]
- Pace, P., et al., An Edge-Based Architecture to Support Efficient Applications for Healthcare Industry 4.0. IEEE Transactions on Industrial Informatics, 2019. 15(1): p. 481-489. [CrossRef]
- Wang, X. and S. Cai, Secure healthcare monitoring framework integrating NDN-based IoT with edge cloud. Future Generation Computer Systems, 2020. 112: p. 320-329. [CrossRef]
- Azimi, I., et al. Empowering healthcare IoT systems with hierarchical edge-based deep learning. In Proceedings of the 2018 IEEE/ACM International Conference on Connected Health: Applications, Systems and Engineering Technologies. 2018. [CrossRef]
- Yu, J., et al. EdgeCNN: A Hybrid Architecture for Agile Learning of Healthcare Data from IoT Devices. in 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS). 2018. [CrossRef]
- Li, J., et al., A Secured Framework for SDN-Based Edge Computing in IoT-Enabled Healthcare System. IEEE Access, 2020. 8: p. 135479-135490. [CrossRef]
- Abirami, S. and P. Chitra, Chapter Fourteen - Energy-efficient edge-based real-time healthcare support system, in Advances in Computers, P. Raj and P. Evangeline, Editors. 2020, Elsevier. p. 339-368. [CrossRef]
- Gia, T.N., et al. Low-cost fog-assisted health-care IoT system with energy-efficient sensor nodes. In 2017, the 13th International Wireless Communications and Mobile Computing Conference (IWCMC). 2017. IEEE. [CrossRef]
- Keramidas, G., N. Voros, and M. Hübner, Components and Services for IoT Platforms. 2016: Springer. [CrossRef]
- Dastjerdi, A.V., and R. Buyya, Fog computing: Helping the Internet of Things realize its potential. Computer, 2016. 49(8): p. 112-116. [CrossRef]
- Osanaiye, O., et al., From cloud to fog computing: A review and a conceptual live VM migration framework. IEEE Access, 2017. 5: p. 8284-8300. [CrossRef]
- Bonomi, F., et al., Fog computing: A platform for internet of things and analytics, in Big data and internet of things: A roadmap for smart environments. 2014, Springer. p. 169-186. [CrossRef]
- Kraemer, F.A., et al., Fog computing in healthcare–a review and discussion. IEEE Access, 2017. 5: p. 9206-9222. [CrossRef]
- Tahir, S., et al., Fog-based healthcare architecture for wearable body area network. Journal of Medical Imaging and Health Informatics, 2017. 7(6): p. 1409-1418. [CrossRef]
- Farahani, B. et al., Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Generation Computer Systems, 2018. 78: p. 659-676. [CrossRef]
- Rahmani, A.-M., et al. Smart e-health gateway: Bringing intelligence to internet-of-things based ubiquitous healthcare systems. In 2015, the 12th Annual IEEE Consumer Communications and Networking Conference (CCNC). 2015. IEEE. [CrossRef]
- Stantchev, V., et al., Smart items, fog and cloud computing as enablers of servitization in healthcare. Sensors & Transducers, 2015. 185(2): p. 121.
- Andriopoulou, F., T. Dagiuklas, and T. Orphanoudakis, Integrating IoT and fog computing for healthcare service delivery, in Components and services for IoT platforms. 2017, Springer. p. 213-232. [CrossRef]
- Datta, S.K., C. Bonnet, and J. Haerri. Fog computing architecture to enable consumer-centric Internet of Things services. In 2015 International Symposium on Consumer Electronics (ISCE). 2015. IEEE. [CrossRef]
- Hou, X., et al., Vehicular fog computing: A viewpoint of vehicles as the infrastructures. IEEE Transactions on Vehicular Technology, 2016. 65(6): p. 3860-3873. [CrossRef]
- Yan, Y. and W. Su. A fog computing solution for advanced metering infrastructure. In 2016 IEEE/PES Transmission and Distribution Conference and Exposition (T&D). 2016. IEEE. [CrossRef]
- Li, J., et al. EHOPES: Data-centered Fog platform for smart living. In 2015 International Telecommunication Networks and Applications Conference (ITNAC). 2015. IEEE. [CrossRef]
- Vilela, P.H., et al., Performance evaluation of a Fog-assisted IoT solution for e-Health applications. Future Generation Computer Systems, 2019. 97: p. 379-386. [CrossRef]
- Aladwani, T., Scheduling IoT Healthcare Tasks in Fog Computing Based on their Importance. Procedia Computer Science, 2019. 163: p. 560-569. [CrossRef]
- Shukla, S., et al. A 3-Tier Architecture for Network Latency Reduction in Healthcare Internet-of-Things Using Fog Computing and Machine Learning. Proceedings of the 2019 8th International Conference on Software and Computer Applications. 2019. [CrossRef]
- Tahir, S., et al., An energy-efficient fog-to-cloud Internet of Medical Things architecture. International Journal of Distributed Sensor Networks, 2019. 15(5): p. 1550147719851977. [CrossRef]
- El Kafhali, S. and K. Salah, Performance modeling and analysis of Internet of Things enabled healthcare monitoring systems. IET Networks, 2019. 8(1): p. 48-58. [CrossRef]
- Badidi, E. and K. Moumane. We are enhancing the processing of healthcare data streams using fog computing at the 2019 IEEE Symposium on Computers and Communications (ISCC). 2019. IEEE. [CrossRef]
- Shrivastava, R. and M. Pandey, Real-time fall detection in fog computing scenario. Cluster Computing, 2020: p. 1-10. [CrossRef]
- Malathi, D., et al., Fog-assisted personalized healthcare-support system for remote patients with diabetes. J Ambient Intell Human Comput. 2019. [CrossRef]
- Tang, B., et al., A hierarchical distributed fog computing architecture for big data analysis in smart cities, in Proceedings of the ASE BigData & SocialInformatics 2015. 2015. p. 1-6. [CrossRef]
- Oueis, J., et al. Small cell clustering for efficient distributed fog computing: A multi-user case. in 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall). 2015. IEEE. [CrossRef]
- Agarwal, S., S. Yadav, and A.K. Yadav, An efficient architecture and algorithm for resource provisioning in fog computing. International Journal of Information Engineering and Electronic Business, 2016. 8(1): p. 48. [CrossRef]
- Gia, T.N., et al. Fog Computing in Healthcare Internet of Things: A Case Study on ECG Feature Extraction. in 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing. 2015. [CrossRef]
- Verma, P. and S.K. Sood, Fog Assisted-IoT Enabled Patient Health Monitoring in Smart Homes. IEEE Internet of Things Journal, 2018. 5(3): p. 1789-1796. [CrossRef]
- Wang, K., et al., Adaptive and Fault-Tolerant Data Processing in Healthcare IoT Based on Fog Computing. IEEE Transactions on Network Science and Engineering, 2020. 7(1): p. 263-273. [CrossRef]
- Jia, X. et al., Authenticated key agreement scheme for fog-driven IoT healthcare system. Wireless Networks, 2019. 25(8): p. 4737-4750. [CrossRef]
- Al-Khafajiy, M., et al., Intelligent Control and Security of Fog Resources in Healthcare Systems via a Cognitive Fog Model. ACM Transactions on Internet Technology, 2020. [CrossRef]
- Saha, R. et al., Privacy Ensured ${e}$ -Healthcare for Fog-Enhanced IoT Based Applications. IEEE Access, 2019. 7: p. 44536-44543.
- Devarajan, M., et al., Fog-assisted personalized healthcare-support system for remote patients with diabetes. Journal of Ambient Intelligence and Humanized Computing, 2019. 10(10): p. 3747-3760. [CrossRef]
- Awaisi, K.S. et al., Leveraging IoT and Fog Computing in Healthcare Systems. IEEE Internet of Things Magazine, 2020. 3(2): p. 52-56. [CrossRef]
- La, Q.D. et al., Enabling fog computing intelligence to reduce energy and latency. Digital Communications and Networks, 2019. 5(1): p. 3-9.
- Muthanna, A., et al., Secure and reliable IoT networks using fog computing with software-defined networking and blockchain. Journal of Sensor and Actuator Networks, 2019. 8(1): p. 15. [CrossRef]
- Sangpetch, O. and A. Sangpetch. Security context framework for distributed healthcare IoT platform. In International Conference on IoT Technologies for HealthCare. 2016. Springer. [CrossRef]
- Luo, E., et al., PrivacyProtector: Privacy-Protected Patient Data Collection in IoT-Based Healthcare Systems. IEEE Communications Magazine, 2018. 56(2): p. 163-168. [CrossRef]
- Al Baqari, M.R., Sdhcare: Secured Distributed Healthcare System. 2020.
- Tang, W., et al., Secure Data Aggregation of Lightweight E-Healthcare IoT Devices With Fair Incentives. IEEE Internet of Things Journal, 2019. 6(5): p. 8714-8726. [CrossRef]
- Thota, C., et al., Centralized fog computing security platform for IoT and cloud in the healthcare system, in Fog computing: Breakthroughs in research and practice. 2018, IGI Global. p. 365-378. [CrossRef]
- Gill, S.S., et al. Fog-based smart healthcare as a big data and cloud service for heart patients using IoT. in International Conference on Intelligent Data Communication Technologies and Internet of Things. 2018. Springer. [CrossRef]
- Sharma, S.K. and X. Wang, Live Data Analytics With Collaborative Edge and Cloud Processing in Wireless IoT Networks. IEEE Access, 2017. 5: p. 4621-4635. [CrossRef]
- Yang, G., et al., A Centralized Cluster-Based Hierarchical Approach for Green Communication in a Smart Healthcare System. IEEE Access, 2020. 8: p. 101464-101475. [CrossRef]
- Yuan, B., S. Ge, and W. Xing, A Federated Learning Framework for Healthcare IoT devices. arXiv preprint arXiv:2005.05083, 2020.
- Shukla, S., et al., An analytical model to minimize the latency in healthcare internet-of-things in a fog computing environment. PloS one, 2019. 14(11): p. e0224934. [CrossRef]
- Sharma, S., K. Chen, and A. Sheth, Toward Practical Privacy-Preserving Analytics for IoT and Cloud-Based Healthcare Systems. IEEE Internet Computing, 2018. 22(2): p. 42-51. [CrossRef]
- Kaur, P., R. Kumar, and M. Kumar, A healthcare monitoring system using random forest and internet of things (IoT). Multimedia Tools and Applications, 2019. 78(14): p. 19905-19916. [CrossRef]
- Panda, S. and G. Panda. Intelligent Classification of IoT Traffic in Healthcare Using Machine Learning Techniques. in 2020 6th International Conference on Control, Automation and Robotics (ICCAR). 2020. IEEE. [CrossRef]
- Patan, R., et al., Smart healthcare and quality of service in IoT using grey filter convolutional based cyber-physical system. Sustainable Cities and Society, 2020. 59: p. 102141. [CrossRef]
- Kumar, P.M., et al., Cloud and IoT based disease prediction and diagnosis system for healthcare using Fuzzy neural classifier. Future Generation Computer Systems, 2018. 86: p. 527-534. [CrossRef]
- Subasi, A., et al. IoT-based mobile healthcare system for human activity recognition. in 2018 15th Learning and Technology Conference (L&T). 2018. IEEE. [CrossRef]
- Farahani, B., M. Barzegari, and F.S. Aliee. Towards collaborative machine learning driven healthcare internet of things. In Proceedings of the International Conference on Omni-Layer Intelligent Systems. 2019. [CrossRef]
- Sharma, S., et al., DeTrAs deep learning-based healthcare framework for IoT-based assistance of Alzheimer patients. Neural Computing and Applications, 2020: p. 1-13. [CrossRef]
| Ref | Category | Heterogeneity | Scalability | Mobility | Security |
|---|---|---|---|---|---|
| [31] | Healthcare | ✓ | × | ✓ | ✓ |
| [32] | × | ✓ | ✓ | × | |
| [33] | ✓ | × | × | ✓ | |
| [30] | ✓ | × | ✓ | ✓ | |
| [34] | × | × | × | × | |
| [35] | × | × | × | × | |
| [36] | Connected Vehicles | × | × | ✓ | × |
| [37] | × | × | ✓ | × | |
| [38] | Smart Living | × | ✓ | × | × |
| [39] | ✓ | × | × | × | |
| [48] | × | × | × | × | |
| [49] | Energy Consumption | ✓ | × | × | × |
| [50] | Resource Management | ✓ | × | × | × |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





