1. Introduction
In recent years, Mobile Edge Computing (MEC) has emerged as a prominent computing paradigm to accommodate the rapid proliferation of Internet of Things (IoT) devices and novel application scenarios such as virtual reality (VR), augmented reality (AR), autonomous driving, and intelligent robotics [
1]. However, ground-based MEC networks face inherent limitations in coverage, deployment flexibility, and the handling of hotspot issues due to the immobility of MEC servers. The limitations of stationary infrastructure present challenges in accommodating the dynamic edge network environment. Consequently, researchers have increasingly focused on UAV-assisted MEC (UAV-MEC), which offers significant advantages in terms of high mobility and low deployment costs [
2,
3].
The existing body of work addresses numerous challenges associated with UAV-MEC systems, including the limited computational and battery capacities of UAVs, trajectory planning, cooperative control of multiple UAVs, and data transmission security. Various optimization problems have been formulated to tackle these challenges by adjusting offloading decisions, bandwidth allocation, caching strategies, and UAV trajectories. Common optimization objectives include minimizing task execution time [
4], reducing energy consumption [
5,
6], or balancing a weighted combination of both [
7]. For instance, resource allocation and task offloading ratios are jointly optimized to minimize the total energy consumption of user devices (UDs) under partial offloading strategies [
8], and the joint design of UAV trajectory, task allocation, and communication resource management aims to minimize a weighted sum of execution latency and energy consumption [
9]. Similarly, maximizing computational efficiency to ensure robust system performance is another focus [
10,
11]. However, these objectives often emphasize system performance over the Quality of Experience (QoE) for UDs, potentially leading to unfair resource allocation.
From the users’ perspective, it is crucial to consider both waiting time and execution time to measure QoE in UAV-MEC systems. Several studies have addressed this by formulating optimization problems aimed at minimizing task response time, which encompasses both waiting and execution times [
12,
13]. For instance, [
14] proposes a joint optimization approach that considers offloading ratios, service policies, and UAV trajectories to minimize the maximum delay of delay-sensitive tasks in each time slot. Furthermore, [
15] introduces a comprehensive metric called the shrinkage ratio, balancing factors such as waiting time, execution time, task length, and UD computational capabilities, providing a straightforward and effective measure of optimization efficiency in UAV-MEC networks. However, these studies often assume that computation tasks are divisible and do not fully account for the impact of a large number of UDs in UAV-MEC systems. In reality, the increasing number of UDs and the binary offloading model for indivisible tasks present significant challenges in maintaining good QoE for users.
Optimizing user QoE in large-scale edge networks remains a challenging problem, as measuring user experience typically involves considering response latency rather than task execution latency [
16]. The offloading decisions of multiple users, resource allocation strategies, and UAV trajectories often lead to tightly coupled optimization problems. A holistic metric called the shrinkage ratio has been proposed to reconcile variables such as waiting delay, processing delay, and the computational resources of edge devices [
15]. However, previous work did not account for the binary offloading approach nor the impact of a growing number of nodes within expansive IoT networks on the complexity of the solution.
In this paper, we investigate the QoE-oriented computation task offloading optimization problem in a large scale UAV-MEC network with considering binary offloading mode at each UD. We aim to minimize the sum of shrinkage ratios for all UDs by jointly optimizing UAV trajectory, task offloading mode selection, network bandwidth and computation resource allocation. To handle the high complexity of large number of UDs and the coupling of drone trajectory for each coverage partition and resource allocation for computation task, we propose an efficient propose a two-tier optimization scheme to solve it. We first develop a low-complexity partition coverage algorithm algorithm based on Welzl method and determine the UAV flight trajectory by solving a TSP problem. Subsequently, for the network bandwidth and computing resource allocation sub-problem, we develop a low-complexity CD-based method for the small scale Iot network and a ADMM-based method which can leverages parallel computing to enhance solving speed, suitable for large-scale networks.
The main contributions of this paper are summarized as follows:
We extend model in [
13,
15] to handle binary task offloading mode and large scale nodes in a UAV-MEC system. Our model takes into consideration the impact of UAV on the response time of UDs while leveraging the radius coverage of UAV to reduce the high complexity in large-scale node scenarios. Our model exhibits practicality and scalability in resource allocation within large-scale IoT-enabled UAV-MEC.
We propose an two-tier optimization scheme to decouple the drone trajectory planning and resource allocation for computation task. We design a circle cover algorithm based on Welzl method to divide area into smaller partitions to reduce the scale of the problem.
We develop a CD-based method and a ADMM-based method for the task offloading mode selection and resource allocation in UAV-MEC system. The CD-based method has a linear complexity with respect to network scale, while the ADMM-based approach can convergence fast, making it suitable for large-scale networks.
We conduct plenty of numerical simulations to evaluate the effectiveness and practicability of our algorithm. Our algorithm outperforms all baseline algorithms and its number of iteration exhibits a linear relationship with the scale of network.
The rest of this paper is organized as follows.
Section 2 discusses the related work on UAV-MEC. In
Section 3, we present a system model for user QoE optimization in large-scale edge networks and formulate it as a combinatorial optimization problem.
Section 4 provides the algorithm for solving this optimization problem. In
Section 5, we validate the effectiveness of the algorithm through numerical experiments.
Section 6 concludes this paper and discusses future work.
2. Related Work
Unmanned aerial vehicles (UAVs) have garnered significant attention in the field of mobile edge computing (MEC) due to their low cost and high flexibility, which can substantially enhance the coverage and efficiency of edge networks [
3]. For instance, Xiang et al. [
17] propose a joint optimization algorithm for UAV-MEC that incorporates task offloading strategies and UAV trajectory planning, demonstrating superior energy efficiency and convergence compared to other methods. Similarly, He et al. [
18] focus on optimizing 3-D multi-UAV trajectories in MEC systems to ensure fairness in task allocation and minimize energy consumption. Zhang et al. [
19] utilize UAVs as aerial relay platforms to forward signals from ground or air to edge servers or other edge devices. Liu et al. [
5] investigate the use of UAVs as resource-constrained mobile edge nodes that provide limited computing services to terminal devices, acting as relays for computation tasks that cannot be completed locally. Gao et al. [
20] address secure data transmission in UAV-relay assisted maritime MEC systems by proposing a scheme that optimizes transmit power, time slot allocation, and UAV trajectory, enhancing both system security and computation capability.
Integration of UAVs with new-generation communication technologies has also been explored. Jiao et al. [
21] maximize the rate of strong users while ensuring the target rate for weak users in an intelligent reflecting surface (IRS)-based UAV-assisted NOMA downlink network by optimizing the IRS-UAV location. Wang et al. [
22] propose an energy minimization scheme for UAV-based MEC and traffic offloading in broadband Terahertz (THz) mobile networks. Additionally, M. A. Baker Siddiki Abir et al. [
23] introduce a digital twin-based aerial MEC architecture for 6G networks, employing UAVs as aerial base stations with MEC capabilities to deliver high network performance for real-time and latency-sensitive applications.
Recent research has also explored the synergy between UAVs and machine learning to enhance MEC systems. For example, Chen et al. [
24] leverage deep reinforcement learning to optimize UAV trajectory and resource allocation in real-time, improving overall system efficiency under dynamic network conditions. Li et al. [
25] use federated learning in UAV-assisted MEC to enable distributed model training while preserving data privacy, essential for sensitive applications. Xu et al. [
26] develop a scalable optimization framework combining graph theory and convex optimization to manage UAV trajectories and resource allocation in dense urban environments, reducing computational complexity and adapting to the varying demands of heterogeneous IoT devices. However, these studies primarily focus on enhancing system performance and often overlook the Quality of Experience (QoE) for user devices, potentially leading to unfair resource distribution.
QoE in UAV-MEC systems is crucial that attracted some researcher attention. Tian et al. [
27] design a three-tier UAV-MEC network that includes users, drones, and a cloud center, introducing an optimization metric called the response ratio based on user preferences and real-time requirements. Shen et al. [
15] propose a metric called the shrinkage ratio to measure the optimization efficiency brought by the UAV-MEC network to users, transforming QoE optimization into a minimization problem of the shrinkage ratio. However, many of these studies assume divisible computation tasks and do not fully consider the challenges posed by a large number of user devices and the binary offloading model for indivisible tasks, which significantly impacts QoE.
3. System Model and Problem Formulation
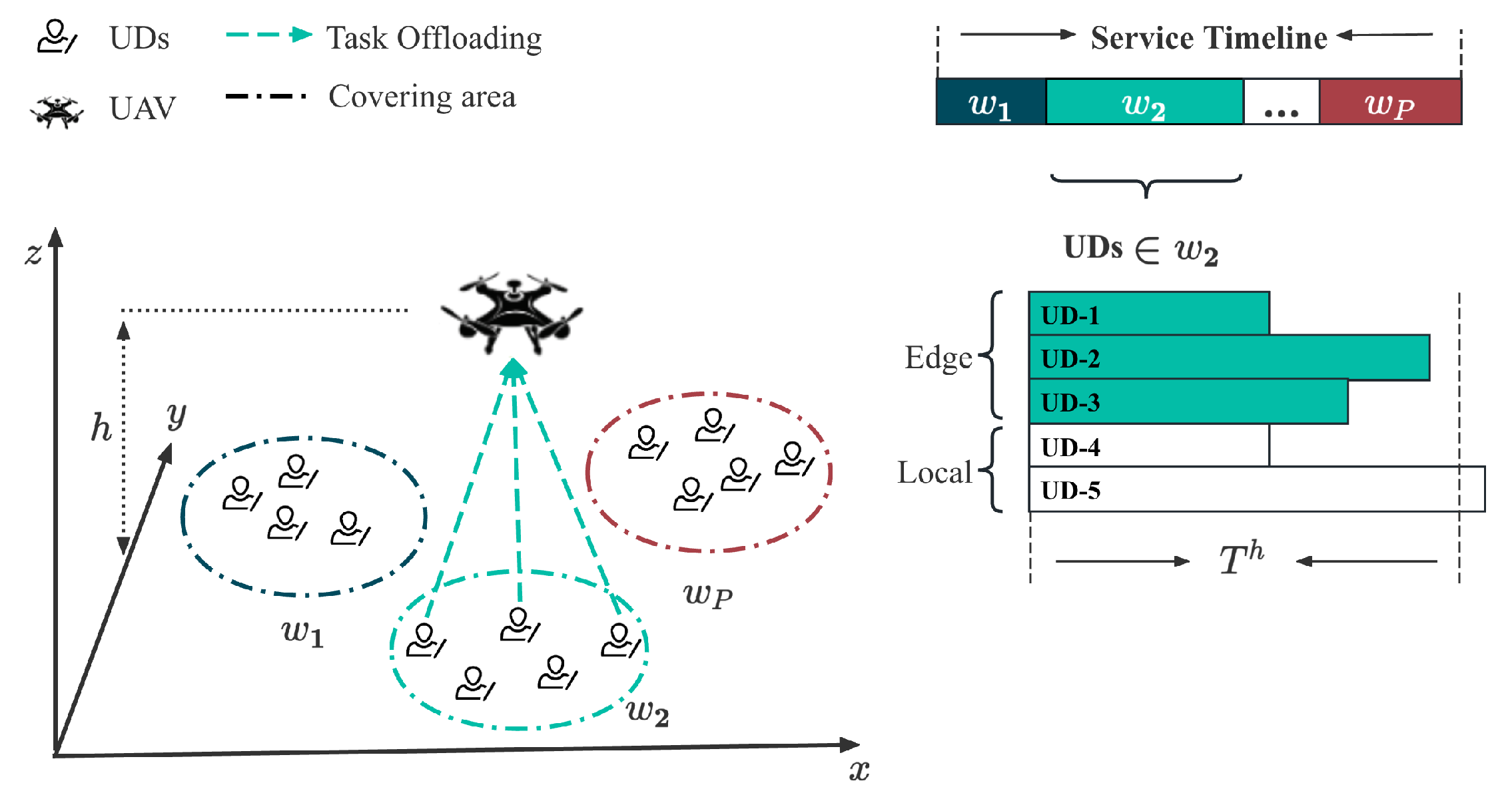
We consider the UAV-assisted MEC network as shown in
Figure 1, which comprises
I UDs and a UAV equipped with a lightweight edge computing server. The set of all UDs is denoted by
. Each UD has an indivisible, computation-intensive task
characterized by the tuple
within a time period, where
represents the amount of computation workload (in CPU cycles), and
denotes the data size (in bytes). It is assumed that each generated task can be completely processed in a single time period.
3.1. UAV Coverage Partition and Flight Model
In a reality Iot network, the spatial distribution of UDs usually exhibits a certain level of clustering [
28], so here we partition them into multiple circles area with a same radius which equals to the coverage radius of UAV [
29]. Let
denote all the coverage circles of UAV, where
represents the coordinates of the center of coverage circle
p, and the set
represents all user equipment located within coverage circle
p. Let
denote the location of UD-
m, where
and
represent the horizontal and vertical coordinates respectively, satisfying
,
,
.
We assume that UAV employ a hover-fly-hover mode similar to [
30]. The UAV’s movement can be simplified to constant-speed linear motion between multiple coverage circles. The UAV does not perform task offloading while in transit and only provides task computing services to UDs within a coverage circle when hovering above it. The UAV starts from a designated coverage area and traverses all coverage circles along the shortest path. Let the non-repetitive ordered set
represent the UAV’s trajectory. Once the partition set
is obtained, we can determine the UAV trajectory
by solving a standard small scale TSP problem.
3.2. Computation Model
Due to the indivisibility of computation tasks, we adopt a binary task offloading mode for each UDs. We define a binary decision variable for UD i to determine the offloading choice. If equals 1, the computation task is offloaded to the edge server on the UAV; otherwise, the task is processed locally.
3.2.1. Local Computing
If
, then UD
i can process the computation task locally at the initial stage of the system without waiting for the UAV’s arrival. Let
denote the local CPU frequency of UD
i. Thus, the total delay of task
in local computation mode can be expressed as:
3.2.2. Edge Computing
If
, then UD
i needs to wait for the UAV to reach its partition and then offload task to the UAV for execution. When the UAV is hovering over coverage circle
p, multiple user devices within the set
communicate with the UAV through orthogonal frequency-division multiple access (OFDMA) such that interference among multiple UDs can be neglected. During the task offloading process, the uplink bandwidth
W is allocated to multiple UDs selecting the offloading computation mode, enabling parallel transmission. To ensure resources wastage, channel bandwidth should only be allocated to UDs who select the edge computation mode. Thus, we have the following bandwidth constraints:
Since air-to-ground communication only occurs when the UAV is in a hovering state, there is no Doppler frequency shift during communication due to the UAV’s high-speed movement [
31]. Let
represent the three-dimensional coordinates of UD
i. When the UAV hovers over coverage circle
p and provides task offloading services to UD
i, the channel gain between them can be expressed as
, where
represents the unit-distance channel gain at 1 meter. The data transmission rate can be expressed as:
where
denotes the transmission power of UD
i, and
represents the additive Gaussian white noise power. The delay of task
offloaded to the UAV can be expressed as:
Assuming that tasks offloaded to the UAV can be executed in parallel, the UAV’s computational resources need to be allocated to multiple user tasks. Let
represent the computational frequency of the edge server, and
represent the computational frequency allocated to UD
i by the edge server. Then, in the edge computation mode, the execution time of task
on the UAV can be expressed as:
Similar to the bandwidth allocation constraints (
2) and (
3), the allocation of UAV’s computational resources should also satisfy the following conditions:
We consider a fixed hover time, that is, the UAV hovers in each area for the same duration
, and the time required for the UAV to fly from the previous area
to the area
is denoted as
. The total time required for the area
to wait for the UAV to reach the center of the area can be expressed as:
In the edge computation mode, the total delay incurred by user
i in processing its computational task within coverage area
can be expressed as:
In addition, due to the usually negligible transmission time compared to task offloading and drone computation [
32], the total latency incurred by user
i in processing its computing task can be expressed as:
3.3. Problem Formulation
We aim to optimize the QoE of task offloading services in UAV-edge networks, a goal achieved by minimizing the sum of all user devices’ shrinkage rates. Similar to [
15], the sum of system shrinkage rates can be represented as:
By jointly optimizing the partitioning strategy of coverage areas
, the UD’s computation mode selection
, uplink bandwidth
, and UAV’s computation resource allocation strategy
, the objective is to minimize the sum of all users’ shrinkage rates. It is noteworthy that the coverage strategy
here includes the coordinates of each coverage circle and the set of user devices it contains. Thus, the aforementioned problem of minimizing the sum of shrinkage rates can be formulated as:
Here, constraints (2), (3), (7), (8) ensure that the uplink bandwidth for task offloading and the UAV’s computation resources are allocated only to valid links, (15)-(17) restrict the feasibility of the coverage strategy, (18) ensures that each device completes the task offloading within the hover time. Due to the involvement of binary constraint (14) and a non-convex objective function, P1 is a coupled MINLP problem. Clearly, solving it directly is challenging.
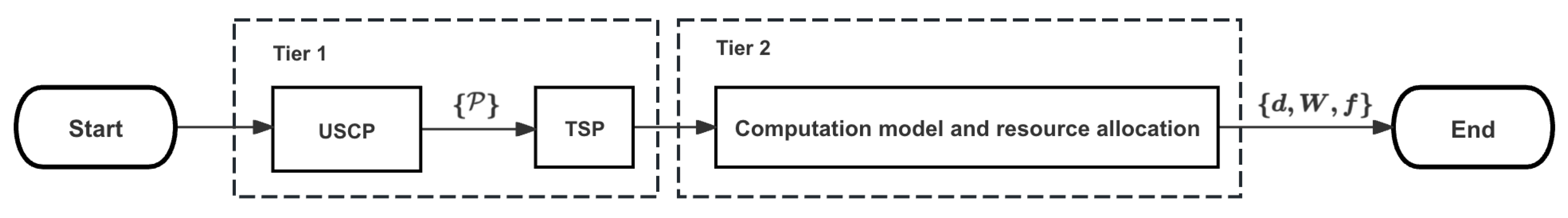
4. Algorithm Design
In this section, an efficient two-tier algorithm is proposed to address the formulated non-convex problem. Firstly, a polynomial-time complexity greedy algorithm based on the Welzl method [
33] for the UAV set covering problem (USCP) is proposed to obtain a feasible
. Secondly, from the perspectives of algorithm complexity and solution quality, two different strategies are proposed in the second tier for computation mode selection and resource allocation problem. The process of the global algorithm is depicted in
Figure 2.
4.1. UAV Set Covering Probelm
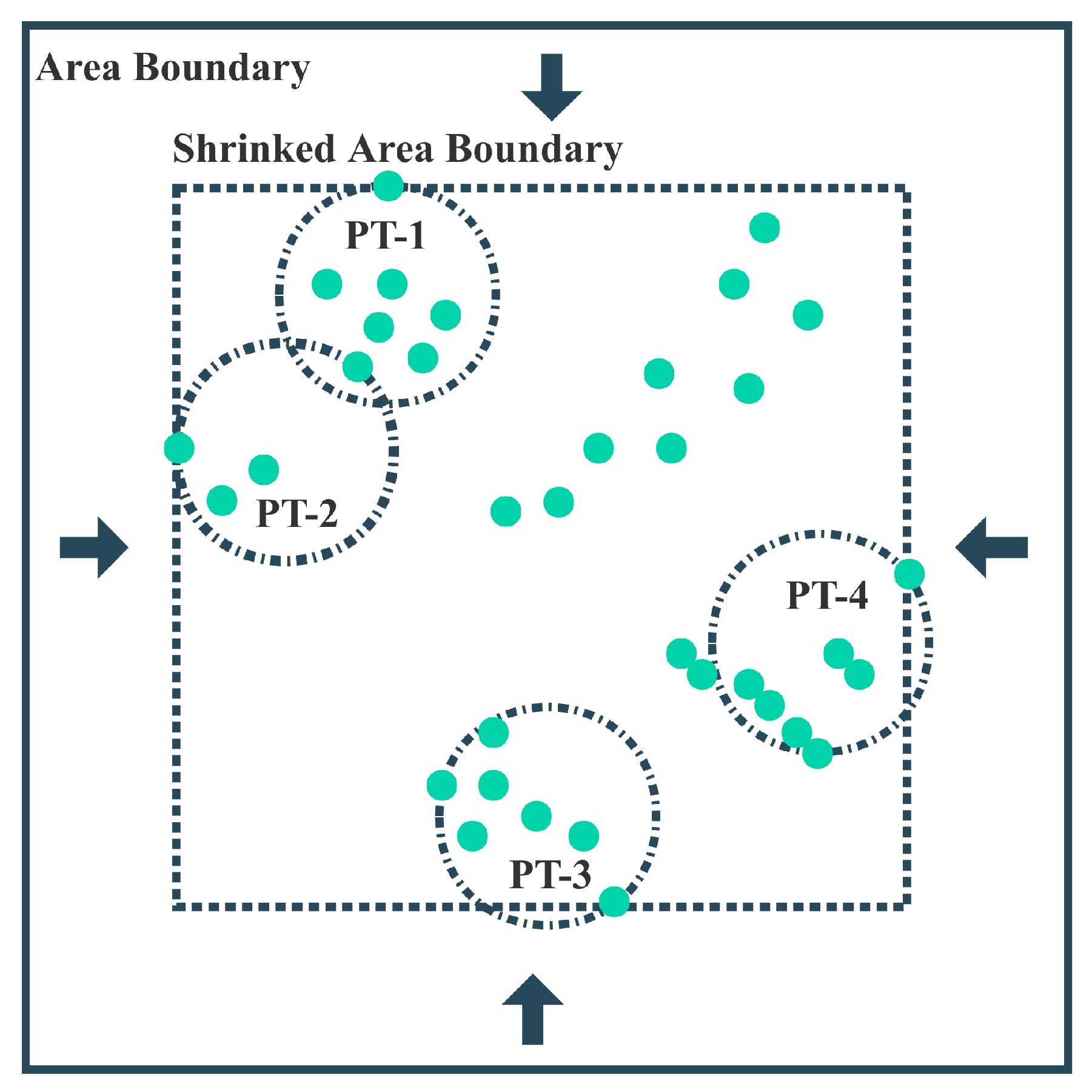
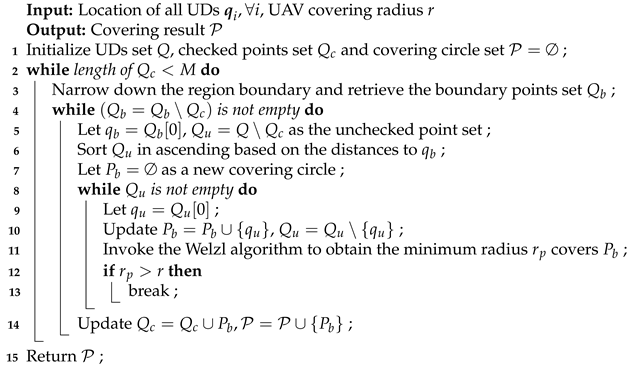
Since the user devices within a single coverage circle can concurrently receive task offloading services provided by the UAV, to enhance system efficiency, we aim to minimize the number of coverage areas, thus minimizing the time spent by UAVs in position shifting. This problem can be described as a fixed-radius circular coverage problem or an UAV set covering problem, which aims to cover all UDs within the system area using multiple circles with a fixed radius r, while minimizing the number of circles used. This is a typical NP-hard problem, for which there is no polynomial-time exact algorithm. In this section, we propose the Welzl-based UAV set covering (WUSC) algorithm, which provides an approximate solution to the coverage circle set in polynomial time.
The Welzl algorithm is an incremental algorithm used to solve the minimum enclosing circle problem. It takes all points within a circular coverage area and returns the minimum radius of the circle. We consider iteratively invoking this algorithm to solve the fixed-radius circular coverage problem. As shown in
Figure 3, the boundary of the system area is continuously reduced until there exists a device exactly on the boundary. Then, starting from a point
i on the boundary and initializing a coverage area
, the device closest to this point within the region is added to the set
, and it is determined using the Welzl algorithm whether the set can be completely covered by a circle with a radius not exceeding
r. This process is repeated until all user devices are included in some coverage set. Algorithm 1 describes the detailed procedure of the WUSC algorithm.
|
Algorithm 1: WUSC algorithm |
 |
Additionally, once the coverage strategy
is obtained, the UAV trajectory
can be obtained by a standard TSP model based on the partitions. Then, P1 can be reformulated as:
Note that P2 is still a MINLP problem. However, since the hover time is constant, there is no coupling between multiple partitions, and thus, the problem can be divided into multiple smaller sub-problems for parallel solution based on the partition dimension. We will present the algorithms for P2 as follows.
4.2. Computation Mode Selection and Resource Allocation
We can decompose P2 into
P independent sub-problems in the following form according to the coverage areas:
For problem P2.1, we will propose two different algorithms to solve it. The first is a low-complexity CD-based algorithm, suitable for smaller-scale IoT networks. The second is a joint optimization algorithm based on ADMM technique, designed for larger-scale networks that require higher solution precision.
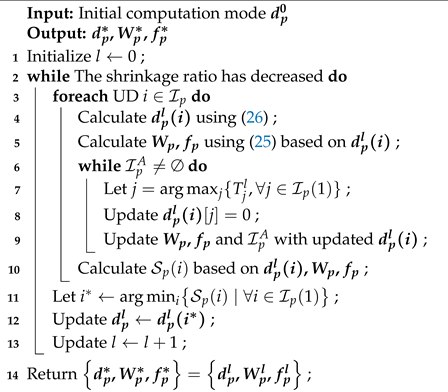
4.2.1. Alternating Optimization using CD Method
In this section, we consider alternating iterative optimization of discrete and continuous variables. Given the computation mode
, let
represent the set of UDs choosing local computation mode in coverage area
p, and
represent the set of users choosing edge computation mode. Then, P2.1 can be equivalently transformed into the following form:
P2.1’ is a convex problem, which can obtain the optimal closed-form solution for the problem using the KKT conditions. By introducing Lagrange multipliers
for the inequality constraints (18), (
2), (
7), we can obtain the Lagrangian function as:
The corresponding KKT conditions can be derived as:
Based on the KKT system of equations (
24), we can derive the following lemma:
Lemma 1. When the optimal solution of P2.1’ is obtained, the resources are fully allocated to the users, i.e., hold strictly.
Proof. From (a), (b), (c), (d), (g), it can be inferred that . Substituting (c) and (d) into the equations yields and , which means that the bandwidth and computational resources should be allocated entirely to the users when the optimal solution is achieved. □
We refer to the resource allocation strategy obtained without considering constraints (18) as the optimal solution , and the optimal solution of P2.1’ as a suboptimal solution . Based on whether , we can analyze P2.1’ in the two different cases as follows.
1) , meaning that there is no UDs violate the hovering constraint under . In this case, we have the following lemma for this optimal solution.
Lemma 2. When holds, both and have corresponding closed-form solutions.
Proof. We have
when hovering constraints are not in effect. Based on (a) and (b), we have
and
. Then we have
and
. Finally, substituting
and
into (a) and (b) yields the following closed-form solutions for
:
□
2)
, which means that some UDs violate the hover constraint under
. If the
has a solution, it indicates that the suboptimal strategy assigns additional bandwidth or computation resources to those UDs that exceed the hover time, allowing them to complete the computation within
. However, this approach simultaneously increases the time consumed for other non-violating devices. Let
denote the set of UDs which choose the edge computing mode and violate the hover constraint, and
represents the others. According to (
24), a complex system of equations with
variables and equalities can be derived. Enumerating
possible closed-form solutions is impractical. Moreover, if the
has no solution, it implies the bandwidth and computation resource of the UAV is insufficient to meet the computational demands of all selected offloading UDs within the given hover time
. Therefore, these two parts
and
cannot be fully decoupled by the CD method.
In summary, we can obtain the optimal
in
using (
25) for the first type of problem. For the second type, the corresponding KKT equations either have no solution or are challenging to solve directly. To minimize coupling and simplify the solution of the KKT equations, a greedy strategy can be adopted by converting the second type problem approximately to the first type. Additionally, for the computation mode
, we consider obtaining a locally optimal solution through a simple one-dimensional linear search. For convenience, let
represent the computation modes of all UDs within coverage area
p. At the beginning of the
-th iteration, the initial value is defined as
. Each user attempts to change their computation mode based on
:
where
denotes the negation operation for binary variables, e.g.,
,
. This generates
different computation modes, and the one with the smallest shrinkage rate is selected as the return value for the
-th iteration. A locally optimal solution is achieved when no user can further reduce the global shrinkage rate by changing their computation mode. Algorithm 2 describes the detailed procedure of the CD-based greedy (CD-Greedy) algorithm for P2.1.
|
Algorithm 2: CD-Greedy Algorithm for P2.1 |
 |
4.2.2. Joint Optimization Using ADMM Method
The main advantage of the CD-based algorithm lies in its simplicity and relatively high efficiency due to the closed-form resource allocation strategy. However, alternating optimization is prone to falling into local optima, and the one-dimensional search causes the number of iterations required for convergence to increase with the network scale. In this section, we will propose an ADMM-based algorithm to jointly optimize computation mode and resource allocation. The main idea is to decompose the coupled problem P2.1 into
parallel small-scale MINLP problems. First, to eliminate the coupled inequality constraints, we introduce auxiliary variables to reformulate P2.1 into the following equivalent form:
where
is the simplified form of the original objective function:
is the equivalent form of the inequality constraints in the original problem:
where
denotes the feasible set of
:
Problem P2.2 can be effectively decomposed using the ADMM method to find the optimal solution to the dual problem. By introducing Lagrange multipliers for the equality constraint (29), we can represent the augmented Lagrangian function of P2.2 as:
where
,
,
, and
represents the step size. The corresponding dual problem can be formalized as:
where
represents the Lagrangian dual function of
,
,
.
The ADMM method solves the dual problem P2.3 by iteratively optimizing . Let the solution obtained at the l-th iteration be . The operations required in the -th iteration can be described as the following three steps:
Since there is no coupling among multiple users, (
37) can be decomposed into
identical subproblems solved in parallel. Each subproblem can be formulated as:
When
, we have
. In this case,
can be directly computed using (
38). When
, (
38) becomes a standard convex optimization problem and yields a closed-form optimal solution. For example, by separating
and
into two independent parts, setting the first derivative to zero and combining with the Cardano formula, we can obtain a unique optimal solution. Therefore, we consider the two possible values of
separately. After obtaining the corresponding
and
, they are substituted into (
38), and the smaller value is chosen as the optimal solution for
. Note that the time complexity for solving each subproblem
is
.
From (
33), it is evident that to ensure the problem’s solvability, it is necessary to ensure
. Since the offloading decisions are known, here we only need to consider the auxiliary variables corresponding to the edge computing mode UDs. The solution for
can be formulated as a convex problem in the following form:
To obtain the optimal solution to P2.4, we consider using convex optimization solver, e.g., CPLEX, CVX. Solvers based on standard convex optimization methods like interior point methods ensure that the obtained solution is the optimal solution, thereby preventing the problem P2.4 from being infeasible due to taking on positive infinity.
This can be achieved by updating the Lagrange multipliers
according to the following rules:
Obviously, the time complexity for updating the Lagrange multipliers is .
Repeat the above three steps until the absolute errors of
and
reach the desired accuracy. The absolute errors of both can be measured by the following equation:
where
is a predefined error bound, typically a very small positive number. Due to the presence of duality gap for P2.1, the ADMM algorithm may not converge to the optimal solution. Therefore, when the algorithm terminates, the dual optimal solution
is an approximate solution, and its performance gap will be evaluated through simulation experiments. Algorithm 3 describes the detailed procedure of the ADMM-based joint optimization algorithm for P2.1.
|
Algorithm 3: ADMM-based Algorithm for P2.1 |
 |
4.3. Computational Complexity Analysis
The WUSC algorithm consists of nested three-level loops, where the outer loop is used to check if there are any uncovered UDs, and the remaining two loops iterate over the boundary point set and attempt to construct a new coverage area starting from each boundary point. The time complexity of implementing the minimum circle covering of n vertices using the Welzl algorithm is , thus the time complexity of generating a coverage area in each iteration of the middle loop is . In addition, considering that WUSC employs sorting, the overall time complexity is .
Let denote the number of iterations, the time complexity of CD-based greedy algorithm can be expressed as = , where represents the partition where user i located. However, due to the computation modes searching along only one dimension for each iteration, in most cases, removing the UD with the maximum timeout only needs one. Therefore, the average time complexity is closer to .
The time complexity of the ADMM method is mainly determined by Step 2. For example, using an interior point method would result in a high time complexity of the step 2 of . The total computational complexity can be given by .
5. Simulation Results
In this section, we evaluate the performance of two algorithms through numerical experiments. The system area is a square with a side length of 1 km, containing a UAV carrying computing equipment to provide task offloading services for all UDs. We assume all UDs are homogeneous, with the same local computing frequency and transmission power,
GHz,
W,
. For the UAV, similar to [
15], we set
GHz,
MHz,
m/s,
m. Additionally, for channel conditions, we set
dBm,
dBm [
9].
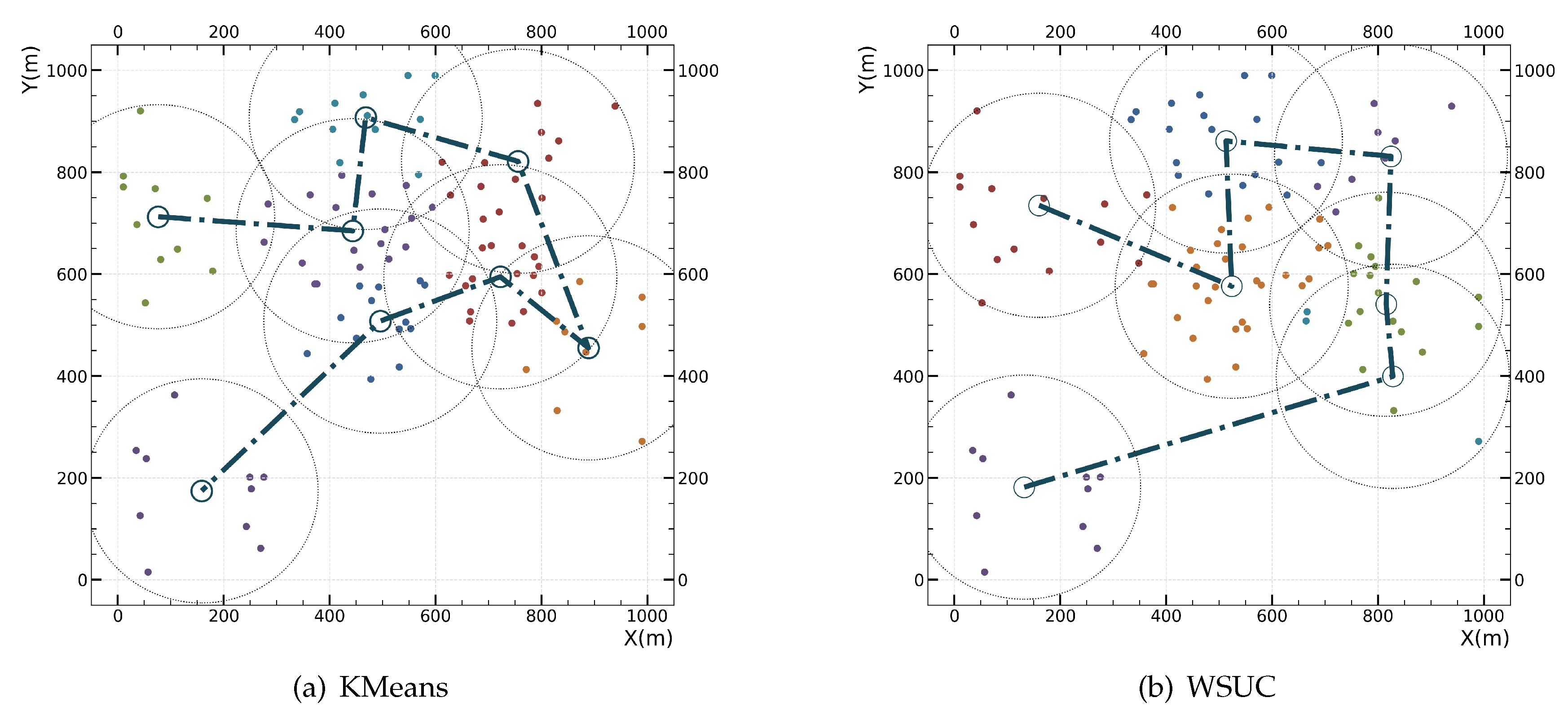
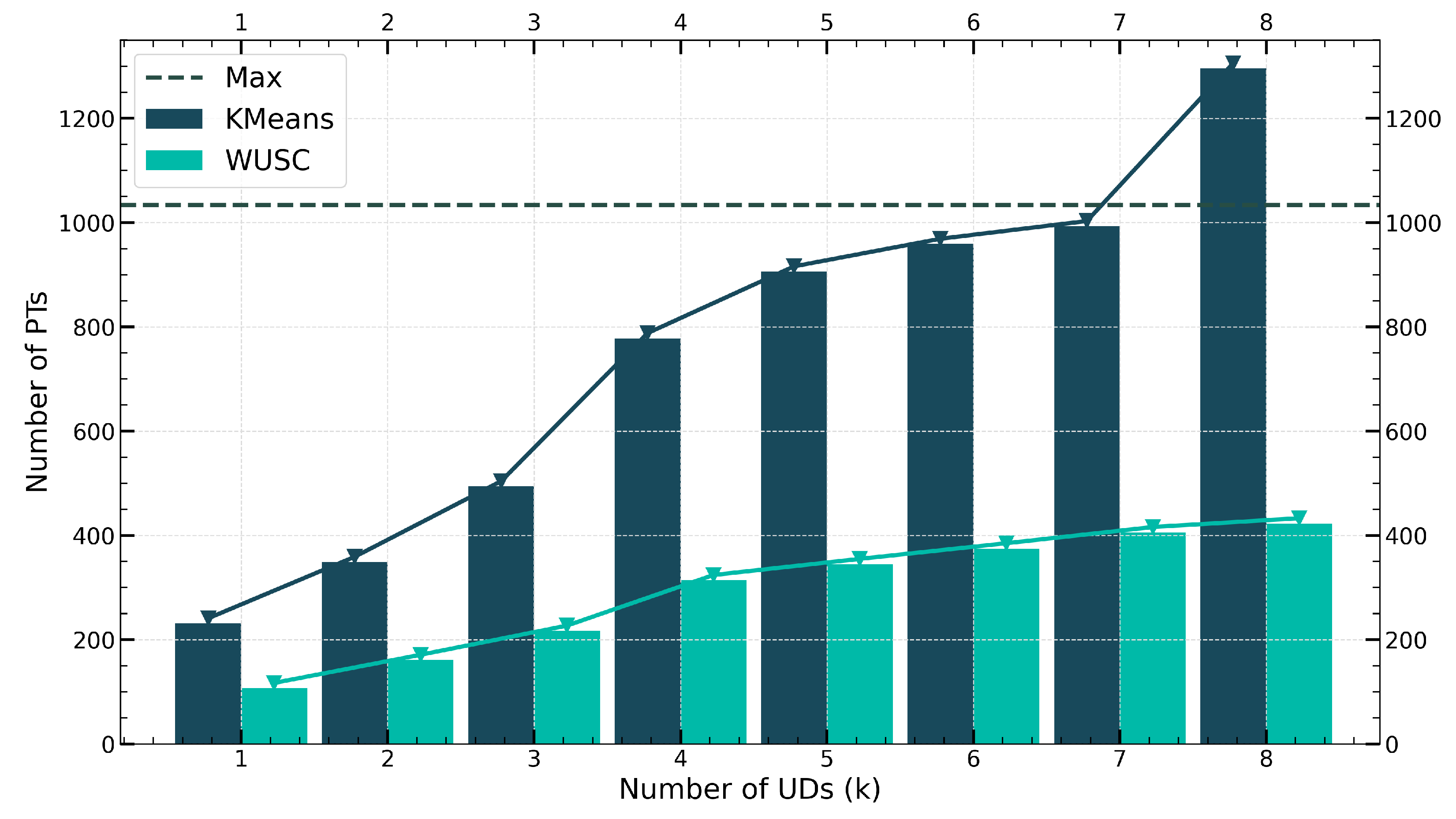
Figure 4 shows the results of performing fixed-radius circular coverage in the system area with 100 UDs using KMeans and WUSC algorithms, as well as the shortest path for the UAV departing from the specified coverage area. KMeans is a commonly used clustering algorithm in machine learning. The test results indicate that WUSC requires fewer coverage circles than KMeans, which to some extent reduces the time the UAV spends on location movement, thereby improving the utilization of bandwidth and computing resources. Experimental results show that compared to the KMeans method, WUSC reduces the time the UAV spends on location movement by 10%.
Figure 5 depicts the area coverage results for different numbers of UDs in a larger area (
km
2). As the total number of UDs increases, the number of coverage circles required by WUSC slowly rises, while KMeans exceeds the maximum number of circles required to cover the entire area at
. The number of coverage circles required by WUSC is close to
of KMeans, indicating that in large-scale fixed-radius circular coverage problems, the solution provided by WUSC is significantly superior to clustering methods.
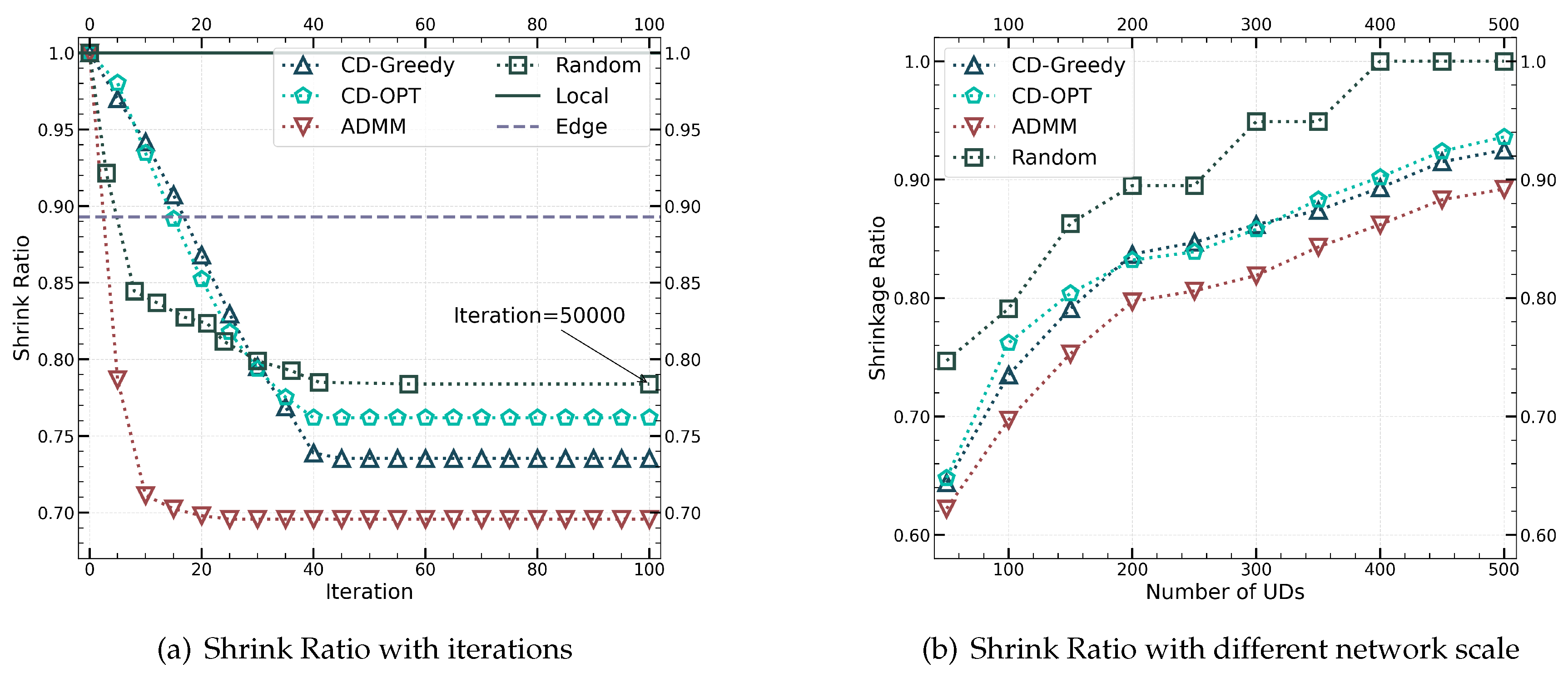
Figure 6 illustrates the trend of shrinkage ratio variation for different algorithms, where
Figure 6a represents the convergence curves of shrinkage ratio with the increase of iteration numbers in a network with 100 UDs.
Figure 6b shows the trend of shrinkage ratio variation as the network scale increases for different algorithms. It can be observed from
Figure 6a that both CD-Greedy and ADMM methods can converge stably to a good result than CD-OPT after tens of iterations. The CD-OPT method is similar to the CD-Greedy method, with the difference that CD-OPT utilizes convex optimization to solve P2.1. In comparison, ADMM has a faster convergence rate, while CD-Greedy requires iterations close to the total number of devices finally offloaded, which is closely related to the characteristic of one-dimensional search. Compared to CD-OPT, Random, Local, or Edge methods, the two proposed algorithms demonstrate excellent performance. From Figure
Figure 6b, it can be seen that both CD-Greedy and ADMM can work normally in networks with hundreds of edge nodes, with ADMM reducing the compression ratio by about
compared to CD-Greedy. The Random method, on the other hand, can only choose the Local strategy due to its inability to obtain feasible offloading schemes.
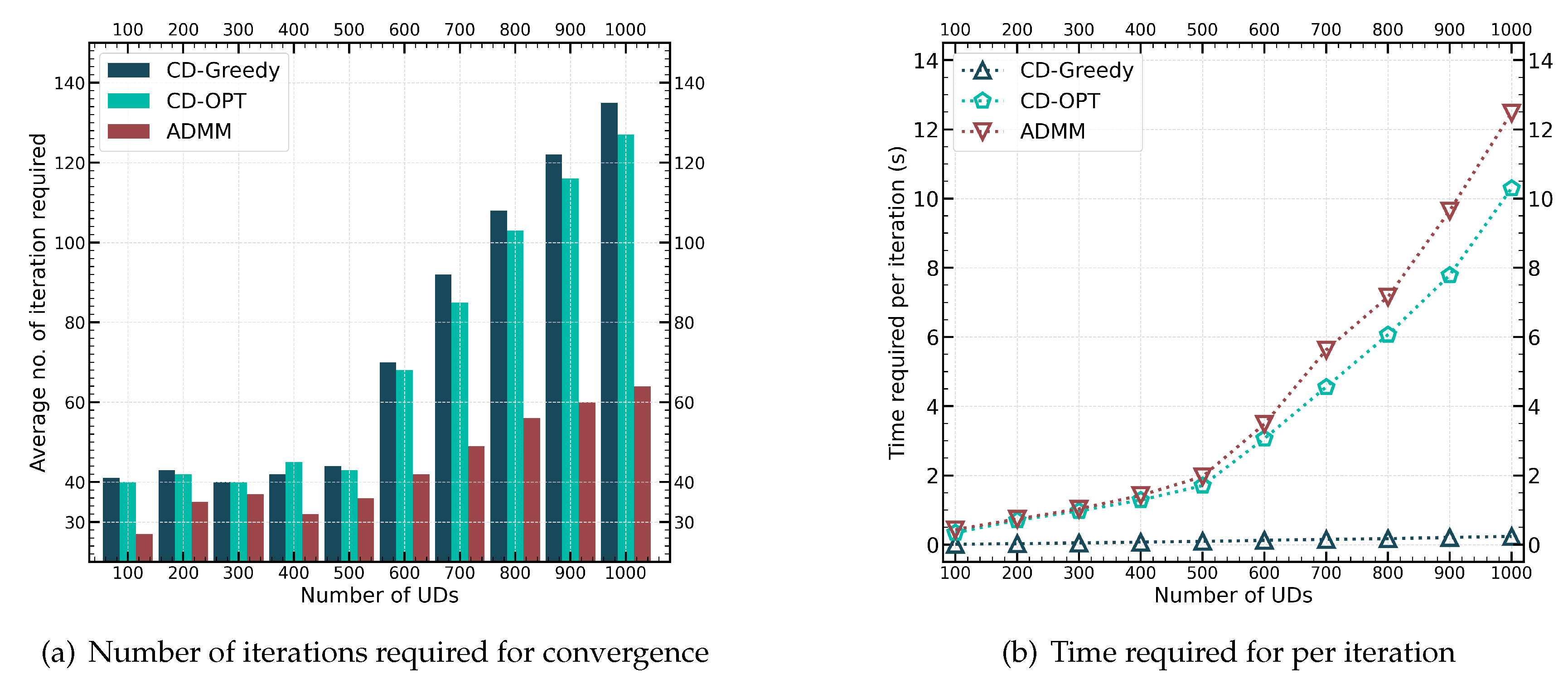
In
Figure 7, we examine the convergence performance of the CD-Greedy, CD-OPT and ADMM methods.
Figure 7a shows the variation of the number of iterations required for convergence of these three algorithms as the number of devices increases from 100 to 1000. When the total number of UDs increases from 100 to 500, the computing capability of the UAV remains constant. However, when the number of UDs increases from 500 to 1000, we adjust the computing performance of the UAV to 10GHz, 20GHz ..., respectively. When the computing resources of the UAV are limited, the number of iterations required for convergence of both methods remains stable, essentially equal to the total number of devices finally offloaded. However, as the computing resources of the UAV increase, more UDs are eventually selected for offloading, leading to a faster increase in the number of iterations required for convergence in CD-Greedy and CD-OPT. In contrast, the increase in iterations for the ADMM method is slower. This highlights the advantage of joint optimization algorithms over alternating optimization algorithms.
Figure 7a shows the trend of the average execution time per iteration of three methods with the increase of network size. It can be seen that the execution time of the convex optimization-based method is more obviously affected by the problem size. However, since ADMM requires fewer iterations to converge, the overall convergence time is shorter compared to CD-OPT. In addition, the CD-Greedy method has significant efficiency advantages in large-scale edge networks, with only millisecond-level execution latency per iteration. This indicates that CD-Greedy and ADMM are suitable for different scenarios with high execution efficiency and higher quality solutions, respectively.
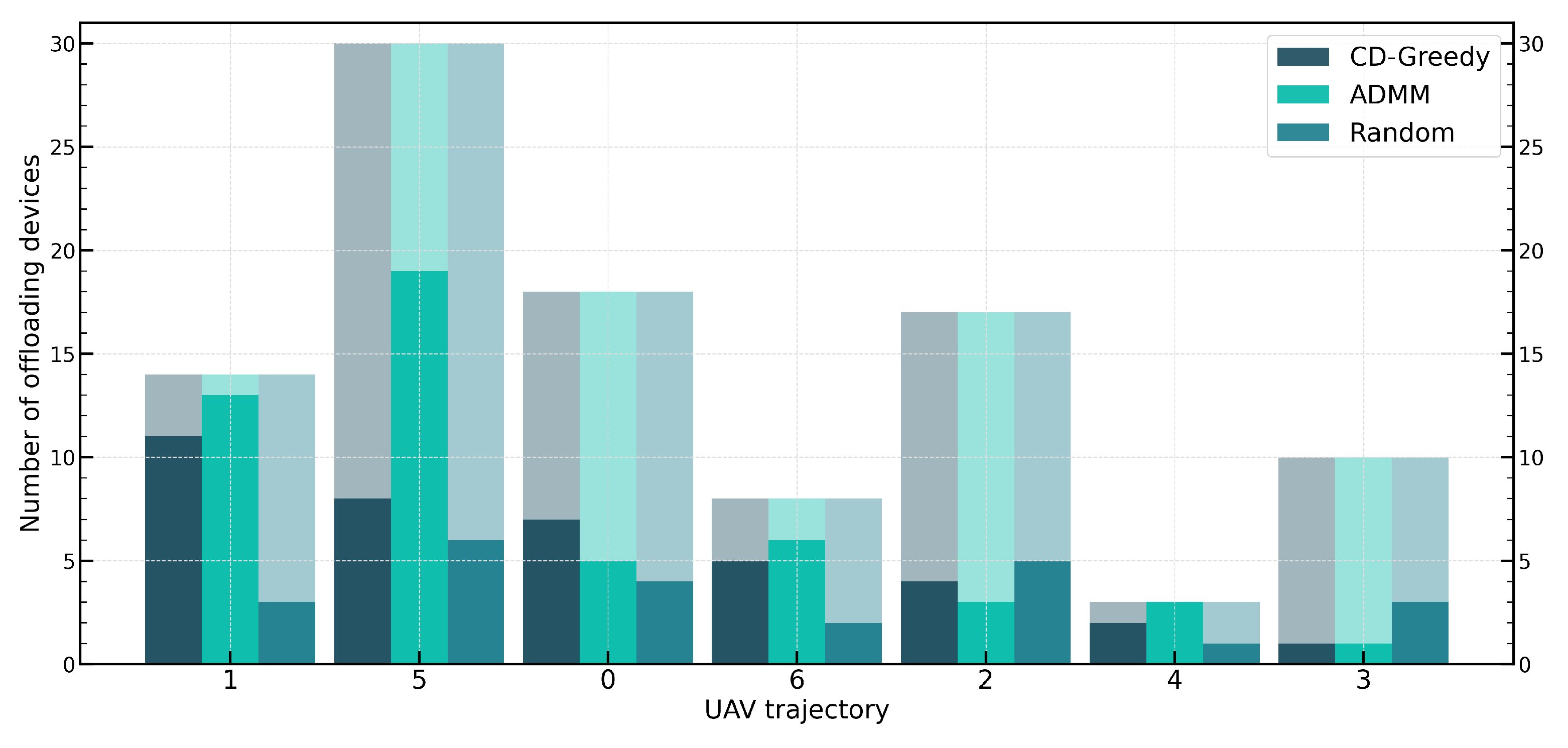
Finally,
Figure 8 illustrates the proportion of UDs offloaded in different coverage areas, with the coverage areas sorted according to the UAV’s trajectory. The results of CD-OPT are similar to those of CD-Greedy, so they are not shown in the figure. From the graph, it can be observed that both CD-Greedy and ADMM tend to select coverage areas near the beginning of the trajectory for offloading. This is because the fixed hovering time ignores the decision of coverage areas’ influence on subsequent areas. Moreover, since coverage areas near the beginning of the trajectory typically have shorter waiting times, offloading more UDs in these areas will result in lower compression ratios. Additionally, due to limited resources in the system, the probability of selecting coverage areas for offloading decreases further when the number of devices selected for offloading reaches a certain threshold. Furthermore, if multiple consecutive service periods are considered, the coverage area at the end of the previous period will become the starting point for the UAV in the next period, thereby achieving relative fairness among multiple coverage areas.
6. Conclusions and Future Work
In this paper, we investigate the minimization of the shrinkage ratio in large-scale UAV-MEC networks. To achieve efficient optimization strategies in large-scale networks, we utilize a partitioning concept combined with a fixed hovering time to decouple interactions between multiple regions, resulting in two low-complexity algorithms. The CD-Greedy algorithm is simple to implement, converges stably, and is widely applicable to various mixed-decision efficient optimization scenarios. The ADMM method, while achieving better optimization results by jointly optimizing integer and continuous variables with fewer iterations, has a longer execution time due to convex optimization, making it suitable for scenarios where high-quality solutions are desired and timeliness is not critical. In our future work, we will focus on enhancing the QoE for dynamic UAV hover times, which presents greater challenges and aligns more closely with real-world scenarios.
Author Contributions
Methodology, X.Y.; Validation, H.H.; Formal analysis, X.Y. and F.H.; Investigation, X.Y. and F.H.; Resources, F.H.; Data curation, X.Y. and H.H; Writing—original draft, X.Y.; Writing—review and editing, H.H. and F.H.; Supervision, H.H and H.S. ; All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported in part by the Science and Technology Foundation of Guangdong Province, China, No. 2021A0101180005. The corresponding author is Huaiwen He.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The main data are included in the article, and detailed numerical experimental data are available on request from the corresponding author.
Acknowledgments
We thank all of the reviewers for their valuable comments.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Feng, C.; Han, P.; Zhang, X.; Yang, B.; Liu, Y.; Guo, L. Computation offloading in mobile edge computing networks: A survey. Journal of Network and Computer Applications 2022, 202, 103366. [Google Scholar] [CrossRef]
- Wang, Z.; Sun, G.; Su, H.; Yu, H.; Lei, B.; Guizani, M. Low-Latency Scheduling Approach for Dependent Tasks in MEC-Enabled 5G Vehicular Networks. IEEE Internet of Things Journal 2024, 11, 6278–6289. [Google Scholar] [CrossRef]
- Xu, J.; Ota, K.; Dong, M. Big Data on the Fly: UAV-Mounted Mobile Edge Computing for Disaster Management. IEEE Transactions on Network Science and Engineering 2020, 7, 2620–2630. [Google Scholar] [CrossRef]
- Nasir, A.A. Latency Optimization of UAV-Enabled MEC System for Virtual Reality Applications Under Rician Fading Channels. IEEE Wireless Communications Letters 2021, 10, 1633–1637. [Google Scholar] [CrossRef]
- Liu, W.; Li, B.; Xie, W.; Dai, Y.; Fei, Z. Energy Efficient Computation Offloading in Aerial Edge Networks With Multi-Agent Cooperation. IEEE Transactions on Wireless Communications 2023. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Miridakis, N.I.; Michalas, A.; Skondras, E.; Vergados, D.J.; Vergados, D.D. Energy Optimization in Massive MIMO UAV-Aided MEC-Enabled Vehicular Networks. IEEE Access 2021, 9, 117388–117403. [Google Scholar] [CrossRef]
- Pervez, F.; Sultana, A.; Yang, C.; Zhao, L. Energy and Latency Efficient Joint Communication and Computation Optimization in a Multi-UAV Assisted MEC Network. IEEE Transactions on Wireless Communications.
- Hua, M.; Wang, Y.; Zhang, Z.; Li, C.; Huang, Y.; Yang, L. Optimal Resource Partitioning and Bit Allocation for UAV-Enabled Mobile Edge Computing. 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), 2018, pp. 1–6.
- Zhao, N.; Ye, Z.; Pei, Y.; Liang, Y.C.; Niyato, D. Multi-Agent Deep Reinforcement Learning for Task Offloading in UAV-Assisted Mobile Edge Computing. IEEE Transactions on Wireless Communications 2022, 21, 6949–6960. [Google Scholar] [CrossRef]
- Xu, Y.; Zhang, T.; Liu, Y.; Yang, D.; Xiao, L.; Tao, M. UAV-Assisted MEC Networks With Aerial and Ground Cooperation. IEEE Transactions on Wireless Communications 2021, 20, 7712–7727. [Google Scholar] [CrossRef]
- Deng, X.; Li, J.; Shi, L.; Wei, Z.; Zhou, X.; Yuan, J. Wireless Powered Mobile Edge Computing: Dynamic Resource Allocation and Throughput Maximization. IEEE Transactions on Mobile Computing 2022, 21, 2271–2288. [Google Scholar] [CrossRef]
- Zhan, C.; Hu, H.; Sui, X.; Liu, Z.; Niyato, D. Completion Time and Energy Optimization in the UAV-Enabled Mobile-Edge Computing System. IEEE Internet of Things Journal 2020, 7, 7808–7822. [Google Scholar] [CrossRef]
- Zhang, L.; Ansari, N. Latency-Aware IoT Service Provisioning in UAV-Aided Mobile-Edge Computing Networks. IEEE Internet of Things Journal 2020, 7, 10573–10580. [Google Scholar] [CrossRef]
- Chen, Z.; Zheng, H.; Zhang, J.; Zheng, X.; Rong, C. Joint computation offloading and deployment optimization in multi-UAV-enabled MEC systems. Peer-to-Peer Networking and Applications 2022, 1–12. [Google Scholar]
- Shen, L. User Experience Oriented Task Computation for UAV-Assisted MEC System. IEEE INFOCOM 2022 - IEEE Conference on Computer Communications, 2022, pp. 1549–1558.
- Liu, W.; Xu, Y.; Wu, D.; Wang, H.; Chu, X.; Xu, Y. QoE-aware Data Aggregation in MEC-enabled UAV Systems: A Matching Game Approach. 2022 IEEE 8th International Conference on Computer and Communications (ICCC), 2022, pp. 725–730.
- Xiang, K.; He, Y. UAV-Assisted MEC System Considering UAV Trajectory and Task Offloading Strategy. ICC 2023 - IEEE International Conference on Communications, 2023, pp. 4677–4682.
- He, Y.; Gan, Y.; Cui, H.; Guizani, M. Fairness-Based 3-D Multi-UAV Trajectory Optimization in Multi-UAV-Assisted MEC System. IEEE Internet of Things Journal 2023, 10, 11383–11395. [Google Scholar] [CrossRef]
- Zhang, S.; Zhang, H.; He, Q.; Bian, K.; Song, L. Joint Trajectory and Power Optimization for UAV Relay Networks. IEEE Communications Letters 2018, 22, 161–164. [Google Scholar] [CrossRef]
- Gao, Y.; Lu, F.; Wang, P.; Lu, W.; Ding, Y.; Cao, J. Resource Optimization of Secure Data Transmission for UAV-Relay Assisted Maritime MEC System. ICC 2023 - IEEE International Conference on Communications, 2023, pp. 3345–3350.
- Jiao, S.; Fang, F.; Zhou, X.; Zhang, H. Joint Beamforming and Phase Shift Design in Downlink UAV Networks with IRS-Assisted NOMA. Journal of Communications and Information Networks 2020, 5, 138–149. [Google Scholar] [CrossRef]
- Wang, F.; Zhang, X. IRS/UAV-Based Edge-Computing and Traffic-Offioading Over 6G THz Mobile Wireless Networks. ICC 2023 - IEEE International Conference on Communications, 2023, pp. 6480–6485.
- Baker Siddiki Abir, M.A.; Zaman Chowdhury, M. Digital Twin-based Aerial Mobile Edge Computing System for Next Generation 6G Networks. 2023 6th International Conference on Electrical Information and Communication Technology (EICT), 2023, pp. 1–5.
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward Edge Intelligence: Multiaccess Edge Computing for 5G and Internet of Things. IEEE Internet of Things Journal 2020, 7, 6722–6747. [Google Scholar] [CrossRef]
- Li, Y.; Li, H.; Xu, G.; Xiang, T.; Lu, R. Practical Privacy-Preserving Federated Learning in Vehicular Fog Computing. IEEE Transactions on Vehicular Technology 2022, 71, 4692–4705. [Google Scholar] [CrossRef]
- Xu, W.; Sun, Y.; Zou, R.; Liang, W.; Xia, Q.; Shan, F.; Wang, T.; Jia, X.; Li, Z. Throughput Maximization of UAV Networks. IEEE/ACM Transactions on Networking 2022, 30, 881–895. [Google Scholar] [CrossRef]
- Tian, S.; Chi, C.; Long, S.; Oh, S.; Li, Z.; Long, J. User preference-based hierarchical offloading for collaborative cloud-edge computing. IEEE Transactions on Services Computing 2021. [Google Scholar] [CrossRef]
- Park, Y.; Nielsen, P.; Moon, I. Unmanned aerial vehicle set covering problem considering fixed-radius coverage constraint. Computers & Operations Research 2020, 119, 104936. [Google Scholar] [CrossRef]
- Alzenad, M.; El-Keyi, A.; Lagum, F.; Yanikomeroglu, H. 3-D Placement of an Unmanned Aerial Vehicle Base Station (UAV-BS) for Energy-Efficient Maximal Coverage. IEEE Wireless Communications Letters 2017, 6, 434–437. [Google Scholar] [CrossRef]
- Du, Y.; Yang, K.; Wang, K.; Zhang, G.; Zhao, Y.; Chen, D. Joint Resources and Workflow Scheduling in UAV-Enabled Wirelessly-Powered MEC for IoT Systems. IEEE Transactions on Vehicular Technology 2019, 68, 10187–10200. [Google Scholar] [CrossRef]
- Ji, J.; Zhu, K.; Niyato, D.; Wang, R. Joint Cache Placement, Flight Trajectory, and Transmission Power Optimization for Multi-UAV Assisted Wireless Networks. IEEE Transactions on Wireless Communications 2020, 19, 5389–5403. [Google Scholar] [CrossRef]
- Dai, B.; Niu, J.; Ren, T.; Hu, Z.; Atiquzzaman, M. Towards Energy-Efficient Scheduling of UAV and Base Station Hybrid Enabled Mobile Edge Computing. IEEE Transactions on Vehicular Technology 2022, 71, 915–930. [Google Scholar] [CrossRef]
- Welzl, E. Smallest enclosing disks (balls and ellipsoids). New Results and New Trends in Computer Science: Graz, Austria, 20–21 June 1991 Proceedings. Springer, 2005, pp. 359–370.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).