1. Introduction
Vector maps are frequently used in many fields, such as navigation, land management, energy development, urban planning and public safety, which lead to an important and unique status for vector maps [
1]. Protecting the privacy and integrity of vector map data is of great significance in promoting the healthy development of the geographic information industry [
2]. Currently, encryption and digital watermarking technologies are the mainstream technical means to effectively protect the security of geographic information [
3]. Encryption technology primarily addresses the issue of confidentiality in the process of information storage and transmission. Plaintext (the original readable information) is converted into ciphertext (the encrypted information) through specific algorithms to prevent unauthorized users from accessing and understanding the information. However, the security of encryption technology relies heavily on the management of the key; if the key is lost or stolen, then the encrypted information will be completely exposed [
4]. Different from encryption technology, digital watermarking technology mainly solves the problems of copyright protection and data traceability. Normally, a specific kind of information (e.g., copyright information, identification, etc.) is embedded into digital media (e.g., images, audio, video, etc.) in an imperceptible way [
5]. In particular, although digital watermarking is designed to be invisible to the human eyes or inaudible to the human ears, in reality, the watermark embedding alters the original data, and this impact needs to be kept within boundaries [
6]. For vector maps, the combination of encryption and digital watermarking technologies is imperative to achieve full lifecycle data protection [
7].
In recent years, algorithms for reversible data hiding in encrypted domain (RDHED) have been proposed [
8,
9,
10,
11,
12], in which the plaintext data are first encrypted and then the additional information is embedded in the encrypted data. RDHED is suitable for scenarios where the data embedder is an unauthorized user and has no access to the original data. In RDHED, the original data can be recovered after additional data extraction, and this make RDHED very suitable for vector maps which have high requirements for data accuracy. However, existing RDHED mainly focus on raster images, and few RDHED algorithms for vector maps have been proposed. Peng et al [
13] proposed an RDHED algorithm for 2D vector graphics based on a real-number reversible mapping model, which strikes a good balance between watermark invisibility, capacity and security. However, the watermark extraction can only be carried out in the ciphertext domain for this algorithm, while in practical applications watermark extraction in both ciphertext and plaintext domains are often required. Subsequently, Peng et al [
14] proposed another RDHED algorithm for 2D vector graphics, which realizes watermark extraction in both ciphertext and plaintext domains and suits more application scenarios. Although not specially designed for vector maps, these algorithms have reference significance for encrypting and watermarking vector maps. Jang et al [
15] proposed a crypto-marking technique for vector maps, which watermarks the map data at first and then encrypts the data using progressive perceptual encryption method. The watermarking and the progressive perceptual encryption are independent of each other. However, the fixed order of first marking and then encrypting in this method limits its application scenarios.
In the algorithms mentioned above, the order of encryption and watermarking is fixed, which is not flexible enough for practical applications. In order to realize flexible interchangeable operations between watermarking and encryption, some scholars further proposed commutative encryption and watermarking (CEW) schemes. These schemes can be categorized into three types according to the mechanism employed to achieve commutativity: separate domains based CEW, homomorphic encryption based CEW, and feature invariant based CEW.
Separate domains based CEW schemes achieve the commutativity by performing encryption and watermarking operations in two different domains. Jiang et al [
16] proposed a CEW scheme based on orthogonal decomposition. The component coefficients of the orthogonal decomposition are independent of each other, while the composite vector is sensitive to any changes in the component coefficients. The 2D image can be orthogonally decomposed into two domains based on this property for encryption and watermarking respectively. This algorithm has no special requirements for encryption and watermarking, so it has high universality. But some plaintext information is exposed in this kind of schemes, leading to security problems.
Homomorphic encryption based CEW schemes achieve the commutativity by taking advantage of homomorphism. Lian [
17] proposed a quasi-commutative watermarking scheme based on a homomorphic encryption method with an additive mechanism to encrypt the video as a whole, which can realize simple homomorphic watermarking operation but lacks robustness. For vector maps, Wu et al [
18] encrypted quantized integer coordinates based on paillier homomorphic encryption and embedded the watermark by homomorphic operations in the ciphertext domain. Although homomorphic encryption algorithms can provide excellent security for the data, they suffer from the defects of computational complexity and low efficiency.
Feature invariant based CEW schemes fulfill the commutativity by embedding watermark information into a certain feature space which keeps unchanged during encryption or decryption process. Compared with the multimedia data such as images, vector maps have various spatial features, which make it more convenient to discover and construct some special invariants to realize the commutativity between encryption and watermarking. For example, Ren et al [
19] constructed two feature invariants based on the sum of inner angles and the storage direction of two adjacent objects according to the inherent characteristics of vector map, and designed a CEW scheme based on these two feature invariants. But the watermark capacity of this algorithm is only half of the number of objects in a vector map. Li et al [
20] proposed a new CEW algorithm for vector maps based on coordinate values which serve as feature invariants. Note that the above two algorithms are only applicable to polyline and polygon objects, unsuitable to point data. To achieve higher watermarking capacity, Ren et al [
21] further proposed a vector map CEW method based on congruence relationship and geometric feature, in which the angles and the distance ratios are selected as the geometric features, and the watermark is embedded into the residuals of the congruence operations performed on the geometric features. The watermark capacity of this algorithm achieves 2 bits per vertex. For the improvement of robustness, Ren [
22] went on to propose a CEW method for vector data based on singular value decomposition(SVD), in which the singular values are selected as the feature invariants.
In literature, a few CEW schemes for vector maps have been proposed. However, most existing CEW algorithms focus on the watermark robustness. Few focus on the reversibility and suit the application scenarios that have high requirements for data accuracy. In this regard, Guo et al [
23] proposed a lossless CEW algorithm for vector data, in which no data distortion is introduced after watermarking. But the watermark capacity is small. Tan et al [
24] proposed a CEW algorithm based on zero watermarking and permutation encryption, and can be applied to high-precision vector maps. However, the algorithm is only applicable to vector maps represented by polylines and polygons and cannot be applied to points.
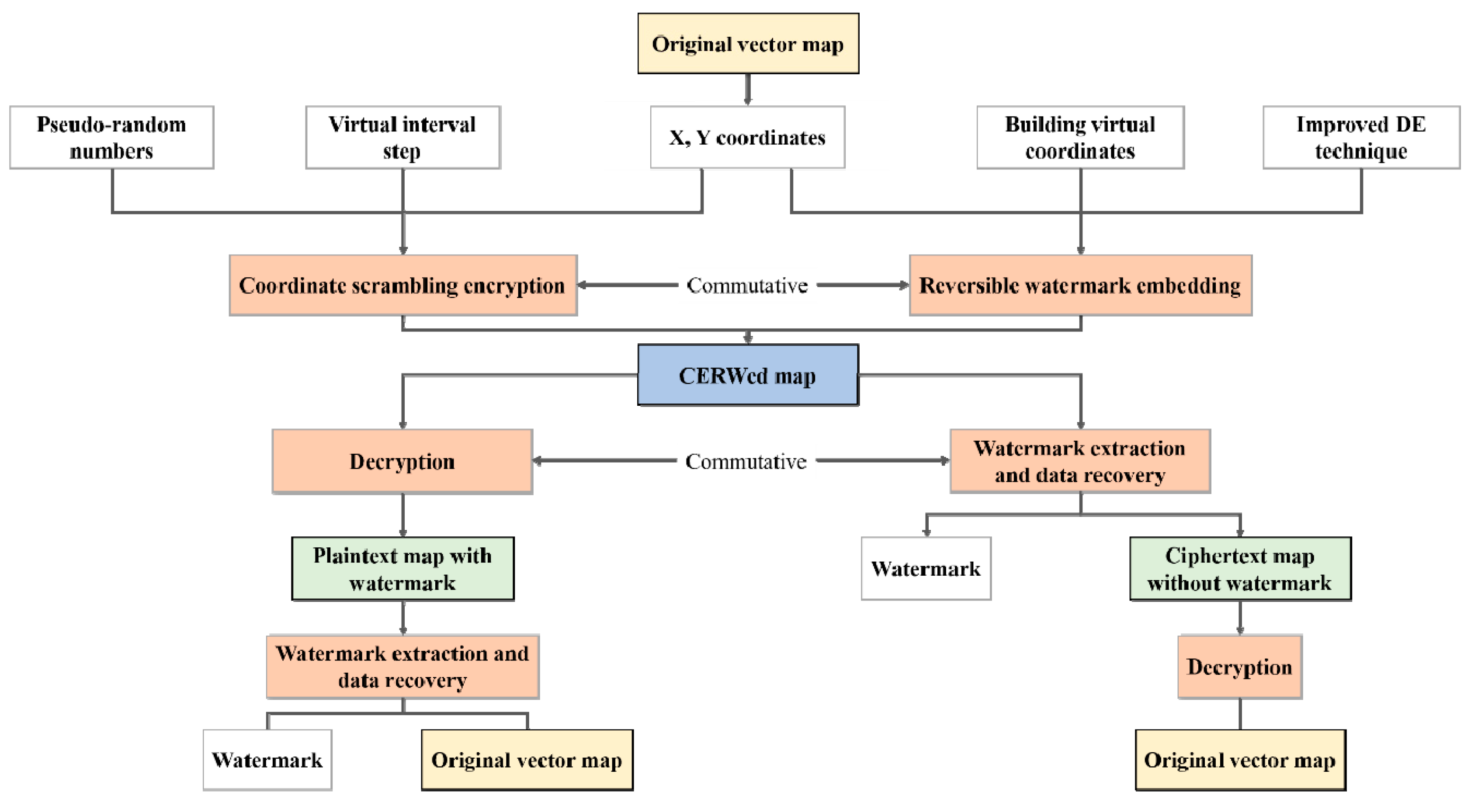
Different from the schemes mentioned above, this paper proposes a novel commutative encryption and reversible watermarking (CERW) method for vector maps, in which not only the commutativity between encryption and watermarking is achieved, but also the reversibility of watermarking is achieved. It means that the original ciphertext map without watermark can be recovered from the ciphertext map with watermark and the original plaintext map without watermark can be recovered from the plaintext map with watermark. The proposed CERW scheme is constructed based on virtual coordinates which uniformly distribute on the number axis. The commutativity between encryption and watermarking is achieved by using feature invariant which is defined as the relative position of a map coordinate in a virtual interval formed by two adjacent virtual coordinates. In the encryption part, the map coordinates are moved by random multiples of the virtual interval step. In the reversible watermarking part, the watermark bit is embedded into the difference computed based on the map coordinate’s relative position in a virtual interval using difference expansion (DE) technique. By introducing virtual coordinates, the proposed CERW scheme can achieve higher watermark capacity and better watermark invisibility than traditional DE watermarking algorithms. Furthermore, the proposed CERW scheme suits all kinds of vector maps, including point maps, such as POI map.
The remainder of this paper is organized as follows.
Section 2 introduces some preliminaries involved in this paper, including the pseudo-random number generation method, difference expansion (DE) technique and principle of cosine-transform-based chaotic system (CTBCS).
Section 3 describes the proposed algorithm in detail.
Section 4 discusses the key parameters involved in the algorithm.
Section 5 verifies the effectiveness and analyzes the performance of the proposed algorithm by implementing a series of experiments. Finally,
Section 6 summarizes and outlooks the full work.
2. Preliminary
2.1. Pseudo-Random Numbers Generation Based on Hash Function and Streaming Cryptograph-y Algorithm
In cryptography, pseudo-random numbers are usually utilized to increase the unpredictability and security of the encryption process [
25]. Hash function is a method that converts an input (information) of arbitrary length to an output of fixed length. In watermarking algorithms, hash function is usually chosen for data integrity checking, password storage and random number generation [
26]. The common ones are MD5 (Message Digest Algorithm 5), SHA-1 (Secure Hash Algorithm) and SHA-2. SHA-256, SHA-384 and SHA-512 are algorithms subdivided under SHA-2. Among them, SHA-512 runs and processes data faster and is more secure than SHA-256 and SHA-384.
Stream cipher is a cryptographic method that generates a stream of ciphertext by performing an exclusive-or operation between a plaintext stream and a key stream, and can be used to provide high-quality, high-entropy pseudo-random number sequence with good statistical properties and randomness. Salsa 20 algorithm can realize fast encryption, which is a stream cipher algorithm with high security [
27].
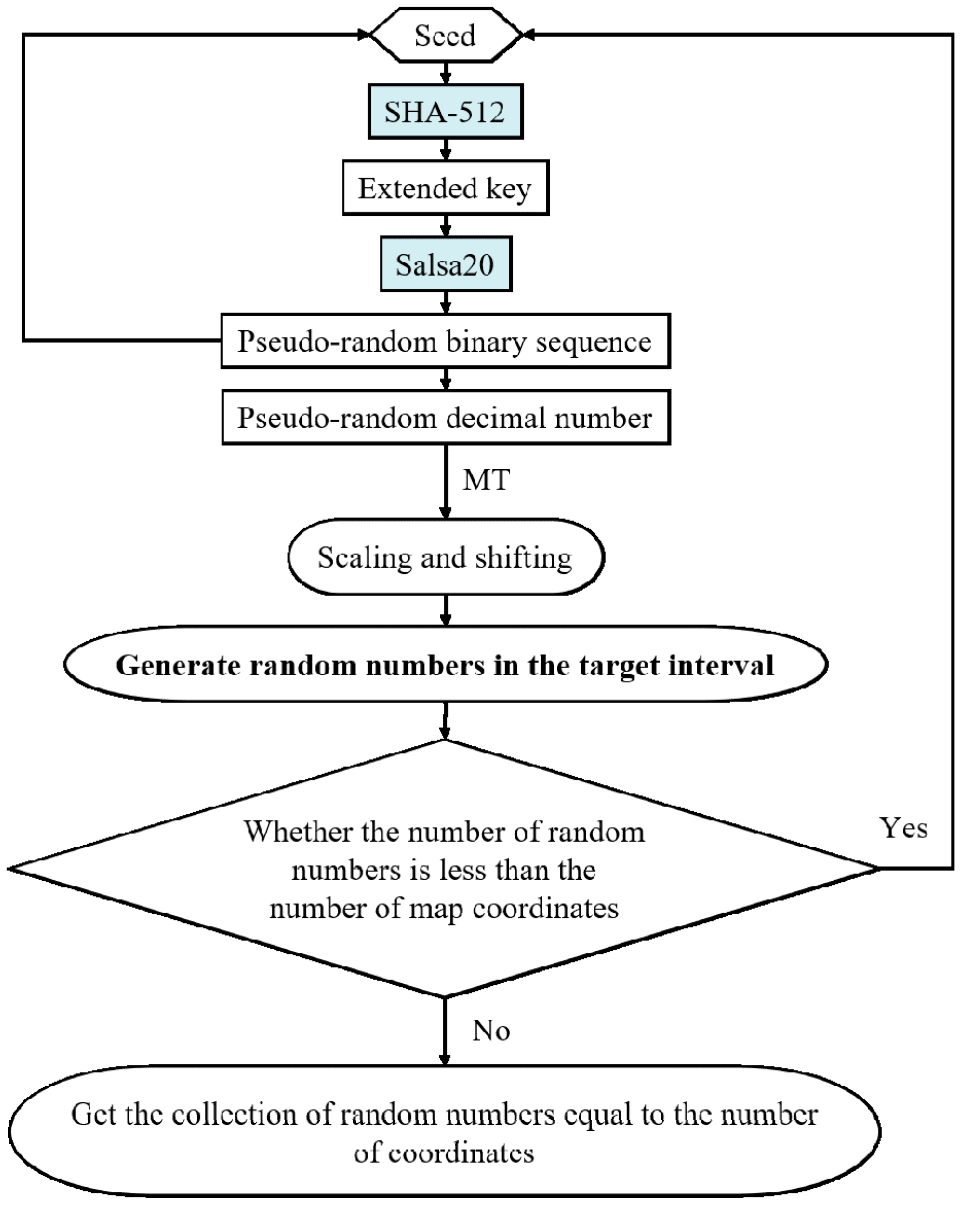
We choose SHA-512 and Salsa20 and design a SHA-512-Salsa20 generator to generate secure and reliable pseudo-random numbers. Specific steps are as follows:
Step 1: A seed is selected as the initial value input, and then the seed is input into SHA-512 to obtain the output of SHA-512 as the extended key. This extended key will be used as the key for the stream cipher.
Step 2: The Salsa20 algorithm is initialized using the extended key.
Step 3: Use the Salsa20 algorithm to generate a pseudo-random binary sequence,and then convert the sequence to a decimal number.
Step 4: Input the pseudo-random binary sequence generated in the previous step as a new seed into SHA-512 and obtain the output of SHA-512 as a new extended key. This step is to increase the randomness and enhance the security.
Step 5: In conjunction with the Mersenne Twister (MT) algorithm, the pseudo-random number generated in Step 3 is scaled and shifted using Eq. (1) in order to generate a random number within the target interval.
A pseudo-random number will be generated as a result of each run of the stream cipher algorithm. denotes the minimum value of the generated pseudo-random numbers and denotes the maximum value of the generated pseudo-random numbers. Here, , , , d are all integers, is the generated pseudo-random number in the interval [, ], is the downward rounding function, is a function that generates random numbers based on the Mersenne Twister and is a pseudo-random number generated by formula (1) that maps real values in the interval [, ] to the interval [, ] by scaling and shifting.
Step 6: Loop through Step 1 to 5 until a sufficient number of random numbers are obtained.
Figure 1.
Flowchart of the pseudo-random number generation
Figure 1.
Flowchart of the pseudo-random number generation
2.2. Difference Expansion (DE) Technique
Difference Expansion (DE) technique was earlier designed for and applied in raster image reversible watermarking, where pairs of pixel values are used to calculate the difference values, and the reversibility of the scheme is achieved by embedding the watermark bits through difference expansion [
28]. Considering the low correlation and redundancy between vertices for vector data, Peng et al [29,30] explored and improved the difference expansion technique based on Wang [
31], which embedded the watermark into the ratio set of the relative coordinates of all vertices of a 2D CAD engineering drawing to improve the watermarking capacity and imperceptibility. But the watermarking data integrity is destroyed if the watermark is extracted by referring to the vertices in reverse order. Subsequent algorithms based on histogram shifting, prediction error expansion, least significant bit substitution (LSB), and wavelet transform combined with difference expansion were devoted to improve the watermark capacity and visual quality.
DE is a reversible watermarking technique. The principle of watermark embedding is to calculate the difference for each pair of neighboring elements, and provide the watermark embedding space by expanding the difference to twice the original value. The smaller the difference value, the less the watermark embedding disturbs the data. Therefore, limiting the difference value to a small range can realize very small graphic distortion after watermark embedding. The fundamentals of the traditional DE technique are described in detail below.
During the watermark embedding stage, firstly, given a pair of neighboring elements of highly correlated carrier data
, an integer transformation is defined to compute their difference
and integer mean
according to Equation (2). Then, a watermark bit
is embedded into the difference
according to Equation (3). Finally, the carrier data with embedded watermark
can be obtained from Equation (4).
For watermark extraction, firstly, the difference
and the integer mean
of the watermarked elements need to be computed according to Equation (5). Then, the original difference
is recovered and the watermark
is extracted by Equation (6). Finally, the original pair of elements
is constructed based on Equation (7).
2.3. Cosine Transform-Based Chaotic System (CTBCS)
Chaotic systems are widely used in the fields of information hiding and cryptography due to their unpredictability and initial value sensitivity. CTBCS [
32] with two chaotic mappings as seed mappings is a composite chaotic system with lower computational complexity compared to high dimensional chaos, and more secure and reliable compared to low dimensional chaos. Therefore, CTBCS can be used for chaotic dislocation during watermark information generation to further enhance the security of the algorithm. Here, we use the existing Logistic mapping and Tent mapping as the seed mapping, which can be mathematically defined as:
Here, the variable is the control parameter of the Logistic mapping and the Tent mapping, .
CTBCS can be mathematically expressed as:
where
and
are two known chaotic mappings as seed mappings,
and
are the parameters of the seed mappings, and
is the transformation constant (in this paper, we set
=
0.5). Set parameter
=
and parameter
= 1
.
is the key parameter of the generated chaotic mapping.
6. Conclusion
In this paper, a CERW algorithm for vector maps is proposed based on virtual coordinates. In the proposed coordinates scrambling encryption scheme, the coordinates are moved by random multiples of the virtual interval step. The random number is generated by a pseudo-random number generator designed using the hash function SHA-512 and the Salsa20 stream cipher algorithm. In the proposed reversible watermarking scheme, the coordinate differences are first calculated with virtual coordinates as references and then the DE technique is utilized to embed watermark reversibly. Because the coordinates scrambling encryption has no impact on the coordinate differences in which the watermark is embedded, the commutativity between encryption operation and reversible watermarking operation is achieved. The operation order of encryption and watermark embedding doesn’t change the final results, and the watermark extraction and data recovery can be performed before or after decryption. The main contributions of this paper are as follows:
(1) Although there are a few existing CEW algorithms for vector maps, the original map can’t be recovered from the watermarked version in these algorithms, which makes the algorithms unsuitable for applications that require high data precision. The proposed CERW algorithm not only achieves the commutativity between encryption and watermarking, but also achieves the watermark reversibility, which makes the proposed algorithm suitable for more kinds of applications than the existing CEW algorithms.
(2) Traditional DE watermarking algorithm often has small watermark capacity and big data distortions when used in vector map watermarking. Especially, the watermarking operation often fails because of the too large data distortions introduced by watermarking when used to watermark a map with sparse vertex distribution. The watermarking performance of traditional DE algorithm is affected significantly by map characteristics. The improved DE (IDE) watermarking algorithm proposed in this paper overcomes the above-mentioned problems of traditional algorithms by introducing virtual coordinates as references in the coordinate difference calculation, and significantly improves the watermark capacity, which is more than 7 times higher than that of the traditional DE methods. Meanwhile, by adjusting the virtual interval step, the proposed IDE algorithm can achieve very small data distortions after watermarking. Furthermore, the watermarking performance of the proposed IDE method is not affected by map characteristics and very stable for different kinds of maps.
(3) The encryption method of the proposed CERW scheme designs a SHA-512-Salsa20 random number generator to implement coordinates scrambling, and achieves good encryption effect and high encryption security as analyzed in section 5.4. It is worth noting that the SHA-512-Salsa20 generator can be replaced with any arbitrary existing pseudo-random number generation method in the proposed encryption scheme.
Proposed algorithm has a relatively poor performance in watermark robustness. The map translation operation has no impact on the coordinate differences, thus proposed algorithm can resist the map translation attack. However, the map scaling and rotation operations will change the coordinate differences, so the proposed algorithm can’t resist the map scaling and rotation attacks. Therefore, improving the robustness of the proposed CERW scheme will be the future work of this research.
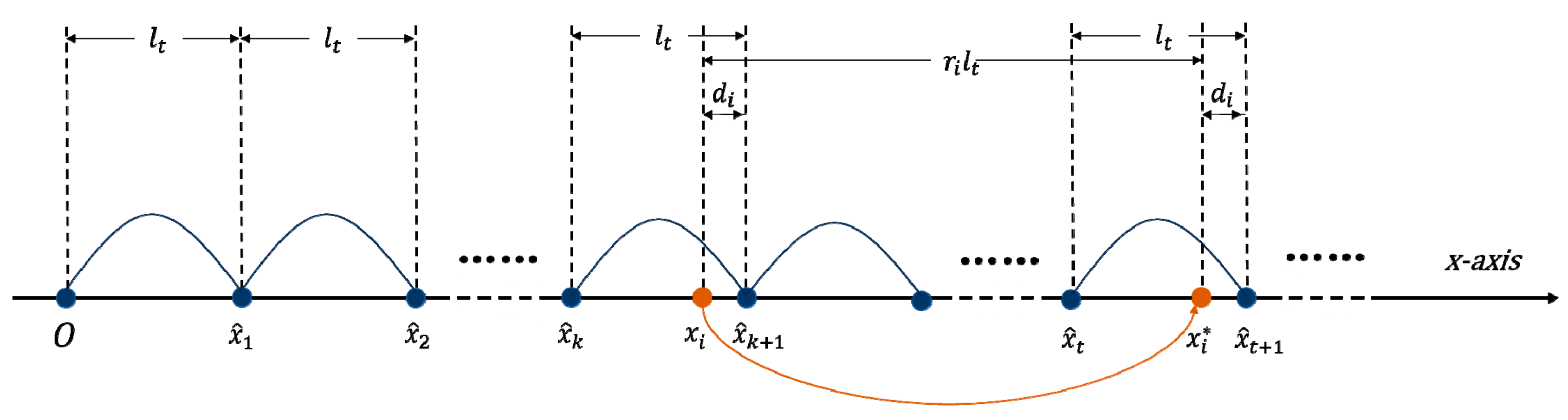
Figure 3.
Schematic diagram of the difference construction and coordinate scrambling based on virtual coordinates
Figure 3.
Schematic diagram of the difference construction and coordinate scrambling based on virtual coordinates
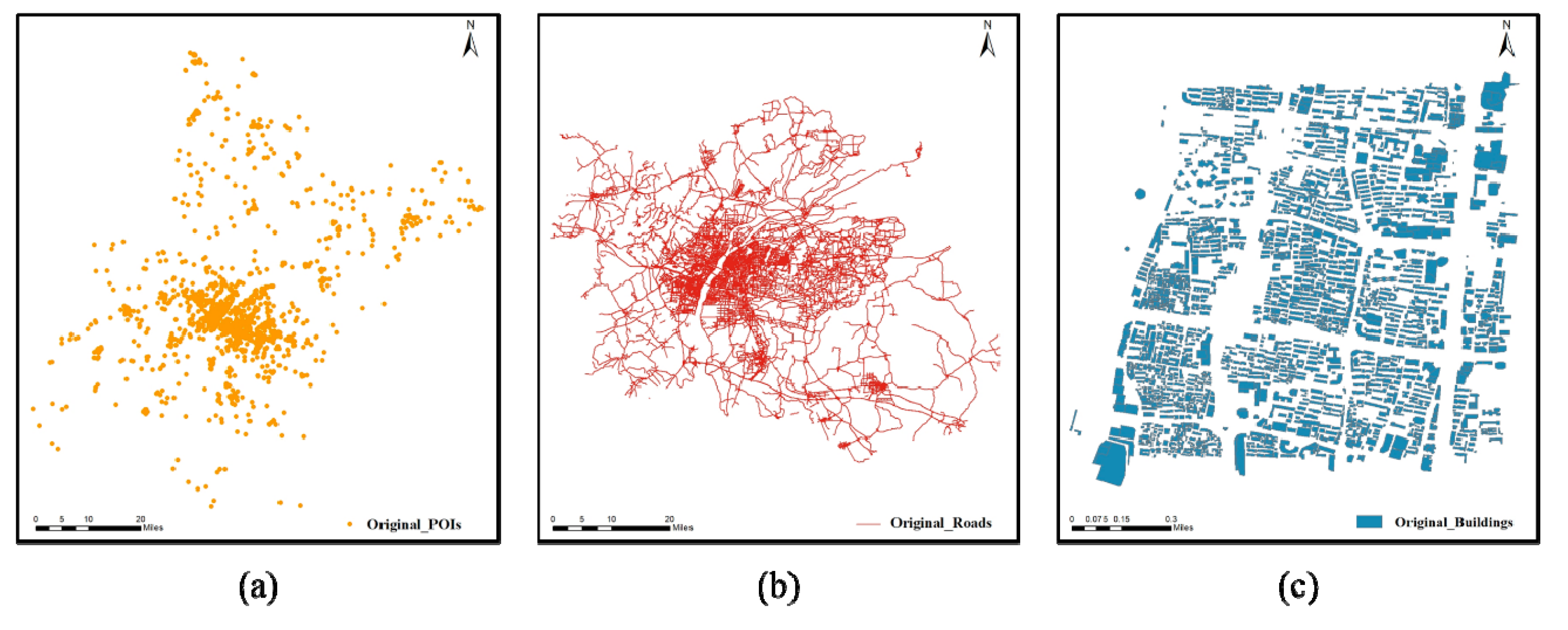
Figure 4.
Original experimental data: (a) POIs, (b) Roads, (c) Buildings
Figure 4.
Original experimental data: (a) POIs, (b) Roads, (c) Buildings
Figure 5.
The visualization of CERWed maps: (a) E-Wed POIs; (b) E-Wed roads; (c) E-Wed buildings; (d) W-Eed POIs; (e) W-Eed roads; (f) W-Eed buildings
Figure 5.
The visualization of CERWed maps: (a) E-Wed POIs; (b) E-Wed roads; (c) E-Wed buildings; (d) W-Eed POIs; (e) W-Eed roads; (f) W-Eed buildings
Figure 6.
The visualization of the recovered plaintext maps: (a) R-Ded POIs; (b) R-Ded roads; (c) R-Ded buildings; (d)D-Red POIs; (e) D-Red roads; (f)D-Red buildings
Figure 6.
The visualization of the recovered plaintext maps: (a) R-Ded POIs; (b) R-Ded roads; (c) R-Ded buildings; (d)D-Red POIs; (e) D-Red roads; (f)D-Red buildings
Figure 7.
Visualization of the encryption and decryption results: (a) Encrypted POIs; (b) Encrypted roads; (c) Encrypted buildings; (d) Decrypted POIs; (e) Decrypted roads; (f) Decrypted buildings
Figure 7.
Visualization of the encryption and decryption results: (a) Encrypted POIs; (b) Encrypted roads; (c) Encrypted buildings; (d) Decrypted POIs; (e) Decrypted roads; (f) Decrypted buildings
Figure 8.
The encrypted maps using slightly different keys and decrypted maps using slightly modified key: (a) encrypted POIs using Key 1 and Key 2; (b) encrypted roads using Key 1 and Key 2; (c) encrypted buildings using Key 1 and Key 2; (d) the result of using Key 1 to decrypt the POIs encrypted with Key 2; (e) the result of using Key 1 to decrypt the roads encrypted with Key 2; (f) the result of using Key 1 to decrypt the buildings encrypted with Key 2
Figure 8.
The encrypted maps using slightly different keys and decrypted maps using slightly modified key: (a) encrypted POIs using Key 1 and Key 2; (b) encrypted roads using Key 1 and Key 2; (c) encrypted buildings using Key 1 and Key 2; (d) the result of using Key 1 to decrypt the POIs encrypted with Key 2; (e) the result of using Key 1 to decrypt the roads encrypted with Key 2; (f) the result of using Key 1 to decrypt the buildings encrypted with Key 2
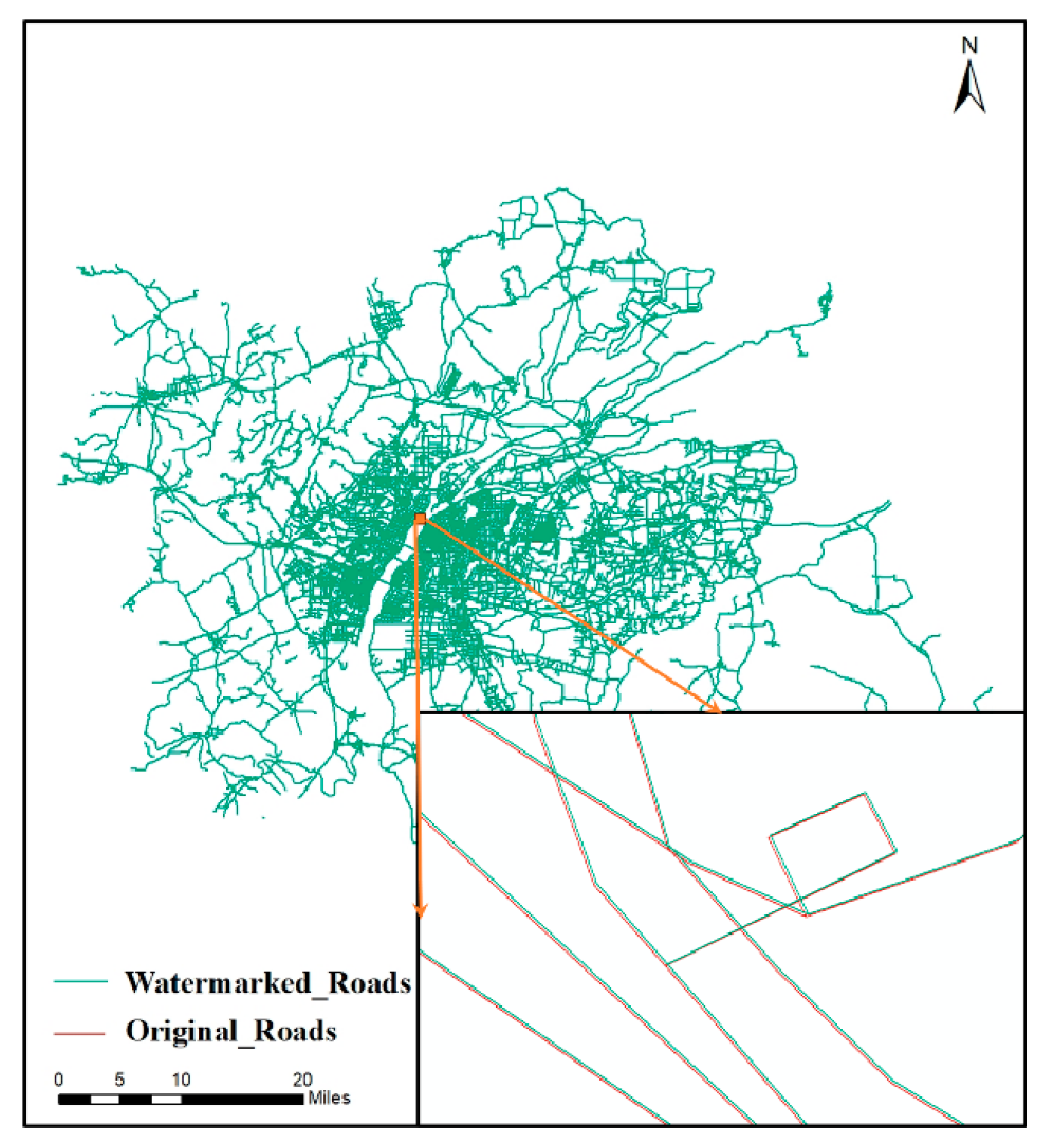
Figure 9.
Overlay of watermarked data and original data (Roads)
Figure 9.
Overlay of watermarked data and original data (Roads)
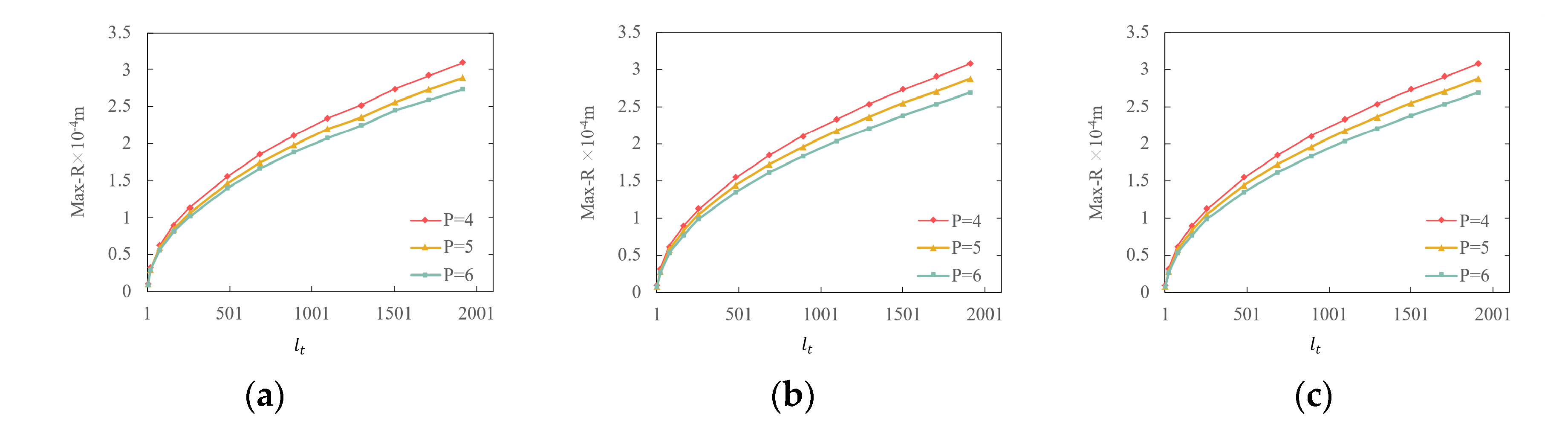
Figure 10.
Max-R versus interval step : (a) POIs; (b) Roads; (c) Buildings
Figure 10.
Max-R versus interval step : (a) POIs; (b) Roads; (c) Buildings
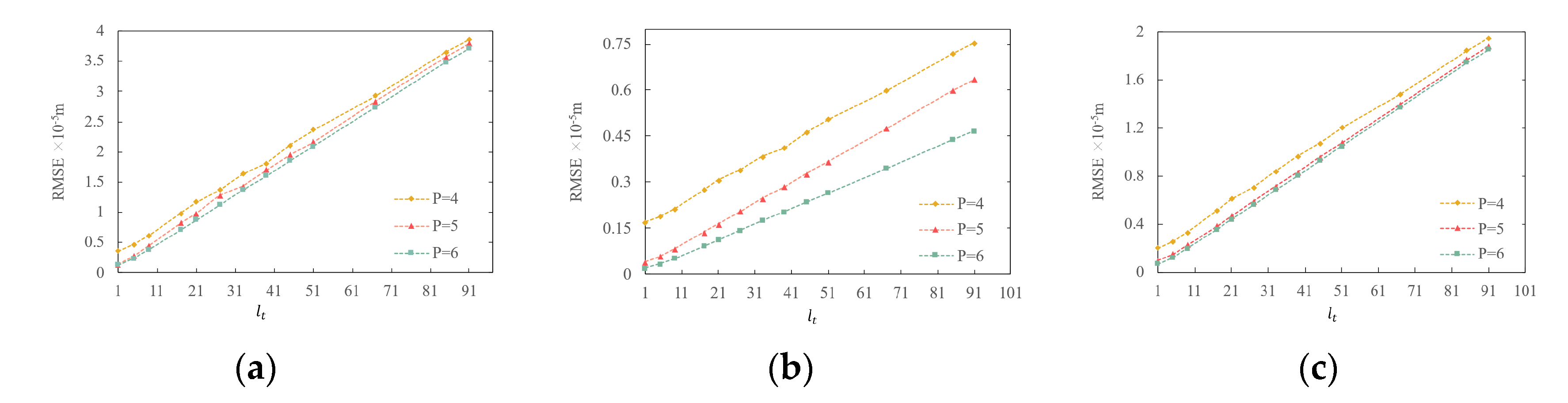
Figure 11.
RMSE versus interval step : (a) POIs; (b) Roads; (c) Buildings
Figure 11.
RMSE versus interval step : (a) POIs; (b) Roads; (c) Buildings
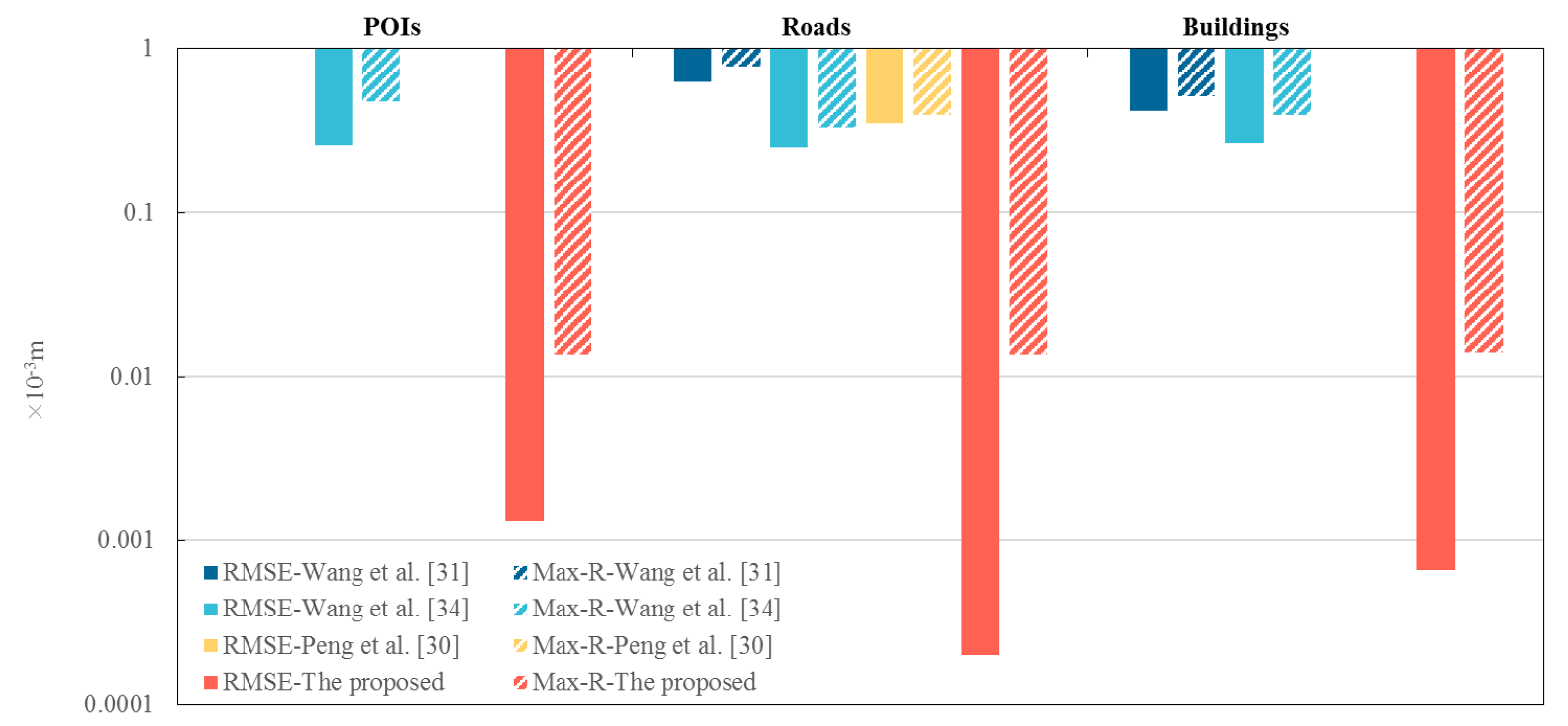
Figure 12.
Comparison of the RMSE and Max-R of different reversible algorithms
Figure 12.
Comparison of the RMSE and Max-R of different reversible algorithms
Table 1.
The detailed information of the experimental data.
Table 1.
The detailed information of the experimental data.
| Maps |
Data types |
Features |
Vertices number |
Scale |
(m) |
| POIs |
Point |
2410 |
2410 |
1:10000 |
1 |
| Roads |
Polyline |
11423 |
122962 |
1:10000 |
1 |
| Buildings |
Polygon |
5660 |
20325 |
1:1000 |
0.1 |
Table 2.
Comparison results between the E-Wed maps and the W-Eed maps
Table 2.
Comparison results between the E-Wed maps and the W-Eed maps
| Datasets |
Consistent vertices count |
Inconsistent vertices count |
RMSE |
| E-Wed and W-Eed POIs |
2410 |
0 |
0 |
| E-Wed and W-Eed roads |
122962 |
0 |
0 |
| E-Wed and W-Eed buildings |
20325 |
0 |
0 |
Table 3.
Comparison results between the R-Ded maps and the D-Red maps
Table 3.
Comparison results between the R-Ded maps and the D-Red maps
| Datasets |
Consistent vertices count |
Inconsistent vertices count |
RMSE |
| R-Ded and D-Red POIs |
2410 |
0 |
0 |
| R-Ded and D-Red roads |
122962 |
0 |
0 |
| R-Ded and D-Red buildings |
20325 |
0 |
0 |
Table 4.
BER results of the extracted watermarks
Table 4.
BER results of the extracted watermarks
| Datasets |
Extraction from
E-Wed maps |
Extraction from
W-Eed maps |
Extraction from
D-Wed maps |
| POIs |
0 |
0 |
0 |
| Roads |
0 |
0 |
0 |
| Buildings |
0 |
0 |
0 |
Table 5.
RMSE values of the encrypted and decrypted maps
Table 5.
RMSE values of the encrypted and decrypted maps
| Datasets |
RMSE between encrypted map and original map (m) |
RMSE between decrypted map and original map (m) |
| POIs |
448973.8688 |
0 |
| Roads |
48368.7397 |
0 |
| Buildings |
15216.4770 |
0 |
Table 6.
Difference between encryption results of Key 1 and Key 2
Table 6.
Difference between encryption results of Key 1 and Key 2
| Datasets |
RMSE(m) |
Max-R(m) |
| POIs |
4322.2641 |
15318.6846 |
| Roads |
615.6829 |
2711.3073 |
| Buildings |
437.2614 |
1757.5051 |
Table 7.
Comparison of watermark capacity in different algorithms (bits/vertex)
Table 7.
Comparison of watermark capacity in different algorithms (bits/vertex)
| Datasets |
Wang et al. [31] |
Wang et al. [34] |
Peng et al. [30] |
The proposed |
| POIs |
- |
1.9887 |
- |
2 |
| Roads |
0.2790 |
1.9761 |
1.9761 |
2 |
| Buildings |
0.1480 |
1.9568 |
- |
2 |
Table 8.
RMSE and Max-R values of different algorithms (=6) (10-3m)
Table 8.
RMSE and Max-R values of different algorithms (=6) (10-3m)
| Datasets |
|
Wang et al. [31] |
Wang et al. [34] |
Peng et al. [30] |
The proposed |
| POIs |
RMSE |
- |
0.25920 |
- |
0.00131 |
| |
Max-R |
- |
0.47274 |
- |
0.01367 |
| Roads |
RMSE |
0.62505 |
0.25107 |
0.34937 |
0.00020 |
| |
Max-R |
0.78143 |
0.33009 |
0.39582 |
0.01373 |
| Buildings |
RMSE |
0.41708 |
0.26517 |
- |
0.00066 |
| |
Max-R |
0.50781 |
0.39302 |
- |
0.01395 |
Table 9.
Comparison of reversibility of different algorithms (P = 6) (m)
Table 9.
Comparison of reversibility of different algorithms (P = 6) (m)
|
Datasets
|
|
Wang et al. [31] |
Wang et al. [34] |
Peng et al. [30] |
The proposed |
| E-Red map D-Red map |
| POIs |
RMSE |
- |
|
- |
0 |
0 |
| |
Max-R |
- |
|
- |
0 |
0 |
| Roads |
RMSE |
0 |
|
|
0 |
0 |
| |
Max-R |
0 |
|
|
0 |
0 |
| Buildings |
RMSE |
0 |
|
- |
0 |
0 |
| |
Max-R |
0 |
|
- |
0 |
0 |