In this section, the term Grid refers specifically to a two-dimensional Grid. Here, the optimum broadcast time and an optimum scheme under models and are calculated when 0 is the originator. Since , these results provide a bound for model.
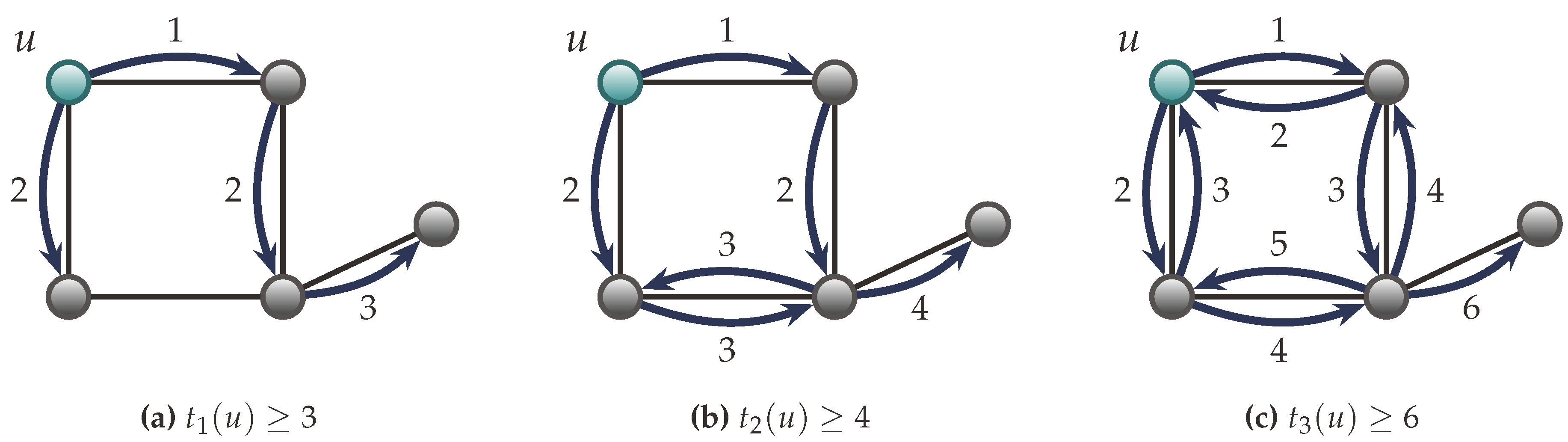
Similar to Remark 2, it is naturally assumed that in any scheme, each informed vertex will inform all of its uninformed neighbors in consecutive time units.
3.2.2. Model
The presence of borders makes the problem much more complex than the analysis in subsection 3.1. It is worth noting that in this section, the use of the word “border” is similar but different from that in Definition 9. Here, in addition to a saturated coordinate (Definition 8), a 0 coordinate is also considered to define a k-border aligning with the usual intuition. Unlike in an infinite Grid, the maximum possible delay any k-border vertex could cause is smaller than that of -border vertices, where .
This section provides the optimum broadcast time and an optimum broadcast scheme for a two-dimensional Grid for some integers and . By symmetry, without the loss of generality, assume .
Intuitively, since the interior vertices may cause more delays, it is implied that there is an optimum broadcast scheme where, for any vertex v, the path that first informs v creeps through the borders first until it branches out in a straight line to reach v. Based on this intuition, Border-creeping paths are defined, which will be the cornerstone of our analysis.
Definition 11 (Border-creeping paths). Inspired by the above motivation, for a vertex v, consider the following four border-creeping paths: -path, -path, -path, and -path. For example, -path starts at 0, creeps the border downward until it reaches the bottom border, then goes right on the bottom border until it reaches the horizontal position of v, and finally, it goes up (not necessarily on any border) until v is reached. The last change of direction is the only part of these paths that may not be on any border.
Other border-creeping paths, such as the -path, are not considered since they are slower than another defined border-creeping path, which in this case would be the -path.
The first move. Which direction should the originator 0 send the message first? Our intuition tells us that the shorter dimension (n, the vertical) should be informed first. The reason is as follows: As discussed, the bottleneck for delaying is the borders; therefore, the optimum scheme should delay informing them as much as possible. If the message is sent through the shorter dimension first, while it is true that the shorter border will be informed sooner, it is also true that it delays the progression of information toward the longer dimension (to the right) with the help of interior vertices and the fact that the bottom border already has significant enough delay. Based on this intuition, assume that the first move is downward along the shorter dimension. Later, we will prove that this is an optimum choice.
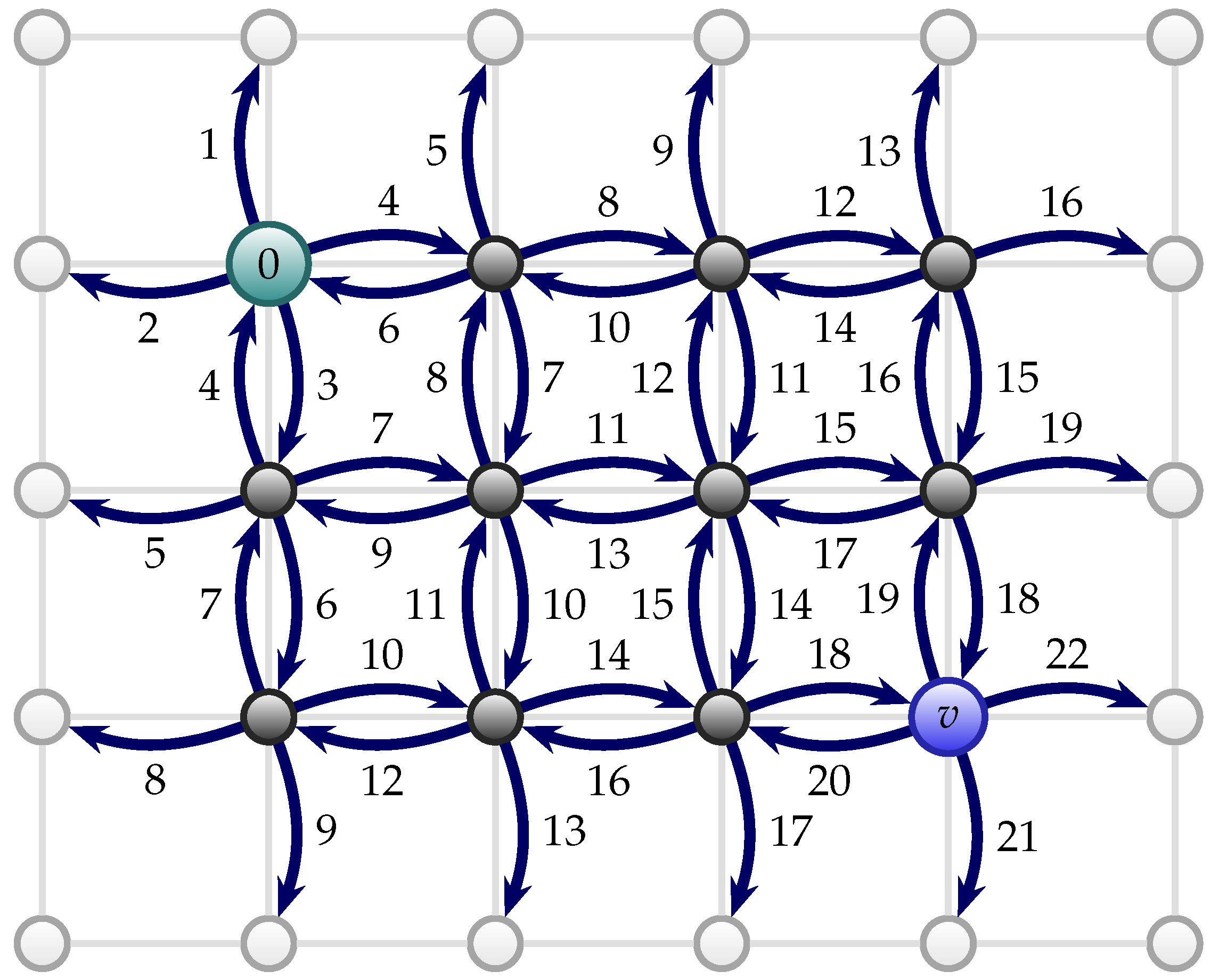
Based on the first move assumption, it is easy to see that for an interior vertex
the maximum time it takes each border-creeping path to reach
v is:
For example, let us investigate the
-path. The 1 is the maximum time it will take to reach the vertex one down of 0 (originator), the
to reach the bottom border, the 2 for changing the direction at the corner vertex and going one to the right, the
to reach the horizontal position of
v, the 3 to change the direction upward and going one up, the
to go up and reach
v. See such portion of the scheme in
Figure 4. These values give an easy upper bound to
for interior vertices.
Lemma 2 (Upper-bound, Interior vertices).
Let be an interior vertex, then
Similar upper bound can be given to border vertices as well; here, however, it is clear which border-creeping path has the minimum time.
Lemma 3 (Upper-bound, Border vertices).
Let be a border vertex, then
Comparison between the maximum time of each two border-creeping paths,
and
, separates the vertices into two groups: the vertices whose
maximum time is less than equal to that of
, and the rest. The boundary is a line; let us denote it with
. The equations associated with each of these six lines are as follows.
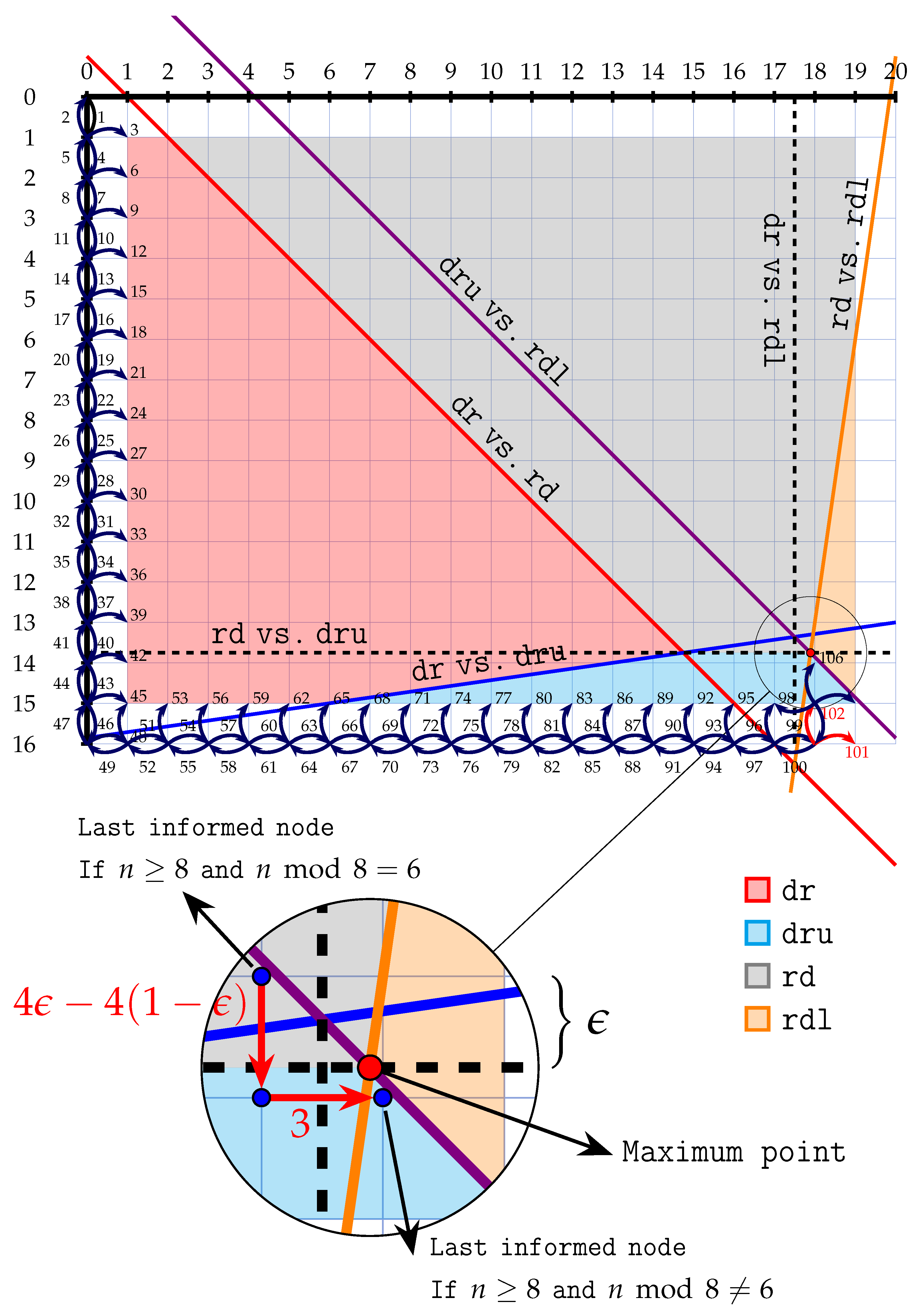
Figure 4 shows an example and also explains how to detect the regions where a particular path has the minimum. For better visualization of these regions and for the analysis to come, it is helpful to note the common intersections of some of these lines,as outlined in Lemma 4.
Lemma 4 (Common intersections). Each of the following four groups of three lines has a common intersection.
-
1.
-
2.
-
3.
-
4.
Proof. The common point for group 1 is , for group 2 is , for group 3 is , and for group 4 is . □
Having established an upper bound, our next step is determining a lower bound by devising an appropriate scheme. For a given scheme S, let be the time for S to inform v for the first time. By definition, for all schemes S. For any vertex v, let be the type of border-creeping path which achieves the upper-bound based on Lemma 2 and Lemma 3.
In any scheme S, if , the behavior of S throughout the -path is uniquely determined. This is because only one behavior causes the vertices of -path to delay the information to v for this duration, and any other behavior will inform v sooner. With this understanding, we investigate whether there exists a scheme S such that for any vertex v, . If such a scheme exists, it would be an optimum scheme. Unfortunately, for large enough n and m, such scheme a cannot exist. This is because the final branch-out behavior is explicitly tailored to the target vertex v. If vertex v and u share the common segment of their border-creeping paths, this will result in conflicting behavior. For example, consider a Grid with and . In this case, . The -path for shares the -path for until vertex . The requirements of the described unique behavior for vertex differ depending on which of these two vertices is being considered. Therefore, such a scheme S cannot exist. However, if we relax the behavioral requirements for this final branching, we can devise a scheme we call the border-evading scheme.
Border-evading scheme. This scheme behaves as follows: For any border vertex v, the behavior of the path informing v is dictated by the -path informing v in time-units. For any interior vertex v, consider the unique behavioral requirement to achieve as described above. At the point of final branching, the requirement is to first send the message to the previous sender on the border, then to the next vertex on the border, and lastly toward v when branching out. We ease this behavior so that, at this point, the message is first sent to the previous sender on the border, then toward v, and finally to the next vertex on the border. In this way, this path conveys the information to v in time-units. It is as if the new behavior aims to evade informing the rest of the border as much as possible, hence the name border-evading scheme.
It is easy to verify that this description for each vertex v has no conflict with the description for another vertex u, which was the case before. In the border-evading scheme, for all interior vertices, the time of all four associated border-creeping paths is reduced by precisely one-time unit compared to their maximum. Accordingly, the separating lines and regions associated with the earliest reaching border-creeping paths (detected before) remain the same.
Thus far it is deduced that for border vertices
and for interior vertices
. Let
B be the set of border vertices, then since
we have
Let
with a preference to be an interior vertex. In this way, if
, then for any interior vertex
v,
; consequently,
and border-evading scheme is an optimum scheme. Otherwise, if
, if we can modify the border-evading scheme in such a way that
in the new scheme is informed at time-unit
then the new scheme will be an optimum scheme, and
. To do that, first, let us find
.
Continuous view. The previously identified regions of the Grid are associated with the type of border-creeping path that reaches those areas the fastest. In the border-evading scheme, consider an edge
. If
is entirely within one region, the time it takes from the first moment
v is inform to the first moment
u is infomed is a constant based on the associated border-creeping path. For example, in the region associated with
, a move to the right has +4 change while in
has +3 and in
has -4. One can change the view from discrete movements (e.g., going up by one unit) to a continuous one. In this view, define the gradient of each point within a region based on the aforementioned uniform changes; in case a point belongs to multiple regions, choose one randomly. The vector field is conservative since it can be viewed as the gradient of a function composed of unions of linear equations. To know the first informed time of a vertex
v, consider a point
p at the coordinate of
v. For any continuous path from 0 to
v (due to path independence), the line integral over the vector field is the answer. This time can be associated with any other point in the Grid. As an example, take a look at
Figure 4, under the magnifying glass. As indicated, the change in the first informed time of the two vertical blue dots is
.
Using the continuous view and Lemma 4, by investigating the vector field, it is not hard to see that a point with maximum time is the intersection of , , and lines; . This is true even for the case , the only case in which comes before . Important note: There are two latent assumptions. The placement of was determined by investigating the vector field and not by directly investigating the line integrals. Take , for example. Its equation was derived from . The latent assumption in the value of is that v’s vertical position is not n, which comes from the +2 applied for changing the direction upward. Consequently, if or are true, the above position might be problematic, and additional checks are required. The first restriction is false if and only if , and the second is false if and only if .
For , based on the vector fields, the choice for will be limited to three possible vertices in the vicinity of ;
See
Figure 4 under the magnifying glass. The red point is
, and the possible three vertices have blue points. To understand which has the higher first informed time, the changes from
to
and then from
to
will be calculated. Let
.
By the slope of the lines, it is deduced that vertices
and
are in the
region (cyan color in
Figure 4), and vertex
in
region (gray). Note that if
, then
is in the boundary of the
and
regions; in this case, we consider the
region. As depicted in
Figure 4, this positioning implies that the change from
to
is
and from
to
is
. Consequently, vertex
is the sole last informed vertex except when (1)
, where
is also the last informed; (2)
, where
is the sole last informed vertex.
On the other hand, if , the inequality is true, which means the latent assumption for the provided is violated. In this case, by using the vector field it is not hard to see that a choice for is coordinate .
Optimum scheme, changing the border-evading scheme. Now that a possible candidates for
(and its time) is determined, we can describe a new similar scheme that will be completed in
and hence is an optimum scheme. If
, no change is necessary. Otherwise, (1) if
, change the behavior at
so that at that point there is no evading of the border as described before; see
Figure 4 for the modification in red. In this way, the
-path time to
is increased by one, and since
-path was the only path that could inform the fastest, the desired scheme is achieved. (2) If
, in this case,
resides (only) in the
region; therefore, with a similar justification modify the behavior of
. Adjust the timing of the vertices whose border-evading path relied on this point, and a new valid scheme is achieved.
First move revisited. At first, it was assumed that the first move is downward, through the smaller dimension. A similar analysis can be made if the first move is toward the right. It can be seen that the new will be informed sooner. Consequently, sending through the smaller dimension as the first move is an optimum choice.
To summarize all the findings:
Theorem 3 (Two-dimensional Grid, Messy model
).
Consider a two-dimensional Grid , where . With 0 as the originator, under the Messy model ,
Moreover, an optimum scheme similar to theborder-evading scheme
is known, in which the sole last informed vertex is
Corollary 1.
Consider a two-dimensional Grid , where . Under the Messy model , for
Proof. By the definitions of the floor and ceiling functions,
and
are obtained. Using the second case for the upper bound and the third case for the lower bound, it is deduced that
□