Submitted:
01 July 2024
Posted:
01 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
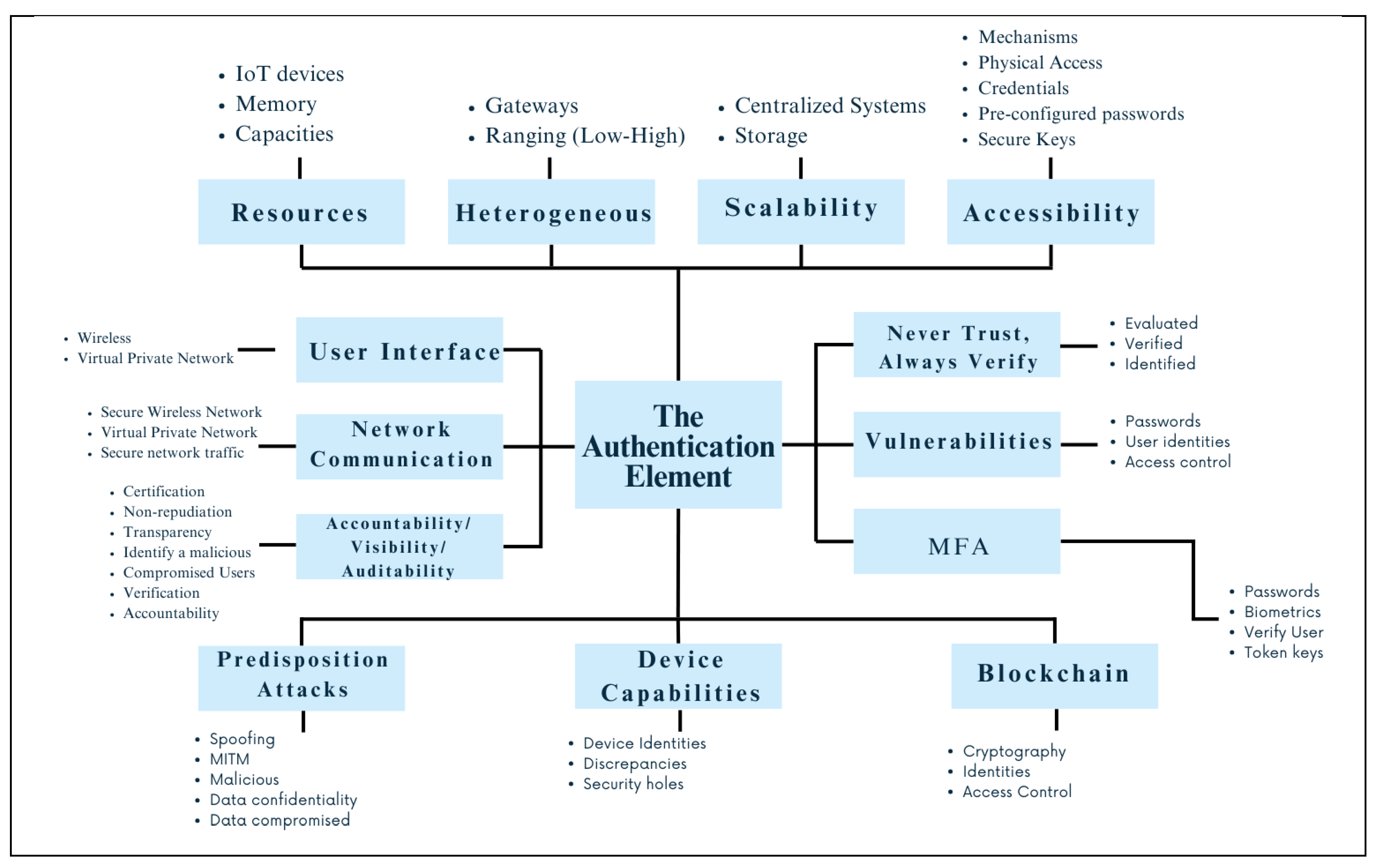
2. Emerging Authentication Technologies for Zero Trust on the IoT
- 1)
- Every data source and computing service is regarded as a corporate asset that requires protection.
- 2)
- All communications are considered insecure, regardless of the network location specified in the access request. No entity seeking access is automatically trusted.
- 3)
- Resource access is granted on a session-by-session basis.
- 4)
- Device characteristics, along with behavioral and environmental factors, are considered in access decisions.
- 5)
- The principle of least privilege is applied.
- 6)
- Access is granted intermittently, not automatically.
- 7)
- Enhancements to security in communications, network infrastructure, and assets are continuously applied.
3. The Performance Evaluation Criteria for Authentication Zero Trust in the IoT
4. Future Direction and Suggestions
5. Conclusion
References
- Dhar, Suparna; Indranil Bose. Securing IoT Devices Using Zero Trust and Blockchain. Journal of Organizational Computing and Electronic Commerce 2020, 31(1), p. 18-34.
- Kummar, Puneet; Satis Jumar; Wasik Iqbal; Apurva Goyal. Emerging Technology and Management Trends. Gautam Vihar Delhi, Manglam, India, 2023, p. 98-124.
- Chen, Z.; Jiang, Y.; Song, X.; Chen, L. A Survey on Zero-Knowledge Authentication for Internet of Things. Electronics 2023, 12, 1145. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A Survey on Zero Trust Architecture: Challenges and Future Trends. Wirel. Commun. Mob. Comput. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Soewito, B.; Marcellinus, Y. IoT security system with modified Zero Knowledge Proof algorithm for authentication. Egypt. Informatics J. 2020, 22, 269–276. [Google Scholar] [CrossRef]
- Patel, Rajesh; Klaus Muller; Giorgi Kvirkvelia; John Smith; Emily Wilson. Zero Trust Security Architecture Raises the Future Paradigm in Information Systems. Informatica and Digital Insight 2024, 1(1), p. 24-34.
- Ahmadi, S. Zero Trust Architecture in Cloud Networks: Application, Challenges and Future Opportunities. J. Eng. Res. Rep. 2024, 26, 215–228. [Google Scholar] [CrossRef]
- Buck, C.; Olenberger, C.; Schweizer, A.; Völter, F.; Eymann, T. Never trust, always verify: A multivocal literature review on current knowledge and research gaps of zero-trust. Comput. Secur. 2021, 110, 102436. [Google Scholar] [CrossRef]
- Shah, S.W.; Syed, N.F.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. LCDA: Lightweight Continuous Device-to-Device Authentication for a Zero Trust Architecture (ZTA). Comput. Secur. 2021, 108, 102351. [Google Scholar] [CrossRef]
- Dhiman, P.; Saini, N.; Gulzar, Y.; Turaev, S.; Kaur, A.; Nisa, K.U.; Hamid, Y. A Review and Comparative Analysis of Relevant Approaches of Zero Trust Network Model. Sensors 2024, 24, 1328. [Google Scholar] [CrossRef] [PubMed]
- Federici, F.; Martintoni, D.; Senni, V. A Zero-Trust Architecture for Remote Access in Industrial IoT Infrastructures. Electronics 2023, 12, 566. [Google Scholar] [CrossRef]
- Nita, S.L.; Mihailescu, M.I. A Novel Authentication Scheme Based on Verifiable Credentials Using Digital Identity in the Context of Web 3.0. Electronics 2024, 13, 1137. [Google Scholar] [CrossRef]
- Alquwayzani, Alanoud Abdullah; Abdullah Abdulrahman Albuali. A systematic Literature Review of Zero Trust Architecture for UAV Security Systems in IoBT. Computer Scient and Mathematics 2024, 1(1), p. 1-33.
- Hasan, M.K.; Weichen, Z.; Safie, N.; Ahmed, F.R.A.; Ghazal, T.M. A Survey on Key Agreement and Authentication Protocol for Internet of Things Application. IEEE Access 2024, 12, 61642–61666. [Google Scholar] [CrossRef]
- Zanasi, C.; Russo, S.; Colajanni, M. Flexible zero trust architecture for the cybersecurity of industrial IoT infrastructures. Ad Hoc Networks 2024, 156. [Google Scholar] [CrossRef]
- Syed, Naeem Firdous; Syed W. Shah; Arash Shaghaghi; Adnan Anwar; Zubair Baig; Robin Doss. Zero Trust Architecture (ZTA): A Comprehensive Survey. IEEE Access 2022, 10, 57143–57179.
- Elsayed, Zag; Nelly Elasyed; Sajjad Bay. A Novel Zero Trust Machine Learning Green Architecture for Healthcare IoT Cybersecurity: Review. Analysis and Implementation in Southeast Conference 2024, Atlanta, GA, USA, (May 18 - May 22, 2024).
- Butpheng, C.; Butpheng, C.; Yeh, K.-H.; Yeh, K.-H.; Hou, J.-L.; Hou, J.-L. A Secure IoT and Cloud Computing-Enabled e-Health Management System. Secur. Commun. Networks 2022, 2022, 1–14. [Google Scholar] [CrossRef]
- Saravanan, K.; Anitha, P. Kamarajapandian; Thomas Paul Roy Arockiadoss; K. Sambath Kumar; R. Hariharan. Design and Elevating Cloud Security Through a Comprehensive Integration of Zero Trust Framework. Intelligent systems and application in engineering 2024, 12, 214–219. [Google Scholar]
- Nawshin, F.; Unal, D.; Hammoudeh, M.; Suganthan, P.N. AI-powered malware detection with Differential Privacy for zero trust security in Internet of Things networks. Ad Hoc Networks 2024, 161. [Google Scholar] [CrossRef]
- Neale, Christopher; Ian Kennedy; Blaine Price; Yijun Yu; Bashar Nuseibeh. The case for Zero Trust Digital Forensics. Forensic Science International: Digital Investigation 2022, 40, 1–13.
- Liu, C.; Tan, R.; Wu, Y.; Feng, Y.; Jin, Z.; Zhang, F.; Liu, Y.; Liu, Q. Dissecting zero trust: research landscape and its implementation in IoT. Cybersecurity 2024, 7, 1–28. [Google Scholar] [CrossRef]
- Raheman, F. From Standard Policy-Based Zero Trust to Absolute Zero Trust (AZT): A Quantum Leap to Q-Day Security. J. Comput. Commun. 2024, 12, 252–282. [Google Scholar] [CrossRef]
- Cena, Joshua. Multi-Factor Authentication Paradigms for Securing Industrial Internet of Things (IIoT) Assets, in Electrical Energy and Power Systems Group (EEPS), Doctoral Degree, 2024, The University of Manchester: Manchester, Lancashire, United Kingdom. p. 12.
- Rivera, J.J.D.; Muhammad, A.; Song, W.-C. Securing Digital Identity in the Zero Trust Architecture: A Blockchain Approach to Privacy-Focused Multi-Factor Authentication. IEEE Open J. Commun. Soc. 2024, 5, 2792–2814. [Google Scholar] [CrossRef]
- Nandy, Tarak; Mohd Yamani Idna Bin Idris; Rafidah Md Noor; Laiha Mat Kiah; Lau Sian Lun; Nor Badrul Annuar Juma’at; Ismail Ahmedy; Norjihan Abdul Ghani; Sananda Bhattacharyya. Review on Security of Internet of Things Authentication Mechanism. IEEE Access 2019, 7, 151054–151089.
- Kawalkar, Sachin A.; Dinesh B. Bhoyar. Design of an Efficient Cloud Security Model through Federated Learning, Blockchain, AI-Driven Policies, and Zero Trust Frameworks. Intelligent systems and application in engineering 2023, 12(10), p. 378-388.
- Walshe, M.; Epiphaniou, G.; Al-Khateeb, H.; Hammoudeh, M.; Katos, V.; Dehghantanha, A. Non-interactive zero knowledge proofs for the authentication of IoT devices in reduced connectivity environments. Ad Hoc Networks 2019, 95, 101988. [Google Scholar] [CrossRef]
- Ali, Belal Ebrahim Mohamed Alshiec. Efficient Trust-Aware Authentication and Task Offloading in Multi-Access Edge Computing Using a Dual Fuzzy Method based Zero Trust Security Framework, Doctoral Degree, College of Science, Technology, Engineering and Maths. 2023, Royal Melbourne Institute of Technology: Royal Melbourne Institute of Technology, Australia.
- Yeoh, W.; Liu, M.; Shore, M.; Jiang, F. Zero trust cybersecurity: Critical success factors and A maturity assessment framework. Comput. Secur. 2023, 133. [Google Scholar] [CrossRef]
- Singhal, Nikita; Deepak Tyagi. Cybersecurity in the Era of Emerging Technology, in Emerging Technology and Management Trends, P. Kumar, et al., Editors. 2023, Manglam: K-129, Gali Pusta, Shiv Om Jewellers, Gautam Vihar Delhi, India, p. 98-124.
- Kim, H.; Lee, E.A. Authentication and Authorization for the Internet of Things. It Prof. 2017, 19, 27–33. [Google Scholar] [CrossRef]
- Capili, Mirene. Simulation-Based Evaluation of Perimeter-Based and Zero Trust Security Implementation on Internet of Things, in Systems Engineering. Doctoral Degree, 2024, The George Washington University: The school of Engineering and Applied Science of The George Washington University, p. 1-24.
- Cambou, B.; Philabaum, C.; Hoffstein, J.; Herlihy, M. Methods to Encrypt and Authenticate Digital Files in Distributed Networks and Zero-Trust Environments. Axioms 2023, 12, 531. [Google Scholar] [CrossRef]
- Mehraj, Saima; M. Tariq Banday. Establishing a Zero Trust Strategy in Cloud Computing Environment, International Conference on Computer Communication and Informatics (ICCCI-2020), University of Exeter: Coimbatore, India, 22-24 January 2020, p. 1-6.
- Zhang, H.; Zhang, Z.; Chen, L. Toward zero trust in 5G industrial internet collaboration systems. Digit. Commun. Networks 2024. [Google Scholar] [CrossRef]
- Olaoye, Godwin Oluwafemi; Ayuns Luz. Future trends and emerging technologies in cloud security,Telecommunication Engineering Centre. Doctoral Degree, 2024, Ladoke Akintola University of Technology: Ladoke Akintola University of Technology, India. p. 1-24.
- Cena, Joshua. Zero trust Architecture for Robust IIoT Security, in Electrical Energy and Power Systems Group (EEPS). Doctoreal Degree, 2024, The University of Manchester: The University of Manchester.
- Adhikari, Tapomoy. Advancing Zero Trust Network Authentication: Innovations in Privacy-Preserving Authentication Mechanisms. Computer Science and Engineering 2024, 1(1), p. 1-22.
- Chuan, T.; Lv, Y.; Qi, Z.; Xie, L.; Guo, W. An Implementation Method of Zero-trust Architecture. J. Physics: Conf. Ser. 2020, 1651, 012010. [Google Scholar] [CrossRef]
- Bhattacharya, S.; Panyam, S.; Deshmukh, G.; Gatala, S.; Vemoori, V.; Seth, D. Integrating User Experience and Acceptance in Authentication: A Synthesis of Technology Acceptance Model and User-Centered Design Principles. Int. J. Comput. Trends Technol. 2024, 72, 15–23. [Google Scholar] [CrossRef]
- Aki, Sai Ranga Subhash. Zero Trust Securityin Wireless and communication Networks. Computer Security and Reliability 2024, 1(1), p. 1-24.
- Tang, F.; Ma, C.; Cheng, K. Privacy-preserving authentication scheme based on zero trust architecture. Digit. Commun. Networks 2023. [Google Scholar] [CrossRef]
- Xu, M.; Guo, J.; Yuan, H.; Yang, X. Zero-Trust Security Authentication Based on SPA and Endogenous Security Architecture. Electronics 2023, 12, 782. [Google Scholar] [CrossRef]
- Chen, Chien-Ming; Xuanang Li; Shuangshuang Liu; Mu-En Wu; Saru Kumari; Youwen Zhu. Enhanced Authentication Protocol for the Internet of Things Environment. Security and Communication Networks 2022, 2022, p. 1–13.
- Kang, H.; Liu, G.; Wang, Q.; Meng, L.; Liu, J. Theory and Application of Zero Trust Security: A Brief Survey. Entropy 2023, 25, 1595. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.J. Zero trust architecture: Redefining network security paradigms in the digital age. World J. Adv. Res. Rev. 2023, 19, 105–116. [Google Scholar] [CrossRef]
- Chen, Xu; Wei Feng; Ning Ge; Yan Zhang. Zero_Trust_Architecture_for_6G_Security. IEEE Network 2023, 1(1), p. 1-8.
- Wu, K.; Cheng, R.; Xu, H.; Tong, J. Design and Implementation of the Zero Trust Model in the Power Internet of Things. Int. Trans. Electr. Energy Syst. 2023, 2023, 1–13. [Google Scholar] [CrossRef]
- Su, R.; Riahi, A.; Natalizio, E.; Moyal, P.; Saint-Jore, A.; Song, Y.-Q. Assessing intra- and inter-community trustworthiness in IoT: A role-based attack-resilient dynamic trust management model. Internet Things 2024, 26. [Google Scholar] [CrossRef]
- Azad, Muhammad Ajmal; Sidrah Abdullah; Junaid Arshad; Harjinder Lallie; Yussuf Hassan Ahmed. Verify and trust: A multidimensional survey of zero trust security in the age of IoT. Internet of Things 2024, 27, 1–27.
- Itodo, C.; Ozer, M. Multivocal literature review on zero-trust security implementation. Comput. Secur. 2024, 141. [Google Scholar] [CrossRef]
- SumanPrakash, P.; Ramana, K.S.; CosmePecho, R.D.; Janardhan, M.; Arellano, M.T.C.; Mahalakshmi, J.; Bhavsingh, M.; Samunnisa, K. Learning-driven Continuous Diagnostics and Mitigation program for secure edge management through Zero-Trust Architecture. Comput. Commun. 2024, 220, 94–107. [Google Scholar] [CrossRef]
- Zhang, J.; Zheng, J.; Zhang, Z.; Chen, T.; Tan, Y.-A.; Zhang, Q.; Li, Y. ATT&CK-based Advanced Persistent Threat attacks risk propagation assessment model for zero trust networks. Comput. Networks 2024, 245. [Google Scholar] [CrossRef]
- Krishnan, Prabhakar; Kurunandan Jain; Shivananda R. Poojara; Satish Narayana Srirama; Tulika Pandey; Rajkumar Buyya. eSIM and blockchain integrated secure zero-touch provisioning for autonomous cellular-IoTs in 5G networks. Computer Communications 2024, 216, 324–345.
- Mekala, Sri Harsha; Zubair Baig; Adnan Anwar; Sherali Zeadally. Cybersecurity for Industrial IoT (IIoT): Threats, countermeasures, challenges and future directions. Computer Communications 2023, 208, 294–320.
- Kaur, M.; Verma, V.K. Cooperative-centrality enabled investigations on edge-based trustworthy framework for cloud focused internet of things. J. Netw. Comput. Appl. 2024, 226. [Google Scholar] [CrossRef]
- Ni, L.; Gong, X.; Li, J.; Tang, Y.; Luan, Z.; Zhang, J. rFedFW: Secure and trustable aggregation scheme for Byzantine-robust federated learning in Internet of Things. Inf. Sci. 2024, 653. [Google Scholar] [CrossRef]
- Cao, Y.; Zhang, J.; Zhao, Y.; Su, P.; Huang, H. SRFL: A secure & robust federated learning framework for IoT with trusted execution environments. Expert Syst. Appl. 2023, 239. [Google Scholar] [CrossRef]
- Varela-Vaca. J.; Gasca, R.M.; Iglesias, D.; Gónzalez-Gutiérrez, J. Automated trusted collaborative processes through blockchain & IoT integration: The fraud detection case. Internet Things 2024, 25. [Google Scholar] [CrossRef]
- Arazzi, M.; Nicolazzo, S.; Nocera, A. A novel IoT trust model leveraging fully distributed behavioral fingerprinting and secure delegation. Pervasive Mob. Comput. 2024, 99. [Google Scholar] [CrossRef]
- Javeed, D.; Saeed, M.S.; Adil, M.; Kumar, P.; Jolfaei, A. A federated learning-based zero trust intrusion detection system for Internet of Things. Ad Hoc Networks 2024, 162. [Google Scholar] [CrossRef]
 Chanapha Bast graduated with a Ph.D. in Information Management from National Dong Hua University, Taiwan, in 2020. She earned her Master of Information Technology and Computer in 2007 from King Mongkut’s University of Technology Thonburi in Bangkok, Thailand. Currently, she serves as a lecturer in the Business Computer Department at the Management Science Faculty of Udon Thani Rajabhat University, Thailand. Her primary research interests include IoT, security, privacy, cybersecurity, network security, and cloud computing. Additionally, she has conducted significant research in blockchain technology. Her contributions have been widely published in various peer-reviewed journals and conference proceedings, underscoring her expertise and commitment to advancing knowledge in these critical areas. Chanapha Bast graduated with a Ph.D. in Information Management from National Dong Hua University, Taiwan, in 2020. She earned her Master of Information Technology and Computer in 2007 from King Mongkut’s University of Technology Thonburi in Bangkok, Thailand. Currently, she serves as a lecturer in the Business Computer Department at the Management Science Faculty of Udon Thani Rajabhat University, Thailand. Her primary research interests include IoT, security, privacy, cybersecurity, network security, and cloud computing. Additionally, she has conducted significant research in blockchain technology. Her contributions have been widely published in various peer-reviewed journals and conference proceedings, underscoring her expertise and commitment to advancing knowledge in these critical areas. |
 Kuo-Hui Yeh (SM’16) serves as a professor at the Institute of Artificial Intelligence Innovation, National Yang Ming Chiao Tung University, Hsinchu, Taiwan. Prior to this appointment, he was a professor in the Department of Information Management at National Dong Hwa University, Hualien, Taiwan, from February 2012 to January 2024. Dr. Yeh earned his M.S. and Ph.D. degrees in Information Management from the National Taiwan University of Science and Technology, Taipei, Taiwan, in 2005 and 2010, respectively. He has contributed over 150 articles to esteemed journals and conferences, covering a wide array of research interests such as IoT security, Blockchain, NFC/RFID security, authentication, digital signatures, data privacy and network security. Furthermore, Dr. Yeh plays a pivotal role in the academic community, serving as an Associate Editor (or Editorial Board Member) for several journals, including the Journal of Information Security and Applications (JISA), Human-centric Computing and Information Sciences (HCIS), Symmetry, Journal of Internet Technology (JIT) and CMC-Computers, Materials & Continua. In the professional realm, Dr. Yeh is recognized as a Senior Member of IEEE and holds memberships with (ISC)², ISA, ISACA, CAA, and CCISA. His professional qualifications include certifications like CISSP, CISM, Security+, ISO 27001/27701/42001 Lead Auditor, IEC 62443-2-1 Lead Auditor, and ISA/IEC 62443 Cybersecurity Expert, covering fundamentals, risk assessment, design, and maintenance specialties. Kuo-Hui Yeh (SM’16) serves as a professor at the Institute of Artificial Intelligence Innovation, National Yang Ming Chiao Tung University, Hsinchu, Taiwan. Prior to this appointment, he was a professor in the Department of Information Management at National Dong Hwa University, Hualien, Taiwan, from February 2012 to January 2024. Dr. Yeh earned his M.S. and Ph.D. degrees in Information Management from the National Taiwan University of Science and Technology, Taipei, Taiwan, in 2005 and 2010, respectively. He has contributed over 150 articles to esteemed journals and conferences, covering a wide array of research interests such as IoT security, Blockchain, NFC/RFID security, authentication, digital signatures, data privacy and network security. Furthermore, Dr. Yeh plays a pivotal role in the academic community, serving as an Associate Editor (or Editorial Board Member) for several journals, including the Journal of Information Security and Applications (JISA), Human-centric Computing and Information Sciences (HCIS), Symmetry, Journal of Internet Technology (JIT) and CMC-Computers, Materials & Continua. In the professional realm, Dr. Yeh is recognized as a Senior Member of IEEE and holds memberships with (ISC)², ISA, ISACA, CAA, and CCISA. His professional qualifications include certifications like CISSP, CISM, Security+, ISO 27001/27701/42001 Lead Auditor, IEC 62443-2-1 Lead Auditor, and ISA/IEC 62443 Cybersecurity Expert, covering fundamentals, risk assessment, design, and maintenance specialties. |
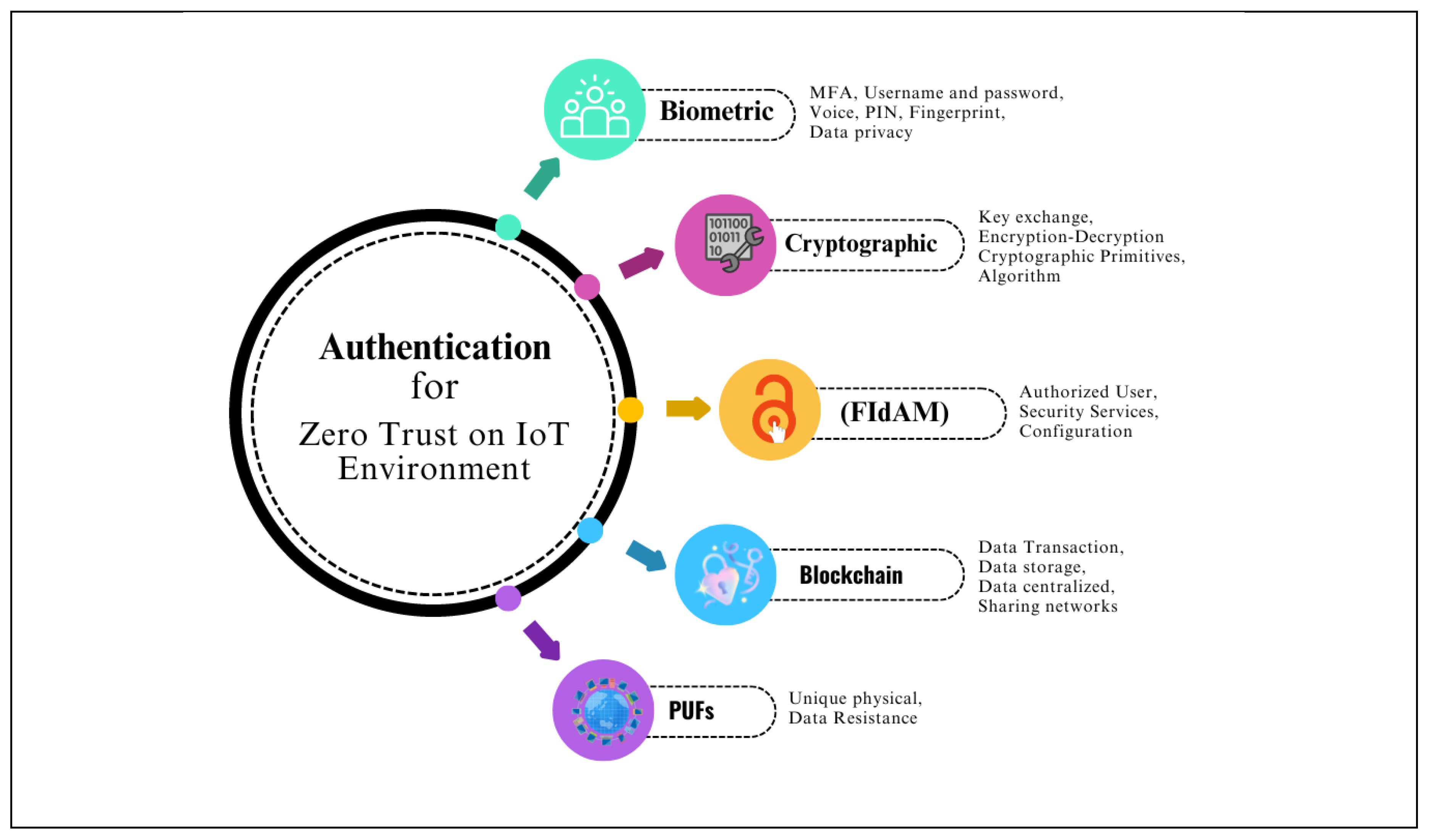
| Author(s) | Implementation | Authentication Technology | Advantages/ Challenges |
|---|---|---|---|
| [3] (2023) |
Using factors as PIN password, verification, facial recognition. | Biometric Authentication |
• Strong authentication based on unique biological or behavioral traits. • Enhances user for memorizing passwords or token. • Potential privacy concerns. • Increasing device costs. |
| [9] (2021) |
Identifying device fingerprints authentication for users and providing entry-point security, identity the subject, and accessing the device. | ||
| [26] (2019) |
Specifying biometric scanner collects unique biological data from users and matches the stored data. | ||
| [5] (2020) |
Using for verification and calculating the discrete algorithm problem. | Cryptographic Authentication |
• Offers mathematically security. • Supports secure key exchange. • Non-repudiation, data integrity, and cryptographic primitives. • Computationally intensive for constrained IoT devices. • Requires secure communication channels for key exchange. |
| [10] (2024) |
Taking uniqueness and persistence of physiological characteristics and user identity. | ||
| [21] (2022) |
Protecting the system by manufacturers. | ||
| [25] (2023) |
Securing protocols for data storage and transmission and using to the confidentiality, integrity, and availability. | ||
| [26] (2019) |
Using to morph actual messages during communication in an insecure network. | ||
| [27] (2023) |
Offering higher confidence over authenticator and verifying an authentication key. | ||
| [28] (2019) |
Using as a key requirement within the scheme to fulfil the cryptographic checksum needed. | ||
| [6] (2024) |
Ensuring only authorized users, devices, and applications can access networks. | Federated Identity and Access Management (FIdAM) |
• Enables seamless authentication across multiple IoT. • Reduce complexity • Supports various authentication methods. • Required trust establishment. |
| [11] (2023) |
Providing the requested security services, access control, and management of configuration updates. | ||
| [29] (2023) |
Adding security for all resource authentication and authorization and strictly enforced. | ||
| Author(s) | Implementation | Authentication Technology |
Advantages/ Challenges |
| [1] (2020) |
Proposing an anonymous access system and computing the divided identity block data. | Blockchain-based Authentication |
• Provide a decentralized. • Enables secure and editable identity management. • Supports distributed trust. • Scalability limitations. • Requires design and implementation to ensure privacy and security. |
| [10] (2024) |
Presenting blockchain technology for zero trust networks and comparing techniques used by different platforms. Presenting a possible approach for trusted transactions. | ||
| [11] (2023) |
Securing data storage, sensitive data and distributing data across multiple nodes. | ||
| [25] (2024) |
Protecting sensitive information and combining blockchain and trust assessment. | ||
| [27] (2023) |
Presenting blockchain technology with zero trust. | ||
| [28] (2019) |
Presenting the potential to increase privacy and security in blockchain applications. | ||
| [9] (2021) |
Designing characteristics that are used in one piece of hardware. | PUFs, or physically unclonable functions | • Unique physical properties. • Offers tamper resistance and counterfeiting capacities. |
| [20] (2024) |
Linking between malware on Android devices and zero trust security. |
| Feature | Mutual Authentication |
Cryptographic Authentication |
Multi-Factor Authentication (MFA) |
Blockchain-based Authentication |
Ref. |
|---|---|---|---|---|---|
| Security | High | Moderate | High | High | [25,30,31] |
| Processing | Low, Moderate | Low | Low, Moderate | Moderate, High | [32,33] |
| Scalability | Moderate | High | High | Scalability limitations | [28,29,34,35] |
| Resource | Moderate | Low | Low, Moderate | Moderate, High | [30,36] |
| Complexity | Moderate | Low | Moderate | High | [21,29,34] |
| Suitability | Moderate | High | Moderate | Limited | [2,28,31,37] |
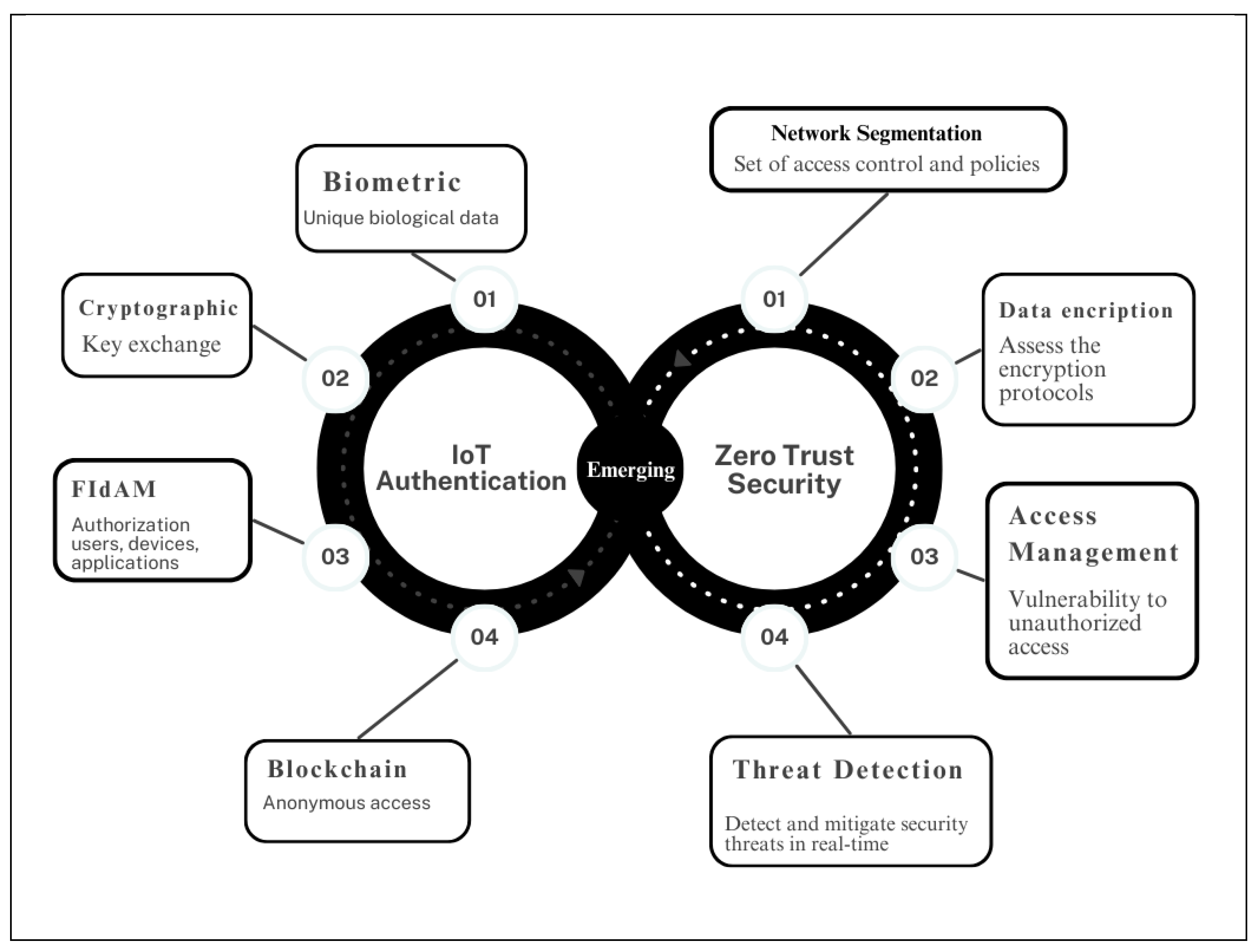
| Evaluation Features | Benefits | Ref. |
|---|---|---|
| IoT Device Identification | • Identify all IoT devices connected to the networks. • Vulnerabilities security. |
[5,24,32,38] |
| Network Segmentation | • Analyze network segmentation. | [7,10,39] |
| Access Management | • Determine authentication methods. • Vulnerability to unauthorized access. |
[11,29] |
| Data Encryption | • Assess the encryption protocols. • Use data transmission within IoT environment. |
[5,14] |
| Threat Detection | • Evaluate mechanisms and analyze effectiveness. | [20,30] |
| Penetration Testing | • Conduct hacking and simulated attacks to assess the authentication mechanisms. • Test against various attacks (spoofing, man in the middle). • Identify and exploit potential vulnerabilities. |
[2,10,29,31,40,41] |
| Formal Verification | • Use techniques and mathematical models to confirm the security characteristics of cryptography and authentication. • Ensure established security guarantees. |
[5,12,39] |
| Simulation and emulation | • Simulate the IoT and authentication to evaluate performance and scalability. • Identify resource constraints and interoperability. |
[29,33] |
| Compliance Testing | • Assess authenticity to security standards. • Ensure compliance with legal data protection and data privacy. |
[10,23,27] |
|
Evaluation/ implementation |
[11] | [12] | [15] | [20] | [24] | [34] | [36] | [38] | [42] | [43] | [44] |
| Stringent access controls | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ |
| Micro-segmentation strategies | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ |
| Threat detection systems | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Data Encryption | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ |
| Zero Trust policies across the IoT environment | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ |
| Integrating IoT security | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ |
| Developing IoT environments under Zero Trust principles | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Future Directions | Suggestions |
|---|---|
| Continuous Adaptive Risk and Trust Assessment (CARTA) | CARTA frameworks are endlessly adapted based on context, behavior, and risk factors for IoT devices [50,51,52,53,54]. |
| Blockchain-based Authentication | Develop blockchain technologies for decentralized, tamper-proof authentication and access control in IoT ecosystems. This technology addresses scalability limitations on a large scale [55,56]. |
| Quantum-resistant cryptography | Investigate quantum-resistant cryptographic algorithms as the protocols to secure IoT authentication against and prepare for potential vulnerabilities from future quantum computing threats[57]. |
| Federated Identity and Access Management (FedIAM) | Implement FedIAM solutions to enable secure and seamless authentication across multiple IoT service providers. This reference implements a standardized authentication protocol to facilitate it across IoT platforms[51,52]. |
| Integration of AI and Machine Learning (ML) | Develop AI/ML techniques for real-time anomaly detection and adaptive authentication mechanisms in IoT environments. To analyze user and device patterns in real-time, dynamically adjust access control policies based on risk assessment[54,58]. |
| Privacy-preserving Authentication | Explore authentication schemes that protect user privacy and sensitive data in the IoT environment. Develop for user control and usage associated with authentication[53,59]. |
| Secure Firmware and Hardware Roots of Trust | Integrate secure hardware and trusted execution environments for IoT device authentication and integrity[60,61]. |
| Future Directions | Suggestions |
| Standardization of Authentication Protocols for Interoperability | Participate in standards and ensure interoperability among different IoT authentication solutions. Develop open-source libraries and references for standardized authentication protocols[51,56]. |
| User-centric Authentication for Improve Usability | Discover user-centric authentication, user preferences, user-friendly interfaces, and workflows such as biometrics and behavioral patterns for secure and convenient IoT access control in an IoT environment[52]. |
| Emerging Technologies | Investigate the security implications of emerging technologies and networks on authentication processes within the IoT environment[57,59,62]. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).





