4.1. Result
In today’s advanced age, understanding information is one of the significant components within the healthcare framework. In any case, with the expanding utilize of data innovation, noteworthy challenges related to the security and security of therapeutic information have risen. The fear of information spillage, cyber-attacks, and security breaches are major concerns for researchers and specialists within the healthcare field. These concerns are opened up by the delicate nature of restorative information, which incorporates individual data, restorative histories, and treatment plans, all of which must be secured to preserve quiet believe and comply with administrative prerequisites.
The quick digitization of healthcare records, such as Electronic Medical Records (EMRs), has brought approximately significant enhancements in healthcare conveyance and persistent results. Be that as it may, this digitization too presents vulnerabilities that can be misused by malevolent on-screen characters. Cyber-attacks on healthcare frameworks can lead to unauthorized get to to understanding information, causing not as it were money related misfortunes but moreover possibly imperiling patients’ lives by controlling basic wellbeing data. Security breaches, where individual wellbeing data is uncovered, can have serious repercussions for patients, counting stigmatization and separation.
To address these squeezing challenges, different imaginative approaches have been created and actualized. Later inquire about offers a plenty of potential arrangements that not as it were improve the security and protection of persistent information but also fortify the productivity and viability of restorative information administration. These arrangements extend from progressed encryption procedures and secure communication conventions to the execution of blockchain innovation and combined learning frameworks. For occasion, blockchain innovation gives a decentralized and permanent ledger that can guarantee the judgment and security of restorative records, making it amazingly troublesome for unauthorized clients to modify or get to touchy information. Combined learning, on the other hand, allows the preparing of machine learning models on decentralized information, guaranteeing that understanding information remains inside the limits of the healthcare teach whereas still contributing to the advancement of vigorous prescient models.
Besides, coordination huge information analytics into healthcare frameworks presents an opportunity to use tremendous sums of information for made strides persistent results, taken a toll lessening, and upgraded clinical decision-making. Be that as it may, this integration too brings forward challenges related to information security and moral contemplations. Guaranteeing that huge information analytics does not compromise understanding protection requires exacting security measures and compliance with moral measures.
The taking after may be a comprehensive survey of the comes about from a writing audit conducted on later inquire about that highlights different perspectives of keeping up persistent information security and security in an progressively distributed and digitized healthcare environment. This audit analyzes the techniques, innovations, and administrative systems that have been proposed and actualized to defend understanding information against modern dangers. By understanding these arrangements, partners within the healthcare industry can adopt best hones and inventive advances to ensure understanding information viably, subsequently cultivating a secure and dependable healthcare biological system.While technology plays an important role, human error is a significant factor in data breaches. Training staff on proper data handling procedures and implementing strong access control measures can help mitigate this risk.Many healthcare institutions still rely on outdated systems that may not have the necessary security features to protect sensitive data. Upgrading these systems is crucial but can be a complex and expensive undertaking
Table 1 underneath gives a outline of the key findings and proposed arrangements from later inquire about, outlining the multifaceted approach required to address the complex challenges of understanding information security and protection in today’s advanced age. Through the blend of these investigate endeavors, it gets to be apparent that a combination of innovative advancement, administrative compliance, and nonstop watchfulness is basic to ensure persistent information in an progressively interconnected world.
Table 1.
Results of Analysis of Literature Study
Table 1.
Results of Analysis of Literature Study
| 1 |
Researcher |
Tahani Aljohani, Ning Zhang [12] |
| |
Problem |
The problem of this research is to develop a SPID (Secure, ID Privacy, and Inference Threat Prevention Mechanisms for Distributed Systems) framework that can facilitate remote patient data collection in distributed systems by ensuring data security, maintaining patient ID privacy, and preventing inference attacks. This framework is designed to address security threats, ID privacy, and inference attacks in distributed systems. |
| |
Method |
The research method used involved analyzing potential threats, determining design requirements, and developing the SPID framework. The research also involved the use of cryptographic building blocks, pseudonym generation, encryption, and dual signature methods to maintain data confidentiality, authentication, and patient anonymity. |
| |
Result |
The result of this research is the development of a SPID (Secure, ID Privacy, and Inference Threat Prevention Mechanisms for Distributed Systems) framework that is effective in facilitating remote patient data collection in distributed systems. The framework is able to maintain data security, preserve patient ID privacy, and prevent inference attacks. By using pseudonymization and encryption, the framework ensures patient anonymity and data security. Performance evaluation is done using queuing theory, considering metrics such as average waiting time and response time. The SPID framework is shown to be effective in preventing various types of attacks, such as identity forgery, man-in-the-middle, linkability, data falsification, replay, and denial. |
| |
|
Anonymity is maintained through pseudonym generation and linking methods, where the level of anonymity increases with the number of patients in the system. |
| 2 |
Researcher |
Jahanzeb Shahid , Rizwan Ahmad et. al [22] |
| |
Problem |
The main issue addressed in this paper is the significant privacy and security risks associated with the Internet of Healthcare Things (IoHT). The paper identifies the vulnerability of healthcare data due to various factors, including weak security protocols, heterogeneity of IoHT devices, and inadequate legislative frameworks. Specific issues highlighted include privacy breaches from data leakage, device lifecycle transitions, and the interconnectedness of different data systems, all of which jeopardize patient data privacy and security. [23] [24] |
| |
Method |
The authors adopt a layered architecture approach to systematically analyze data protection and privacy issues in IoHT. They classify IoHT devices and systems, review communication protocols, and identify potential points of data leakage. The paper also evaluates global governance initiatives and legislative frameworks, comparing different approaches to identify best practices and gaps. This structured analysis is supported by a review of recent literature and existing IoHT implementations.[25] |
| |
Result |
Identification of multiple vulnerabilities in IoHT systems, including weak communication protocols and insecure middleware. Need for better technical standards and stronger regulatory frameworks to protect healthcare data. [26] |
| 3 |
Researcher |
Vijaykumar Bidve, et al [11] |
| |
Problem |
Manual processes in handling and maintaining patient data in hospitals lead to significant inefficiencies and errors. These issues arise from the time-consuming nature of manual data entry, the high risk of human error, and the difficulties in organizing and retrieving paper records. Human errors can result in incorrect treatments and misdiagnoses, while the lack of real-time data access hinders effective communication and care coordination. Overall, these inefficiencies compromise patient safety and care quality, highlighting the need for transitioning to electronic health records (EHRs) and automated systems to improve accuracy and data management.
[11] |
| |
Method |
The research method in this paper involved developing a blockchain-based patient data management system to overcome inefficiencies of traditional systems. It began with analyzing existing systems’ limitations, such as data fragmentation and vulnerability to tampering. The system’s design integrated blockchain’s decentralized ledger for enhanced security and automated data management through smart contracts. Development included custom blockchain network creation, ensuring compliance with healthcare standards. Rigorous testing validated system performance, highlighting improvements in security, data integrity, and efficiency over manual methods. Comparative analysis underscored blockchain’s advantages in healthcare data management, affirming its potential to revolutionize the field. [11] |
| |
Result |
The research culminated in the creation of a robust patient data management system leveraging blockchain technology. This system prioritizes secure data control and access exclusively for authorized healthcare users. By harnessing blockchain’s decentralized ledger, the system ensures that patient data remains secure and tamper-proof. Each transaction and access attempt is recorded transparently, enhancing accountability and preventing unauthorized alterations. Through the implementation of smart contracts, automated protocols govern data handling, guaranteeing adherence to predefined rules without human intervention. |
| |
|
This approach not only safeguards patient privacy but also facilitates efficient data sharing among healthcare providers while maintaining compliance with regulatory standards. Overall, the developed system represents a significant advancement in healthcare data management, addressing longstanding challenges of security, accessibility, and integrity through innovative blockchain solutions. [11] |
| 4 |
Researcher |
Sejong Lee, et al. [27] |
| |
Problem |
This research aims to design a decentralized blockchain-based patient information exchange system to enable secure and efficient sharing of electronic medical records (EMRs). [27] |
| |
Method |
The research method used in the study involved proposing a blockchain-based EMR-sharing system that allows patients to manage and share their EMRs securely. The system was implemented using simulation models with Hyperledger Fabric, an open-source blockchain framework.[27] |
| |
Result |
The simulation of the proposed blockchain-based EMR-sharing system showed that it takes an average of 0.01014 seconds to download 1 MB of EMR, and data can be freely shared with other users regardless of the size or format of the data. Additionally, the security analysis confirmed that the distributed ledger structure and re-encryption-based data encryption method effectively protect users’ EMRs from forgery and privacy leak threats, ensuring data integrity. [27] |
| 5 |
Researcher |
Stephen V. Flowerday, Christos Xenakis |
| |
Problem |
The primary problem addressed in the paper is the significant cybersecurity threats and privacy concerns associated with distributed healthcare environments. As the healthcare industry increasingly adopts distributed systems to manage and analyze sensitive patient data, the risks of unauthorized access, data breaches, and non-compliance with data protection regulations also rise. The challenge lies in balancing the utilization of advanced data-driven technologies for healthcare improvements while ensuring the security and privacy of patient data.[24] |
| |
Method |
Review of AI techniques for privacy preservation, Personal Health Train (PHT) approach, and ontological modeling for network asset representation.[25] |
| |
Result |
Federated Learning identified as a promising AI technique for biomedical applications; PHT allows compliant data analysis; ontological models enhance threat detection in healthcare environments. [26] |
| 6 |
Researcher |
Ons Aouedi, et al. [28] |
| |
Problem |
Handling privacy-sensitive medical data with Federated Learning (FL).[28] |
| |
Method |
The research method used in the document involves a comprehensive review of current solutions applying federated learning-based approaches in healthcare and the Internet of Medical Things (IoMT). The paper also discusses the workflow of typical federated learning algorithms and outlines the challenges and future research directions in using federated learning for IoMT.[28] |
| |
Result |
Importance of FL in collaborative learning systems in healthcare, emphasizing privacy, security, and efficiency. Challenges include overfitting, efficient training management, and anomaly detection.
[28] |
| 7 |
Researcher |
Sohaib Saleem, et al.[29] |
| |
Problem |
Lack of coordination and communication among healthcare stakeholders, security and privacy issues in standard EMR systems.[29] |
| |
Method |
The research methodology used in the study on blockchain-based solutions for EMR issues and challenges involved a systematic literature review (SLR) to collect data, find gaps in current research, and answer formulated research questions. |
| |
|
The SLR methodology followed guidelines by Barbara Kitchenham and involved steps such as motivation and research questions, search strategy, inclusion and exclusion criteria, classification criteria, and data extraction. The search strategy included using digital libraries like IEEE Xplore, ACM Digital Library, ScienceDirect, Scopus, and Springer to find peer-reviewed studies published in reputable journals, conferences, books, and workshops. Data extraction focused on EMR issues, EMR Blockchain, Electronic Medical Records Blockchain, EMR Privacy, Security, and the benefits of blockchain technology in the EMR environment.[29] |
| |
Result |
Blockchain technology enhances security, decentralization, data privacy, patient data ownership, and interoperability in EMR management. [29] |
| 8 |
Researcher |
Javier Rojo et al.[30] |
| |
Problem |
The research method used in the study involved deploying the proposed architecture in simulated healthcare institutions and developing a web application for doctors to operate with the Personal Health Trajectory of patients.[30] |
| |
Method |
Deployment of architecture in simulated healthcare institutions, development of a web application for doctors.[30] |
| |
Result |
Successful integration of patient health data, allowing comprehensive access and enhancing patient information management through blockchain federation. [30] |
| 9 |
Researcher |
Chandra Thapa, Seyit Cantepe |
| |
Problem |
Challenges in data security, privacy, and trust in precision health.[24] |
| |
Method |
Centralized and decentralized data storage, data-to-modeler and model-to-data approaches, multi-party computation (MPC).[25] |
| |
Result |
Emphasis on the importance of data security and privacy in precision health, with regulatory and ethical requirements guiding data management practices. [26] |
| 10 |
Researcher |
Vikram Jeet Singh, et al.[31] |
| |
Problem |
The challenges associated with implementing big data analytics in healthcare are multifaceted and include maintaining data privacy and security. Ensuring the confidentiality of patient information is of utmost importance, given the sensitive nature of health records and stringent regulatory requirements such as HIPAA and GDPR. Healthcare organizations should invest in strong encryption methods, secure data storage solutions, and comprehensive access controls to protect against unauthorized access and data breaches. Additionally, there is a need to balance data accessibility for analytics with privacy concerns, ensuring that only authorized personnel can access certain data sets. Implementing big data analytics also needs to address issues related to integrating data from multiple sources, standardizing data formats, and ensuring data quality and accuracy. The complexity of healthcare data, coupled with the need for real-time analysis, further complicates these efforts, requiring advanced technologies and sophisticated algorithms to manage and analyze data safely and effectively. [31] |
| |
Method |
To address the challenges of maintaining data privacy and security in big data analytics in healthcare, healthcare providers must implement a comprehensive set of security measures. These measures include strong encryption techniques to protect data both in transit and at rest, ensuring that sensitive patient information remains confidential and safe from unauthorized access. Access control is essential, which involves implementing multi-factor authentication and role-based access to restrict data access to only those individuals with the necessary permissions. |
| |
|
In addition, regular data backup and recovery procedures are essential to protect against data loss or corruption, thus enabling the recovery of critical information in the event of a cyberattack or system failure. By integrating these security protocols, healthcare providers can create a resilient and secure data environment that supports the effective use of big data analytics while complying with regulatory standards and maintaining patient trust. [31] |
| |
Result |
Emphasizing compliance with data privacy regulations such as HIPAA (Health Insurance Portability and Accountability Act) in the United States and GDPR (General Data Protection Regulation) in Europe is of paramount importance in the field of healthcare data analytics. These regulations establish comprehensive guidelines and standards for the protection of patient information, ensuring that healthcare organizations manage data with the highest level of confidentiality and integrity. Compliance with these regulations requires the implementation of robust security measures, including advanced encryption techniques, secure authentication protocols, and strict access controls to protect sensitive data from unauthorized access, breaches, and other cyber threats. In addition, regular audits, thorough risk assessments, and comprehensive data backup and recovery plans are essential for maintaining data security and ensuring ongoing compliance. By integrating these rigorous security practices, healthcare providers can not only meet regulatory requirements, but also build and maintain patient trust, ultimately improving the effectiveness and reliability of healthcare data analytics. [31] |
Based on the analysis, the current state of the art in patient data security and privacy focuses on utilizing advanced technologies such as blockchain, Federated Learning (FL), and privacy-preserving AI techniques to address various challenges in healthcare data management. These studies highlight the importance of secure data collection, efficient data sharing, and strong regulatory compliance to ensure the privacy and security of patient information. The integration of blockchain and FL offers a promising solution for decentralized and secure data management, while the comprehensive review and analysis underscores the need for improved technical standards and stronger legislative frameworks to effectively protect healthcare data.
4.2. Discussion
Tahani Aljohani and Ning Zhang [
12] in this study developed the SPID (Secure, ID Privacy, and Inference Threat Prevention Mechanisms for Distributed Systems) framework that aims to improve security and privacy in remote patient data collection in distributed systems. They use cryptography, pseudonymization, and data encryption techniques to maintain data confidentiality and patient anonymity. The performance evaluation of this framework uses queuing theory to measure the average waiting time and response time, showing that SPID is effective in preventing various attacks such as identity forgery and data falsification. Overall, this framework provides a holistic solution to address security threats, ID privacy, and inference attacks in a distributed system environment.
Meanwhile, Jahanzeb Shahid, Rizwan Ahmad and team[
32]focused on the security and privacy risks associated with the Internet of Healthcare Things (IoHT). They identified that heterogeneous IoHT devices and weak communication protocols increase vulnerability to health data leakage. Their study concluded the need to improve legislative frameworks as well as security standards to effectively protect health data from cyber-attacks and privacy breaches. Their analysis underscores the importance of rigorous technical updates and adequate regulatory approaches to address security challenges in the evolving IoHT environment.
Vijaykumar Bidve and his colleagues[
11] developed a patient data management system using blockchain technology, which allows users to have greater control over their data. By using blockchain, they secured only authorized data access and effectively ensured data integrity. This research shows that blockchain not only enhances the security of medical data, but also facilitates the secure exchange of data between different entities in the health system. Thus, blockchain provides a potential solution for improving patient data management while maintaining strong privacy.
Sejong Lee and colleagues [
27] designed a blockchain-based electronic medical record (EMR) exchange system to improve the security and privacy of medical data. Using Hyperledger Fabric, they simulated this system and found that this approach is effective in protecting EMRs from the threat of forgery and leakage. The blockchain implementation allows medical data to be shared and replicated across multiple nodes, ensuring the availability of information without a single point of failure. Their results highlight the potential of blockchain to significantly improve the integrity and security of electronic medical data.
Stephen V. Flowerday and Christos Xenakis[
33] investigate significant cyber threats and privacy concerns in distributed health environments. Their study includes a review of various artificial intelligence (AI) techniques and ontology modeling approaches that can be applied to strengthen surveillance and management against cyber threats in health systems. By exploring techniques such as Federated Learning and ontology models, they offer solutions to maintain a balance between data-powered technological innovation and strict patient data security and privacy.
Ons Aouedi and his team [
28] explore the use of federated learning to manage sensitive medical data in the Internet of Medical Things (IoMT). They highlighted the challenges and future research directions in applying federated learning to maintain data privacy and efficiency in a distributed environment. This research suggests that adopting federated learning can enable collaboration in data analysis without compromising patient privacy or medical data security.
Sohaib Saleem and his colleagues[
29] examined the problems and challenges in conventional electronic medical record (EMR) systems and proposed a blockchain-based solution. They showed that blockchain can improve the security, privacy, and interoperability of EMR data with transparency and decentralization. By utilizing blockchain technologies such as BPDS, MedRec, and MedShare, they proved that this approach can improve efficiency and security in health data management.
Javier Rojo and team[
30] developed an innovative architecture to integrate patient health data from multiple sources using blockchain technology. Their comprehensive study demonstrates that by implementing a blockchain-based approach, healthcare institutions can facilitate easier and more secure access to integrated health information. This method ensures that data from various sources is combined efficiently and securely, promoting better coordination among different healthcare providers. Consequently, the use of blockchain technology in this context significantly improves the quality and accessibility of integrated health information, thereby enhancing overall patient care and data management across the healthcare sector.
Chandra Thapa and Seyit Cantepe discussed the challenges of managing data security and privacy in the context of precision health. They highlight various computational approaches such as Data-to-Modeler (DTM), Model-to-Data (MTD), and Multi-Party Computing (MPC) to protect sensitive data from cyberattacks and effectively manage data consent. Their research reinforces the importance of strict regulations and careful technical implementation in protecting patient data privacy and security.
Vikram Jeet Singh and team [
31] considers the challenges of applying big data analytics in healthcare by maintaining data privacy and security. The research emphasizes the importance of implementing security measures such as encryption, access control, and data recovery strategies to protect health data from unauthorized access. By adhering to regulations such as HIPAA and GDPR, this research highlights the importance of compliance with global data privacy standards to address the challenges of medical data security in the digital age.
4.3. Challenges in Patient Data Security and Privacy
The results of the literature study state that there are challenges in Patient Data Security and Privacy that can compromise the security of patient data so that it can provide opportunities for data leakage.
1) Cyber Attack Threats
Cyber attacks can affect distributed health systems, which consist of various interconnected digital devices and platforms. Attackers can use spoofing techniques to impersonate legitimate entities to access or alter patient data. Attackers can alter or falsify critical medical data after gaining access to them, which can be fatal in healthcare situations. For example, falsification of drug allergy information on medical records can lead to the wrong medication being given to patients and negatively impact their health.
In addition, unauthorized third parties can intercept data sent over the network. Man-in-the-Middle attacks allow attackers to intercept and alter data before it reaches its final destination. These changes often go unnoticed and can lead to harmful results, such as treatment that is not appropriate for the patient’s condition. Replay attacks can also be very dangerous, especially when it comes to medical transactions that require real-time authentication. This occurs when an attacker records previously transmitted data and then repeats it.
2) Privacy of Patient’s Identity
While medical data is usually anonymized to maintain patient privacy, contemporary de-anonymization techniques can reveal a patient’s true identity by combining anonymized data with other data sources. For example, location data from medical records can be used to identify a person. In a data-rich environment, where multiple data sources can be accessed and integrated easily, the risk of this re-identification is very high. Not only does this compromise individual privacy, but it can also allow unauthorized people to know sensitive medical information such as a person’s medical history or mental health condition.
3. Secure Communications and Data Storage
Many devices in the Internet of Healthcare Things (IoHT) and Electronic Medical Records (EMR) systems still use weak communication protocols. These protocols often lack adequate encryption, making them vulnerable to eavesdropping and data manipulation. An obvious example is a medical device connected to a hospital network that is not encrypted, allowing an attacker to monitor and alter the transmitted data.
In addition, storing data on a central server poses a high risk of a single failure. If the server suffers an attack or technical failure, all stored medical data may be lost or accessed without authorization. For example, a ransomware attack on a hospital’s central server could result in all patient data being locked and inaccessible, disrupting hospital operations and putting patients at risk. Reliance on centralized storage also increases the risk of unauthorized access if security measures are not strictly implemented.
4. Regulatory Compliance
The implementation of new technologies in healthcare systems must comply with various data security and privacy regulations, such as HIPAA in the United States, GDPR in the European Union, and the Privacy Act in Australia. These regulations set strict standards for data protection, including requirements for informed consent, secure data transfer and appropriate data processing. Meeting these requirements can be challenging, especially when new technologies need to be integrated into existing systems.
For example, the implementation of blockchain in medical records must comply with data privacy requirements, even though the technology is fundamentally designed for transparency and openness. Different regulations in different regions also require special customisation, which can add to the complexity of implementing new technologies in the global healthcare system.
4.4. Opportunities in Improving Patient Data Security and Privacy
Based on this analysis, there are opportunities that can improve the security and privacy of patient data in a distributed system. These opportunities can be useful to be utilized in implementing security and privacy so that patient data can be maintained and there is no data leakage.
While the challenges faced in patient data security and privacy are significant, there are also various opportunities to improve data protection through the application of advanced technologies and innovative methods. Here are some potential solutions that can be adopted
1) Application of Blockchain Technology
Blockchain offers a decentralized approach that can improve the security of medical data. In a blockchain system, data is not stored in one central location but is distributed across various nodes in the network. Any changes to medical data must be verified by multiple nodes, which ensures data integrity and transparency. In addition, blockchain allows patients to control who has access to their medical data, providing greater control over their personal information. For example, by using smart contracts, patients can grant access permission only for a specific period or for a specific purpose, increasing the security and privacy of their data.
The opportunities for patient data security and privacy using blockchain are.
1. Decentralized Security Blockchain offers a decentralized approach that allows data to be stored across many nodes in the network. This reduces the risk of a single failure and increases the resilience of data against attacks. Since any changes to medical data must be verified by multiple nodes, it ensures data integrity and transparency.
2. Secure Access Control With blockchain, patients can control who has access to their medical data. This allows for more dynamic and secure granting and revocation of access, and ensures that only authorized parties can access sensitive medical information.
2) Federated Learning
Federated learning allows machine learning models to be developed collaboratively without moving the medical data from where it originated. The data remains in its original location, while the models are sent to the data location to be trained. This maintains the privacy of patient data and reduces the risk of data leakage. For example, hospitals can work together to develop disease prediction models without directly sharing patient data, ensuring that patient privacy is maintained. The technology also enables the integration of insights from different data sets without compromising privacy, which can improve the accuracy of prediction and diagnosis models.
1. Collaboration Without Data Sharing. Federated learning allows machine learning models to be developed collaboratively without having to move medical data from where it originated. The data remains in its original location, while the models are sent to the data site to be trained. This maintains the privacy of patient data and reduces the risk of data leakage.
2. Improved Accuracy and Privacy. This technology enables integration of insights from different datasets without compromising patient privacy. The models generated from federated learning can be more accurate as they utilize data from multiple sources, while still maintaining the privacy of each dataset.
3) Cryptography and Anonymization Techniques
Patient data can only be accessed by authorised persons through cryptographic techniques such as data encryption and the use of pseudonyms. Data encryption ensures that the information obtained cannot be read without the right encryption key, even if the data is intercepted. To keep the data safe while being processed, pseudonymisation replaces the original identity with an artificial identifier. For example, a patient’s medical history can be stored with a pseudonymised identifier, which can only be linked to the real identity with a secure decryption key. Multi-party computing (MPC) also allows calculations to be performed on encrypted data without the need to decrypt it, maintaining security and privacy during data analysis.
1. Encryption and Pseudonymization Cryptographic techniques, such as data encryption and the use of pseudonyms, ensure that medical data can only be accessed by authorized parties. Patient information is encrypted so that it can only be read by authorized recipients. Pseudonymization replaces real identities with artificial identifiers to maintain privacy while the data is processed.
2. Multi-Party Computing (MPC) MPC allows calculations to be performed on encrypted data without the need to decrypt the data, maintaining privacy and security during data analysis. This is especially useful in scenarios where multiple parties need to work together to analyze sensitive data without revealing their personal information.
4) Development of New Security Standards and Protocols.
To avoid cyberattacks, more secure communication protocols for IoHT devices and EMR systems should be developed and implemented. Stronger protocols can prevent eavesdropping and alteration of data by third parties. For example, end-to-end encryption can be used in medical data communication to ensure that unauthorised parties cannot access or alter the transmitted data. An important step to protect patient privacy is to ensure that new technologies meet strict data security regulations. This includes implementing appropriate administrative, physical, and technical procedures as well as effective regulatory oversight to monitor and enforce compliance.
1. Stronger Security Protocols.
Developing and implementing more secure communication protocols for IoHT devices and EMR systems is critical to preventing cyberattacks. These protocols should be designed to prevent eavesdropping and data alteration by third parties.
2. Regulatory Compliance and Oversight.
One important way to protect patient privacy is to ensure that new technologies meet strict data security regulations. This includes implementing appropriate administrative, physical, and technical procedures as well as effective regulatory oversight to monitor and enforce compliance.
4.5. Solutions to Enhance Patient Data Security and Privacy
In an effort to address the challenges of patient data security and privacy in distributed health systems, several solutions have been proposed through various researches and recent technologies. Based on the analysis of relevant papers, these solutions offer innovative approaches that can significantly improve the security and privacy of patient data. Here are some of the main solutions that can be implemented.
1) Blockchain Implementation for Medical Data Management.
Blockchain is a powerful technology that can enhance the security and privacy of medical data by transmitting data in a decentralised manner. The immutable, shareable, transparent, and secure record management system offered by blockchain allows electronic medical record (EMR) data to be distributed between different parties without threatening their security and privacy. By using smart contracts, blockchain can ensure that only authorised parties can access and manipulate medical data, thereby reducing the risk of data misuse and unauthorised access. In addition, this technology enables stricter access control and data encryption, which protects patient data from cyber attacks and man-in-the-middle actions.
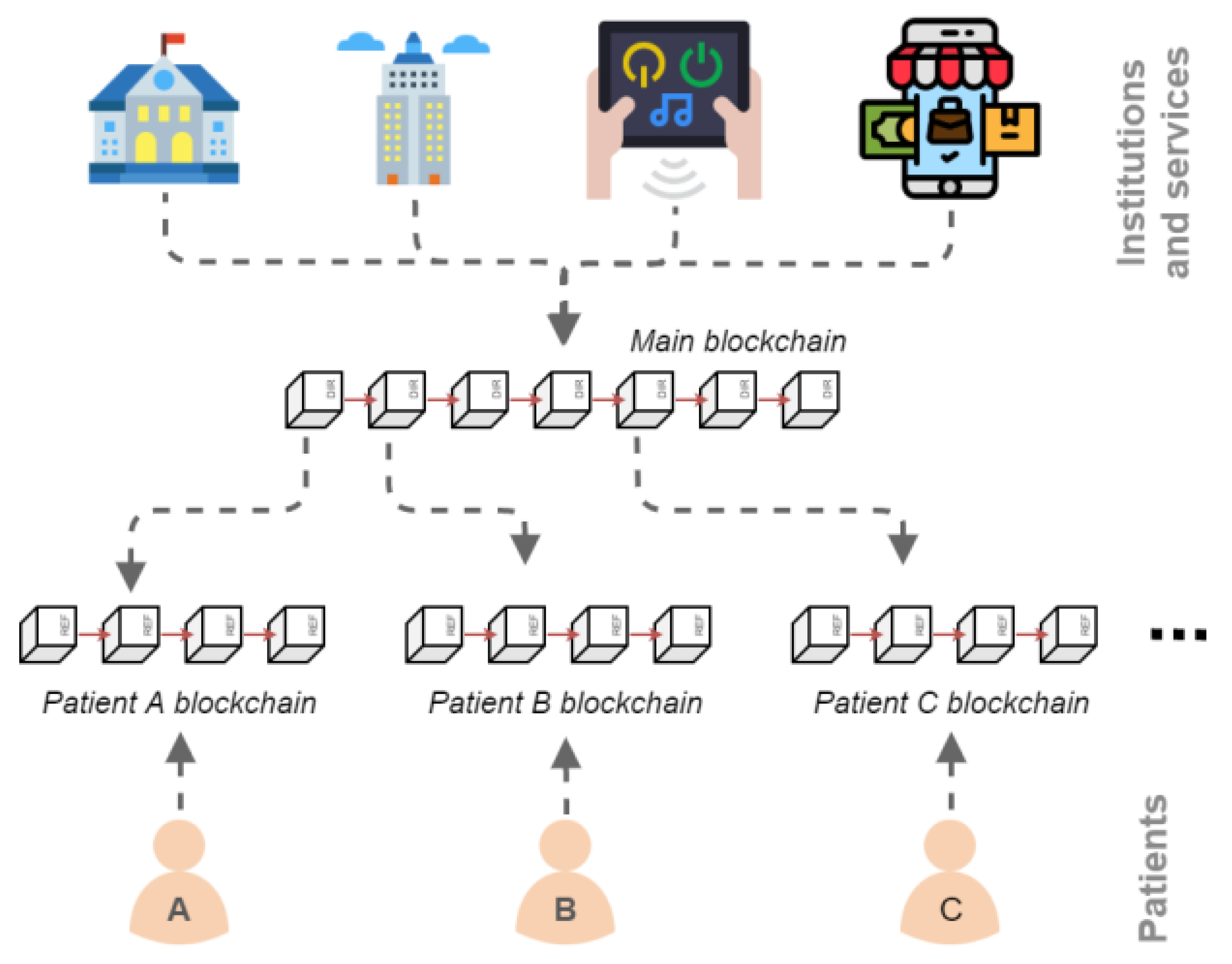
This blockchain technology in maintaining the security and privacy of patient data can help to keep the data safe. Tra’s solution offers unified access to this patient-based distributed system using blockchain federation. Each patient has their own blockchain containing their health data, and the main blockchain stores the location of that patient’s blockchain. Blockchain federation is an idea where multiple low-level blockchains (patient blockchains) are interconnected using a top-level blockchain (main blockchain).
Figure 1.
Blockchain Federation [
30]
Figure 1.
Blockchain Federation [
30]
This solution offers an architecture using REST APIs so as to facilitate the development of health applications using Personal Health Crosswalks derived from patients. The offered blockchain consists of the connection of patient blockchains using other blockchains on the main blockchain to provide access to all these blockchains. Each of these patient blockchains is self-contained and thus considered a federated data structure. This means that each blockchain holds the information of a single patient. The routing structure is applied with another blockchain, the main blockchain. Where each blockchain stores the location of the patient’s blockchain and the information needed in the identification of the patient to whom it belongs.
The way this proposed architecture works is that the storage and management of data in a blockchain system in healthcare aims to ensure the privacy and security of patient information. The patient’s health information is not stored directly on the patient blockchain, but rather on the storage system at the facility or service that generated the data. The patient blockchain only stores references in the form of URLs and data location keys. When organisations or healthcare services need to access patient data, they can use the main blockchain to identify the patient blockchain and access the required data through the stored references. The management of data access rights is controlled by the patient, but in emergency situations or with special permission from the patient, authorised healthcare providers can access the data through the main blockchain. This system gives patients full control over their health information, while ensuring that data can be accessed by those who need it in the right situation.
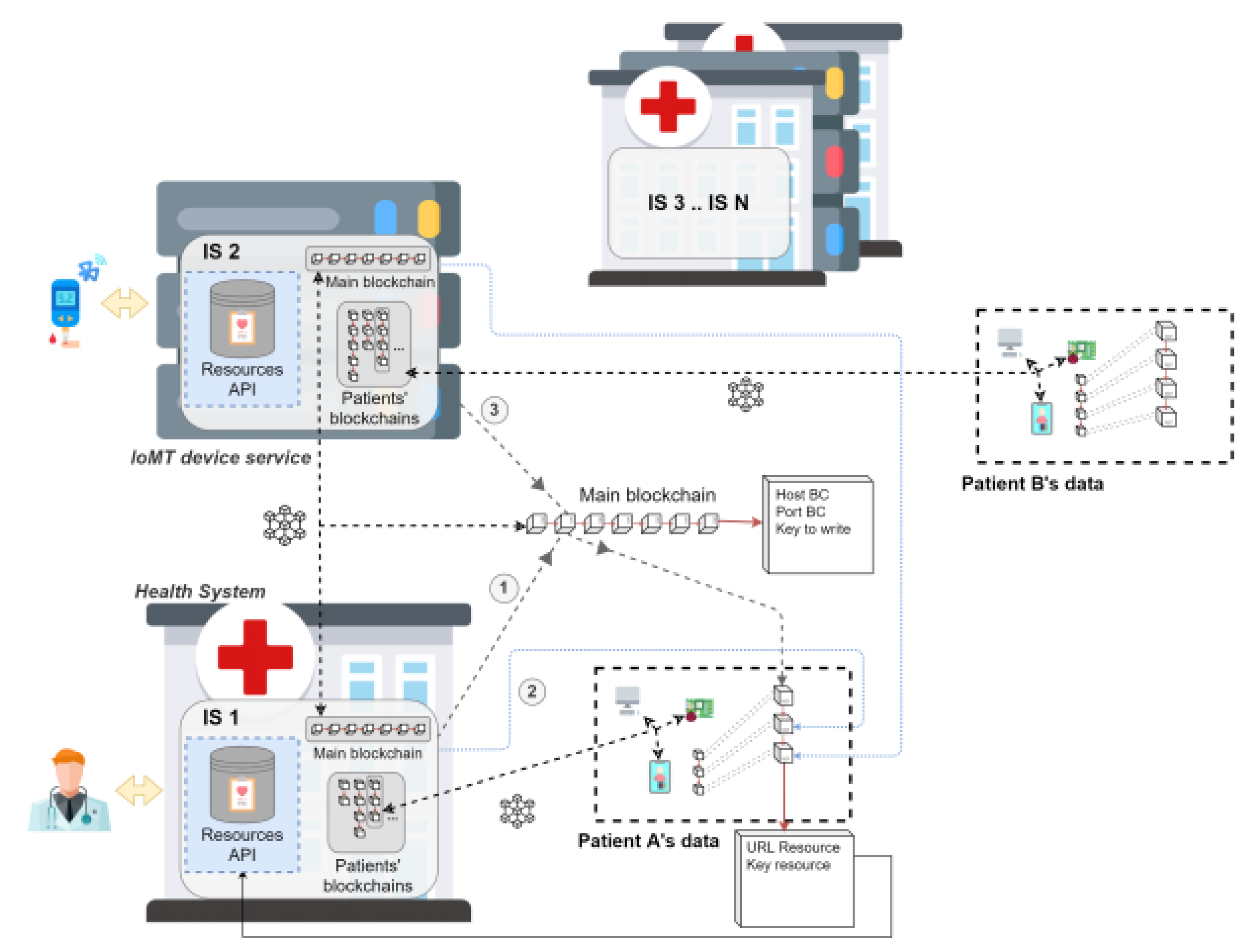
Figure 2.
The architecture offered in the blockchain federation research paper conducted by Javier Rojo and team [
30].
Figure 2.
The architecture offered in the blockchain federation research paper conducted by Javier Rojo and team [
30].
Results from the implementation and validation of the combined blockchain architecture to demonstrate the feasibility and effectiveness of the proposed solution in integrating distributed medical data. For the implementation part, the blockchain architecture was developed using Hyperledger Fabric due to its flexibility and strong access control capabilities. Web service APIs were developed for each healthcare facility or IoT device to provide access to relevant healthcare data. In addition, smart contracts are used to manage data management rules, permissions, and integration between the main blockchain and the patient blockchain.
This blockchain design includes two main components: the patient blockchain and the primary blockchain. Each patient will have a separate blockchain that stores references to their health data, and the permission system will ensure that only authorised parties can access or add to that data. Meanwhile, the primary blockchain manages the metadata and location of the patient blockchain, enabling search and access to the patient blockchain by various healthcare institutions and services. The API developed not only enables data storage and access through the patient blockchain, but also enables interactions between healthcare institutions and the blockchain, such as adding and accessing data references on the patient blockchain.
Simulations and testing were conducted on simulated medical data to test how the system manages, stores, and accesses information. The implementation was tested in a test environment that simulated real-world scenarios with multiple healthcare facilities and patients. The validation part tested the data access performance and measured the speed and efficiency of accessing medical data through the patient blockchain. The results show that this architecture enables fast and efficient access to relevant data.
In addition, validation includes the system’s ability to manage access rights based on permissions granted by patients or healthcare facilities to ensure strict access control and ensure that only authorised entities have access to data including testing. The interoperability of the system was tested to ensure that this architecture can be integrated with various medical data storage systems that already exist in healthcare facilities. It was shown that this architecture can be integrated without major changes to the existing systems. The system also allows patient health data to be presented in a uniform and consistent format, even if the data is obtained from different sources. In terms of security and privacy, this validation ensures that the system is capable of maintaining the confidentiality of patient data through cryptographic mechanisms and permission-based access control, ensuring that the data is secure and only authorised parties can access the data indicating that it is accessible.
The tests also show that the data stored on the blockchain cannot be modified or manipulated, thus guaranteeing the integrity and authenticity of the patient’s health data. The scalability of the system was tested to assess its ability to handle the increasing amount of medical data. The results show that the architecture has excellent scalability and can handle the increasing data and support a growing number of patients and healthcare facilities without compromising performance or efficiency.
The key benefits of a blockchain federation architecture for integrating decentralised healthcare data include several key aspects that can significantly improve the management and use of healthcare data. The architecture enables the integration of distributed patient health data without moving all data to a central repository. This approach allows each medical facility or IoMT device to store data in its own storage system, while the blockchain acts as a reference network that connects all this data. This solves the problem of complex and risky data migration and improves interoperability between the various systems used by healthcare organisations. It seamlessly integrates data from multiple sources and provides easy and efficient access to relevant health information.
As the core technology of this architecture, blockchain ensures high data security and protection. The immutable and decentralised nature of blockchain makes it extremely difficult for unauthorised parties to alter or access data without permission. In addition, permission-based encryption and access control mechanisms ensure that only authorised parties can access the data, according to the permission granted by the patient or healthcare facility. This is especially important in the context of sensitive medical data, where security and privacy are paramount.
The combined blockchain architecture provides a single, consistent view of patient health data. This means patients and healthcare professionals have centralised and integrated access to their health history without having to manually merge data from multiple sources. This feature is particularly useful in emergency situations and during diagnosis and treatment, as it provides a more complete understanding of the patient’s health status. Consistent data access also facilitates coordination between healthcare facilities, improving healthcare efficiency and the quality of services provided.
2) Federated Training (FL) for Machine Training Model Training.
Federated Learning (FL) is an innovative approach in machine learning that enables training models using data spread across multiple locations, such as IoT devices or enterprises without having to transfer raw data to a central data centre. The core idea of FL is to allow entities or organisations that have sensitive data, such as hospitals or enterprises, to maintain the privacy of their patient or customer data, while collaboratively training better and more general machine learning models.
The main concept of FL is data decentralisation. Instead, the data stays where it originates and only the models are sent to where they are processed. This means that sensitive data remains securely stored and does not need to be transferred directly to other entities or large data centres that are prone to security breaches or data theft.
The application of FL in a medical context is very promising. For example, hospitals can work together to train models to detect diseases or predict outcomes based on their patients’ data, without having to disclose patients’ personal details to other entities. This not only improves the quality of patient care with better models, but also complies with strict data privacy regulations.
But FL also has challenges that need to be overcome. One of the main issues is latency, as data must be processed at the source before models can be synchronised. This requires careful management of computing resources and reliable communication technology. In addition, the security aspect is also important, as the delivery of the model and its results can be subject to attacks if not properly protected.
To address the security risks, additional encryption methods and strong security protocols should be implemented in the FL system. This includes the use of end-to-end encryption to protect data during transmission, as well as strict authentication mechanisms to ensure that only authorised entities can participate in the model training process.
Overall, FL represents a significant step forward in enabling data collaboration without compromising individual privacy. By continuing to develop appropriate techniques and policies, FL can be a powerful tool in improving healthcare and other applications that require analysing data from multiple sources, while adhering to strict privacy and security standards.
3) Use of Advanced Cryptographic Techniques.
The use of advanced cryptographic techniques, such as end-to-end encryption, pseudonymisation and multi-party computing (MPC), has become key in the effort to protect the security of sensitive medical data.
End-to-end encryption is a very important technique in securing data during the transmission process. It ensures that data remains encrypted from source to destination, preventing unauthorised parties from snooping or manipulating data in transit. In the context of healthcare, this means that medical data sent between medical devices, hospital information systems, or other healthcare entities remains protected at all times.
Pseudonymisation is a technique that transforms data into a form that is unrecognisable except to those with the decryption key. In a medical context, this means that the patient’s identifying information can be masked, yet still be useful for medical data analysis and processing. In this way, the data can be used for research or analysis purposes without compromising the privacy of the individual concerned.
Multi-party computing (MPC) is a technique that allows multiple parties to collaborate on data processing without having to disclose the raw data to other parties. In a medical context, this means that multiple hospitals or healthcare institutions can collaborate in calculating statistics or analysing trends from their patient data without the need to transfer the actual data. Not only does this increase the privacy of patient data, but it also enables greater collaboration in medical research and the development of predictive models.
The importance of using advanced cryptographic techniques is also seen in the need for reliable and robust security systems in the Internet of Medical Things (IoMT) era. IoMT systems enable the collection of medical data from various connected devices, such as medical sensors or health monitoring devices, all of which require strong protection from cyberattacks and security breaches.
By continuing to develop and apply these advanced cryptographic techniques, healthcare organisations can ensure that sensitive medical data remains secure and patient privacy is maintained, while harnessing the immense potential of data to improve healthcare, medical research and innovation in healthcare.
4) Development of Secure Communication Protocols.
Developing secure communication protocols is one of the crucial solutions to improve the security and privacy of patient data. In an increasingly technology-dependent healthcare environment, such as the Internet of Medical Things (IoMT) and electronic medical record (EMR) systems, the need for robust data protection has become even more pressing.
Secure communication protocols refer to rules and technologies designed to protect medical data during transmission between devices or systems. The goal is to prevent eavesdropping attacks and data manipulation by unauthorized parties when data moves from one point to another.
One important approach in developing secure communication protocols is to use peer-to-peer (P2P) technology. This technology eliminates the need for a central point that is vulnerable to attacks, as data does not need to pass through a single central server. Instead, each device on the network has the ability to communicate directly with each other, thus improving security by reducing potential points of vulnerability.
In addition, a secure communication protocol should also consider the use of strong encryption technology. Encryption ensures that data sent over the network can only be read by designated recipients who have the correct decryption key. This technique not only protects medical data from unauthorized access, but also ensures data integrity, i.e. it ensures that the data is not altered or manipulated during the transmission process.
In the context of IoMT, where connected medical devices are constantly transmitting data to a central system or between other devices, secure communication protocols are essential. This is because the transmitted medical data is often highly sensitive and can contain personal information that is vulnerable to privacy breaches if not properly protected.
The development of secure communication protocols must also consider the issue of latency (delay) in communication. Particularly in the context of real-time or urgent healthcare use, delays in data transmission can have a serious impact on clinical decisions and responses to patient conditions. Therefore, the designed protocol must be efficient and capable of handling large amounts of data without compromising security or speed.
By developing secure communication protocols and strengthening their security infrastructure, healthcare organizations can maintain patient trust, improve healthcare efficiency, and drive innovation in the use of technology to support better healthcare overall.
Translated with DeepL.com (free version)
5) Regulatory Compliance and Security Audits.
Complying with applicable regulations such as HIPAA in the United States, GDPR in the European Union, and Privacy Act in Australia, is essential to ensure the security and privacy of medical data. These regulations set strict standards for data management, including requirements for informed consent, secure data transfer, and proper data processing. Periodic security audits and assessments should be conducted to ensure that all health systems meet the set standards and remain protected from the latest threats.