Submitted:
08 July 2024
Posted:
10 July 2024
You are already at the latest version
Abstract
Keywords:
I. Introduction
II. Complexities in IoT Software Engineering to Thrive in the Complicated World of Internet of Things
A. Characteristics of IoT Applications
B. Need for Software Engineering Practices
C. Overview of Software Engineering Phases
III. Challenges in IoT Software Engineering
A. Scalability and Solutions
B. Security Measures
C. Opportunities and Advancements
- 1.
- Cross-Domain Development Tools
- 2.
- Simulation Tools and Testbeds
- 3.
- Penetration Testing
IV. Challenges in Software Engineering for IoT Applications
A. Resource Constraints
B. Heterogeneity of Devices and Protocols
- 1.
- Diverse Hardware and Software Characteristics: The IoT ecosystem comprises diverse devices, each with unique hardware specs, operating systems, and software setups. This diversity complicates software development, deployment, and upkeep, requiring developers to accommodate individual device characteristics. Considering potential compatibility issues stemming from hardware, sensor, and communication changes is crucial throughout application development.
- 2.
- Communication Protocols: IoT devices utilize diverse communication protocols like MQTT, CoAP, and HTTP for inter-device and backend communication. Achieving seamless communication and data exchange across networks demands overcoming compatibility and interoperability barriers among protocols. Careful selection and configuration of protocols are essential to meet application requirements and constraints, considering factors like latency, bandwidth utilization, and security.
C. Security Concerns
D. Data Management
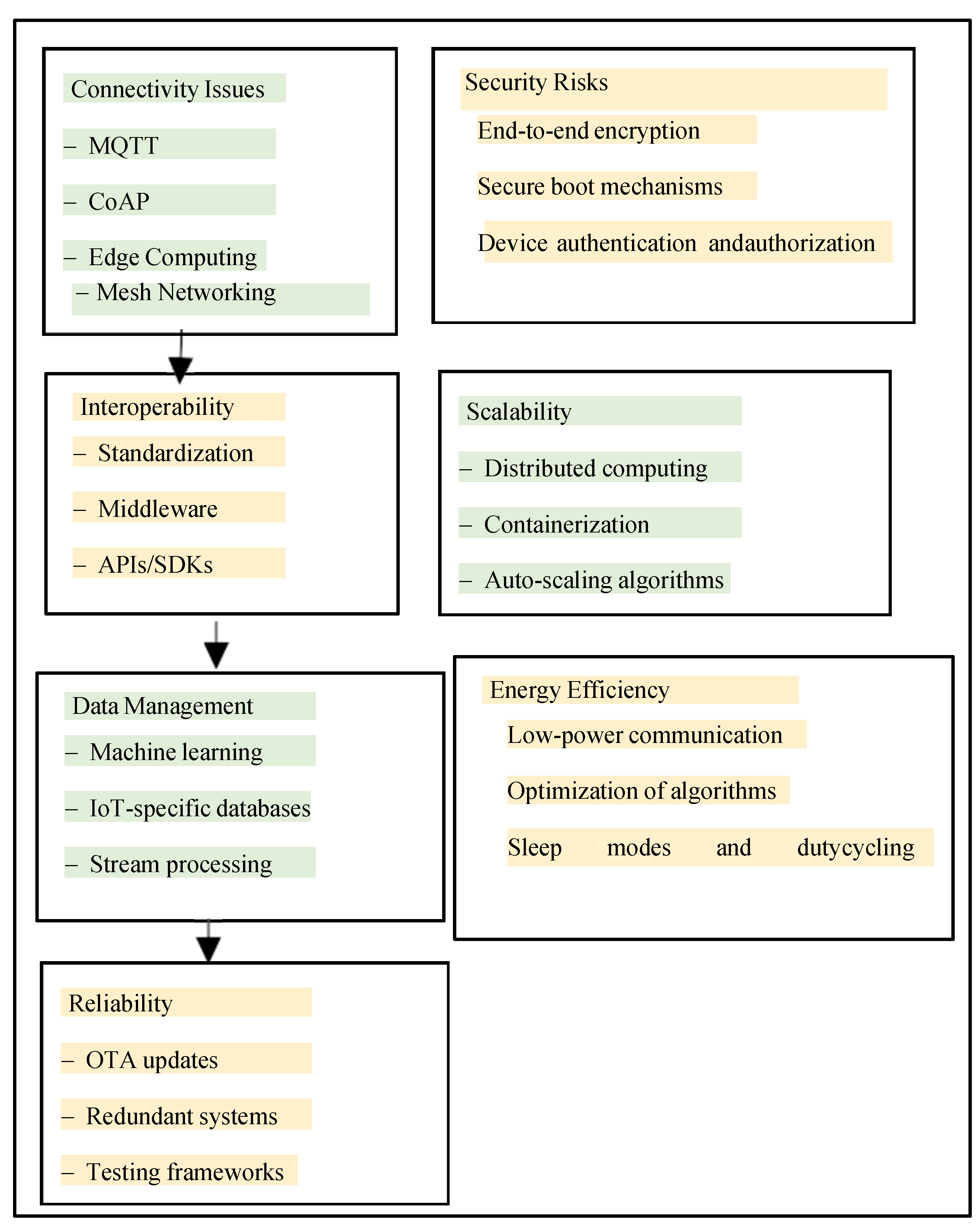
| Challenge/ Opportunity |
Advancements |
|---|---|
|
Connectivity Issues |
• Development of lightweight communication protocols such as MQTT and CoAP • Integration of edge computing to reduce data transmission • Implementation of mesh networking for enhanced coverage and reliability |
|
Security Risks |
• Adoption of end-to-end encryption techniques • Integration of secure boot mechanisms • Implementation of device authentication and authorization protocols |
|
Interoperability |
• Standardization efforts by organizations like IEEE and IETF • Development of middleware solutions for protocol translation • Use of APIs and SDKs for seamless integration with different platforms |
|
Scalability |
• Employment of containerization technologies like Docker and Kubernetes • Implementation of distributed computing architectures • Utilization of auto-scaling algorithms for resource management |
|
Data Management |
• Deployment of IoT-specific databases like MongoDB and InfluxDB • Utilization of stream processing frameworks such as Apache Kafka and Apache Flink • Integration of machine learning for real-time data analytics and anomaly detection |
|
Energy Efficiency |
• Optimization of software algorithms for reduced energy consumption • Utilization of low-power communication protocols like LoRaWAN • Implementation of sleep modes and duty cycling to minimize energy usage |
|
Reliability |
• Implementation of redundant systems for fault tolerance • Adoption of over-the-air (OTA) updates for remote maintenance • Employment of testing frameworks like JUnit and Mockito for robustness testing |
V. Artificial Intelligence and Machine Learning
A. Enhancing Functionality and Performance
B. Model-Driven Development
C. Domain-Specific Language (DSL)
D. AI and Machine Learning Integration
E. Security Frameworks
VI. System Architecture for IoT Software Engineering
A. Importance of System Architecture
B. Main Layers
- 1.
- Device Layer
- 2.
- Network Layer
- 3.
- Cloud Layer
- 4.
- Application Layer
| Application Layer |
| ✓ Machine Learning Integration: Real-time data analytics, predictive maintenance, anomaly detection ✓ Over-the-Air (OTA) Updates: Remote updates for software and firmware ✓ User Interfaces: Mobile apps, web dashboards ✓ Domain-Specific Languages (DSLs): Streamlined development |
| Cloud Layer |
| ✓ Cloud Storage: Scalable databases like MongoDB, InfluxDB ✓ Stream Processing: Frameworks like Apache Kafka, Apache Flink ✓ Data Analytics: Advanced analytics platforms, machine learning models ✓ Security Frameworks: End-to-end encryption, secure boot mechanisms, authentication and authorization protocols |
| Network Layer |
| ✓ Communication Protocols: MQTT, CoAP, HTTP ✓ Edge Computing: Data processing closer to source ✓ Mesh Networking: Enhanced coverage and reliability |
| ✓ Standardization and Interoperability: Middleware solutions, APIs, SDKs |
| Device Layer |
| ✓ Embedded Software: Firmware updates, real-time responsiveness ✓ Resource Optimization: Low-power algorithms, sleep modes, duty cycling ✓ Device Authentication: Ensuring secure device identities ✓ Redundant Systems: Ensuring fault tolerance and reliability |
VII. Future Directions
A. Evolving Nature of IoT Systems
- 1.
- Interoperability and Standardization: An ever- increasing number of Internet of Things (IoT) devices and platforms necessitates standardisation and interoperability to guarantee smooth integration and communication between various systems. To facilitate interoperability across various devices and platforms, future IoT systems would most likely embrace standardised frameworks and protocols
- 2.
- Edge Computing: A rising trend towards edge computing, which involves processing and analysing data closer to the source, is being driven by the ever-increasing volume of data created by IoT devices. Internet of Things (IoT) applications that are sensitive to latency and have bandwidth constraints can benefit from edge computing since it decreases latency, bandwidth utilisation, and dependence on centralised cloud infrastructure [6].
- 3.
- AI and Machine Learning: Improving the intelligence and functionality of IoT systems is anticipated to be largely driven by the integration of AI and ML approaches. Automated decision-making, anomaly detection, predictive maintenance, and real-time data analytics are some of the expected uses of AI and ML algorithms in future Internet of Things systems [7].
- 4.
- Security and Privacy: Concerns about security and privacy are likely to continue to take centre stage as the number of Internet of Things (IoT) devices continues to grow and vital infrastructure becomes more linked. Encryption, authentication, access control, and secure firmware upgrades are some of the strong security features that future IoT devices will need to include to safeguard data from cyber threats and keep it private [1].
B. Ongoing Software and Firmware Updates
- 1.
- Compatibility Testing: Prior to distributing software and firmware upgrades, compatibility testing should be carried out to confirm that the updates are compatible with the hardware, software, and configurations that are already in place. Compatibility testing is a useful tool for identifying potential conflicts, dependencies, and problems that may occur during the process of updating.
- 2.
- Over-the-Air (OTA) Updates: OTA updates allow for the remote deployment of software and firmware updates to Internet of Things devices, thereby reducing the need for manual intervention. However, in order to avoid unauthorised access and tampering, over-the-air (OTA) updates would need to include sophisticated security features. The implementation of secure over-the-air (OTA) protocols, encryption, and authentication techniques is recommended in order to safeguard against potential security violations.
- 3.
- Rollback Mechanisms: Rollback procedures: In the event that upgrades are unsuccessful or compatibility problems arise, rollback procedures should be in place so that the prior version of software or firmware can be reverted to. Rollback mechanisms serve as a safety net in the event that unanticipated problems arise during the process of updating, thereby ensuring the continuity of operations and reducing the amount of downtime that occurs.
- 4.
- Testing in Real-world Environments: Software and firmware updates should be tested in real-world scenarios in order to simulate realistic usage situations and discover any issues that may develop in production deployments. This must be done in order to ensure that the software and firmware are functioning properly. It is important to confirm the performance, dependability, and stability of updates before they are released to a wider audience. Real-world testing helps validate these aspects.
- 5.
- User Communication and Feedback: It is essential to maintain effective communication with end-users throughout the update process in order to provide them with information regarding the intentions, advantages, and potential consequences of upgrades. In order to gain insights into the user experience, identify any faults or concerns, and prioritise future improvements based on user demands and preferences, it is important to solicit feedback from users.
VIII. Conclusion
A. Summary of Key Findings
B. Implications of Future IoT Applications
C. Final Thoughts and Recommendations
References
- Celik, Z.B., Fernandes, E., Pauley, E., Tan, G. and McDaniel, P., 2019. Program analysis of commodity IoT applications for security and privacy: Challenges and opportunities. ACM Computing Surveys (CSUR), 52(4), pp.1-30. [CrossRef]
- Bandyopadhyay, D. and Sen, J., 2011. Internet of things: Applications and challenges in technology and standardization. Wireless personal communications, 58, pp.49-69. [CrossRef]
- Wang, M. and Mittal, A., 2024. Innovative Solutions: Cloud Computing and AI Synergy in Software Engineering. Asian American Research Letters Journal, 1(1).
- Kamruzzaman, M.M., Alrashdi, I. and Alqazzaz, A., 2022. New opportunities, challenges, and applications of edge-AI for connected healthcare in internet of medical things for smart cities. Journal of Healthcare Engineering, 2022. [CrossRef]
- Sallam, K., Mohamed, M. and Mohamed, A.W., 2023. Internet of Things (IoT) in supply chain management: challenges, opportunities, and best practices. Sustainable Machine Intelligence Journal, 2, pp.3- 1. [CrossRef]
- Chen, L. and Li, M., 2024. AI-Enabled Cloud Platforms: Revolutionizing Software Development. Asian American Research Letters Journal, 1(1).
- Pan, Y. and Zhang, L., 2021. Roles of artificial intelligence in construction engineering and management: A critical review and future trends. Automation in Construction, 122, p.103517. [CrossRef]
- Shahinmoghadam, M. and Motamedi, A., 2019, May. Review of BIM- centred IoT deployment–state of the art, opportunities, and challenges. In Proceedings of the 36th International Symposium on Automation and Robotics in Construction (ISARC 2019) (pp. 1268-1275).
- Rossi, M. and Russo, G., 2024. Innovative Solutions: Cloud Computing and AI Synergy in Software Engineering. MZ Journal of Artificial Intelligence, 1(1), pp.1-9.
- Lone, A.N., Mustajab, S. and Alam, M., 2023. A comprehensive study on cybersecurity challenges and opportunities in the IoT world. Security and Privacy, 6(6), p.e318. [CrossRef]
- Rahim, M.A., Rahman, M.A., Rahman, M.M., Asyhari, A.T., Bhuiyan,.
- M.Z.A. and Ramasamy, D., 2021. Evolution of IoT-enabled.
- connectivity and applications in automotive industry: A review. Vehicular Communications, 27, p.100285. [CrossRef]
- Debnath, D. and Chettri, S.K., 2021. Internet of Things: Current Research, Challenges, Trends and Applications. In Applications of Artificial Intelligence in Engineering: Proceedings of First Global Conference on Artificial Intelligence and Applications (GCAIA 2020) (pp. 679-694). Springer Singapore.
- Shafik, W., 2024. Blockchain-Based Internet of Things (B-IoT): Challenges, Solutions, Opportunities, Open Research Questions, and Future Trends. Blockchain-based Internet of Things, pp.35-58.
- Banafaa, M., Shayea, I., Din, J., Azmi, M.H., Alashbi, A., Daradkeh,.
- Y.I. and Alhammadi, A., 2023. 6G mobile communication technology: Requirements, targets, applications, challenges, advantages, and opportunities. Alexandria Engineering Journal, 64, pp.245-274. [CrossRef]
- Pool, R., van Berkel, J., van den Braak, S., Harbers, M. and Bargh, M.S., 2020. The internet of things in a smart society: How government policy can help seize opportunities and mitigate threats. Beyond Smart and Connected Governments: Sensors and the Internet of Things in the Public Sector, pp.25-48.
- Müller, O. and Weber, S., 2024. AI-Enabled Cloud Platforms: Revolutionizing Software Development. MZ Journal of Artificial Intelligence, 1(1), pp.1-10.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




