Submitted:
13 July 2024
Posted:
16 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Work
2.1. Traditional Transaction Monitoring System
2.2. Traditional Finance Relies on Mature Traditional Regulatory Standards and Means
2.3. Common Problems and Challenges of Traditional Financial Transaction Supervision
3. Application of AI Fraudulent Behaviour Prediction
3.1. Traditional fraud detection methods
3.2. Fraud detection with AI
3.3. Using Artificial Intelligence and Machine Learning Algorithms in Fraud Detection
4. Methodology
4.1. Experimental Design
4.2. Data Processing
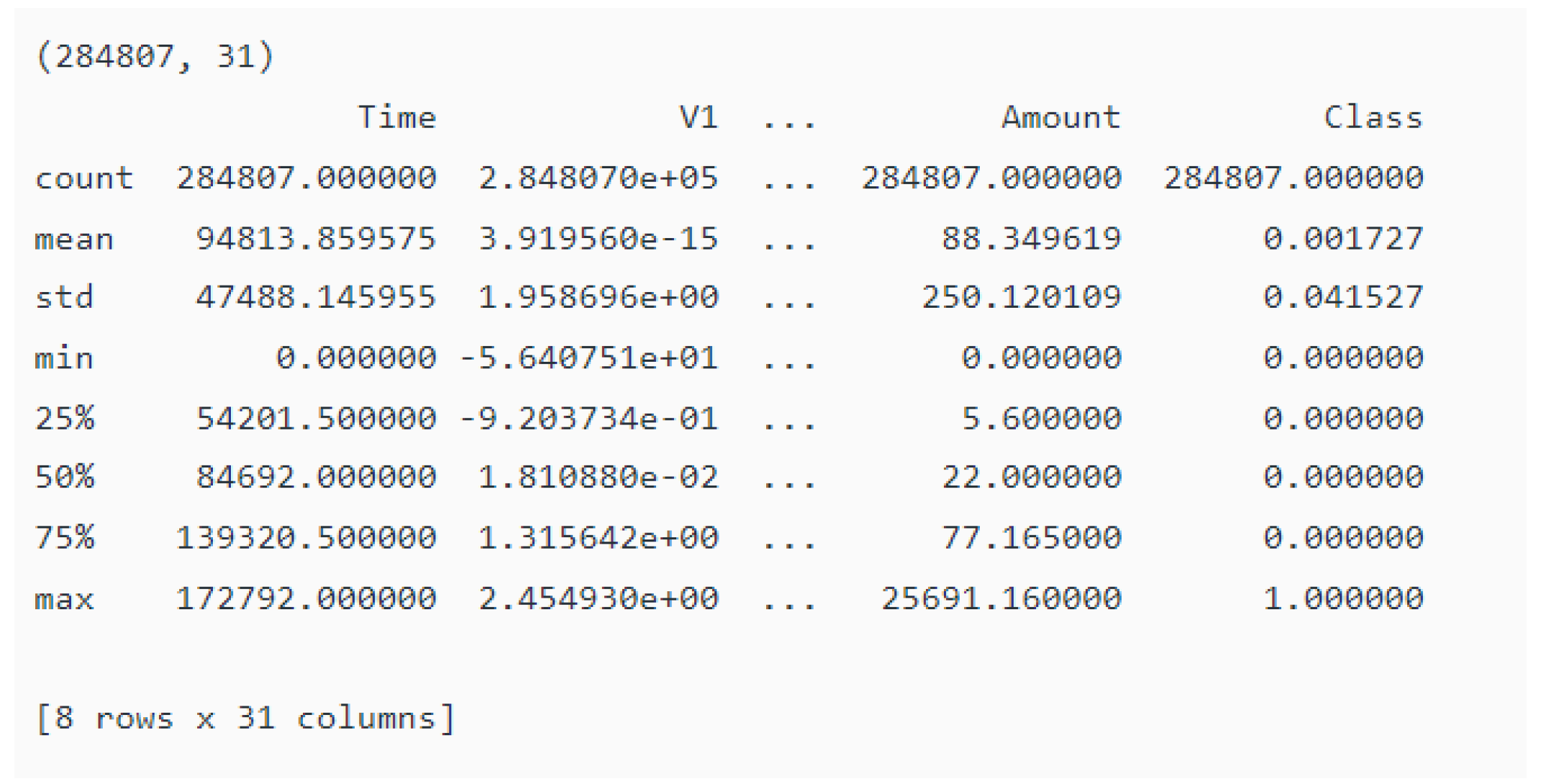
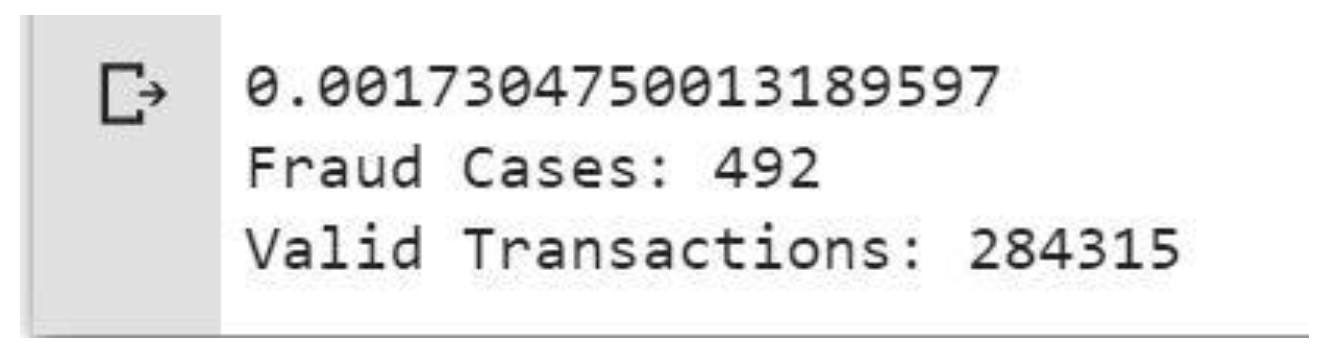
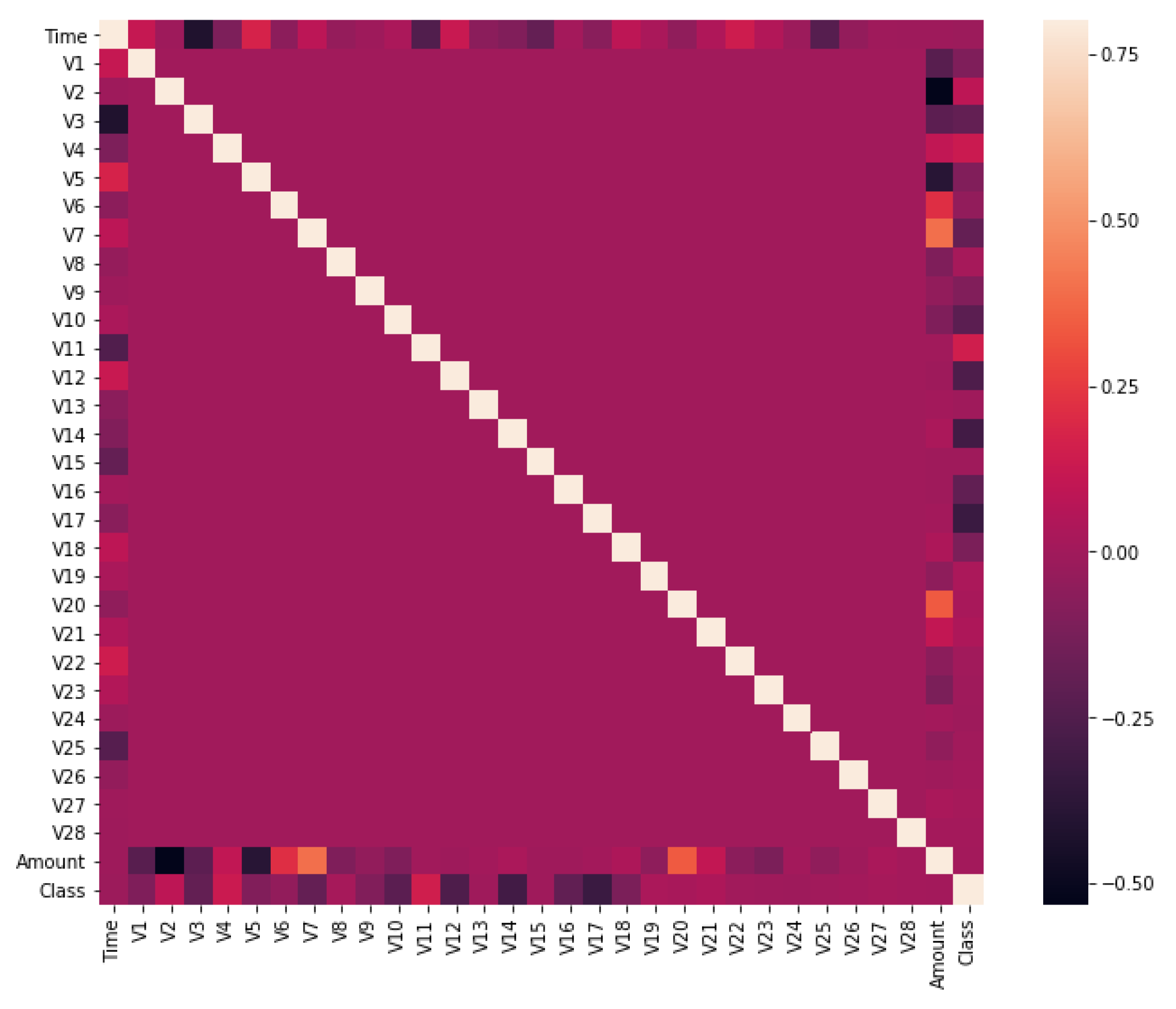
4.3. Plot Correlation Matrix
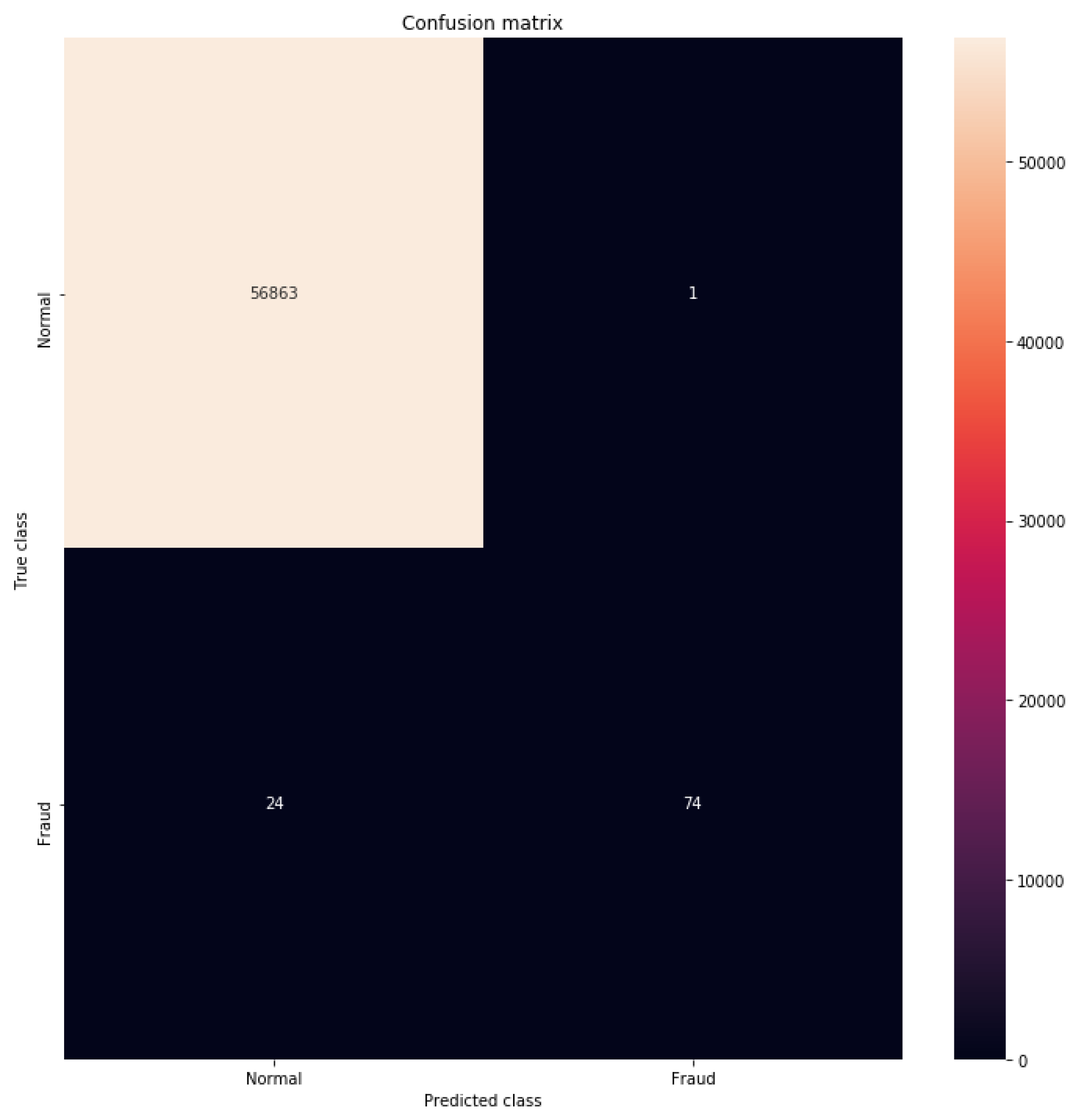
4.4. Experimental Result
4.5. Experimental Discussion
5. Conclusion
References
- Shi, Y.; Yuan, J.; Yang, P.; Wang, Y.; Chen, Z. Implementing intelligent predictive models for patient disease risk in cloud data warehousing. Appl. Comput. Eng. 2024, 67, 34–40. [Google Scholar] [CrossRef]
- Zhan, T.; Shi, C.; Shi, Y.; Li, H.; Lin, Y. Optimization techniques for sentiment analysis based on LLM (GPT-3). Appl. Comput. Eng. 2024, 67, 41–47. [Google Scholar] [CrossRef]
- Lin, Y.; Li, A.; Li, H.; Shi, Y.; Zhan, X. GPU-Optimized Image Processing and Generation Based on Deep Learning and Computer Vision. J. Artif. Intell. Gen. Sci. (JAIGS) ISSN:3006-4023 2024, 5, 39–49. [Google Scholar] [CrossRef]
- Chen, Z.; Lou, Y.; Wang, B.; Lei, H.; Yang, P. Application of Cloud-Driven Intelligent Medical Imaging Analysis in Disease Detection. J. Theory Pr. Eng. Sci. 2024, 4, 64–71. [Google Scholar] [CrossRef]
- Wang, B.; Lei, H.; Shui, Z.; Chen, Z.; Yang, P. Current State of Autonomous Driving Applications Based on Distributed Perception and Decision-Making. World J. Innov. Mod. Technol. 2024, 7, 15–22. [Google Scholar] [CrossRef] [PubMed]
- Jiang, W.; Qian, K.; Fan, C.; Ding, W.; Li, Z. Applications of generative AI-based financial robot advisors as investment consultants. Appl. Comput. Eng. 2024, 67, 28–33. [Google Scholar] [CrossRef]
- Yang, J.; Qin, H.; Por, L.Y.; Shaikh, Z.A.; Alfarraj, O.; Tolba, A.; Elghatwary, M.; Thwin, M. Optimizing diabetic retinopathy detection with inception-V4 and dynamic version of snow leopard optimization algorithm. Biomed. Signal Process. Control. 2024, 96. [Google Scholar] [CrossRef]
- Fan, C.; Li, Z.; Ding, W.; Zhou, H.; Qian, K. Integrating artificial intelligence with SLAM technology for robotic navigation and localization in unknown environments. Appl. Comput. Eng. 2024, 67, 22–27. [Google Scholar] [CrossRef]
- Guo, L.; Li, Z.; Qian, K.; Ding, W.; Chen, Z. Bank Credit Risk Early Warning Model Based on Machine Learning Decision Trees. Journal of Economic Theory and Business Management 2024, 1(3), 24–30. [Google Scholar]
- Li, Z.; Fan, C.; Ding, W.; Qian, K. Robot Navigation and Map Construction Based on SLAM Technology. World J. Innov. Mod. Technol. 2024, 7, 8–14. [Google Scholar] [CrossRef]
- Fan, C.; Ding, W.; Qian, K.; Tan, H.; Li, Z. Cueing Flight Object Trajectory and Safety Prediction Based on SLAM Technology. J. Theory Pr. Eng. Sci. 2024, 4, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Ding, W.; Tan, H.; Zhou, H.; Li, Z.; Fan, C. Immediate traffic flow monitoring and management based on multimodal data in cloud computing. Appl. Comput. Eng. 2024, 71, 1–6. [Google Scholar] [CrossRef]
- Zhou, C.; Zhao, Y.; Liu, S.; Zhao, Y.; Li, X.; Cheng, C. (2024). Research on Driver Facial Fatigue Detection Based on Yolov8 Model.
- Xin, Q.; Xu, Z.; Guo, L.; Zhao, F.; Wu, B. IoT traffic classification and anomaly detection method based on deep autoencoders. Appl. Comput. Eng. 2024, 69, 64–70. [Google Scholar] [CrossRef]
- Yang, T.; Li, A.; Xu, J.; Su, G.; Wang, J. Deep learning model-driven financial risk prediction and analysis. Appl. Comput. Eng. 2024, 67, 54–60. [Google Scholar] [CrossRef]
- Zhou, C.; Zhao, Y.; Zou, Y.; Cao, J.; Fan, W.; Zhao, Y.; Cheng, C. Predict Click-Through Rates with Deep Interest Network Model in E-commerce Advertising. arXiv 2024, arXiv:2406.10239. [Google Scholar]
- He, Z.; Shen, X.; Zhou, Y.; Wang, Y. Application of K-means clustering based on artificial intelligence in gene statistics of biological information engineering. BIC 2024: 2024 4th International Conference on Bioinformatics and Intelligent Computing (pp. 468-473).
- Gong, Y.; Zhu, M.; Huo, S.; Xiang, Y.; Yu, H. (2024, March). Utilizing Deep Learning for Enhancing Network Resilience in Finance. In 2024 7th International Conference on Advanced Algorithms and Control Engineering (ICAACE) (pp. 987-991). IEEE.
- Zhou, C. , Zhao, Y., Cao, J., Shen, Y., Gao, J., Cui, X.,... & Liu, H. (2024). Optimizing search advertising strategies: Integrating reinforcement learning with generalized second-price auctions for enhanced ad ranking and bidding. arXiv:2405.13381.
- Tian, J.; Li, H.; Qi, Y.; Wang, X.; Feng, Y. Intelligent medical detection and diagnosis assisted by deep learning. Appl. Comput. Eng. 2024, 64, 121–126. [Google Scholar] [CrossRef]
- Yang, P.; Chen, Z.; Su, G.; Lei, H.; Wang, B. Enhancing traffic flow monitoring with machine learning integration on cloud data warehousing. Appl. Comput. Eng. 2024, 67, 15–21. [Google Scholar] [CrossRef]
- Restrepo, D.; Wu, C.; Cajas, S. A.; Nakayama, L. F.; Celi, L. A. G.; Lopez, D. M. (2024). Multimodal Deep Learning for Low-Resource Settings: A Vector Embedding Alignment Approach for Healthcare Applications. medRxiv, 2024-06.
- Cajas, S. A. , Restrepo, D., Moukheiber, D., Kuo, K. T., Wu, C., Chicangana, D. S. G.,... & Celi, L. A. A multi-modal satellite imagery dataset for public health analysis in colombia.
- hang H, Diao S, Yang Y, Zhong J, Yan Y. Multi-scale image recognition strategy based on convolutional neural network. Journal of Computing and Electronic Information Management. 2024 Apr 30;12(3):107-13.
- Zhou, Y.; Zhan, T.; Wu, Y.; Song, B.; Shi, C. RNA secondary structure prediction using transformer-based deep learning models. Appl. Comput. Eng. 2024, 64, 88–94. [Google Scholar] [CrossRef]
- Liu, B.; Cai, G.; Ling, Z.; Qian, J.; Zhang, Q. Precise positioning and prediction system for autonomous driving based on generative artificial intelligence. Appl. Comput. Eng. 2024, 64, 42–49. [Google Scholar] [CrossRef]
- Cui, Z.; Lin, L.; Zong, Y.; Chen, Y.; Wang, S. Precision gene editing using deep learning: A case study of the CRISPR-Cas9 editor. Appl. Comput. Eng. 2024, 64, 134–141. [Google Scholar] [CrossRef]
- Rosner, B.; Tamimi, R.M.; Kraft, P.; Gao, C.; Mu, Y.; Scott, C.G.; Winham, S.J.; Vachon, C.M.; Colditz, G.A. Simplified Breast Risk Tool Integrating Questionnaire Risk Factors, Mammographic Density, and Polygenic Risk Score: Development and Validation. Cancer Epidemiology Biomarkers Prev. 2020, 30, 600–607. [Google Scholar] [CrossRef] [PubMed]
- Wang, B.; He, Y.; Shui, Z.; Xin, Q.; Lei, H. Predictive optimization of DDoS attack mitigation in distributed systems using machine learning. Appl. Comput. Eng. 2024, 64, 95–100. [Google Scholar] [CrossRef]
- Zhan, X.; Ling, Z.; Xu, Z.; Guo, L.; Zhuang, S. Driving Efficiency and Risk Management in Finance through AI and RPA. Unique Endeavor in Business & Social Sciences 2024, 3, 189–197. [Google Scholar]
- Xu, Z.; Guo, L.; Zhou, S.; Song, R.; Niu, K. Enterprise Supply Chain Risk Management and Decision Support Driven by Large Language Models. Applied Science and Engineering Journal for Advanced Research 2024, 3, 1–7. [Google Scholar]
- Song, R.; Wang, Z.; Guo, L.; Zhao, F.; Xu, Z. (2024). Deep Belief Networks (DBN) for Financial Time Series Analysis and Market Trends Prediction.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



