1. Introduction
The continuous growth of technological capabilities of the digital era and the direct impact of Information and Communication Technologies (ICT) on contemporary social processes are the basis of the continuous development of modern society based on global informatization. An example in this direction is carried out in [
1] discussion of the problems related to the growing role of informatization and the impact on global poverty, including the relationship between the two processes. The relationship between informatization and globalization gives rise to various problems in modern society, as discussed in [
2]. As a result of informatization and globalization, the growing requirements for ensuring personal (digital) privacy [
3], as well as for the level of competence of users of services in the network space (digital literacy) [
4] must be considered. In the last cited article different sub-section of literacy related to the computer0supported education are determined – digital literacy (DL), technological literacy (TL), and internet literacy (IL). The article concludes that the three types of literacy jointly influence the correct organization of digital education and makes relevant suggestions. A systematic review of the first type DL based on qualitative methodology is presented in [
5], where four major themes connected to qualitative content understanding are determined – digital literacy, digital competencies, digital skills, and digital thinking. The article proposes recommendations for adequate research in the real life.
Different basic requirements to the information society and globalization define a continuous process of social, economic, scientific, and technical development of the social information environment [
6] with the aim of creating opportunities to satisfy people’s informational needs while realizing the rights of citizens, authorities, and organizations. As an example, the last cited article raises the question of whether the old models of social communications in the digital space are still relevant, proposing a horizontal two-stage flow model based on the new media methodology. It is emphasized that this need is dictated by the growing spread of information and messages in social movements. Regardless of the applied model of social communication and information exchange, the main issue that is raised is the protection of personal space (privacy), including personal data, which requires a good knowledge of the rules and requirements (security literacy) [
7] including the main problem of the privacy in the digital environment of Internet of Things [
8].
A discussion of globalization, informatization and information society and the specific features of the privacy and data protection (in historical and contemporary aspects) are discussed in this article. The main technological aspect and components of the digital age (digital society) are presented and the relation between them is determined.
2. Globalization of the Contemporary Society
Globalization as a major feature of digital society is based on the total informatization as a process of expanding the possibilities and application of ICT and the opportunities for people to communicate through the global network and share different information. This is confirmed by the entry of new digital technologies into public life, such as cloud computing, intelligent mobile communications, intelligent process management applications (smart home, smart city, smart transports, etc.).
A common definition of globalization defines it as the continuous movement and exchange of ideas, goods, services, information, technology, and different cultural practices. This raises the question of the relationship between informatization and digitalization, as a discussion of the problems in this direction in modern society is presented in [
9]. Additionally, [
10] states that globalization directly affects the development of modern science and technology, emphasizing that the development and application of ICT, in turn, affect globalization trends with the transition from offline to online processes.
Globalization of the contemporary economy is characterized by relations increasing in the national and international interconnections which is related to the level of so called “internetalization”. This term is introduced in several publications to present the important role of Internet. This is supported by remote access capabilities to various resources, distributed data functionalities, and request flow management in distributed service systems [
11], creating a fully integrated world. In various articles, globalization is discussed in a concrete area, which does not prevent new concepts from being defined, such as the Energy Internet of Things (EIoT) directly connected to specific opportunities for example configuration of the final cloud of a terminal, virtualization of data flow and resources, big data analysis (BDA) and heterogeneous spatiotemporal data. This allows, in addition to the specific development of applications for equipment condition assessment, digital monitoring and diagnostics and building a smart city, to formulate recommendations for the development of data science, digitalization of enterprises and a smart city.
Based on the various discussions, it is possible to analyze digitalization and informatization as two different approaches to shaping modern society, defining digitalization as the main approach to modernize its management, but confirming the advantages of informatization for general globalization. The result of this statement are topics with the addition "electronic" or "digital", as well as new concepts starting with "smart-", "intelligent", "Cyber-physical", "-4.0" (from "Industry 4.0"), etc. In particular, the term "Industry 4.0", describing the fourth industrial revolution with a perspective until 2025, includes different contemporary technologies such as cloud / mobile cloud computing, Internet of Things (IoT), Cyber-physical systems (CPS), big data analysis (BDA), etc. One suggested conclusion in the literature is that technological development based on computerization and digitalization determines the so-called third generation of social development, while informatization connects with a subsequent fourth generation, allowing embedding, sharing, and editing of information resources directly in the network space. The transition from digitalization to informatization is associated with the latest data technologies and machine learning algorithms that create stubborn challenges in the digital space.
It can be said that the continuous growth of technological capabilities of the digital era and the direct impact of ICT on modern social processes are the basis of the continuous development of modern society based on global informatization. As a consequence of informatization and globalization, the increase in possible attacks for breaching information security [
12] should be considered, which leads to an increase in the requirements for ensuring personal (digital) privacy [
7]. These requirements are directly related to the need for competence of users of services in the network space (digital literacy). This determines the need to increase the global processes in IS (social, economic, scientific, technological, etc.) and development of actual contemporary technical environments to support all people’s information needs based on the protection of citizens’ rights, including privacy, authorities, and data protection.
3. Main Components of the Digital Age
3.1. Specific Features of Informatization
Informatization is defined by UNESCO before several years as processes for “development and application of methods and means of collecting, transforming, storing and disseminating information, enabling the formation of new knowledge…”. The features of the informatization process are discussed in [
13], where it is stated that it accelerates the new industries based on contemporary technological innovation, facilitates and actualization. In addition, it can be stated that based on the global informatization of society, the functions of employment are being transformed and the type and goals of scientific research are changing.
The first introduction of the term "informatization" into the public sphere was made in the late 1970s in two publications (by Marc Porat, 1977 and in by Simon Nora and Alain Minc, 1978) to define the role of information in the industry. After some years G. Wang (1994) associated this new term with the processes of popularizing information and accelerating its dissemination in the contemporary society. This is extended in the end of the 20th and the beginning of the 21st century whit including the digital information processing and "World Wide Web" in social development. This relates to development of global digital infrastructure for communication and dissemination of specific information resources which increase the society computerization. Achieving this goal is associated with expanding the functional capabilities of the network space and developing adequate policies for managing resources and communications in it, which requires ensuring the effectiveness of interaction between objects in the global network and justifies the meaning of the word "internetalization".
A definition of UNESCO determines the informatization as a central issue with the main goal of promoting "sustainable human development and building inclusive knowledge societies, and also for enhancing the free flow of information and ideas throughout the world" [
14]. In a general aspect, the term clearly indicates basic requirements for ensuring free expression of opinions, access to information and protection of privacy and personal data in cyberspace. Various publications discuss the features and problems of global informatization and define it as a global technological, socio-economic and cultural process for important changes in the life of the individual. This defines two main theoretical-methodological approaches to informatization.
A technological approach, primarily associated with technical and technological means and tools to support all activities in society, the main components of which have been defined over the years as electronization, meditation, computerization, intellectualization.
A sociological approach reflecting the impact on all spheres of human activity (knowledge, skills, moral, economic, and cultural interests, personal development, etc.). This approach is associated with the introduction of the term "globalization of society".
Modern technologies of a digital society have significantly expanded the understanding of the concept of "
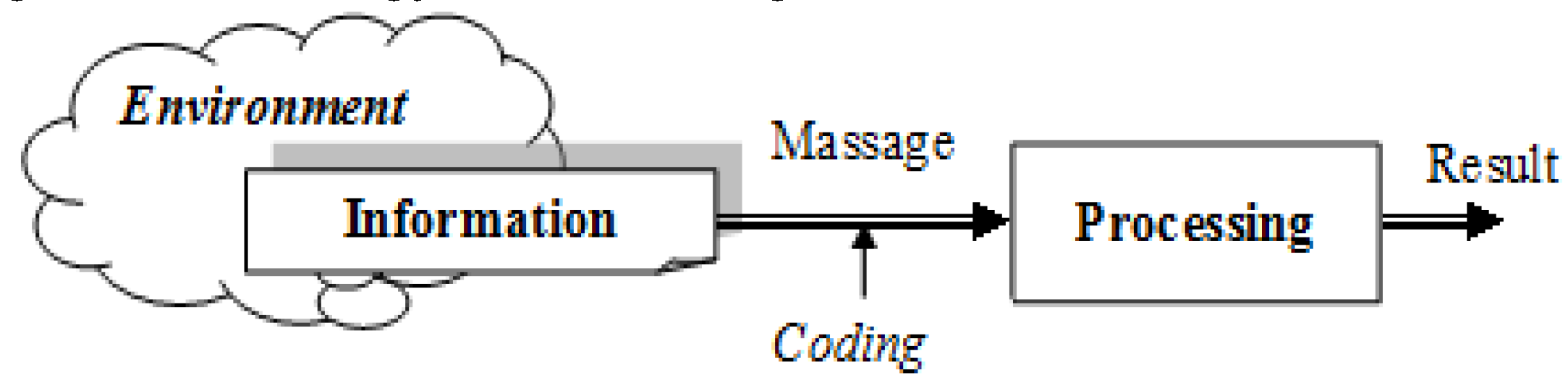
information" as a set of knowledge and information about events and objects, supporting the formation of new knowledge. In a technological aspect, an information environment corresponding to the specifics is used for its maintenance, representing a set of various technical means, as well as organizational, economic and legal mechanisms. The goal is to automate processing of information, its systematization, storage and distribution, which can be summarized as a functional transformation
f:{D}→{R} of elements from the set of input data
{D} into the set of output results
{R}. For its implementation, a computer environment is needed, allowing automation of the process by presenting (encoding) the information objects in the form of messages –
Figure 1. The implementation of information processes and their research in smart homes and cloud computing can be made by using the technology of vector regression [
15].
The formalization in the presentation and research of information processing can be done in several ways, such as based on the theory of finite automata [
16], mathematical description by vector regression [
15], algorithmic presentation in distributed service [
11], etc.
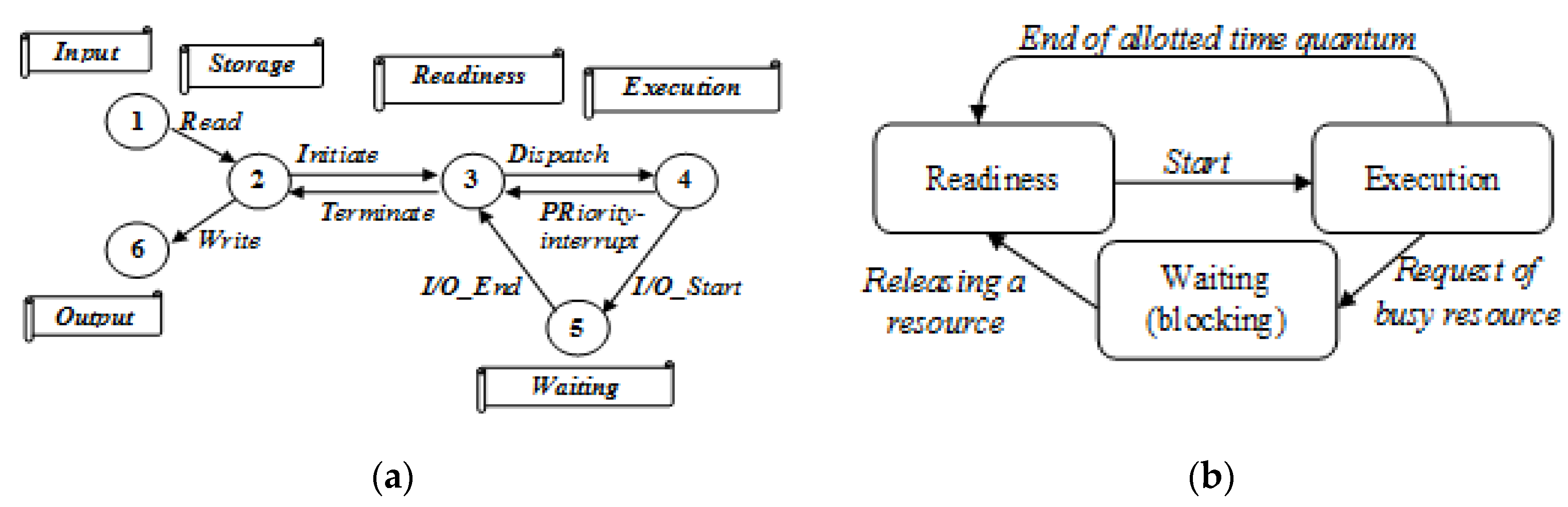
Graph theory provides a useful approach to graphically formalization of processes as a set of states represented as nodes on a directed graph. Based on this approach, a formal model of a basic computing process as a state transition network (STN) is shown in
Figure 2a. Transitions between states are assumed to be instantaneous, and the functional algorithm determines values for system parameters and characteristics. A summary of the processes in a multitasking mode of operation, where active applications (tasks) compete to claim and occupy the available computing resources, is presented in
Figure 2b.
3.2. Creation of Information Technology
Information technology (IT) in a generalized aspect is a development of the term "technology", which is associated with activities for the development, improvement and application of the ways and means (toolkit) for the organization of a given processing (in particular, production). It is implemented by activating and maintaining one or more processes related to actions to transform some object and aimed at achieving a certain goal. The execution of the process is determined by the chosen strategy and is realized through a certain technology. In this sense, during information processing, information processes are generated and implemented based on developed information technology. This defines IT as a set of activities for receiving (collecting), processing, storing, and transforming information objects to ensure human activity and according to the set main purpose and purpose of the obtained results.
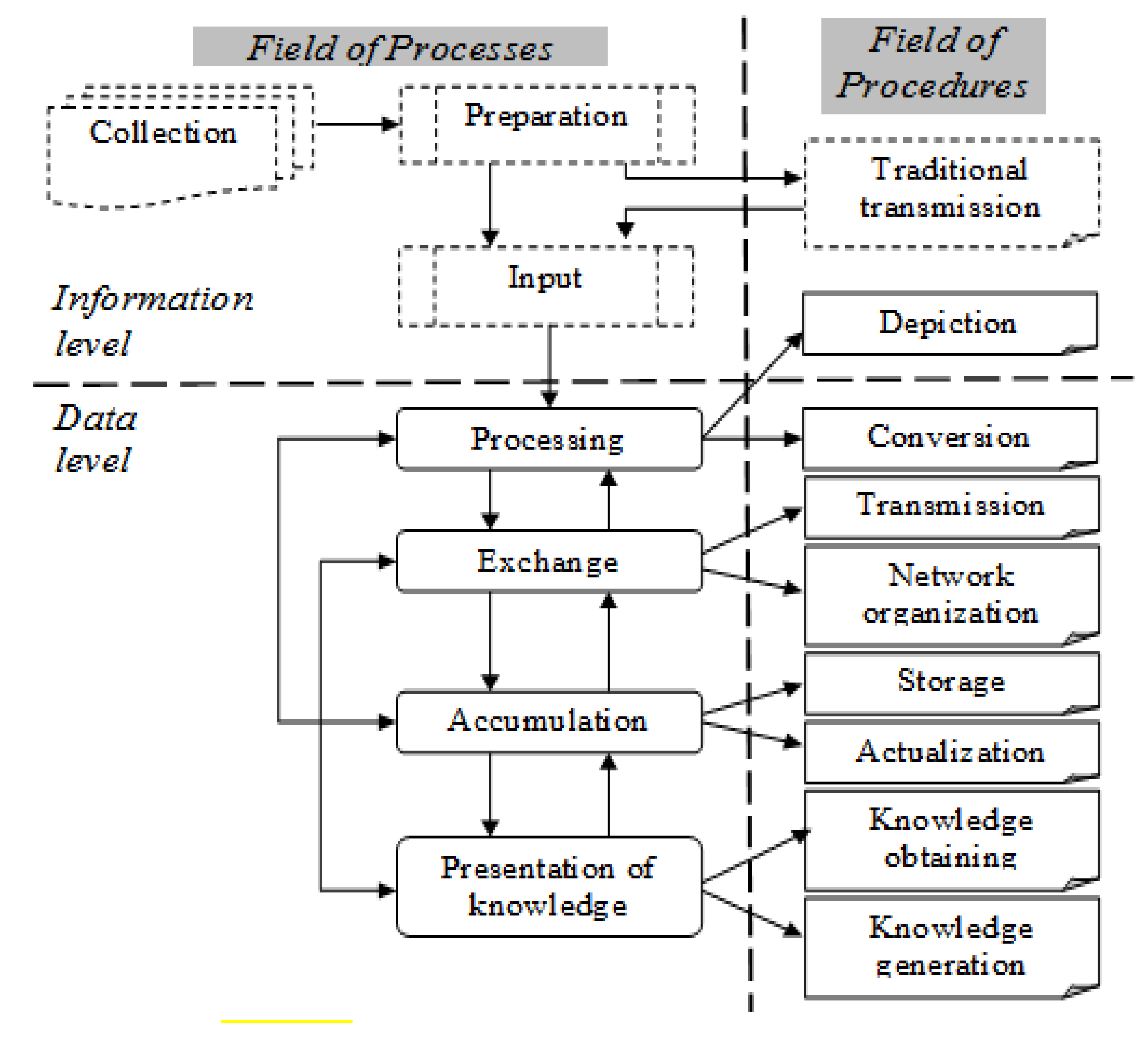
One definition of the purpose of IT is known, as a technology to produce new knowledge for the needs of human needs. This requires correct allocation of the main activities of information processing to unified procedures for purposeful management of information processes. This determines the need to unite the computer and communication processes whit preliminary elements of manual processing. An example of a conceptual model of IT is presented in
Figure 3 with sectors defined in vertical and horizontal direction. The upper horizontal level reflects processes and procedures for the presentation of information in an easily perceptible form (mainly manual activities), and the lower level is associated with computer presentation and data processing. As seen in the concluding process, the highest product of IT is knowledge, which becomes an important strategic resource related to artificial intelligence systems.
Several main characteristics of IT can be summarized:
Expediency (increasing the efficiency of processes);
Integrity (building IT as a complete system);
Modularity (unification of specialized functional modules;
Dynamic development (accelerated development and continuous modification based on modern technologies);
Dynamic development (accelerated development and continuous modification based on modern technologies).
These characteristics are usually reflected through the initial development of a conceptual model, and the actual implementation is based on the so-called logical model for defining the structure and organization of connections.
3.3. Principles and Features of the Information Society
The main task of the Information Society (ISoc) is not only to develop and implement ICT and appropriate software, but also to ensure high efficiency of their application in various fields of science, production, and social life. This determines the central place of information in public relations and orientation of the economy towards digitization based on new knowledge (at the beginning of the 21st century, some authors introduced the concepts of knowledge economy or knowledge society). In this sense, modern ISoc is connected to the global informatization of public and business relations by offering remote access to resources (e-access) and electronic service (e-servicing). The general structuring of ISoc is based on electronization (digitalization) of different spheres as the government at the state or local level (e-governance/e-government), conducting educational processes (e-learning), commercial relationships and business (e-commerce /e-business), bank operations (e-banking), medical support (e-health), etc. The implementation of processes and interactions in society and the economy through the possibilities of the global network and modern ICT is often reflected by the term "Network Society", and citizens are defined as "digital citizens".
It can be assumed that discussions on the model of the modern information society started already in 1962, when Fritz Machlup introduced the term "knowledge industry". Later, in the 70s and 80s of the XX century, the terms "post-industrial society" and "post-modern society", "information economy", "information revolution", etc. were launched. In the 90s of the XX century the idea was confirmed that in the information society, the central resource of the economy is knowledge presented through modern IT and distributed in the global network. At the end of the last century and at the beginning of the 21st century, ISoc was already being talked about as an opportunity to receive information from various geographically distant places and to share it with many users through the possibilities of ICT. Their place and role in the information society is reduced to the following: ✓ effective use of society’s information resources; ✓ optimization and automation of information processes; ✓ active participation in business or in social activities for realization (as a rule) of the most important "intellectual" functions; ✓ ensuring informational interaction between people and in the dissemination of mass information; ✓ occupying a central place in the informatization of society and in the process of accumulating knowledge.
The global objective of the ISoc can be defined in the following main directions:
Public sphere – creation of conditions for users for effective electronic information services while protecting personal privacy;
Production sphere – provision of complex automation in material production;
Scientific sphere – creation of conditions for continuous development of science to adequately guarantee scientific research.
ISco can be summarized as a society in which the main product is information, and the successful implementation of all processes in it is determined by the level of development of the applied information and communication technologies (ICT). Along with traditional computing and networking processes, the capabilities of cloud services, the Internet of Things, big data analytics, and cybersecurity must also be analyzed, along with the technology equipment that supports them.
Globalization in the digital society requires the timely solution of information security problems and taking adequate measures to protect information resources from accidental or intentional actions, such as disclosure, modification or destruction.
4. Digital Age and Privacy
Globalization and the opportunities for distributed access to various information resources in the digital society require their consideration as an economic resource with a certain value, which must not only be preserved and increased, but also be able to be protected in the process of its processing and use. All this raises the requirements for information operation and places strict responsibilities in the construction of virtual information spaces with the application of adequate approaches for analysing the level of security based on developed policies for information security and reliable access control. The goal should be to ensure reliable information security, confidentiality and protection of personal data, privacy protection [
7], which is essential in the continuous increase in the use of the global network and network technologies. These requirements are the main reason for updating regulations in the field of personal data protection [
17], introducing procedures for strict regulation of access and use of information, both by employees in the organizations and by external customers. The structuring of organizational capital, the cost of intellectual property protection, the level of responsibility in the performance of official duties and the general organizational culture are defined as important factors in choosing an appropriate cyber security and data protection strategy.
4.1. Historical Development of the Privacy
Historical roots of privacy can be found as far back as Aristotle’s philosophical discussion of the distinction between public and private spheres. Later, in the 12th-18th century, various documents related to this area were generated in Great Britain (Assize of Clarendon, 1166; Magna Carta, 1215; Habeas Corpus Act, 1679; The English Bill of Rights, 1689), as well as in the United States (by President James Madison in 1789) and France (Declaration of the Rights of Individuals and Citizens, 1789). This continued into the 19th century, with Samuel D. Warren and Louis Brandeis’s article "The Right to Privacy" being of particular significance, defining the "right to be left alone" paradigm as the definition of privacy.
Europe’s work on privacy began after World War II, with various documents discussing human rights (1948, 1950); racial discrimination (1965); discrimination on grounds of sex (1975), rights of the child (1985) and discrimination against persons with disabilities (1995); as well as Council of Europe Recommendation No. R(99) on Internet Privacy (1999). The first decade of the 21st century saw the adoption of documents on the security of information systems and networks (Security Culture, 2002; Periodic Review of Security Regulation, 2006; Cross-Border Privacy Enforcement, 2006; Equality Act, 2010 and others.).
Personal Data Protection (PDP) is an important part of technologies for privacy protection and defines the principles if relationship between the persons and institutions (governance, public and private organizations, etc.). The development of technology and increased application of computers in information processing in the 1960s and 1970s necessitated the development of a strong policy on the right to data protection in general and specifically imposed rules on the collection, storage and processing of personal data. This led to the adoption of specific PDP laws in individual countries (Hessen in Germany, 1970; Sweden, 1973; Germany, 1977; France, 1978, etc.) with Spain, Portugal and Austria including PDP as a human right in their constitutions. In the 1980s, principles were developed for the protection of data in cross-border flows. A sample summary of the main regulations in the field of PDP are summarized in
Table 1 and
Table 2.
The continuous development of the information society and globalization necessitated the aforementioned update of the personal data protection regulation (GDPR) effective from May 2018 [
17].
4.2. Challenges of the Digital Age to Users Security and Oersonal Privacy
There are various challenges of the digital space to personal privacy [
18], and below is a summary of the main possibilities for breaching the security and privacy of the user.
(1) Participants in the PDP are defined in three categories – Data Controller, Data Processor and Data subject (the last group includes the persons who are the owners of personal data). Directive 95/46/EC determines the obligation of the Data Controller to declare the purpose and categories of processing personal data. In today’s digital world (social media, cloud, e-business, etc.) it becomes increasingly difficult to define the role of the specific actor, because the functions of customer, seller and supplier, as well as the relationship between them, can only be defined on a case-by-case basis. In addition, an electronic service provider may only have certain PDP obligations if it is defined as Data Controller or Data Processor.
(2) In the digital world, several clear rights have been granted to users as "data subject", which must be respected during the processing. It is a basic obligation before starting the digital processing (provision of personal data) to declare for what purpose An important point is matching the data categories with the set goal - there is a case of unlawfully exceeding data categories when creating a personal profile (for example, names, date of birth, address, phone number, social life, gender, country, hobbies, relationships, etc.).
(3) PDP legislation allows the owner to review the collected personal data in his profile and make corrections (blocking incorrect data, deleting invalid or outdated data, etc.). This obliges the data controller to provide unrestricted access to each user’s own profile, as well as to prevent unauthorized access to third-party data. The user himself can define which persons can access his profile and define an authentication procedure.
(4) Another important right of the data subject is to request the deletion of part or all personal data in the profile if the purpose has been achieved. This also applies when refusing to use a given service or environment. A possible problem is that with such a request, the user cannot be sure that it will be fulfilled. One of the reasons is that in the digital space there is a continuous transfer of information (including personal data) to different places, which cannot guarantee the complete deletion of the request. An even more difficult situation is when data is transferred to third parties and in case of possible deletion in the first source, the data will remain available to the second recipient. Unfortunately, defined strict rules are difficult to apply in digital spaces (cloud/mobile blockchain, social media, communications in mobile networks, e-business sites, etc.).
(5) A possible challenge to users’ privacy is their sharing of data on the global network. It is especially dangerous when communicating with unknown users or responding to unregulated emails. There are various occasions in the global network to share personal data, but there is no categorical confirmation of their protection, especially for sensitive personal data. Special attention is paid to the latter in the GDPR regulation of May 2018. Violation of correct communications can lead to data loss or destruction of their integrity and veracity, as well as cause impaired accountability or the possibility of hacker attacks. All this obliges the owner of an information space in the network to take precautionary measures to protect user data and to promptly notify users of possible dangers.
(6) Another privacy challenge is the transfer of data to other countries. Directive 95/46/EC regulates the possible transfer of personal data to a third country only if the recipient has ensured a level of protection adequate to that in EU countries. Nevertheless, there is a practice of transferring data to nodes located in different countries, for which it is not certain that the specified requirement is fulfilled. This applies to data storage in remote data centers or cloud infrastructure, as well as between service providers in the case of social media, information exchange between collaborators, etc. The regulation clearly states that the owner of the data must be informed of each transfer of his personal data, but there are no guarantees that this is realized.
(7) The regulations clearly stated the main duty of the data controller to take the necessary adequate measures for the security of the maintained information and the protection of user data. Compliance with this requirement must be monitored, including the protection measures taken. Unfortunately, it is not declared who and how should do this, including checking the countermeasures against unauthorized access to information resources and personal information on the network. Users should consider these dangers themselves when choosing to provide personal data in the network space.
5. Conclusions
The global model for personal data protection determines the place and role of different participants in data processing – Data Subject, Data Controller, Data receiver, etc. Different documents in the sphere of user security and personal privacy determine requirements and suitable technological tools to ensure the necessary level of protection of personal profiles. This can be made based on the preliminary investigation of technological aspect of activities in the field and carried out researched in this field. Mine components of data protection system and its structural organization can be determined with specific tools defining for each structural level. In addition, the mine potential problems for breaching privacy in the contemporary digital society which uses different technologies such as social networks, cloud computing, Internet of Things, big data analytics must be clear determined and the necessary measures should be promptly taken.
Funding
This research received no external funding.
Data Availability Statement
The research conducted is based on information in the cited sources and mainly in the author’s publications [
7,
8,
17,
18]. More extensive information on information technology, modeling and data protection can be found in the Romansky’s chapter 13 entitled “Formalization and Discrete Modelling of Communication in the Digital Age by Using Graph Theory” of the book “Handbook of Research on Advanced Applications of Graph Theory in Modern Society”, IGI Global, 2020 (
https://www.igi-global.com/gateway/book/220804), and in the Romansky’s book “Digital Age and Personal Data Protection”, LAP LAMBERT Academic Publishing, 2022 (
https://morebooks.de/shop-ui/shop/product/978-620-4-73564-1).
Conflicts of Interest
The author declare no conflicts of interest.
References
- Zou, R.; Yang, J.; Feng, C. Does informatization alleviate energy poverty? A global perspective. Energy Economics, 2023, vol.126, art.106971. [CrossRef]
- Ordenov, S.; Polishchuk, O.; Skyba, I.; Shorina, T. Clarification of problems in modern society in the processes of informatization and globalization. E3S Web of Conferences, 2020, vol.164, art.11037. [CrossRef]
- Fainmesser, I. P.; Galeotti, A.; Momot, R. Digital privacy. Manage ent Science, 2023, vol.69, no.6, pp.3157-3173. [CrossRef]
- Yeşilyurt, E.; Vezne, R. Digital literacy, technological literacy, and internet literacy as predictors of attitude toward applying computer-supported education. Education and information technologies, 2023, vol.28, no.8, pp.9885-9911. [CrossRef]
- Tinmaz, H.; Lee, Y. T.; Fanea-Ivanovici, M.; Baber, H. A systematic review on digital literacy. Smart Learning Environments, 2022, vol. 9, no.21. [CrossRef]
- Hunt, K.; Gruszczynski, M. “Horizontal” two-step flow: The role of opinion leaders in directing attention to social movements in decentralized information environments. Mass Communication and Society, 2024, vol.27, no.2, pp.230-253. [CrossRef]
- Romansky, R. Digital age and personal data protection. International Journal on Information Technologies & Security, 2022, vol.14, no.3, pp.89-100.
- Romansky, R. Internet of Things and user privacy protection. IEEE International Conference on Information Technologies (InfoTech-2023), 20-21 September 2023, IEEE eProceedings (CD ROM), pp. 49-53.
- Ordenov, S.; Polishchuk, O.; Skyba, I.; Shorina, T. Clarification of problems in modern society in the processes of informatization and globalization. E3S Web of Conferences (EDP Sciences), 2020, vol. 164, p. 11037. [CrossRef]
- Xianqiang, Z. H. U.; Bijun, X. U. New characteristics of globalization under the background of accelerated development of informatization. Frontiers of Data and Computing, 2021, vol.3, no. 2, pp.16-22. [CrossRef]
- Kravets, O.Ja.; Aksenov, I.A.; Redkin, Yu. V.; Mutin, D. I.; Atlasov, I. V.; Zaslavskiy, A. A. Algorithms and methods for managing request flows in a distributed service system. International Journal on Information Technologies and Security, 2023, vol. 15, no. 4, pp. 73-80.
- Alseadoon, I.M. The power of intention in detecting social engineering attacks. International Journal on Information Technologies and Security, 2023, vol. 15, no. 3, pp. 75-86.
- Babenko, V.; Perevozova, I.; Mandych, O.; Kvyatko, T.; Maliy, O.; Mykolenko, I. World informatization in conditions of international globalization: Factors of influence. Global Journal of Environmental Science and Management, 2019, vol.5 (Special Issue), 2019, pp.172-179. [CrossRef]
- UNESCO. Internet Governance. (https://www.unesco.org/en/internet-governance).
- Haboubi, S.; Salem, O.B. Predictive analytics for energy consumption in smart homes with fog and cloud computing using support vector regression. International Journal on Information Technologies and Security, 2022, vol. 14, no. 1, pp. 49-60.
- Zozulya, M.M.; Kravets, O.Ja.; Atlasov, I.V.; Aksenov, I.A.; Bozhko, L.M.; Rahman. P.A. Algorithmization of the software testing system based on finite automata. International Journal on Information Technologies and Security, 2022, vol. 14, no. 1, 2022, pp. 77-86.
- Romansky, R. A survey of informatization and privacy in the digital age and basic principles of the new regulation. International Journal on Information Technologies and Security, 2019, vol. 11, no. 1, 2019, pp. 95-106.
- Romansky, R.; I. Noninska, I. Challenges of the digital age for privacy and personal data protection. Mathematical Biosciences and Engineering (Special Issue “Emerging Technologies: Recent Advances and Future Challenges”), Publisher AIMS Pres, 2020, vol. 17, no. 5, pp.5288-5303 (article MBE2020268). [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).