1. Introduction
ZTA is a cybersecurity architecture emphasizing that no entity, regardless of its location within or outside the network, should be automatically trusted. Instead, every access request must go through authentication, authorization, and continuous validation. As businesses increasingly migrate to cloud platforms like Microsoft Azure, it is essential to establish a ZTA to protect against sophisticated security breaches. However, this transformation is not straightforward. Deploying ZTA in Azure involves a meticulous and complex process requiring deep technical expertise and a thorough understanding of Zero Trust principles and Azure's intricate ecosystem. Azure's intricate user interface exacerbates the challenge, making the navigation and configuration of security settings daunting. Every element, beginning with the establishment of identity management and access restrictions to the installation of network security and the maintenance of continuous surveillance, demands careful planning and precision. Regardless of these challenges, it is crucial to effectively integrate ZTA into Azure to bolster security and safeguard critical assets in an ever-expansive digital landscape.
Previous research explores the application of zero-trust security in intelligent manufacturing, which is essential for safeguarding Industry 4.0 environments [
1]. The article highlights several obstacles, including the intricacy of incorporating zero-trust concepts into current legacy systems, rising expenses, and potential effects on productivity. In addition, the authors emphasize the importance of ongoing authentication, live monitoring, and robust security frameworks. They support the need for more research to improve zero-trust architectures specifically designed for IoT and cloud-based manufacturing systems to achieve effortless implementation and heightened security. They propose investigating machine learning (ML) and artificial intelligence (AI) to enhance predictive threat detection and response, highlighting the significance of adaptive security measures. Additionally, the report emphasizes the need to create uniform procedures and foster cooperation among relevant parties to tackle interoperability concerns. This paper highlights the importance of continuous improvements to safeguard innovative industrial systems effectively.
A blockchain framework developed to enhance healthcare data management by bolstering security, privacy, and interoperability was also introduced in 2023 [
2]. The authors encountered difficulties achieving a harmonious equilibrium between the openness and secrecy of delicate information, incorporating blockchain protocols into pre-existing healthcare information technology systems, and guaranteeing adherence to rigorous regulatory obligations. Although Hyperledger Fabric has shown notable enhancements in security, crucial areas still require additional research, like scalability, performance concerns, and user adoption. Future endeavors encompass the investigation of sophisticated cryptographic methods, the improvement of blockchain scalability, the execution of real-world pilot studies, and the promotion of collaboration between healthcare practitioners and technology developers to establish standardized protocols. This study emphasizes the significance of employing new strategies to safeguard and efficiently handle confidential healthcare information in an ever-growing digital environment.
Researchers also noted the urgent need to ensure safe remote access in Industrial Internet of Things (IIoT) settings [
3]. The authors suggest implementing a zero-trust architecture that prioritizes multi-level authorization, continuous authentication, and strong access control measures to improve security, scalability, and maintainability. Incorporating zero-trust concepts into current IIoT infrastructures posed difficulties, especially in striking a balance between security and operational efficiency and guaranteeing smooth integration with older systems. Notwithstanding these difficulties, the suggested resolution, executed utilizing open-source technology such as Software-Defined Networks (SDN) and Trusted Execution Environments (TEE), exhibited noteworthy enhancements in safeguarding both the network and edge domains. The authors suggest that future research should focus on resolving scalability and performance concerns, enhancing zero-trust implementations, and investigating advanced cryptographic techniques to strengthen security. This study emphasizes the crucial importance of cutting-edge security frameworks in protecting industrial systems from constantly changing cyber threats.
The security environment of the metaverse was also researched [
4], highlighting significant concerns and suggesting a ZTA model to address these difficulties. The authors emphasize the intricate interaction among enabling technologies such as AR, VR, and cloud computing, which give rise to distinct security and privacy risks. A vital obstacle noted is balancing, providing engaging user experiences, and implementing strong security measures. The authors encountered challenges when including ZTA into preexisting metaverse frameworks without compromising performance. The study highlights that the existing security solutions frequently prove insufficient to address the dynamic and decentralized characteristics of the metaverse. Potential areas for future research include enhancing ZTA implementations to manage real-time interactions effectively and establishing universally accepted security standards that can be implemented across many metaverse platforms. The writers promote the idea of stakeholders working collaboratively to address these concerns comprehensively.
Previous research also examines a thorough security architecture designed for the banking sector [
5]. The system combines ZTA with blockchain technology to tackle cybersecurity issues. The authors highlight the significance of identity and access management, device and network security, and data protection. The challenges involve the delicate equilibrium between security and operational efficiency and guaranteeing a smooth interface with existing systems. The suggested framework utilizes blockchain technology to bolster security safeguards, providing unalterable verification and heightened data integrity. Although the study has potential, it highlights scalability and performance difficulties that additional research needs to address. Future endeavors involve enhancing ZTA implementations, investigating sophisticated cryptographic techniques, and conducting practical pilot studies to verify the framework's efficacy. In addition, the authors promote the idea of financial institutions and technology developers working together to create standardized security procedures and establish best practices.
A new framework that aims to improve security in IoT settings called ZAIB (Zero-Trust and ABAC for IoT using Blockchain) was also introduced [
6]. The framework combines a zero-trust architecture with attribute-based access control (ABAC) and blockchain technologies to provide safe device communication. The challenges encompass effectively controlling dynamic access, preserving data integrity, and safeguarding against assaults. The study highlights the significance of ongoing surveillance and flexible security measures. Authors note that future research should prioritize enhancing the scalability and performance of the ZAIB framework, investigating sophisticated cryptographic techniques, and carrying out real-world pilot tests to verify its efficacy. Furthermore, it is imperative to establish uniform protocols and optimal methods to promote the broader implementation of this security framework in diverse IoT applications. The paper emphasizes the urgent requirement for inventive security measures to protect sensitive data in progressively intricate IoT networks.
Researchers investigated integrating zero-trust principles and quantum fingerprinting to improve network security, specifically in countering MAC spoofing [
7]. Implementing quantum fingerprinting posed difficulties, such as the intricacy of integration and the need to sustain system performance. The authors stress the importance of ongoing authentication and cryptographic solid techniques. Future research should prioritize enhancing the framework's scalability and performance, investigate advanced cryptographic techniques, and conduct thorough real-world pilot tests to evaluate its usefulness. Furthermore, the study emphasizes the need for established standards and cooperation among industry players to promote the general acceptance of this unique security paradigm. This research highlights the need for advanced technology to create safe and robust networks to combat ever-changing cyber threats.
The complexity of deploying Zero Trust Network Architecture (ZTNA) in cloud environments was also researched [
8]. The authors note significant obstacles, such as the need to uphold security while also guaranteeing operational efficiency and seamlessly incorporating with existing systems. The user emphasizes the significance of ongoing surveillance, flexible security measures, and robust data safeguarding. Future research should prioritize the optimization of ZTNA installations, developing improved cryptographic methods, and validating these approaches in real-world scenarios. Furthermore, it is imperative to collaborate across the entire business to establish standardized norms and optimal practices. This evaluation emphasizes the necessity for cutting-edge security solutions to safeguard cloud computing from ever-changing cyber threats. The authors propose that providing advanced training for IT personnel and conducting frequent security audits can bolster the effectiveness of ZTNA installations. In summary, the essay comprehensively examines the possibilities and constraints of ZTNA in cloud computing, providing significant perspectives for future advancements in this domain.
A methodology that enables the seamless integration of AI in Industry 5.0 by employing zero-touch orchestration inside the edge-to-cloud continuum was introduced in 2023 by researchers [
9]. The authors stress the importance of smoothly incorporating AI into systems and improving the automation and decision-making procedures. Primary obstacles involve overseeing the entire lifecycle of AI operations and guaranteeing reliable connection between edge and cloud components. Subsequent investigations should delve into sophisticated orchestration strategies, enhancing the deployment of AI models, and conducting real-world validations. The cooperation between industry and academics is essential for developing standardized protocols and optimal practices. The study highlights the capacity of AI to transform Industry 5.0 by implementing inventive, automated, and robust frameworks.
Previous research suggests that ZTA seeks to revolutionize security strategies by shifting away from traditional perimeter defenses and embracing a paradigm that thoroughly authenticates the identity of any person and device attempting to access resources. This strategy is particularly crucial for scenarios that entail geographically distant users and assets hosted in the cloud. ZTA does not rely on implicit trust created based on physical or network locations. Instead, it prioritizes ongoing authentication and verification to guarantee resource access security [
10]. Studies highlight the challenges of moving from obsolete systems to ZTA, which necessitate meticulous preparation and the active participation of all essential stakeholders to accomplish a seamless move and improve security posture [
11].
Ongoing research indicates that the core technologies of ZTA, such as identity authentication, access control, and trust assessment, are still being developed. Organizations' lack of knowledge about the advantages and disadvantages of ZTA and the complexities involved in implementing it hinders its adoption. Additional inquiry is necessary to address these challenges and develop more sophisticated ZTA solutions [
12]. Implementing ZTA has difficulties ensuring robust availability and tamper resistance in policy decision points. These elements are essential for maintaining a strong and secure system [
13].
Studies in the field of 6G networks suggest that traditional security frameworks are inadequate for the upcoming generation of networks, demonstrating increased openness and heterogeneity. A cutting-edge software-defined ZTA has been proposed for 6G networks. This architecture offers flexible and scalable security mechanisms, effectively mitigating threats such as Distributed Denial of Service (DDoS) attacks and zero-day exploits. However, unresolved issues still need to be addressed, such as more thorough simulation studies and real-world validations to enhance and optimize ZTA implementations for future networks [
14].
Studies on zero trust for applications and network security reveal that globalization, the COVID-19 epidemic, and the shift to cloud services necessitate a departure from traditional security protocols. The study highlights the significance of continuous identity verification and minimizing the delegation of authority to safeguard the security of network systems. A significant finding is that insecure APIs present a considerable threat in zero-trust environments, underscoring the need for enhanced API security policies and awareness [
15].
A recent study suggests that using a zero-trust approach in cloud computing efficiently addresses several security concerns, such as internal and external cyber threats and the need for enhanced visibility and automated trust calculations. Comparative assessments of different ZTA models and frameworks demonstrate that while ZTA can significantly improve security, its full implementation requires addressing specific challenges in various domains and integrating new technologies to build robust, trust-based enterprise networks [
16].
Previous research has also highlighted the innovative use of ML in implementing ZTA, particularly for calculating trust, which remains a complex and subjective task. ML techniques have shown promise in enhancing security through continuous monitoring and adjusting trust metrics. As a result, this leads to a security framework that is more adaptable and responsive than conventional frameworks [
17]. Future investigations should improve machine learning techniques to maximize their accuracy and effectiveness in practical zero-trust architecture implementations.
The rest of this paper is organized as follows. In the next section, we will cover some basic security principles, followed by a section about the specifics of Azure ZTA implementation. We will then move to a ZTA scenario to analyze its capabilities and suitability for mid-size organizations. We will follow up by examining the scenario with some additional best practices and discussing future work and the conclusion.
2. Azure Security Principles
Azure security has a comprehensive and complex toolkit to protect cloud-based resources from various threats. Microsoft Azure provides multiple integrated security features and services to safeguard data, applications, and infrastructure. The following are the fundamental components of Azure security:
Azure Network Security: The Azure Virtual Network (VNet) is a crucial component that guarantees the separation and division inside the cloud environment. Virtual networks (VNets) can be extended to on-premises locations by establishing secure connections such as virtual private networks (VPNs) and ExpressRoute. Azure offers comprehensive security services, including Azure Sentinel, which uses artificial intelligence and machine learning to detect and mitigate potential security risks [
18].
Azure Active Directory (Azure AD) is crucial for managing identities and controlling access in Identity and Access Management. The platform provides features such as Multi-Factor Authentication (MFA), Conditional Access, and Identity Protection to guarantee the security of user identities and control resource access. Azure AD also enables integration with supplementary identity providers and applications [
19].
Azure IoT Edge and Azure Sphere are purpose-built to bolster the security of Internet of Things (IoT) deployments. Azure Sphere exemplifies the integration of hardware-based security with a tailored Linux-based operating system and a security service to ensure the reliability of devices and safeguard communication [
20]. Azure IoT Edge includes built-in security features for deploying and managing IoT devices [
21].
Azure offers various services to protect data during storage and transmission. Azure Key Vault simplifies the administration of encryption keys and confidential information, while Azure SQL Database provides Transparent Data Encryption (TDE) and Always Encrypted features to protect sensitive data [
22,
23]. Furthermore, Azure's compliance certifications ensure data handling meets rigorous regulatory criteria.
Azure Security Center provides a comprehensive view of security for all Azure services, offering recommendations and insights to improve security procedures. In addition, it effortlessly integrates with Azure Sentinel to offer enhanced protection against advanced threats and comprehensive monitoring features [
24,
25]. Azure Defender enhances these capabilities to encompass hybrid and multi-cloud systems, protecting against various threats.
Azure ensures application security by implementing secure development practices, automated security testing, and runtime protection mechanisms. Azure DevOps includes built-in security features for code repositories, CI/CD pipelines, and artifact storage [
26]. Furthermore, Azure Container Registry and Azure Kubernetes Service (AKS) provide functionalities to bolster the security of containerized applications [
27].
Azure offers a comprehensive compliance framework with certifications and attestations such as ISO 27001, GDPR, and HIPAA, guaranteeing compliance and governance. Azure Policy and Blueprints help organizations maintain compliance and governance across cloud environments [
28].
Azure Blockchain Workbench provides a suite of tools for constructing and managing blockchain networks, explicitly focusing on protecting key management and assuring the integrity of transactions. This entails incorporating Azure Key Vault for the secure storage of keys and employing cryptographic techniques to ensure the confidentiality and security of data [
29].
Azure Sentinel is a cloud-based Security Information and Event Management (SIEM) platform that offers advanced capabilities for detecting and mitigating security risks. It employs artificial intelligence to quickly identify and mitigate potential hazards while integrating with various Azure services and third-party solutions to provide a comprehensive security solution [
30].
Azure provides a comprehensive security framework encompassing network security, identity management, data protection, threat detection, and compliance measures. By leveraging these technologies and services, enterprises can effectively protect their cloud infrastructures and minimize potential dangers.
3. Azure ZTA
Azure ZTA is a modern cybersecurity framework emphasizing the concept of "never trust, always verify." This architecture shifts away from the traditional security model that depends on defending the boundary to a more extensive and meticulous approach that prioritizes securing individual resources and data streams. Consequently, it enhances organizations' overall security using Azure cloud services [
31]. ZTA moves away from exclusively depending on network location for trust and instead requires the authentication of both the user and the device before granting access to resources [
32]. This paradigm is crucial for enterprises with remote users and assets in the cloud, making it highly pertinent in the present digital landscape [
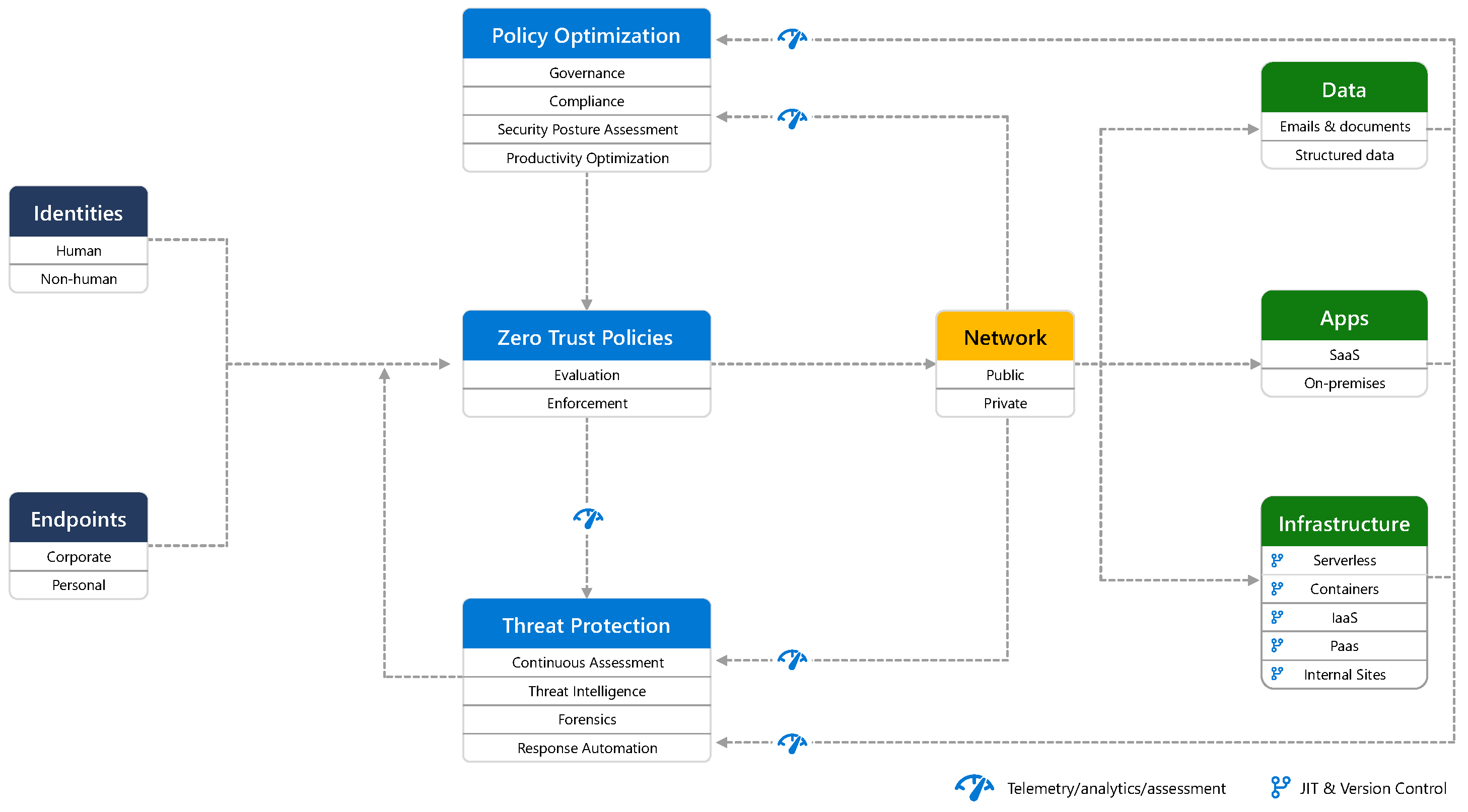
33]. The basic architecture can be seen in Figure 1:
Implementing ZTA requires significant alterations across the company, demanding a carefully built framework to provide a smooth transition [
34]. The main concepts involve continuous verification and permission granting, minimizing vulnerable areas by dividing resources, and granting the least access [
35]. Azure's ZTA employs advanced technologies, including micro-segmentation, identity management, and continuous monitoring, to guarantee the security of data and applications [
36].
Incorporating ZTA into existing systems poses challenges due to its complex nature and the need for a cultural shift in security procedures [
37]. However, studies have highlighted the effectiveness of ZTA in reducing breach risks and enhancing overall security by implementing strict access controls and monitoring [
38]. Zero trust systems have shown significant improvements in dealing with cyber threats in cloud environments [
39], smart manufacturing [
40], and healthcare [
41].
Research suggests that ZTA can provide a robust defense against advanced attacks by enforcing stringent access rules and continuously monitoring the system [
42]. In addition, the utilization of ZTA in specific domains, such as cyber-physical systems [
43] and Kubernetes environments [
44], highlights its flexibility [
45].
Azure ZTA acts as a resilient security framework that enhances the protection of resources in cloud environments by removing the assumption of trust and enforcing stringent access controls. Implementing it can significantly reduce security vulnerabilities and strengthen the resilience of enterprise systems against cyber threats. In the next section, we'll comprehensively analyze how Azure ZTA can be implemented in a mid-size company migrating to the cloud.
4. Experimental Setup and Study Methodology
We used a test Azure environment with a custom scenario while researching the topic of this paper. Suppose we must implement Azure ZTA in an organization transitioning to a cloud-centric infrastructure. The organization must ensure secure access to resources while managing a distributed workforce. The focus is on identity and access management (IAM) to protect sensitive data and services. The practical implementation involves setting up Microsoft Entra ID for identity management, configuring MFA, Self-Service Password Reset (SSPR), Just-In-Time access (JIT), and passwordless authentication, and enforcing access control. It also requires the implementation of a secure network infrastructure, which involves using Azure Network Security Services. The starting point of the process is an Azure tenant and at least one user with a Global Admin role to introduce the changes needed. The first part of the implementation needs to be done in Entra ID, as the most convenient way to implement ZTA starts with the Conditional Access configuration.
4.1. Azure Conditional Access with MFA and SSPR
Azure Entra ID Conditional Access is crucial to Microsoft's identity and access management service. It helps companies efficiently manage and protect access to their applications and data. Organizations can employ this capability to implement automatic access control decisions based on pre-established regulations. These policies enable administrators to create specific access rules and criteria, ensuring only authorized users can access sensitive information. Conditions may include several elements such as user characteristics, device adherence, geographical location, and amount of danger. Organizations can enhance security by combining several measures, such as implementing multi-factor authentication, restricting access to specific locations, or enforcing device compliance checks. This high level of exact control enhances security by ensuring that access is granted only when specified conditions are met, thereby preventing unauthorized entrance and improving overall security.
For CA to work, we need to meet specific requirements:
We need to turn off security defaults;
We need to disable per-user MFA;
We need a license that supports it (Business Premium, Entra ID P1 or P2).
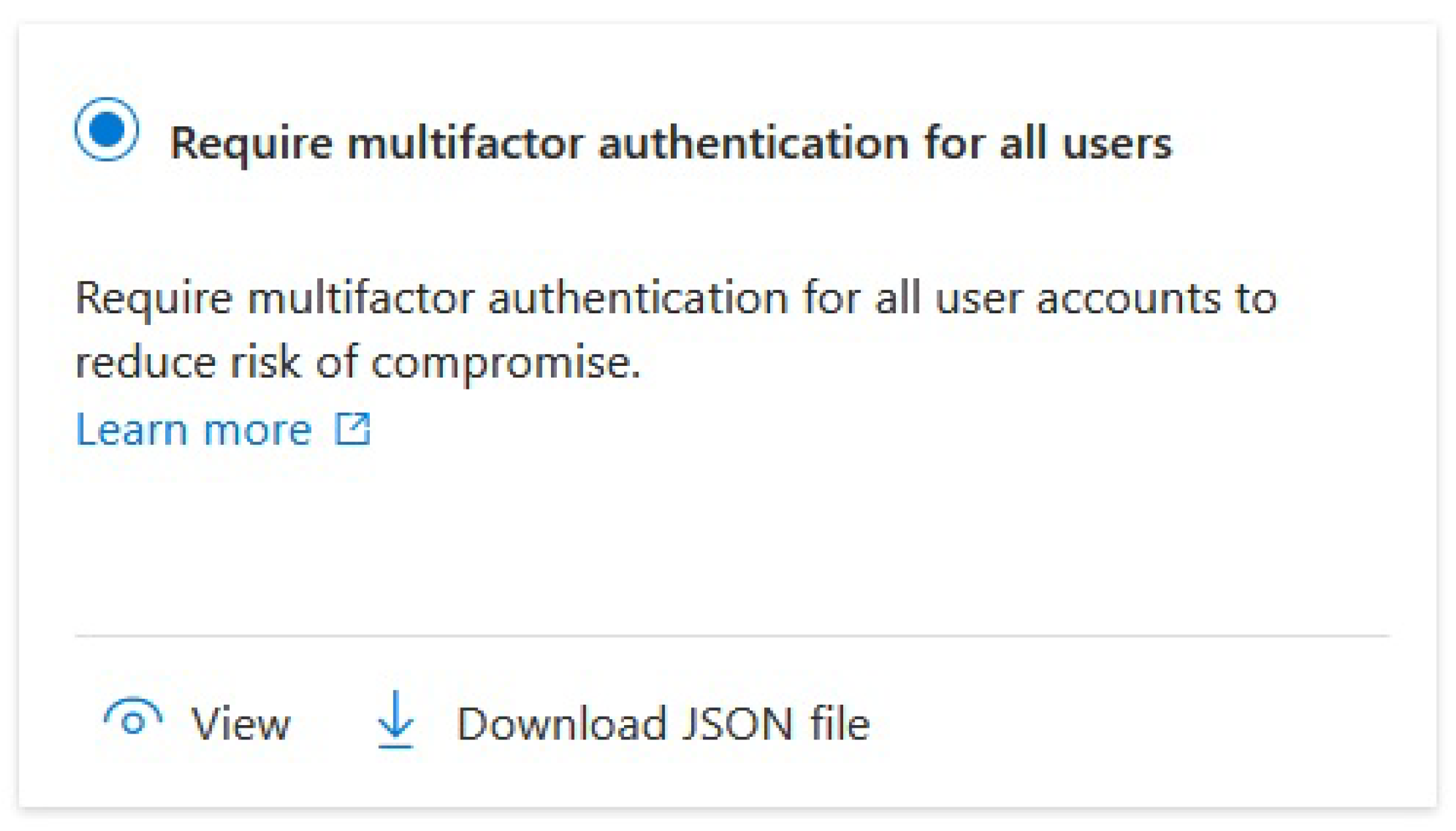
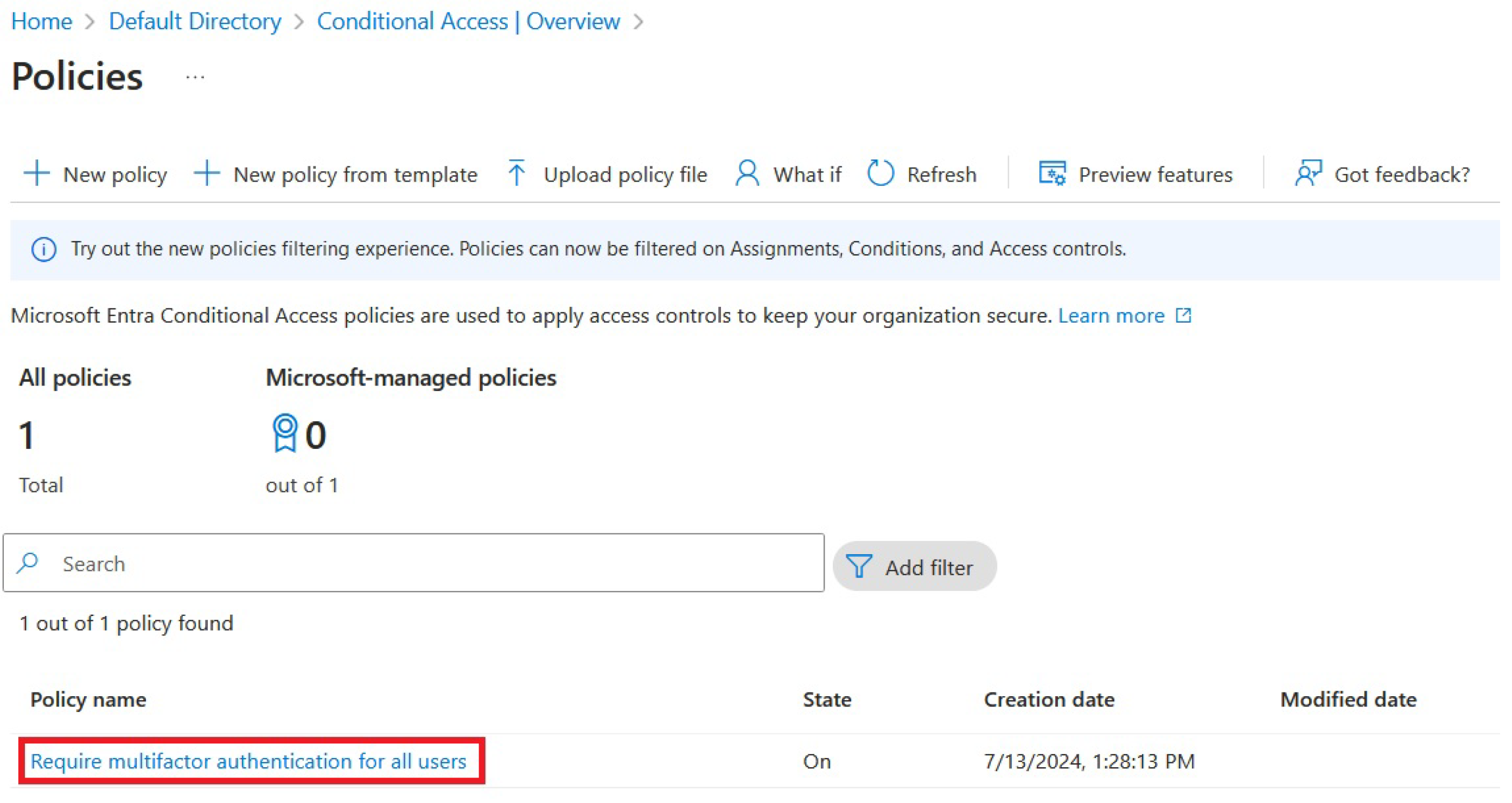
After we activate the required license, Azure UI takes us to the Microsoft 365 Admin Center, where we get the list of available permits and, if we’re using a trial license, when the trial is valid. We can turn off the security defaults and start configuring Conditional Access Policies there. The first policy that seems to be a reasonable starting point is to enforce MFA for all users. This makes the environment much more secure as we don’t have to rely only on passwords that can be brute forced if not configured correctly. So, after we get to the Home/Default Directory/Conditional Access tab, we can select the following blade from the UI:
Figure 1.
Configuring MFA as a mandatory Conditional Access Policy from a template.
Figure 1.
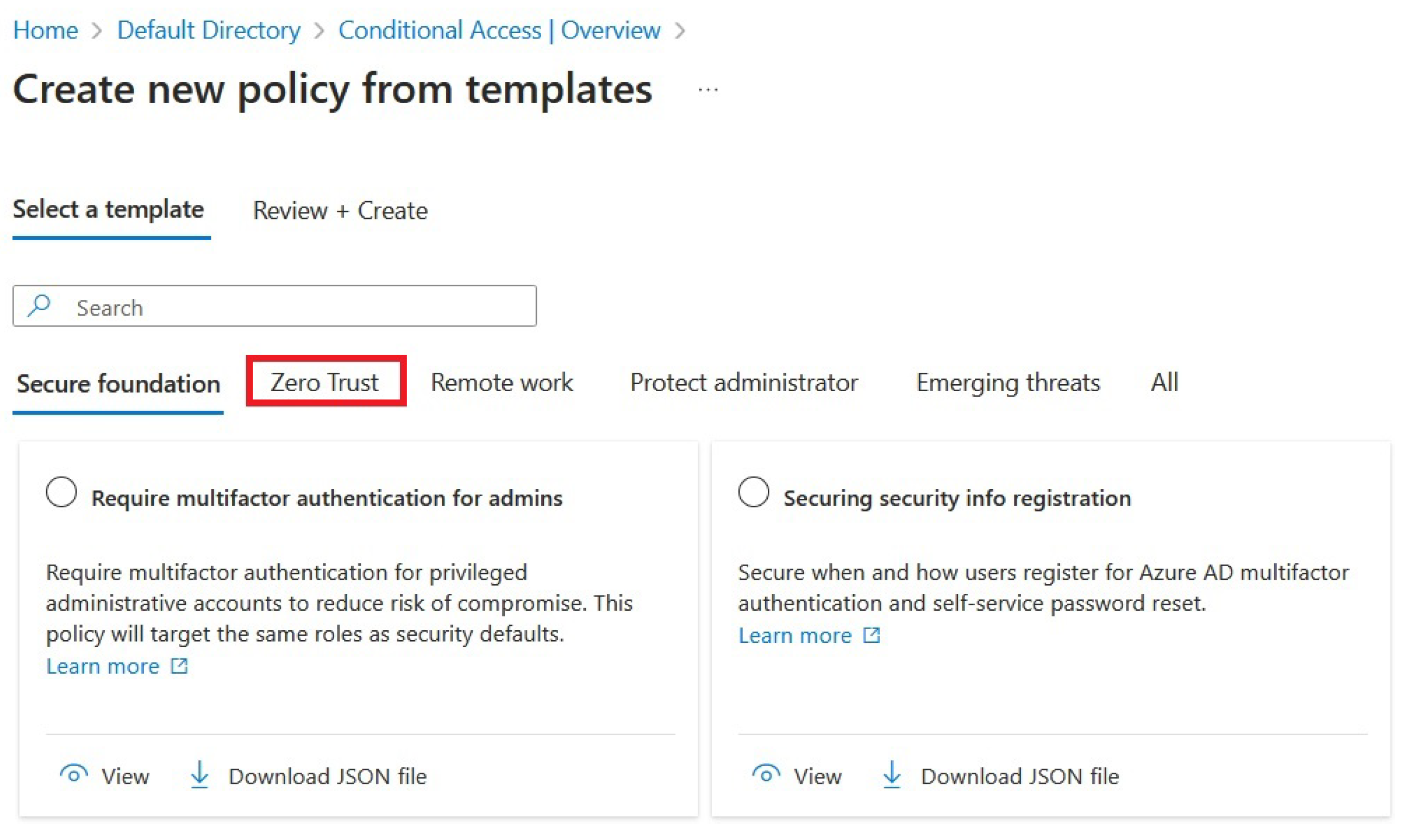
Configuring MFA as a mandatory Conditional Access Policy from a template.
There’s a “Zero Trust” tab available here, with a selection of templates to use for ZTA implementation, as we can see in
Figure 2:
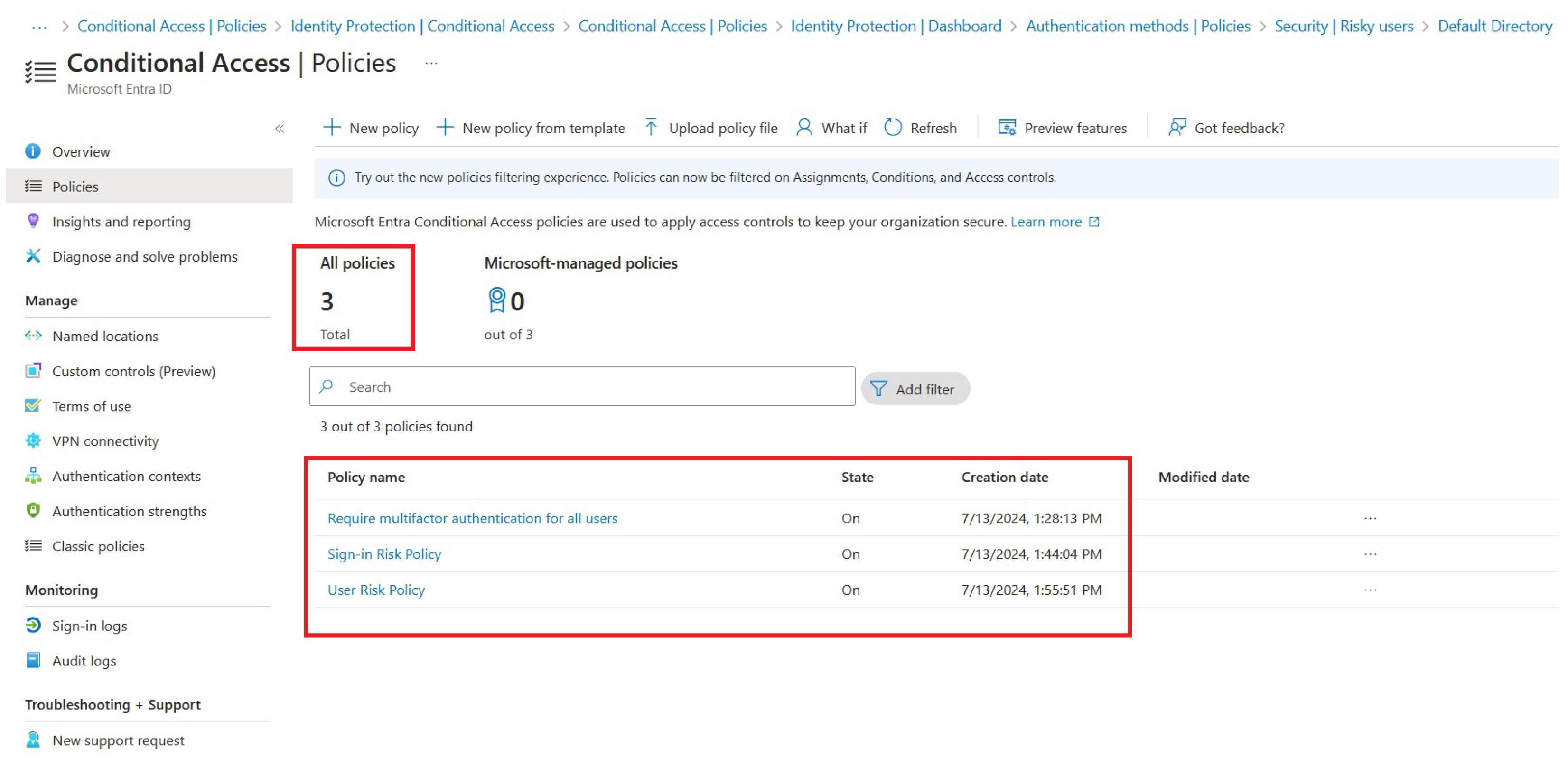
We can quickly check which Conditional Access Policies are enabled for our tenant, as can be seen in
Figure 3:
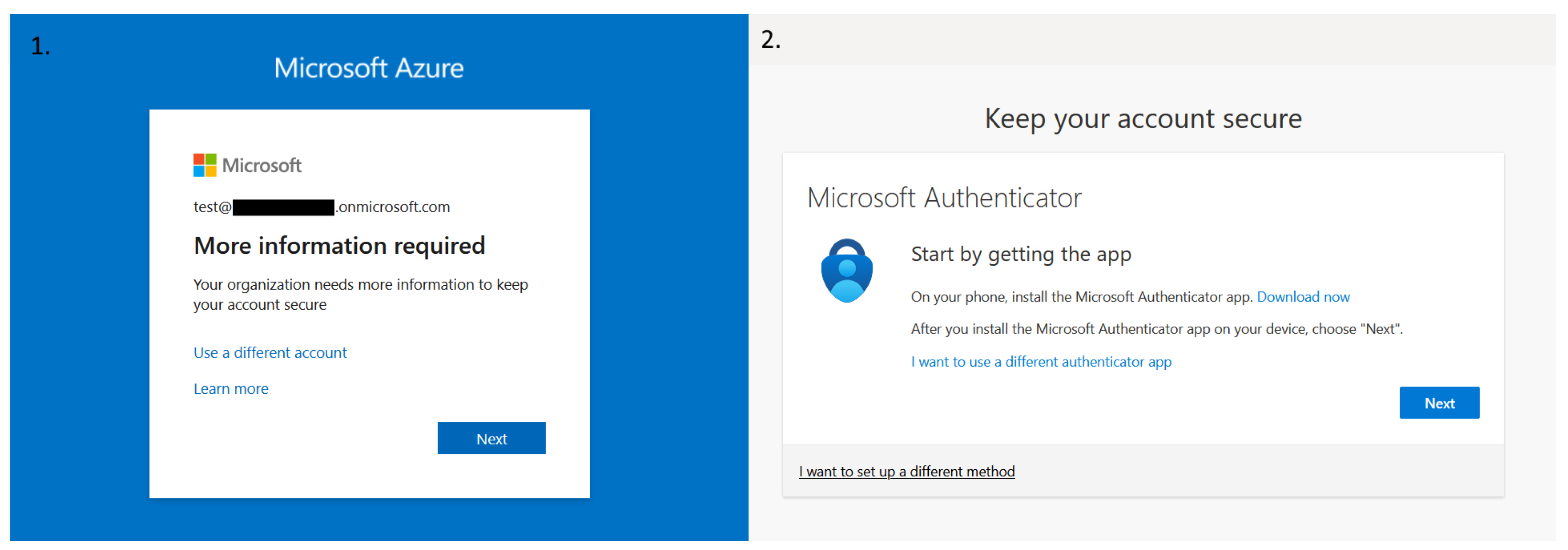
After enabling this specific Central Access Policy, we will get a familiar message when dealing with MFA on Azure, as we can see in
Figure 4:
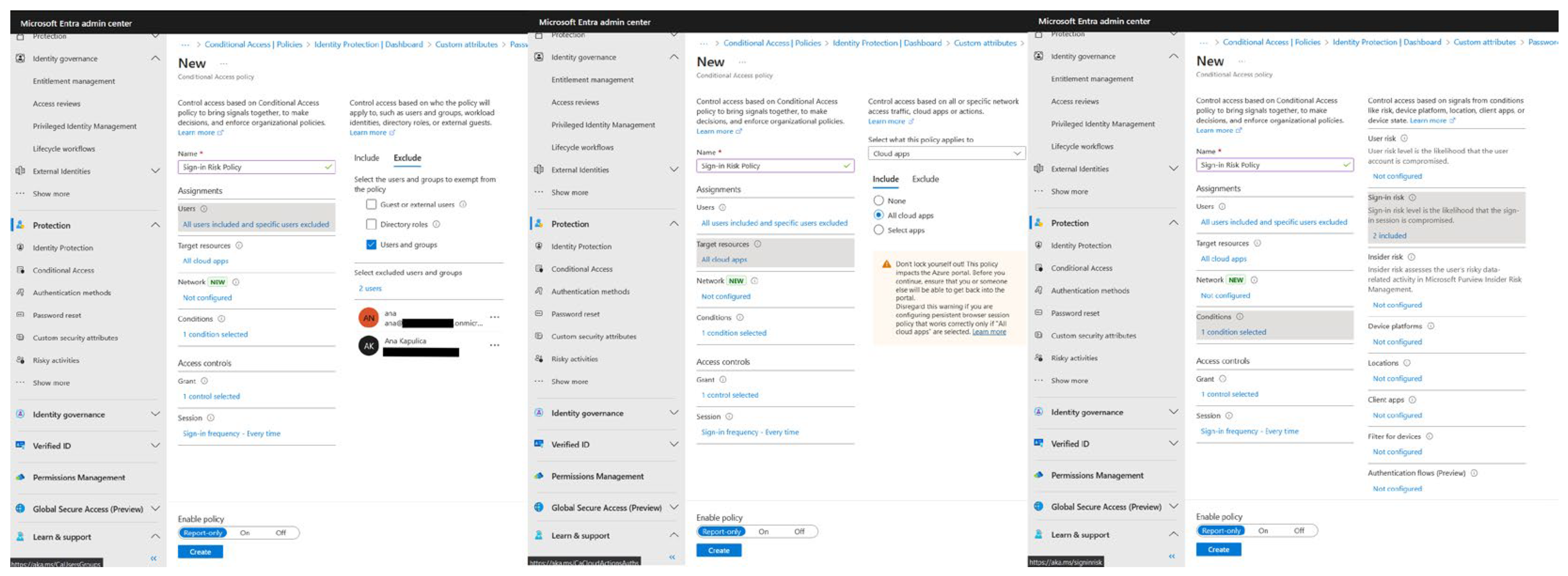
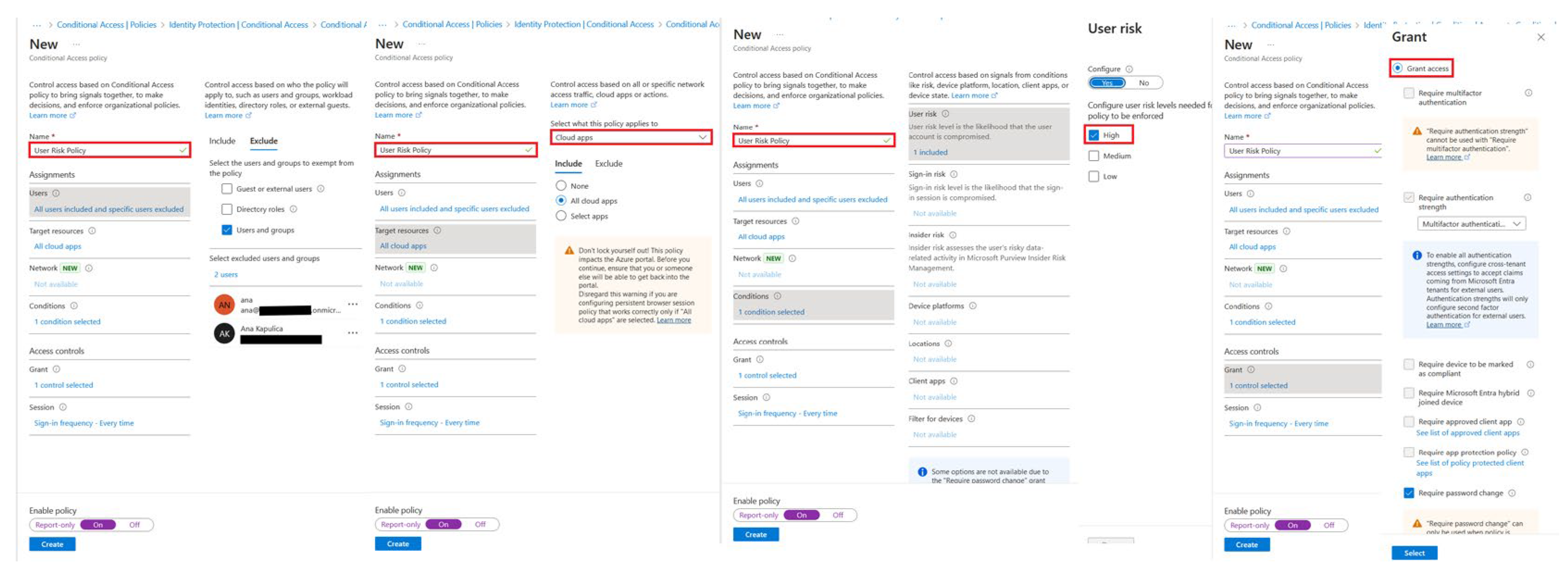
Now that we have the basic Central Access Policy, we must add additional security measures to follow the ZTA architecture. In this regard, Microsoft recommends implementing additional risk policy configurations to protect our environment, specifically the User and Sign-in risk policies.
User risk policy requires a secure password change if a user’s risk level is detected as high. MFA is required before a password change is doable, so we first enforced the MFA policy on all users, as this significantly increased the baseline security level.
The Sign-in risk policy requires MFA if a sign-in risk level is detected as medium or high. This way, the user can prove they are while trying to sign in. It’s good practice to have some emergency access or a break-glass account(s) during these implementations so we don’t lock ourselves out of our tenant. Let’s first configure the Sign-in policy, as we can see in
Figure 5:
By having a break-glass account, we can target our policy so we won’t lock ourselves out of the environment. Specifically, we want to configure the policy only to affect specific users (in our scenario, test users) and target the policy to resources needing it (for example, cloud applications). In this way, we can use conditions to segment controls based on sign-in risk level and select our specific level (for example, medium and high). The “Grant” part of the policy requires us to choose what the policy grants or blocks if the conditions are met – in our scenario, it grants access to MFA every time a user tries to sign in.
The next step is configuring the User risk policy, as can be seen in
Figure 6:
We can check if the process has finished successfully by checking Conditional Access Policies, as can be seen in
Figure 7:
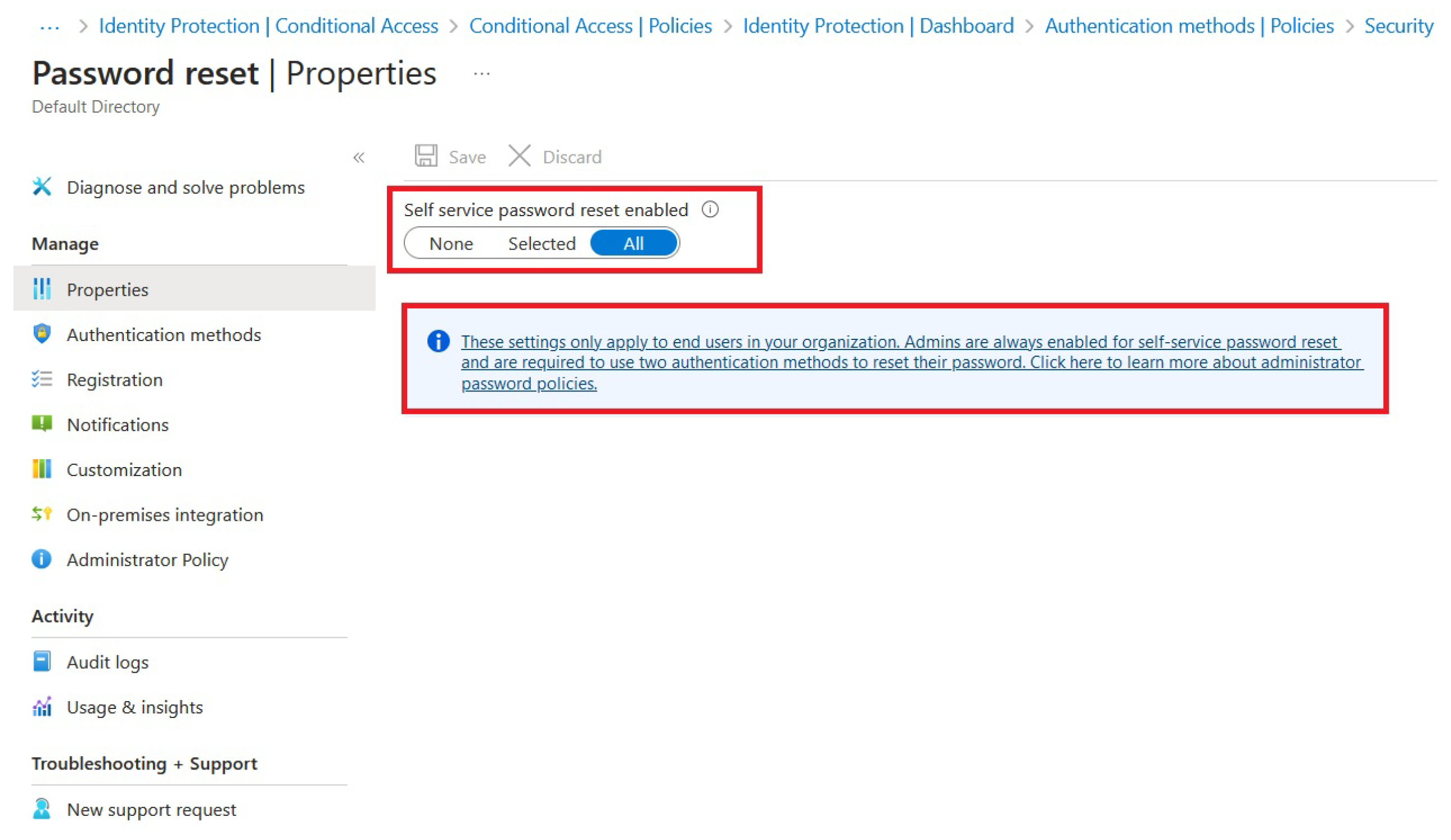
The next logical step in our ZTA process should be to enable SSPR (Self-Service Password Reset). The critical point here is that SSPR can be enabled with MFA, which makes the overall process much more secure. The configuration can be seen in
Figure 8:
This will also help reduce helpdesk dependence and allow more user convenience while assisting in the timely resolution of account lockouts without compromising security
4.2. Azure Passwordless Authentication
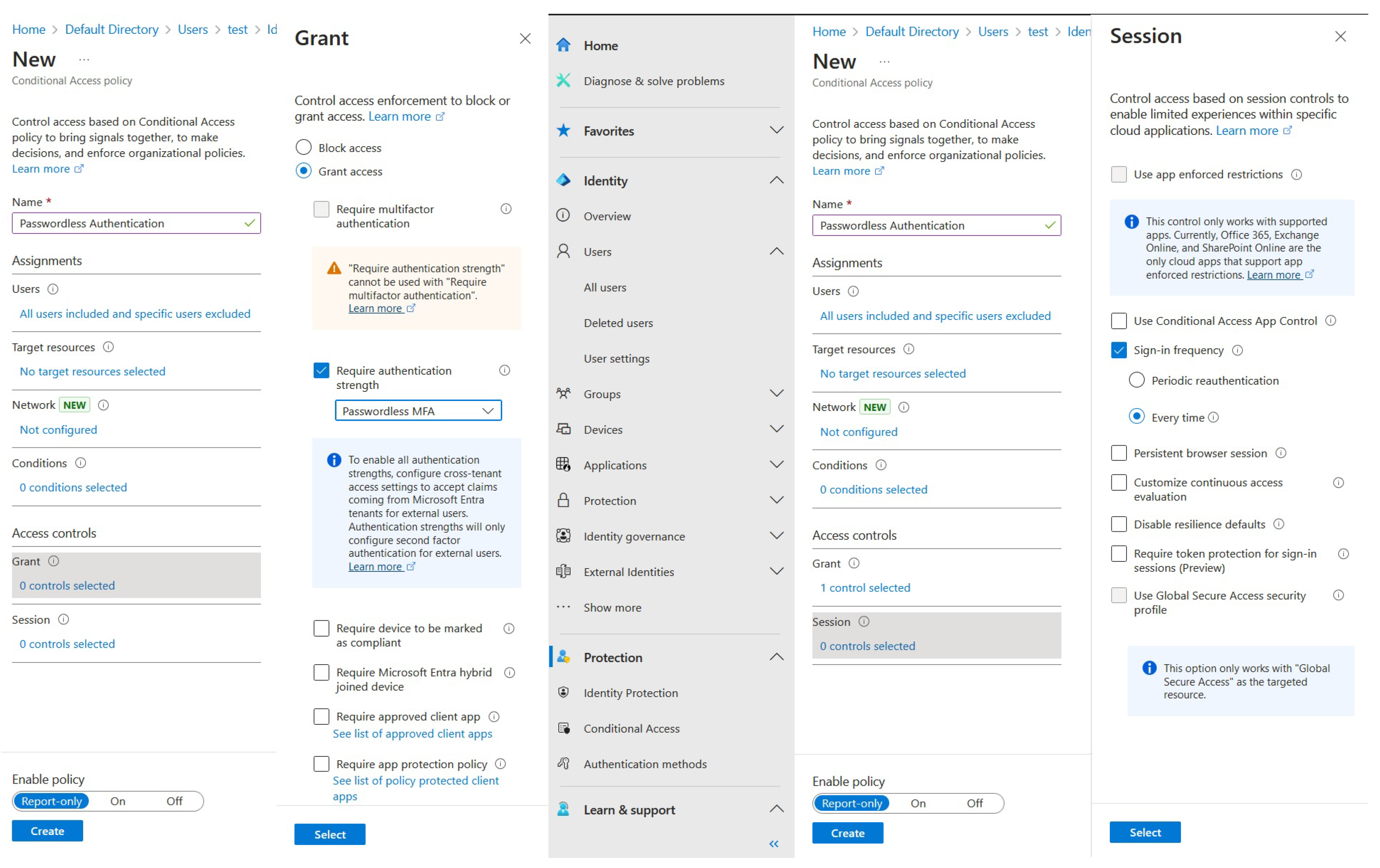
Let’s now analyze Azure’s passwordless authentication option. By using this capability, we can eliminate vulnerabilities associated with traditional passwords, such as weak passwords, re-using old passwords, and phishing attacks. In ZTA, where continuous verification and strong authentication are important, passwordless methods (like biometrics, hardware tokens, or mobile authenticator apps) ensure that only legitimate users can access resources. This approach reduces the attack surface, enhances user experience with seamless logins, and aligns with Zero Trust principles by requiring multifactor authentication and reducing reliance on potentially compromised credentials.
We will enable passwordless authentication by implementing another conditional access policy, as can be seen in
Figure 9:
This is a fundamental change in the way we approach authentication in terms of ease of use; if we were to implement the same idea in the private data center, we would be forced to configure multiple services like Active Directory Certificate Services (AD CS), Active Directory Federation Services (AD FS), Microsoft Identity Manager (MIM) or create a hybrid Active Directory (AD) with Entra ID to get access to an equivalent set of features.
4.3. Azure Access Review
Azure access reviews, a Microsoft Entra ID Governance component, enable organizations to effectively oversee and regulate user access to resources. Organizations can guarantee that only authorized users keep access by implementing regular evaluations of group memberships, application access, and role assignments. This approach aids in reducing security risks, ensuring compliance with regulatory standards, and adhering to the principle of least privilege. Automated reviews can be tailored to specific scenarios, such as privileged roles or critical data access, and can be seamlessly incorporated with other Azure AD features to provide a complete identity governance solution.
Access reviews are an essential part of ZTA architecture, as they ensure that users have the appropriate level of access based on their current roles. It also forces us to do regular reviews and validations to help enforce the fundamental “least privilege” principle, reducing the risk of unauthorized access, which further aligns with ZTA’s “never trust, always verify” core mantra.
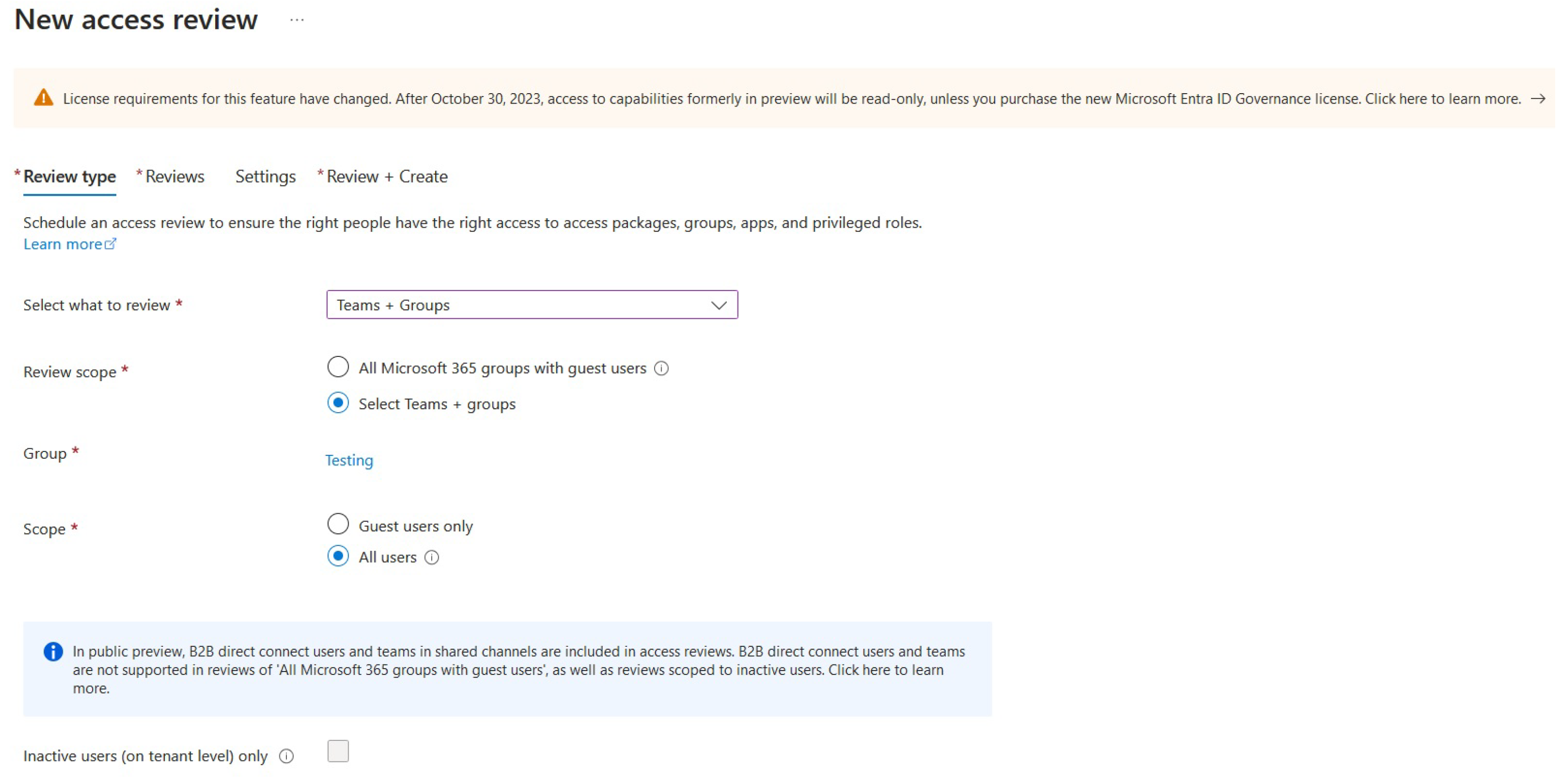
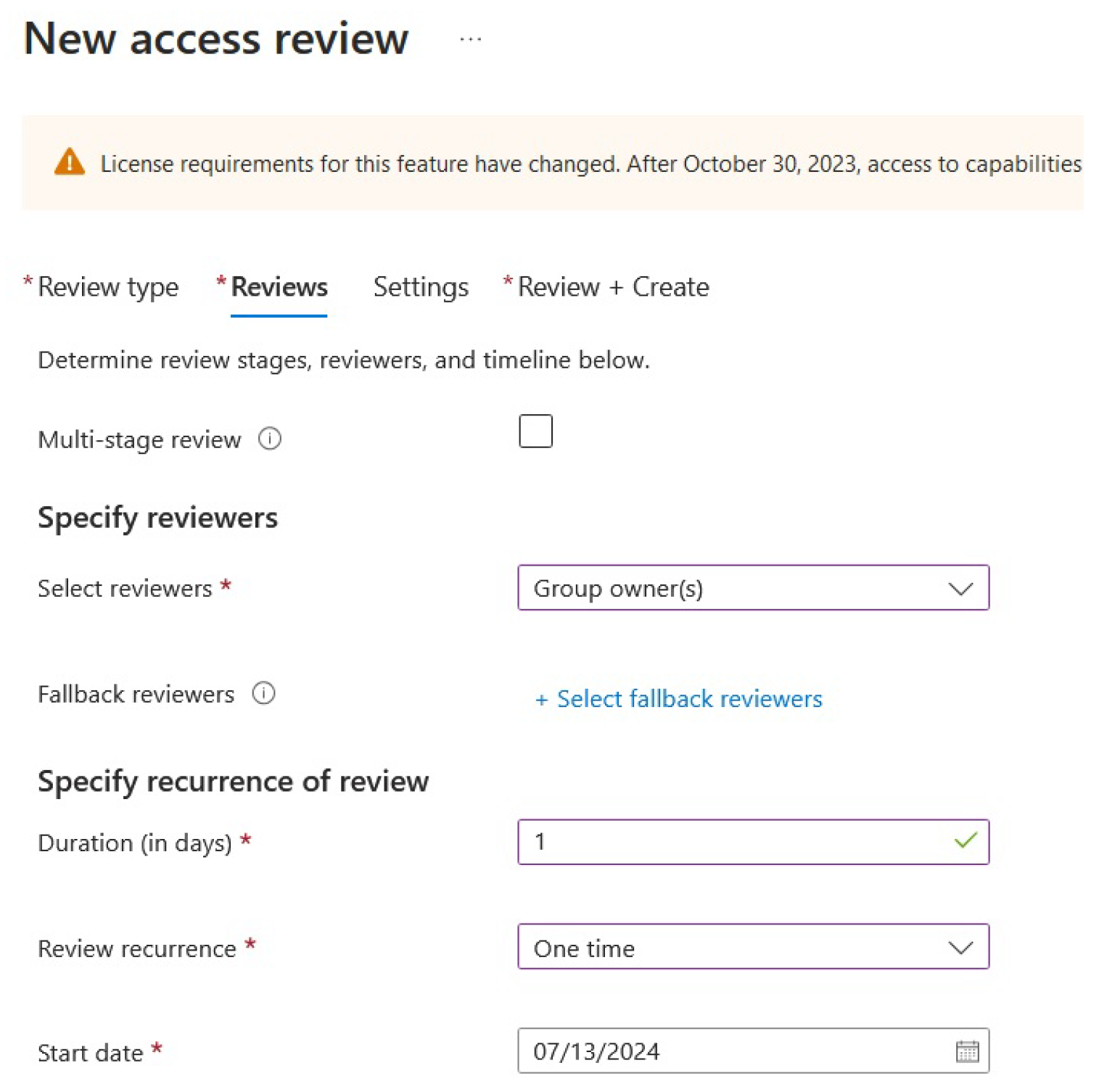
To create an access review, we need an access review scope, for example, a group, as can be seen in
Figure 11:
Figure 10.
Creating an Azure access review.
Figure 10.
Creating an Azure access review.
This implementation method ensures that all members of a particular group will be reviewed. The access review wizard asks for some additional settings, like selecting reviewers, people who will have the chance to do the access review, as can be seen in
Figure 11:
Based on these settings, the group owner will do the review; it will last for one day and will be a one-time occurrence.
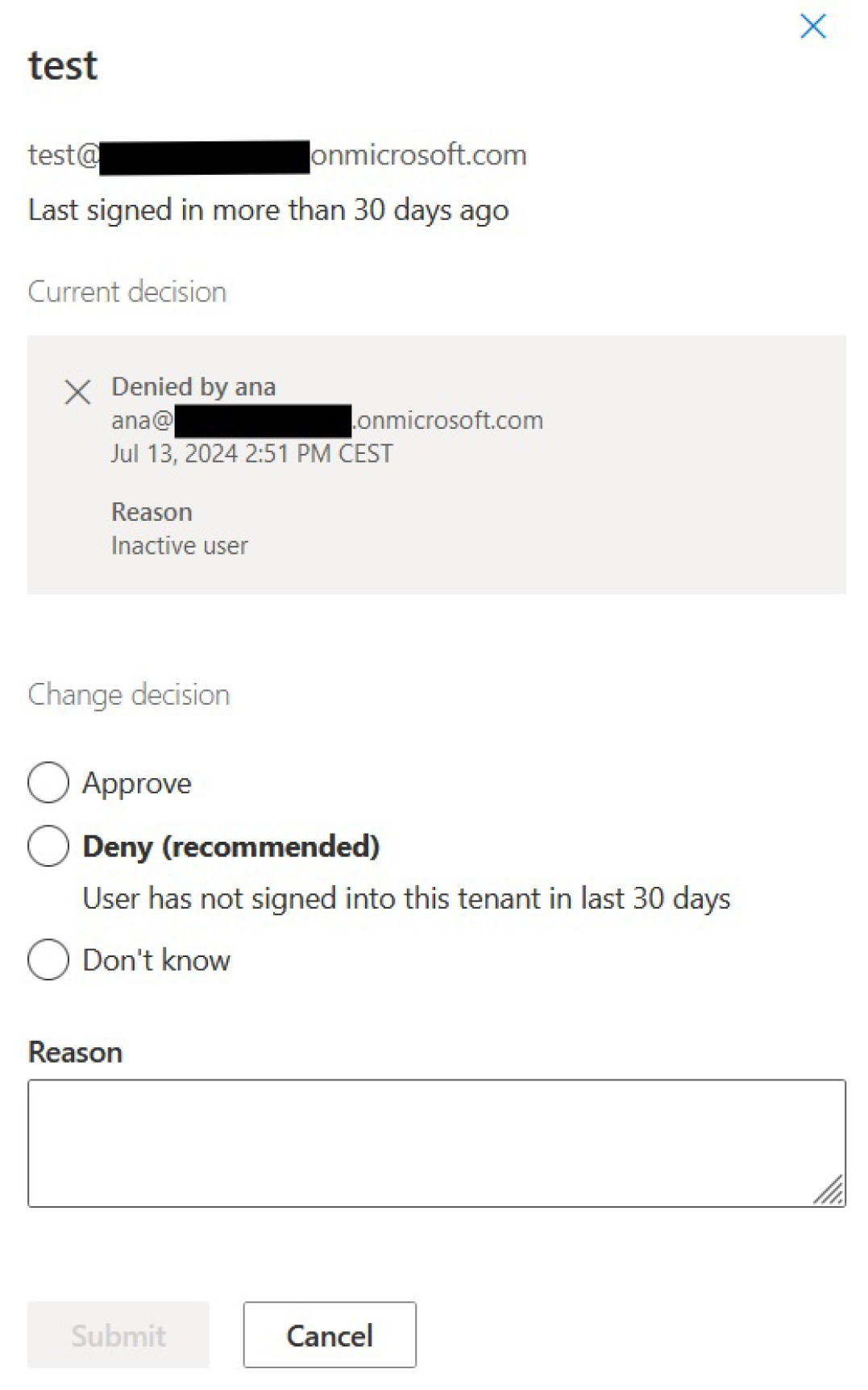
Settings selected in the wizard will configure access review but will not start its implementation. If the reviewer has an email inbox, an email will be there, prompting the start of the review. The other way to begin the review process is from the My Access portal. Let’s say we treat the access review process as an attack and want to deny access. We’d select the necessary settings for that in the My Access/Access reviews tab, as demonstrated in
Figure 12:
The decision can still be changed after it has been made until the review itself ends. An overview of the entire review process can be seen under the Access review details overview window in the Microsoft Entra admin center.
4.4. JIT Access
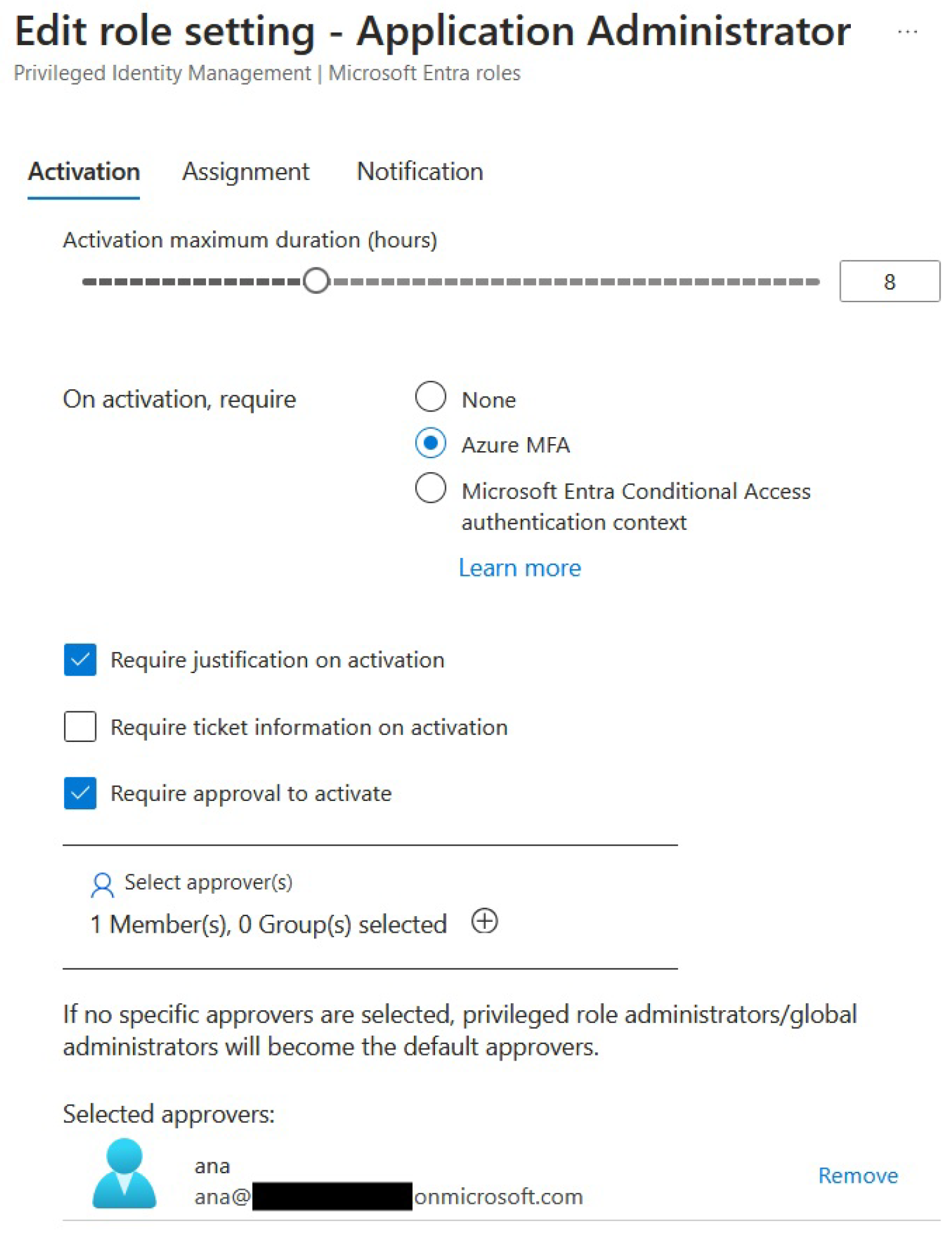
Continuing with the Zero Trust Architecture implementation, Just-In-Time (JIT) access is critical in a Zero Trust Architecture because it minimizes the risk of excessive or unused privileges being exploited by attackers. By granting privileged access only when needed and for a limited duration, JIT access ensures that users have the least amount of privilege necessary to perform their tasks. This reduces the potential attack surface and aligns with the Zero Trust principle of "least privilege." Implementing JIT through Azure's Privileged Identity Management (PIM) helps secure administrative tasks, prevent privilege abuse, and maintain continuous verification. Let’s prepare one of the Azure roles for JIT access, as seen in
Figure 13:
The maximum duration of the activation has been set to 8 hours; the duration of the activation depends on the organization’s needs. We have also checked off the “Require justification on activation” and “Require approval to activate” for extra security.
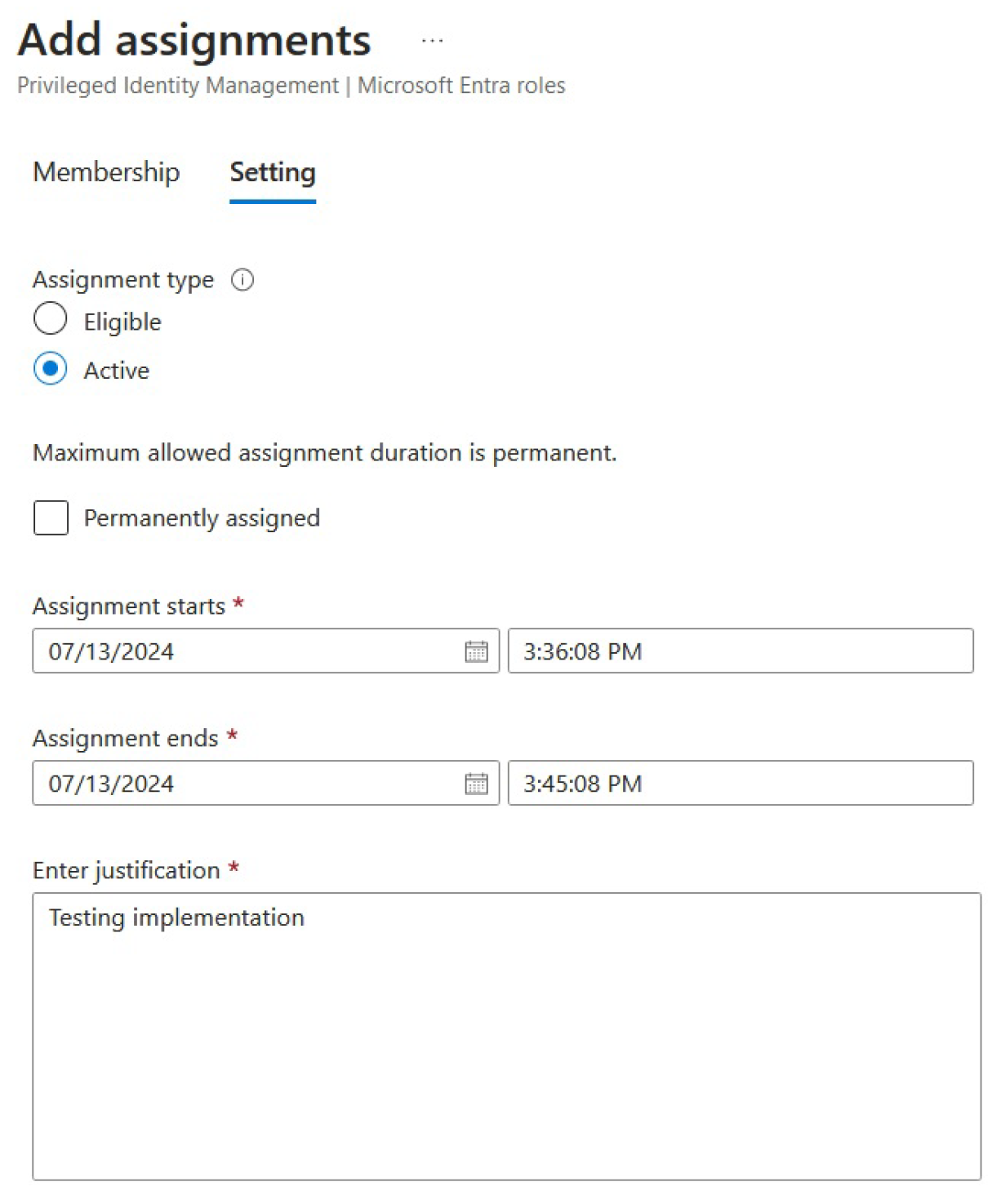
After configuring some of the settings, we can continue to add the assignment to our test user, as shown in
Figure 14:
We can view all added assignments through the Assignments tab for the particular role, where we can also remove, update, or extend them.
4.5. Application of Azure ZTA on Azure Networking
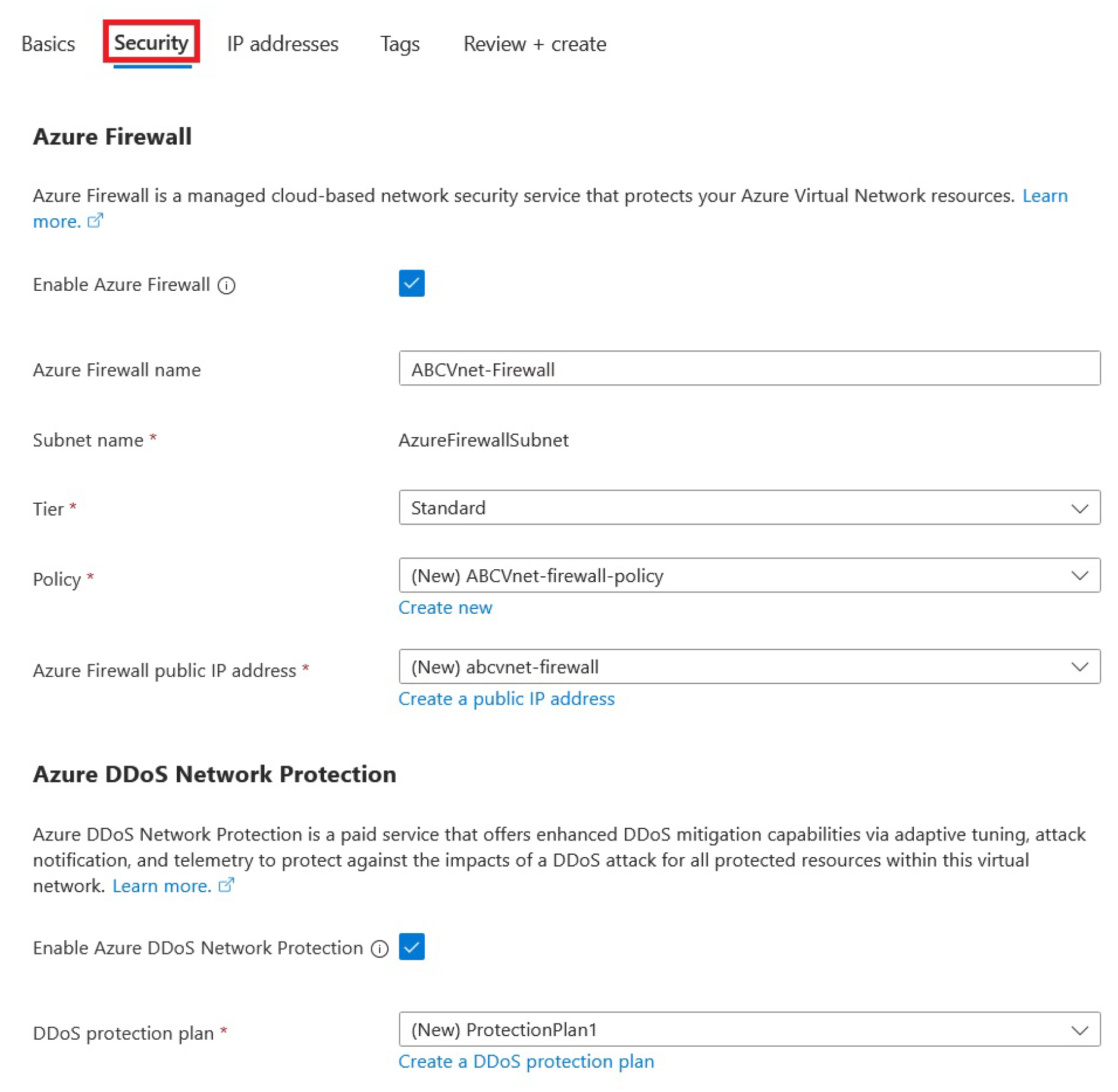
Besides achieving Zero Trust in identity management, it is also important to protect network resources. Achieving Zero Trust with network security in Azure is crucial because it ensures comprehensive protection across all layers of your cloud environment. This approach reduces the attack surface and helps prevent breaches by ensuring that every network transaction is authenticated and authorized. We can do this on any existing or new Azure virtual network by going to the “Security” configuration tab, as can be seen in
Figure 15:
The “AzureFirewallManagementSubnet” is the subnet used for firewall management traffic. It separates the management plane traffic, such as logging, monitoring, and configuration changes, from the data plane traffic for better security and compliance. Therefore, if we create a Virtual Machine and put it in one of those subnets, it will mix VM workloads with firewall operations, which can compromise network security and the firewall's performance.
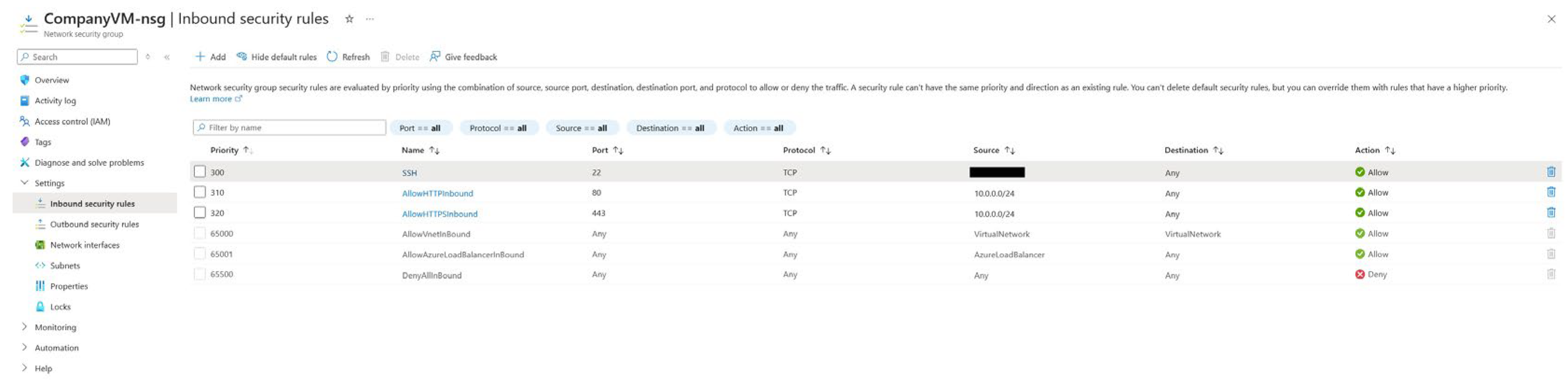
After this configuration, we can use an existing or a new VM and associate it with the Azure virtual network created in the previous step. All configured security settings within the virtual network also apply to the virtual machine. One more configuration for its security is left, configuring its network security group on the network interface card level to provide more granular control of inbound and outbound traffic. It ensures that each VM independently manages its network traffic filtering rather than relying on a centralized firewall for all firewalling tasks, which aligns with the context of Zero Trust networks. We can also use this to provision network security group inbound and outbound rules to standardize inbound and outbound firewall rules for any VM, as can be seen in
Figure 16 for inbound rules:
These inbound rules are standard inbound rules. The SSH connections for testing purposes in this demonstration are only allowed from a specific public IP address, and HTTP and HTTPS traffic is allowed from only select subnets. In this scenario, a company subnet could access an internal site hosted on that virtual machine. This ensures no outsider can access the internal network, strengthening the organization's security posture.
5. Analyzing Azure ZTA Implementation and Its Implications
In our implementation, we successfully established a Zero Trust Architecture using Microsoft Azure. This approach demonstrates how a zero-trust model can protect an organization’s resources by continuously verifying identities and strictly controlling access, thereby reducing the risk of security breaches in a cloud-centric environment.
We implemented Azure ZTA by employing an extensive array of security measures:
Multi-factor authentication is a security measure that mandates using multiple verification methods to gain access, minimizing the chances of illegal access.
Self-Service Password Reset enables users to manage their passwords securely, reducing the need for administrative intervention.
Passwordless Authentication: Mitigates the risks associated with weak passwords, bolstering security.
Access Reviews: Consistently validates permissions to conform with the idea of least privilege.
Just-In-Time Access: Grants temporary authorization to resources, minimizing vulnerability to potential risks.
Network Security Group: manages traffic within Azure, providing an additional layer of network security.
Implementing ZTA guarantees a strong security position by consistently validating access requests, anticipating possible breaches, and reducing vulnerable areas that attacks can target. ZTA, or Zero Trust Architecture, is an active security approach that safeguards sensitive data, ensures adherence to regulatory requirements, and improves overall resilience. ZTA combines these technologies to create a flexible and responsive security framework that effectively safeguards corporate resources and tightly regulates and monitors access, even in the face of changing threats. By employing a holistic approach, the danger of data breaches and illegal access is greatly diminished, creating a secure and compliant IT environment.
It is essential to consider certain disadvantages. Implementing and configuring a Zero Trust Architecture can be intricate and time-intensive, necessitating a substantial commitment in terms of time and experience. Due to duplicate features in multiple locations, the Azure portal can present challenges, particularly for inexperienced users. However, some of these features may not function as intended, exhibiting either bugs or inconsistent results despite being the same feature but in a different location. Organizations lacking a dedicated IT security team may find disabling security settings and establishing customized policies challenging. In addition, although Azure provides a free trial for many services, utilizing advanced capabilities such as Microsoft Entra ID P2 licensing for an extended period incurs extra expenses, which can be significant for large enterprises.
Another possible drawback is the difficulty level involved in handling and keeping the Zero Trust Architecture. Organizations must ensure their staff receive comprehensive training to manage the new security protocols and tools effectively. This may require continuous training and education to stay updated on the ever-changing security threats and updates to Azure services. Organizations must consider these variables regarding improved security and operational benefits to assess whether this approach aligns with their strategic goals and available resources.
6. Future Work
Five major topics should be researched in the future from the perspective of Azure ZTA implementation: complex micro-segmentation, continuous monitoring and analytics, Data Loss Prevention (DLP), more broad integration of Machine Learning (ML) to help with the deployment process, and Secure Access Service Edge (SASE) implementation. We will strengthen our security position by improving our implementation of ZTA, especially for large-scale organizations.
Micro-segmentation divides the network into smaller, distinct sections to limit the lateral expansion of security vulnerabilities. By employing micro-segmentation, we may create specific security protocols that restrict access to essential assets based on specific criteria, such as user roles, device types, and application contexts. This method enhances the system's resistance to attacks and confines any breaches to a particular location, thus avoiding their spread over the entire network. Furthermore, micro-segmentation improves compliance efforts by ensuring that sensitive data remains inside predefined boundaries. This limits the lateral movement of threats and protects sensitive resources by ensuring that only authorized traffic can flow between segments. Azure Virtual Network (VNet) peering allows secure communication between segments, while Azure Security Center provides continuous monitoring and recommendations for segmentation policies.
Consistent surveillance and analysis are essential for maintaining an up-to-date and efficient security posture. Utilizing software like Microsoft Sentinel may obtain real-time and ongoing knowledge of our environment, allowing us to recognize and deal with developing dangers immediately. Sentinel efficiently integrates multiple data sources to provide comprehensive security analytics and threat intelligence. The system employs machine learning and artificial intelligence to identify anomalies and potential security breaches, enabling proactive threat detection and swift crisis response. Continuous monitoring allows us to swiftly adapt to evolving threats and maintain high security across our system.
DLP solutions protect sensitive data by avoiding unauthorized access and unintentional disclosure of information. By enforcing DLP standards, we may efficiently monitor, detect, and stop the transfer of sensitive information across different devices, networks, and cloud platforms. DLP solutions can monitor and control data flow while enforcing rules prohibiting unlawful data transfer. This ensures that confidential information remains within the organization's control. This capability is crucial for protecting intellectual property and personal information and complying with regulatory requirements like GDPR and HIPAA. This is also an area where ML integration might substantially help when dealing with various regulatory compliance frameworks.
SASE combines network security functionalities with wide-area network (WAN) capabilities to create secure connections among users, systems, and devices. The SASE framework integrates several components to make a unified system, such as secure online gateways, cloud access security brokers, firewall-as-a-service, and zero trust network access. This technique ensures the consistent enforcement of security policies, regardless of the user's geographical location, guaranteeing secure and uninterrupted access to applications and data. SASE enables the shift to a decentralized workforce by offering secure remote access and streamlining the administration of multiple security solutions.
By incorporating these technologies into our Zero Trust Architecture (ZTA), we enhance our ability to detect, reduce, and resolve security vulnerabilities, ensuring a strong and secure environment. The subsequent protocols for executing ZTA will aid us in guaranteeing robust security, protecting confidential data, and complying with evolving regulatory requirements.
7. Conclusions
Utilizing Microsoft Azure to implement a Zero Trust Architecture provides notable security benefits. One of the main advantages is the heightened security provided by implementing MFA for all users. This supplementary level of protection guarantees that simply possessing a password is inadequate for gaining access to the system, diminishing the likelihood of unauthorized entry. By implementing conditional access controls, security is strengthened as security requirements are applied dynamically depending on the risk levels of users and devices. This method facilitates the ongoing surveillance and validation of identities, essential for upholding a strong security stance in a cloud-focused setting.
Another benefit is decreasing vulnerable areas targeted for attacks by implementing passwordless authentication techniques like biometrics, hardware tokens, or mobile authenticator apps. These solutions mitigate the risks commonly associated with standard passwords, including using weak passwords, password reuse, and susceptibility to phishing attempts. In Azure's Privileged Identity Management (PIM), the implementation of Just-In-Time (JIT) access guarantees that users are granted just the essential privileges for the shortest possible duration by the Zero Trust principle of least privilege. By doing this, the likelihood of power misuse is reduced, and the overall security architecture is strengthened.
The implementation also incorporates functionalities that enhance user experience and optimize operational efficiency. Implementing self-service password resets decreases reliance on help desk assistance and empowers users to fix account lockouts quickly, ultimately improving user convenience and productivity. Regular access reviews ensure that permissions are consistently updated to align with users' roles and responsibilities, adhering to the zero-trust principle of ongoing verification.
Author Contributions
Conceptualization, V.D.; Methodology, V.D. and Z.M.; Validation, A.K. and Z.M.; Formal analysis, D.R. and A.K.; Investigation, D.R. and A.K; Resources, D.R.; Writing—original draft, Z.M. and D.R.; Writing—review & editing, V.D.; Supervision, V.D.; Project administration, V.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Paul, B.; Rao, M. Zero-Trust Model for Smart Manufacturing Industry. Applied Sciences 2022, 13, 221. [Google Scholar] [CrossRef]
- Thantharate, P.; Thantharate, A. ZeroTrustBlock: Enhancing Security, Privacy, and Interoperability of Sensitive Data through ZeroTrust Permissioned Blockchain. BDCC 2023, 7, 165. [Google Scholar] [CrossRef]
- Federici, F.; Martintoni, D.; Senni, V. A Zero-Trust Architecture for Remote Access in Industrial IoT Infrastructures. Electronics 2023, 12, 566. [Google Scholar] [CrossRef]
- Gupta, A.; Khan, H.; Nazir, S.; Shafiq, M.; Shabaz, M. Metaverse Security: Issues, Challenges and a Viable ZTA Model. Electronics 2023, 12, 391. [Google Scholar] [CrossRef]
- Daah, C.; Qureshi, A.; Awan, I.; Konur, S. Enhancing Zero Trust Models in the Financial Industry through Blockchain Integration: A Proposed Framework. Electronics 2024, 13, 865. [Google Scholar] [CrossRef]
- Awan, S.M.; Azad, M.A.; Arshad, J.; Waheed, U.; Sharif, T. A Blockchain-Inspired Attribute-Based Zero-Trust Access Control Model for IoT. Information 2023, 14, 129. [Google Scholar] [CrossRef]
- Zaid, B.; Sayeed, A.; Bala, P.; Alshehri, A.; Alanazi, A.M.; Zubair, S. Toward Secure and Resilient Networks: A Zero-Trust Security Framework with Quantum Fingerprinting for Devices Accessing Network. Mathematics 2023, 11, 2653. [Google Scholar] [CrossRef]
- Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. Security of Zero Trust Networks in Cloud Computing: A Comparative Review. Sustainability 2022, 14, 11213. [Google Scholar] [CrossRef]
- Alberti, E.; Alvarez-Napagao, S.; Anaya, V.; Barroso, M.; Barrué, C.; Beecks, C.; Bergamasco, L.; Chala, S.A.; Gimenez-Abalos, V.; Graß, A.; et al. AI Lifecycle Zero-Touch Orchestration within the Edge-to-Cloud Continuum for Industry 5.0. Systems. 2024, 12, 48. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture. 2019. [Google Scholar] [CrossRef]
- Teerakanok, S.; Uehara, T.; Inomata, A. Migrating to Zero Trust Architecture: Reviews and Challenges. Secur. Commun. Networks 2021. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A Survey on Zero Trust Architecture: Challenges and Future Trends. Wireless Communications and Mobile Computing 2022. [Google Scholar] [CrossRef]
- Po-Han Ho, Hong-Yen Chen, Tsungnan Lin. Zero Trust Architecture of Token Network. 2023 IEEE International Conference on Metaverse Computing, Networking and Applications (MetaCom), 2023. [CrossRef]
- Chen, X.; Feng, W.; Ge, N.; Zhang, Y. Zero Trust Architecture for 6G Security. arXiv 2022. [Google Scholar] [CrossRef]
- Qazi, F.A. Study of Zero Trust Architecture for Applications and Network Security. 2022 IEEE 19th International Conference on Smart Communities: Improving Quality of Life Using ICT, IoT and AI (HONET), 2022. [Google Scholar] [CrossRef]
- Sarkar, S.; Choudhary, G.; Shandilya, S.K.; Hussain, A.; Kim, H. Security of Zero Trust Networks in Cloud Computing: A Comparative Review. Sustainability 2022. [Google Scholar] [CrossRef]
- Munasinghe, S.; Piyarathna, N.; Wijerathne, E.; Jayasinghe, U.; Namal, S. Machine Learning Based Zero Trust Architecture for Secure Networking. 2023 IEEE 17th International Conference on Industrial and Information Systems (ICIIS), 2023. [Google Scholar] [CrossRef]
- Copeland, M.; Jacobs, M. Azure Network Security Configuration; Springer, 2020. [Google Scholar] [CrossRef]
- Chilberto, J.; Zaal, S.; Aroraa, G.; Price, E. Identity Security with Azure Active Directory; Springer, 2020. [Google Scholar] [CrossRef]
- Stiles, D. The Hardware Security Behind Azure Sphere. IEEE Micro 2019, 39, 20–28. [Google Scholar] [CrossRef]
- Jensen, D. Azure IoT Edge Security. Beginning Azure IoT Edge Computing. 2019. [Google Scholar] [CrossRef]
- Ward, B. Securing Azure SQL; Springer, 2020. [Google Scholar] [CrossRef]
- Chaturvedi, C.; Gupta, B. Cloud Computing Security. Handbook of Research on Intrusion Detection Systems. 2020. [Google Scholar] [CrossRef]
- De Tender, P.; Rendón, D.; Erskine, S. Azure Sentinel (Preview). Pro Azure Governance and Security. 2019. [Google Scholar] [CrossRef]
- Nightingale, E. B. A View from Industry: Securing IoT with Azure Sphere. Proceedings of the 20th International Workshop on Mobile Computing Systems and Applications, 2019. [Google Scholar] [CrossRef]
- Chandrasekara, C.; Herath, P. Azure DevOps Security Options. Hands-on Azure Boards. 2019. [Google Scholar] [CrossRef]
- Ifrah, S. Secure Your Microsoft Azure Containers; Springer, 2020. [Google Scholar] [CrossRef]
- Verma, A.; Malla, D.; Choudhary, A. K.; Arora, V. A Detailed Study of Azure Platform & Its Cognitive Services. 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), 2019; 129–134. [Google Scholar] [CrossRef]
- Tanana, D. Vulnerability Analysis of Azure Blockchain Workbench Key Management System. arXiv 2023. [Google Scholar] [CrossRef]
- Atlidakis, V.; Godefroid, P.; Polishchuk, M. Checking Security Properties of Cloud Service REST APIs. 2020 IEEE 13th International Conference on Software Testing, Validation and Verification (ICST), 2020; 387–397. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture. 2019. [Google Scholar] [CrossRef]
- Teerakanok, S.; Uehara, T.; Inomata, A. Migrating to Zero Trust Architecture: Reviews and Challenges. Secur. Commun. Networks 2021. [Google Scholar] [CrossRef]
- Rose, S. D. Planning for a Zero Trust Architecture. 2021. [Google Scholar] [CrossRef]
- Prydybailo, O. B. Zero trust architecture: the basics organization principles. Connectivity. 2022. [Google Scholar] [CrossRef]
- Chuan, T.; Lv, Y.; Qi, Z.; Xie, L.; Guo, W. An Implementation Method of Zero-trust Architecture. Journal of Physics: Conference Series 2020. [Google Scholar] [CrossRef]
- Ferretti, L.; Magnanini, F.; Andreolini, M.; Colajanni, M. Survivable zero trust for cloud computing environments. Comput. Secur. 2021. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A Survey on Zero Trust Architecture: Challenges and Future Trends. Wireless Communications and Mobile Computing 2022. [Google Scholar] [CrossRef]
- Phiayura, P.; Teerakanok, S. A Comprehensive Framework for Migrating to Zero Trust Architecture. IEEE Access 2023. [Google Scholar] [CrossRef]
- Edo, O. C.; Tenebe, T.; Etu, E.; Ayuwu, A.; Emakhu, J.; Adebiyi, S. Zero Trust Architecture: Trend and Impact on Information Security. International Journal of Emerging Technology and Advanced Engineering 2022. [Google Scholar] [CrossRef] [PubMed]
- Hasan, S.; Amundson, I.; Hardin, D. S. Zero Trust Architecture Patterns for Cyber-Physical Systems. SAE Technical Paper Series. 2023. [Google Scholar] [CrossRef]
- Robinson, P. Why is zero trust so difficult? Computer Fraud & Security 2023. [Google Scholar] [CrossRef]
- Syed, N.; Shah, S. W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero Trust Architecture: A Comprehensive Survey. IEEE Access 2022. [Google Scholar] [CrossRef]
- Paul, B.; Rao, M. Zero-Trust Model for Smart Manufacturing Industry. Applied Sciences 2022. [Google Scholar] [CrossRef]
- D'Silva, D.; Ambawade, D. Building A Zero Trust Architecture Using Kubernetes. 2021 6th International Conference for Convergence in Technology (I2CT), 2021. [Google Scholar] [CrossRef]
- Bertino, E.; Brancik, K. Services for Zero Trust Architectures - A Research Roadmap. 2021 IEEE International Conference on Web Services (ICWS), 2021. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).