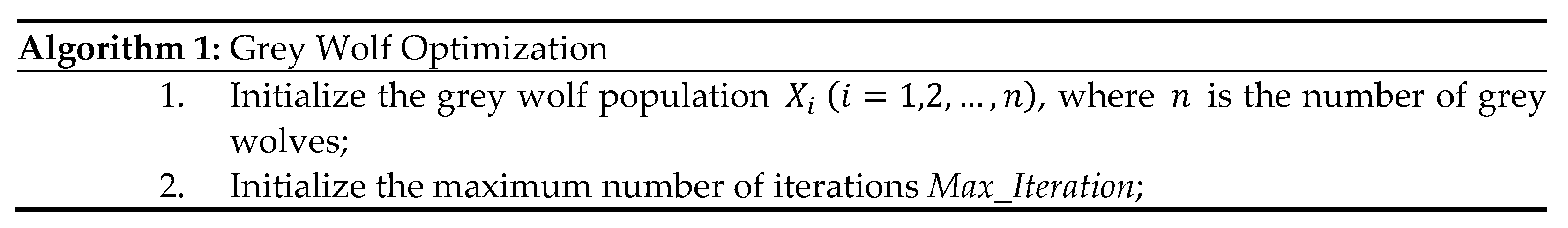1. Introduction
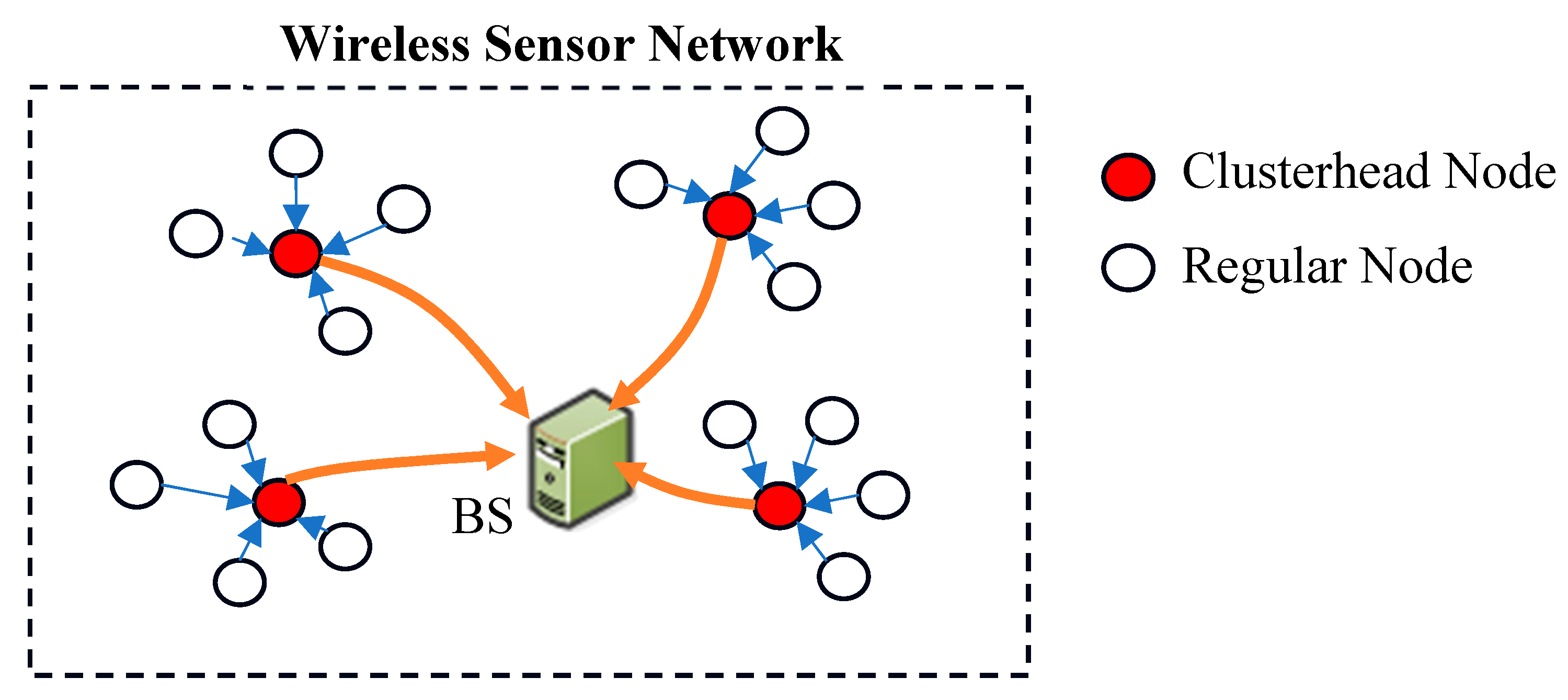
In nature, various micro-sensors are organized to form a sensor network used for monitoring and control purposes. A Wireless Sensor Network (WSN) consists of small, low-power, and inexpensive sensor nodes capable of detecting, measuring, collecting, and processing data from their environment, such as conductivity, temperature, and pressure [
1,
2]. These networks are employed in various applications, including commercial, industrial, military, civil, healthcare, security, and emergency surveillance [
3]. Typically, a large number of these low-cost, multi-functional sensor nodes are randomly distributed over an area of interest. These sensors collaborate to communicate data wirelessly to a base station (BS) and between nodes using multi-hop communication [
4].
Table 1.
List of acronyms.
Table 1.
List of acronyms.
| Acronym |
Description |
| ACO |
Ant Colony Optimization |
| AODV |
Ad hoc On demand Distance Vector |
| ARE |
Average Residual Energy |
| AR-SC |
Adjustable Range Set Covers |
| BACA |
Binary Ant Colony Algorithm |
| BS |
Base Station |
| BSTS |
Bulk Service a Time Scheme |
| CCA |
Clear Channel Assessment |
| CCBE |
Cross-layer Cluster-Cased Energy-efficient |
| CEE |
Cross-layer Energy Efficiency |
| CGA |
Chaotic Genetic Algorithm |
| CH |
Clusterhead |
| CL-MAC |
Cross-Layer MAC |
| CREC |
Cross-layer, Reliable, and Efficient Communication protocol |
| CSMA/CA |
Carrier Sense Multiple Access with Collision Avoidance |
| DLC |
Data Link Control |
| DWEHC |
Distributed Weight Based Energy-Efficient Hierarchical Clustering |
| EAP-CMAC |
Energy Aware Physical-layer Network Cooperative MAC |
| ECC |
Error Correction Codes |
| ECCA |
Enhanced Clear Channel Assessment |
| EEUC |
Energy-Efficient Unequal Clustering |
| EOAMRCL |
Energy Optimization Approach based on MAC/Routing Cross-Layer |
| EQPD-MAC |
Energy-aware QoS MAC protocol based on Prioritized Data andMulti-hop routing |
| FIS |
Fuzzy Inference System |
| FND, HND, LND |
First Node Dead, Half of Nodes Dead, Last Node Dead |
| FQA |
Fuzzy Logic with a Quantum Annealing Algorithm |
| GCRAD |
Cross-layer Routing for Disaster |
| GCWGC |
Greedy Coverage Weighted Communication |
| GWO |
Grey Wolf Optimization |
| HC |
Hill Climbing |
| HEED |
Hybrid Energy-Efficient Distributed Clustering |
| IoT |
Internet of Things |
| IP |
Internet Protocol |
| LEACH |
Low-Energy Adaptive Clustering Hierarchy |
| MAC |
Medium Access Control |
| NAV |
Network Allocation Vector |
| NS2 |
Network Simulator version 2 |
| OCCH |
Optimized Connected Coverage Heuristic |
| OSI |
Open Systems Interconnection |
| OSTS |
One Service a Time Scheme |
| OTTC |
Overlapping Target and Connected Coverage |
| PHY |
Physical Layer |
| PNC |
Physical Layer Network Coding |
| QoS |
Quality of Service |
| RSSI |
Received Signal Strength Indication |
| SA |
Simulated Annealing |
| TCP |
Transmission Control Protocol |
| TDMA |
Time-Division Multiple Access |
| TSLC |
Topological Structure by Layered Configurations |
| WSN |
Wireless Sensor Network |
WSNs offer significant advantages such as scalability, simplicity, ease of deployment, and self-organizing capabilities [
5]. However, the communication process in WSNs is energy-intensive because each node acts as a relay, forwarding received information to its neighbors until it reaches the BS. Compared to wired sensor networks, WSNs face limitations including restricted battery power, limited memory and processing capacity, non-rechargeable batteries, environmental constraints, lack of global addressing, security issues, mobility challenges, and short communication ranges [
6]. Sensor nodes in WSNs are often powered by small batteries with limited capacity [
7], making energy efficiency crucial for extending the network's lifespan [
8,
9]. In challenging environments such as monitoring volcanoes, replacing the batteries is difficult and necessitates a longer operating period [
10]. Thus, developing energy-efficient routing strategies to minimize battery usage is essential for WSNs [
9,
11]. Various approaches have been employed to conserve energy in nodes, utilizing routing protocols from the physical layer to the network layer to improve data collection methods [
12]. Achieving energy balance across different sensor nodes remains a primary concern in sensor network design, as the power usage of nodes varies depending on application demands. Wireless sensors are often deployed in harsh environments where they cannot be replaced or recharged [
13].
Recent research literature has proposed several strategies to increase the lifetime of WSNs, including transmission range optimization, power-saving sleep modes, low-power hardware designs, and power-aware protocols [
14]. Consequently, various routing and Medium Access Control (MAC) protocols have been developed to address these issues, enabling faster and more cost-effective information delivery to the BS. WSN nodes typically face constraints in energy, processing power, and memory. Therefore, it is essential to conduct research and development on low-computation, resource-aware algorithms for WSNs, focusing on small, embedded sensor nodes with limited resources. Given the critical importance of energy consumption in WSNs, specific hardware and algorithms [
15] have been designed with energy efficiency or awareness as a primary focus. Methods such as fuzzy clustering, nano topology, and rough set theory are applied, especially to identify abnormalities in sensor networks [
16].
The protocol stack in a WSN combines elements of the TCP/IP and OSI models. The data link, network, and physical layers are the most studied in the literature for reducing energy consumption in WSNs. The primary purpose of the network layer is routing, facilitated by the routing protocol, which determines the path between transmitting and receiving nodes to enable effective data transport. The data link layer comprises two sublayers: DLC (Data Link Control), responsible for multiplexing and error management, and MAC, which handles channel access and scheduling. The physical layer is accountable for data encryption, frequency generation, and modulation [
17].
Within a layered architecture, each layer has independent functionality and can only use the services provided by the layer directly below it. Therefore, communication is restricted to adjacent layers. Conversely, the cross-layer technique allows any layer to utilize services from any other layer. This interaction between different layers of the network protocol stack enhances WSN performance. Cross-layer designs have identified six options based on potential interactions between the routing, MAC, physical, and application layers [
18].
This paper makes several key contributions to the field of WSN clustering:
Designed a novel cross-layer protocol targeting the MAC and network layers.
Optimized clustering by identifying optimal CHs based on residual energy, intra-cluster distances, and inter-cluster distances.
Implemented a robust objective function for CH selection.
Utilized Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) and Network Allocation Vector (NAV) for active mode/sleep mode management.
Highlighted the effectiveness of cross-layer designs in peer protocols, and identified key strategies from these protocols to inform the development of our own.
Conducted extensive simulations comparing our protocol with peers.
Demonstrated superior performance of EOAMRCL in terms of overall network remaining energy, number of dead nodes, total data received at the BS and network lifetime.
Validated the effectiveness of our cross-layer approach in reducing energy consumption and enhancing network performance.
The remainder of the paper is structured as follows:
Section 2 reviews related works and discusses the incorporation of OSI layers in WSN clustering.
Section 3 details the integration of WSN node sleep scheduling into the CSMA/CA mechanism.
Section 4 introduces the fundamentals of the Grey Wolf Optimization (GWO) algorithm and its application in optimization.
Section 5 outlines our proposed Energy Optimization Approach based on MAC/Routing Cross-Layer (EOAMRCL).
Section 6 evaluates the performance of the proposed approach through simulation results and analysis. Finally,
Section 7 concludes the study with final remarks and future perspectives.
2. Incorporating OSI Layers in WSN Clustering
The cross-layer protocol design has become a key focus in recent network research, especially in WSNs, as it plays a crucial role in developing new protocols that address the challenge of energy saving within the constraints of WSNs. By leveraging the cross-layer principle, this approach significantly increases energy efficiency, thereby enhancing overall network performance.
Sakib et al. [
19] propose the EQPD-MAC (Energy-aware QoS MAC protocol based on Prioritized Data and Multi-hop routing) protocol, an innovative solution designed to address energy efficiency and Quality of Service (QoS) challenges in WSNs. The EQPD-MAC protocol integrates prioritized data handling with multi-hop routing to ensure the timely delivery of high-priority packets while conserving energy. This approach is particularly crucial in WSNs where energy resources are limited and efficient data transmission is necessary for maintaining network functionality. The methodology behind EQPD-MAC involves an adaptive active/sleep time mechanism aimed at minimizing idle listening and reducing overall energy consumption. By implementing a cross-layer communication strategy that incorporates the Ad hoc On demand Distance Vector (AODV) routing protocol, EQPD-MAC achieves efficient multi-hop routing. The protocol supports four levels of packet priority, dynamically adjusting active times based on the network load to optimize performance. This ensures that high-priority data packets are delivered promptly, enhancing the QoS of the network. The EQPD-MAC protocol was implemented and tested using the Castalia Simulator, with performance comparisons made against three other QoS MAC protocol. The results demonstrated that EQPD-MAC significantly reduced sensor node energy consumption by up to 30.3%, per-bit energy consumption by up to 29.6%, and sink node energy consumption by up to 27.4%. Additionally, EQPD-MAC increased throughput by up to 23.3% compared to the other protocols, showcasing its superior energy efficiency and network performance. Advantages of the EQPD-MAC protocol include its superior energy efficiency achieved through adaptive active/sleep times, effective handling of multi-priority packets ensuring timely delivery of critical data, enhanced throughput, and reduced latency.
Wang et al. [
20] propose a novel hybrid clustering and routing protocol for WSNs that combines Fuzzy Logic with a Quantum Annealing algorithm (FQA) to enhance network stability and minimize energy consumption. The Fuzzy Inference System (FIS) is employed to select appropriate CHs based on parameters such as residual energy, number of neighbors, distance to the BS, and node centrality. During the routing phase, the quantum annealing algorithm is utilized to find the optimal route from the CHs to the BS, enhancing energy efficiency. The authors introduce an on-demand re-clustering mechanism that reduces computation time and overhead compared to periodic clustering methods. An energy threshold is defined to filter candidate CHs, further optimizing the process. The FQA protocol is evaluated against peer protocols across various scenarios, showing superior performance in terms of energy consumption, network lifetime, number of alive nodes, and throughput. Simulation results demonstrate that the proposed FQA protocol significantly outperforms the compared protocols, achieving better energy efficiency and network performance. This hybrid approach leverages the strengths of fuzzy logic for CH selection and the global optimization capability of quantum annealing for routing, providing a robust solution for energy-efficient WSN management.
Xenakis et al. [
21] employed Simulated Annealing (SA) to address the significant challenge of energy loss and node placement in WSNs. Their research focuses on optimizing the energy efficiency of topology control, power management, and packet transmission within WSNs. By leveraging SA, they aim to find optimal solutions for deploying network topologies that meet both coverage and connectivity requirements. Their approach involves several key strategies. Firstly, they optimize the network's topology to ensure that sensor nodes are deployed in a manner that maximizes coverage while maintaining necessary connections. This involves careful placement of nodes to achieve the best possible balance between coverage and connectivity, thereby minimizing energy wastage. Additionally, Xenakis et al. address power control by implementing Error Correction Codes (ECC) at the MAC layer, which helps in transmitting data packets more reliably and with reduced energy consumption. At the physical layer, they control power usage to further enhance energy efficiency. These combined strategies aim to reduce the average power dissipation across the network. Their findings suggest that using SA to deploy an almost optimal topology significantly lowers power consumption and improves network coverage compared to traditional random sampling heuristics. The use of SA allows for a more systematic and efficient exploration of the possible configurations, leading to better overall performance in terms of energy usage and network lifespan. Moreover, by integrating ECC at the MAC layer, the protocol ensures that data packets are transmitted with higher reliability, reducing the need for retransmissions and thus saving energy. This layered approach, which simultaneously addresses topology control, power management, and packet transmission, demonstrates a comprehensive method for enhancing WSN performance. Xenakis et al.'s work underscores the effectiveness of combining advanced optimization techniques like SA with energy-efficient protocols to tackle the inherent challenges of WSNs. Their research provides valuable insights into how systematic optimization can lead to significant improvements in both energy consumption and network reliability, paving the way for future innovations in WSN design and management.
EAP-CMAC, a novel cooperative MAC protocol proposed by Sami et al. [
22], stands for Energy Aware Physical-layer Network Cooperative MAC. This protocol is designed for ad hoc wireless networks, blending collaborative communication with physical layer network coding (PNC). The EAP-CMAC protocol dynamically selects the optimal transmission mode among three options: classic collaboration, direct transmission, and PNC-based transmission. This selection process considers the quality of the source-to-destination connection and the status of the destination queue. One of the key innovations of EAP-CMAC is its combined approach to power allocation and relay selection. This approach takes into account the residual energy of nodes and their positional information, aiming to minimize power dissipation and significantly extend the network's lifespan. By optimizing power distribution and relay choices based on these factors, the protocol enhances energy efficiency across the network. To rigorously evaluate the performance of EAP-CMAC, Sami et al. presented a 3D Markov model. This model analyzes the protocol's operation and estimates the probability of successful data transfer within the network. Additionally, the protocol introduces a precise NAV parameter to increase spatial reuse, further improving network efficiency. Analytical research and simulation results demonstrate that EAP-CMAC outperforms other methods focused on network lifespan extension. The optimal power distribution strategy employed by EAP-CMAC enhances network lifespan performance by 7% compared to an equal power distribution approach. This significant improvement underscores the effectiveness of the protocol's power allocation and relay selection mechanisms. Furthermore, the protocol's ability to adaptively choose the best transmission mode based on real-time network conditions ensures robust and efficient communication. This adaptability, coupled with strategic power management, makes EAP-CMAC a highly effective solution for enhancing the longevity and performance of ad hoc wireless networks. Sami et al.'s work highlights the critical importance of integrating collaborative communication and advanced network coding techniques to achieve superior energy efficiency and network lifespan. Their research provides a valuable framework for future developments in cooperative MAC protocols, showcasing the potential for significant advancements in the field of ad hoc wireless networks.
Niroumand et al. [
23] proposed a novel cross-layer geographic routing approach for WSNs tailored for disaster relief operations, named Geographic Cross-layer Routing for Disaster (GCRAD). This innovative solution integrates routing and MAC layer functions through a unified route formation method for relay selection. GCRAD evaluates several criteria for relay selection, including the number of prospective relay nodes, the state of the node queue, and the distance from the BS. By incorporating these criteria into a single phase, GCRAD effectively eliminates inefficient transmissions, shortens the communication process, and minimizes collision probabilities. This streamlined approach enhances the efficiency of the routing process, making it particularly suitable for the high-demand, time-sensitive scenarios often encountered in disaster relief operations. The GCRAD protocol's design aims to address the unique challenges posed by disaster-related traffic, where rapid and reliable communication is critical. By focusing on a comprehensive set of relay selection criteria, GCRAD ensures that the most suitable relay nodes are chosen, thereby optimizing the overall network performance. Simulation results using the NS2 simulator demonstrate that GCRAD significantly reduces power consumption, end-to-end latency, and improves the delivery rate compared to advanced inter-geographic routing strategies. The protocol's ability to reduce power consumption is crucial in disaster scenarios where energy resources are limited and replenishment may not be feasible. Moreover, GCRAD's reduction in end-to-end latency ensures that critical information is relayed swiftly across the network, which is vital for effective disaster response. The protocol's improved delivery rate indicates its robustness in maintaining reliable communication even under the stressful conditions typical of disaster environments. Niroumand et al.'s research highlights the importance of cross-layer integration in enhancing the performance of WSNs for disaster relief. Their work provides valuable insights into how geographic routing strategies can be optimized through cross-layer design, leading to more efficient and reliable communication networks. The GCRAD protocol sets a precedent for future research and development in the field, demonstrating that a well-designed cross-layer approach can address the complex requirements of disaster relief operations. By ensuring energy efficiency, reducing latency, and maintaining high delivery rates, GCRAD contributes to the advancement of WSN technology in critical applications.
Mohamed et al. [
24] conducted an in-depth analysis of four representative connected coverage algorithms: Adjustable Range Set Covers (AR-SC), Optimized Connected Coverage Heuristic (OCCH), Greedy Coverage Weighted Communication (GCWGC), and Overlapping Target and Connected Coverage (OTTC). Their study focused on evaluating the characteristics and performance of these recent energy-efficient coverage strategies within the context of Industrial WSNs (IWSNs). The researchers performed extensive comparisons to integrate the features of fundamental design concepts aimed at maximizing connectivity and coverage of IWSNs. These comparisons were based on several critical metrics, including average power consumption, network lifespan, dead node rate, and coverage time. By simulating various network properties within a noisy environment, they aimed to achieve optimal network coverage. Each of the four algorithms was examined for its suitability in different industrial domains based on its coverage features. For instance, AR-SC focuses on adjusting the sensor range to form optimal coverage sets, whereas OCCH employs heuristics to enhance connected coverage efficiently. GCWGC utilizes a greedy approach to balance coverage and communication weights, and OTTC aims to overlap target areas while maintaining connectivity. The study revealed that achieving uniform performance across all metrics is challenging. Consequently, the selection of a hedging algorithm should be tailored to the specific requirements of the practical application. Factors such as maximum longevity, convergence speed, and other essential performance metrics must be considered when choosing the most appropriate algorithm. Once the primary performance criterion is identified, efforts can be directed toward optimizing additional parameters to enhance overall network performance. This research provides valuable insights for IWSN designers, offering them the knowledge to select practical hedging approaches that meet expected performance metrics in various industrial applications. By understanding the strengths and limitations of each algorithm, designers can make informed decisions that align with their specific operational needs. Mohamed et al.'s work highlights the importance of tailored algorithm selection in the context of IWSNs. Their comprehensive analysis demonstrates that while no single algorithm excels in all aspects, each has distinct advantages that can be leveraged depending on the application. This approach ensures that IWSNs can achieve optimal performance, reliability, and energy efficiency in diverse industrial environments.
A novel Cross- Layer MAC (CL-MAC) protocol [
25] has been developed for WSNs to effectively manage multi-stream, multi-packet, and multi-hop traffic patterns while accommodating varying traffic loads. The CL-MAC protocol is designed around a stream configuration packet structure that utilizes routing data to efficiently transport multiple data packets across different multi-hop streams. The core functionality of CL-MAC involves evaluating all neighboring flow configuration requests and packets held within the buffer of the routing layer when constructing a flow. This comprehensive assessment allows CL-MAC to make informed decisions about scheduling based on the current state of the network. By doing so, the protocol can dynamically adjust its methods to optimize performance under varying conditions. One of the key features of CL-MAC is its ability to adapt to the real-time network environment, ensuring efficient data transmission even under high traffic loads. This adaptability is crucial for maintaining high performance in WSNs, where traffic patterns can be unpredictable and variable. The efficacy of CL-MAC was thoroughly examined using the ns2 simulator, and its performance was compared to other protocols across various network configurations and under different load and traffic conditions. The simulation results demonstrated that CL-MAC significantly enhances the delivery rate and reduces end-to-end delay. Furthermore, it achieves these improvements while also lowering the average power consumption per transmitted packet. These findings highlight the potential of CL-MAC to provide superior performance in terms of energy efficiency and data delivery reliability. By leveraging cross-layer design principles, CL-MAC can coordinate between different protocol layers to optimize resource use and network performance. The development of CL-MAC addresses several critical challenges in WSNs, such as managing diverse traffic patterns and maintaining energy efficiency. Its ability to handle multiple streams and packets concurrently, while adjusting to network conditions, makes it a robust solution for various WSN applications. Moreover, the reduction in end-to-end delay ensures timely data delivery, which is essential for applications that require real-time monitoring and rapid response. The lower power consumption per packet extends the overall network lifespan, making CL-MAC an energy-efficient choice for long-term deployments.
Kannughatta et al. [
26] proposed an innovative MAC protocol designed to enhance energy efficiency in WSNs by utilizing a leader-follower communication technique. This protocol aims to eliminate intra-area collisions and minimize inter-area collisions through the implementation of two distinct MAC protocol stacks. The proposed MAC protocol introduces a sleep schedule to conserve idle power by employing a duty cycle mechanism. This duty cycle ensures that nodes alternate between active and sleep states, thereby reducing unnecessary energy consumption when nodes are idle. By effectively managing the activity periods of sensor nodes, the protocol significantly extends the overall network lifespan. In their study, Kannughatta et al. explored current MAC protocols to identify the most effective strategies for achieving energy efficiency. They found that the leader-follower communication technique was particularly effective in coordinating data transmission within the network. The leader node handles the majority of communication tasks, while follower nodes remain in a low-power sleep state until they are needed. This approach not only reduces energy consumption but also helps in organizing the network's communication structure more efficiently. The dual MAC protocol stacks play a crucial role in the proposed solution. One stack is dedicated to managing intra-area communications, ensuring that data transmissions within a specific area are collision-free. The second stack handles inter-area communications, focusing on reducing collisions between different areas of the network. This dual-stack approach enhances the protocol's ability to manage complex traffic patterns and maintain high performance under varying network conditions. Simulation results demonstrated the effectiveness of the proposed MAC protocol in comparison to the most commonly used MAC protocols in WSNs. The results showed significant improvements in energy efficiency, with reduced collision rates and lower power consumption. These enhancements translate into a longer network lifespan and more reliable data transmission. The introduction of a sleep schedule and duty cycle mechanism ensures that the protocol can adapt to the network's real-time conditions, making it suitable for various WSN applications. The leader-follower technique provides a structured approach to data transmission, reducing the overall energy expenditure and improving network efficiency.
Weiwei et al. [
27] proposed a novel protocol named CREC (Cross-layer, Reliable, and Efficient Communication protocol) based on the innovative concept of node initiative. This approach allows for the integration of multiple functions within a unified protocol framework, significantly enhancing the overall communication operations in WSNs. The CREC protocol offers several key features, including dispersed congestion management, robust geographic routing, and medium access contention networking. These features are designed to optimize energy efficiency, ensure the fidelity of sensory data, and account for physical channel effects, thereby facilitating efficient and reliable data transmission. One of the core innovations of the CREC protocol is its focus on node initiative, which empowers individual nodes to perform multiple roles within the network. This capability allows nodes to dynamically adapt to changing network conditions and requirements, ensuring that communication remains efficient and reliable. By integrating these functions into a single framework, CREC minimizes the complexity and overhead typically associated with multi-layer systems. Dispersed congestion management is a critical component of CREC, helping to prevent data bottlenecks and ensuring smooth data flow across the network. This feature is particularly important in WSNs, where congestion can lead to increased energy consumption and reduced network performance. By managing congestion effectively, CREC enhances the overall efficiency of the network. Robust geographic routing within CREC ensures that data packets are transmitted through the most efficient paths, taking into account the geographic positions of nodes. This routing strategy reduces the likelihood of packet loss and ensures timely data delivery, which is essential for maintaining the accuracy and reliability of sensory data. Medium access contention networking is another vital aspect of CREC, enabling nodes to access the communication medium in an orderly manner. This feature reduces collisions and ensures that data packets are transmitted without interference, further improving the reliability of data transmission. Simulation results demonstrate that the CREC protocol significantly improves energy usage and network performance compared to previously suggested multi-layer systems. The protocol's ability to optimize energy consumption while maintaining high levels of data fidelity and transmission reliability makes it a valuable solution for WSNs.
Jun et al. [
28] proposed an innovative routing algorithm named Topological Structure by Layered Configurations (TSLC) to enhance the performance quality of data transmission in WSNs. This algorithm leverages the cross-layer design technique to integrate the functionalities of the network and MAC layers, thereby optimizing the overall network performance. The TSLC algorithm operates by dynamically accessing and utilizing the status information of network nodes across both the MAC and network layers. This cross-layer approach allows for more informed decision-making regarding routing and data transmission, ultimately leading to more efficient network operations. One of the primary goals of the TSLC algorithm is to conserve energy across the entire network. By intelligently managing the routing paths and data transmission processes, TSLC minimizes energy consumption, which is critical for extending the lifespan of WSNs. The algorithm achieves this by selecting optimal routes that reduce the number of transmissions and retransmissions, thereby conserving the battery life of individual sensor nodes. In addition to energy conservation, the TSLC algorithm also aims to prolong the overall network lifespan. By ensuring that energy consumption is balanced across all nodes and avoiding the premature depletion of any single node's battery, the algorithm maintains network functionality for a longer period. This is particularly important in WSNs deployed in remote or inaccessible areas where node replacement or recharging is not feasible. The cross-layer design of the TSLC algorithm also contributes to improving the service performance quality of the network. By coordinating the activities of the MAC and network layers, the algorithm can reduce latency, improve data throughput, and enhance the reliability of data transmission. This results in a higher QoS for applications relying on WSNs, such as environmental monitoring, industrial automation, and security surveillance. Simulation results demonstrate the effectiveness of the TSLC algorithm in achieving its design goals. The algorithm shows significant improvements in energy savings, network lifespan, and service performance quality compared to traditional routing algorithms. These results validate the benefits of the cross-layer design approach and highlight the potential of TSLC to enhance the efficiency and reliability of WSNs.
To address the challenges of high energy consumption, collision detection, transmission delay, and throughput in mobile WSNs (MWSN), Xin et al. [
29] proposed a Cross-layer Energy Efficiency (CEE) model. This innovative model integrates three critical layers: the physical layer (PHY), the MAC layer, and the network layer, each contributing to enhanced network performance. The CEE model employs full-duplex interfaces in the PHY layer, allowing simultaneous transmission and reception of data, which significantly reduces the time required for data exchange and minimizes collision occurrences. This feature is crucial for improving the overall data throughput and reducing transmission delays in MWSNs. In the network layer, the CEE model focuses on the strategic placement of nodes. By optimizing node placement, the model ensures efficient coverage and connectivity, which are essential for reducing energy consumption and enhancing network reliability. Proper node placement also helps in minimizing the distance over which data must be transmitted, thereby conserving energy and prolonging the lifespan of the sensor nodes. The MAC layer within the CEE model incorporates an advanced MAC protocol designed to manage data access and transmission effectively. This protocol reduces the likelihood of collisions and ensures that data packets are transmitted in an orderly and efficient manner. By coordinating the activities of sensor nodes, the MAC protocol helps in maintaining a low level of energy consumption and improves the overall efficiency of the network. Compared to existing models, the CEE model offers several significant advantages. In terms of power control, the model dynamically adjusts the power levels used for data transmission, ensuring that energy is used efficiently without compromising the quality of communication. This adaptive power control mechanism is essential for maintaining energy efficiency across the network. The CEE model also excels in reducing transmission delays and improving throughput. By leveraging full-duplex communication and optimizing the MAC protocol, the model ensures that data packets are delivered promptly and reliably. This is particularly important in MWSNs, where timely data transmission is critical for many applications, including those in the Internet of Things (IoT). Performance assessments of the CEE model demonstrate its effectiveness in minimizing energy dissipation and outperforming other transmission models. The results indicate that CEE can be effectively utilized in practical MWSN deployments, offering a robust solution for enhancing energy efficiency and network performance.
Mammu et al. [
30] introduced a novel method called interlayer Cluster-Based Energy-efficient routing (CCBE) to extend the network lifespan and enhance the energy efficiency of WSNs. The CCBE approach organizes nodes into hexagonal architectures, with each hexagonal group comprising a CH and several cluster members. The CCBE method begins with the CH selection process, which considers both the distance from the BS and the remaining energy of the nodes. This dual consideration ensures that the chosen CHs are optimally positioned to minimize energy consumption during data transmission and are capable of managing the network's energy resources effectively. By selecting CHs with higher residual energy and closer proximity to the BS, the protocol reduces the energy expenditure associated with long-distance transmissions. Once the CHs are selected, a contention-free protocol is implemented to prevent collisions during transmission operations. This protocol ensures that data packets are transmitted without interference, which is crucial for maintaining efficient communication and conserving energy. The CH then assigns transmission slots to each cluster member based on their remaining energy levels. This slot assignment strategy aims to extend the sleep duration of nodes with lower energy reserves, thereby conserving their battery life and balancing the overall energy consumption within the network. The effectiveness of the CCBE protocol was demonstrated through simulations, which showed that it outperforms the Hybrid Energy-Efficient Distributed Clustering (HEED) ( ) and Low-Energy Adaptive Clustering Hierarchy (LEACH) () protocols in terms of energy dissipation, network lifespan, and throughput. The simulation results highlighted that CCBE's approach to CH selection, collision prevention, and energy-aware slot assignment significantly enhances the energy efficiency and longevity of WSNs. By organizing nodes into hexagonal clusters and optimizing CH selection, CCBE minimizes the energy required for data transmission and reduces the likelihood of collisions. The protocol's energy-aware slot assignment further ensures that the network's energy resources are used efficiently, allowing for longer operational periods without the need for battery replacement or recharging. Mammu et al.'s research underscores the importance of interlayer strategies in enhancing the performance of WSNs. The CCBE protocol's comprehensive approach to energy management and efficient data transmission provides a robust framework for improving the sustainability and reliability of WSNs. By addressing key challenges such as energy dissipation, collision prevention, and balanced energy consumption, CCBE offers a practical solution for extending the lifespan of sensor networks.
Kurian et al. [
31] addressed the challenge of optimal sensor placement in WSNs to enhance sensing coverage, taking into account sensor limitations such as energy, communication distance, and sensing range. They aimed to optimize sensor placement using a variant of the Ant Colony Optimization (ACO) algorithm, known as the Binary Ant Colony Algorithm (BACA), and integrated it with other optimization algorithms like Hill Climbing (HC) and SA. ACO simulates the search process carried out by ants when looking for food. Each ant makes a random probabilistic path, representing a possible solution. Ants leave a pheromone trail to trace their way back to the colony. When an ant finds a shorter path, it strengthens the pheromone trail by repeatedly traveling back and forth, encouraging other ants to follow the optimized route. If another ant discovers a better path, it updates the pheromone trail, continuously improving the solution until an optimal path is found after several iterations. The BACA algorithm differs from ACO in that it makes binary path decisions (0 or 1), indicating whether a sensor is in sleep or active mode, with the goal of optimizing sensor configuration and coverage. The solution is then updated based on the quality of previous solutions, evaluated using a fitness function. Specifically, old pheromone trails evaporate while better paths have their pheromone strengthened. However, when the search space is large and complex, or if initial trial solutions are poorly chosen, BACA's performance can be limited. To enhance solution exploration and achieve a global optimum, BACA is integrated with the HC algorithm, which iteratively compares adjacent solutions and selects the best one, and the SA algorithm, which iteratively reduces the probability of accepting worse solutions as the solution progresses.
Khujamatov et al. [
32] presented an innovative energy-efficient clustering and routing mechanism for WSNs using a hybrid approach that combines Chaotic Genetic Algorithm (CGA) and GWO . This method, named CGA-GWO, aims to address the significant challenge of minimizing overall energy consumption in WSNs, which is crucial for extending the operational lifespan of these networks. The hybrid approach leverages the strengths of both CGA and GWO to select energy-aware cluster heads and establish optimal routing paths to the base station, thereby ensuring efficient energy utilization. The proposed CGA-GWO method was evaluated through extensive simulations and compared with other relevant systems. The performance metrics considered in the evaluation included the number of live nodes, average remaining energy level, packet delivery ratio, and the overhead associated with cluster formation and routing. These metrics provide a comprehensive assessment of the system's efficiency and effectiveness in managing energy consumption and ensuring reliable data transmission. The simulation results demonstrated that CGA-GWO outperforms the other systems in terms of energy efficiency and network lifetime. Specifically, CGA-GWO showed a higher number of live nodes over time, indicating better energy conservation and longer operational periods. The average remaining energy levels were also higher in networks using CGA-GWO, underscoring its effectiveness in managing energy consumption. Furthermore, the packet delivery ratio was improved, highlighting the system's reliability in data transmission. The overhead associated with cluster formation and routing was significantly reduced, making CGA-GWO a more efficient solution for WSNs.
The collection of research works reviewed (
Table 2) underscores the importance of cross-layer optimization and the strategic integration of multiple OSI layers to enhance the performance and energy efficiency of WSNs. These studies reveal common features and techniques that collectively contribute to the advancement of WSN technology. A recurring theme across these works is the emphasis on energy efficiency, which is paramount given the limited power resources of WSN nodes. By leveraging cross-layer designs, protocols can optimize energy usage by coordinating functions across the physical, data link, and network layers. This holistic approach allows for more informed and effective decision-making, as it considers the interactions and dependencies between different layers of the network stack.
One of the key techniques highlighted is the use of adaptive duty cycles and sleep schedules managed by the MAC layer. Protocols such as EQPD-MAC and CL-MAC incorporate dynamic scheduling to ensure nodes spend minimal time in active states unless necessary. This technique significantly reduces idle power consumption and extends the overall network lifespan. The integration of these schedules with routing decisions ensures that energy savings do not compromise data transmission reliability or latency.
Another common technique is the strategic selection of CHs and relay nodes based on multiple criteria, including residual energy and distance to the BS. The protocols CCBE and GCRAD exemplify this approach by evaluating nodes’ energy levels and proximity to optimize data routing paths and reduce energy expenditure. This method ensures balanced energy consumption across the network, preventing early depletion of nodes and maintaining network functionality over a longer period.
The importance of robust and reliable data transmission is also a focal point in these studies. Techniques such as ECC and PNC are employed to enhance data integrity and reduce retransmissions. By ensuring that data packets are transmitted accurately and efficiently, these methods contribute to lower energy consumption and improved network performance. The use of full-duplex communication in the CEE model further highlights the potential of advanced physical layer techniques to enhance throughput and reduce delays.
The incorporation of geographic and hierarchical routing strategies is another significant aspect observed. Protocols like GCRAD and TSLC utilize geographic information and layered topological structures to make routing decisions that optimize both energy efficiency and coverage. These strategies ensure that data packets follow the most efficient paths, reducing the number of hops and associated energy costs.
Congestion management and collision avoidance are critical for maintaining network performance under varying traffic loads. Protocols such as CREC and CL-MAC address these challenges by implementing advanced MAC layer mechanisms to manage medium access and prevent data collisions. These approaches ensure smooth data flow and minimize energy wastage due to retransmissions.
Collectively, these works demonstrate that effective WSN protocols must integrate multiple layers and techniques to address the complex and interrelated challenges of energy efficiency, data transmission reliability, and network longevity. Cross-layer designs, which coordinate functions across the physical, data link, and network layers, provide a comprehensive framework for optimizing WSN performance. Techniques such as adaptive duty cycles, strategic node selection, robust data transmission methods, and advanced routing strategies are essential components of these integrated solutions.
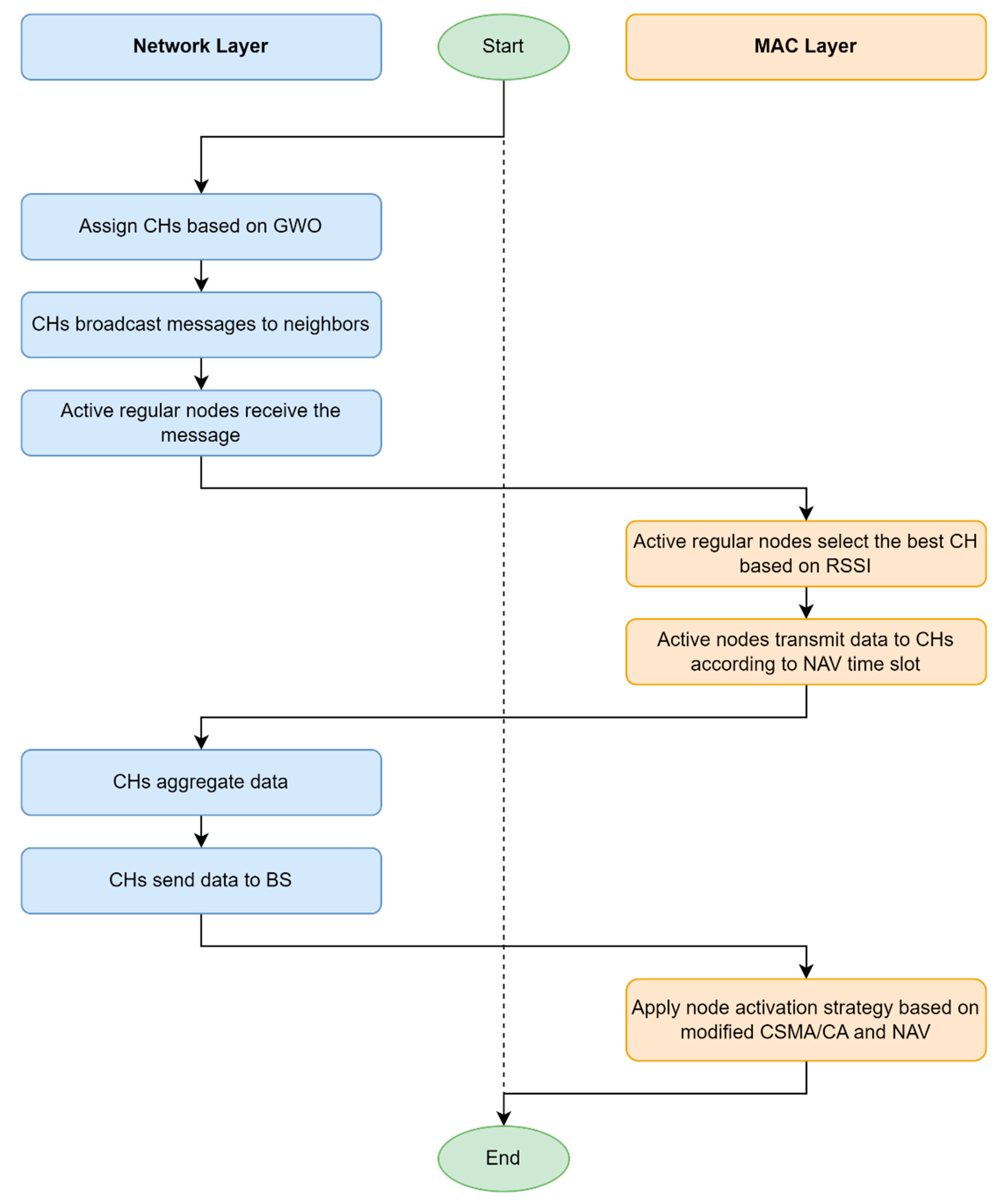
5. Energy Optimization Approach based on MAC/Routing Cross-Layer (EOAMRCL)
To minimize energy consumption in WSNs, we propose a centralized approach with a hierarchical architecture, where the network is partitioned into clusters, and all processes are managed at the BS. Our proposed protocol, EOAMRCL, focuses on both the MAC layer and the network layer, which are essential in self-organizing networks for enhancing performance and addressing scaling issues. This cross-layer protocol offers a comprehensive clustering solution by utilizing an objective function to identify the optimal CHs based on residual energy levels, intra-cluster distances, and inter-cluster distances. Additionally, during the transmission phase, each node creates an active mode/sleep mode schedule based on the NAV, leveraging the MAC layer's duty cycle schedule. This schedule is generated using inter-layer routing information, ensuring efficient and energy-saving communication within the network.
5.1. Incorporating Node Paring in CSMA/CA and NAV (MAC Layer)
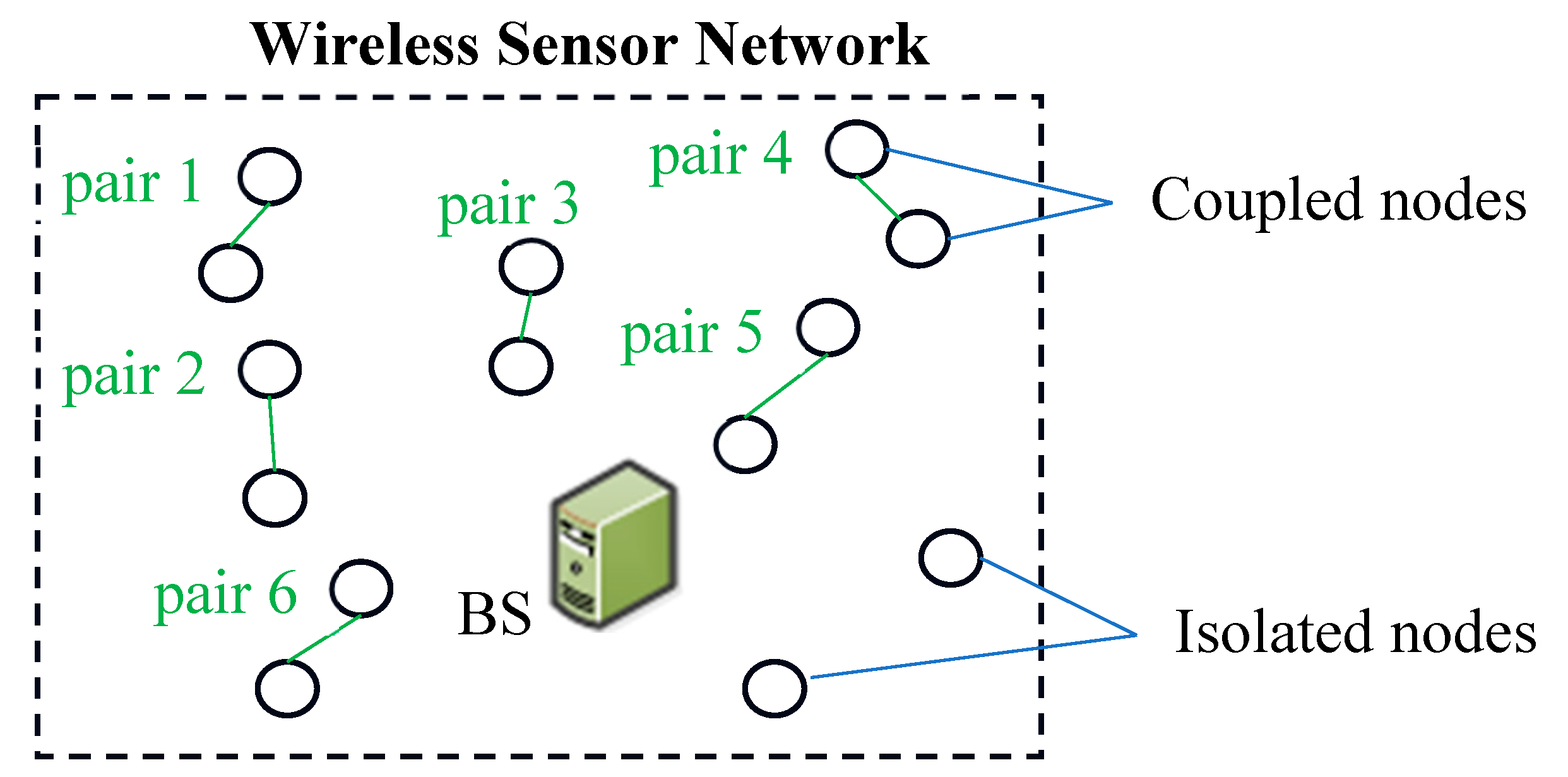
In our protocol, we make several key assumptions: the nodes in the network are randomly dispersed, and at each iteration, all the sensors gather data and transmit it to a central BS. The sensor nodes relay their position data to the BS, enabling the formation of clusters. Within these clusters, nodes that are within intra-cluster transmission range and of the same application type are connected in pairs based on minimal distance, using broadcast matching information shared with all nodes in the network (
Figure 1). This connectivity ensures that nodes become aware of one another's presence and positions, facilitating efficient communication within the network.
A significant feature of our approach is the alternation between "Sleep" and "Wake" modes within a single communication period. In sleep mode, nodes conserve energy by not communicating with CHs, resulting in minimal energy dissipation (
Figure 2). This reinforces the energy-saving benefits of the proposed approach. Unpaired nodes, however, operate continuously in active mode until their energy is depleted, highlighting the critical importance of energy conservation in the network. If the initial node in a pair is closer to the sink than its associated node it will transition to wake-up mode, also known as active mode. During active mode, the node collects data from its environment and transmits it to the CHs. Meanwhile, the associated node's transceiver will enter sleep mode and remain powered off during this time, conserving energy. In subsequent iterations, nodes in active mode will switch to sleep mode, and those in sleep mode will become active, ensuring a balanced energy consumption across the network.
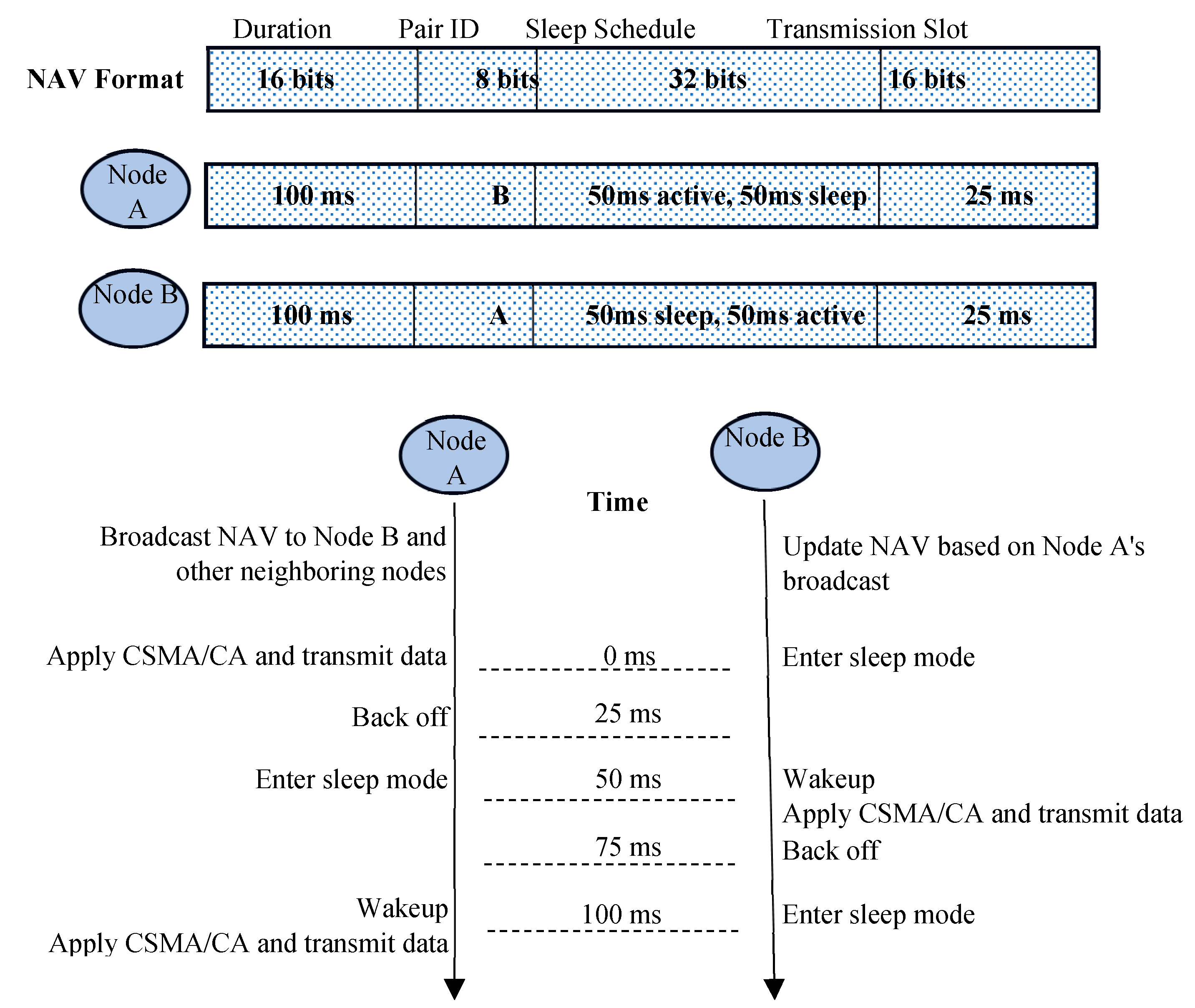
Figure 3 shows the integration of a sleep mode into the CSMA/CA mechanism. This integration primarily aims to enhance energy efficiency, which is crucial for the longevity of WSNs. By incorporating sleep mode, nodes can significantly reduce their energy consumption when they are not actively transmitting or receiving data. This approach helps in maintaining the balance of energy consumption across the network. Nodes can be paired to alternate their active and sleep cycles, ensuring that no single node is overburdened, thereby preventing early depletion of individual nodes' energy resources.
In traditional CSMA/CA, the Network Allocation Vector (NAV) is used to indicate the duration that the channel will be occupied. This helps prevent collisions by informing nodes of the ongoing transmission duration. In the proposed CSMA/CA mechanism with node pairing and sleep scheduling, the NAV must be adapted to account for the new sleep/activate mode and node pairing dynamics. Below is a conceptual update to the NAV mechanism (
Figure 4).
5.2. Pre-Clustering Phase (Network Layer)
In our proposed protocol, we assume that the system includes a certain percentage (
) of advanced nodes, which have an additional energy factor
compared to the normal nodes. Each sensor node initially has an energy level of
. For advanced sensor nodes, their energy is increased by the factor
, making their total energy
. Equation (1) is used to calculate the predicted network's total energy construction using
nodes.
Consequently, the total energy of the network is enhanced by this factor. We improved the election technique by incorporating the remaining energy of individual nodes, taking into account the different probabilities for advanced and ordinary nodes. The probability function for normal and advanced member nodes is defined by Equations (2) and (3) respectively:
At the end of each clustering round, the BS calculates the threshold probability of clusterheads
:
Where ARE represents the average residual energy in the network.
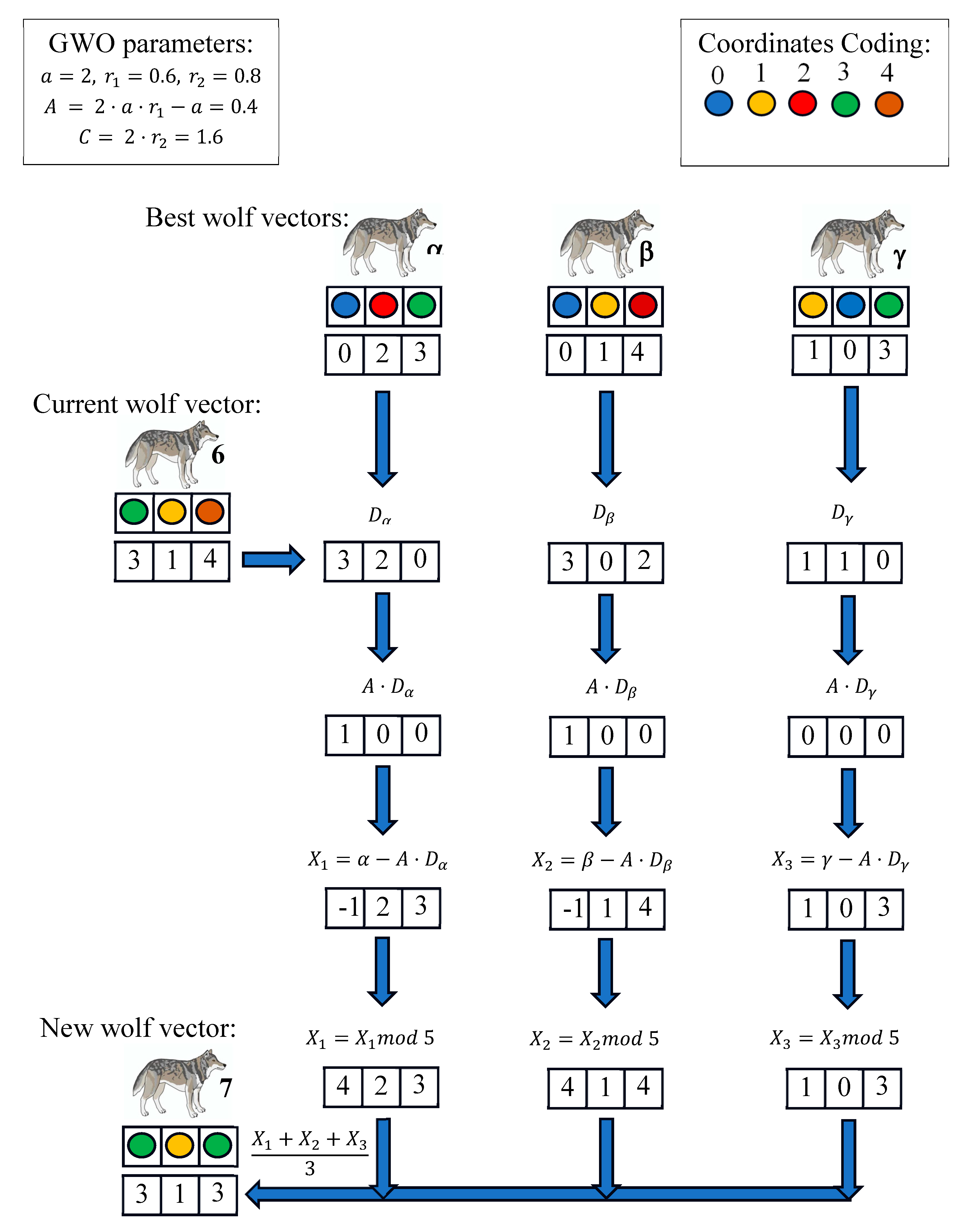
5.3. Clusters Formation Phase (Network Layer)
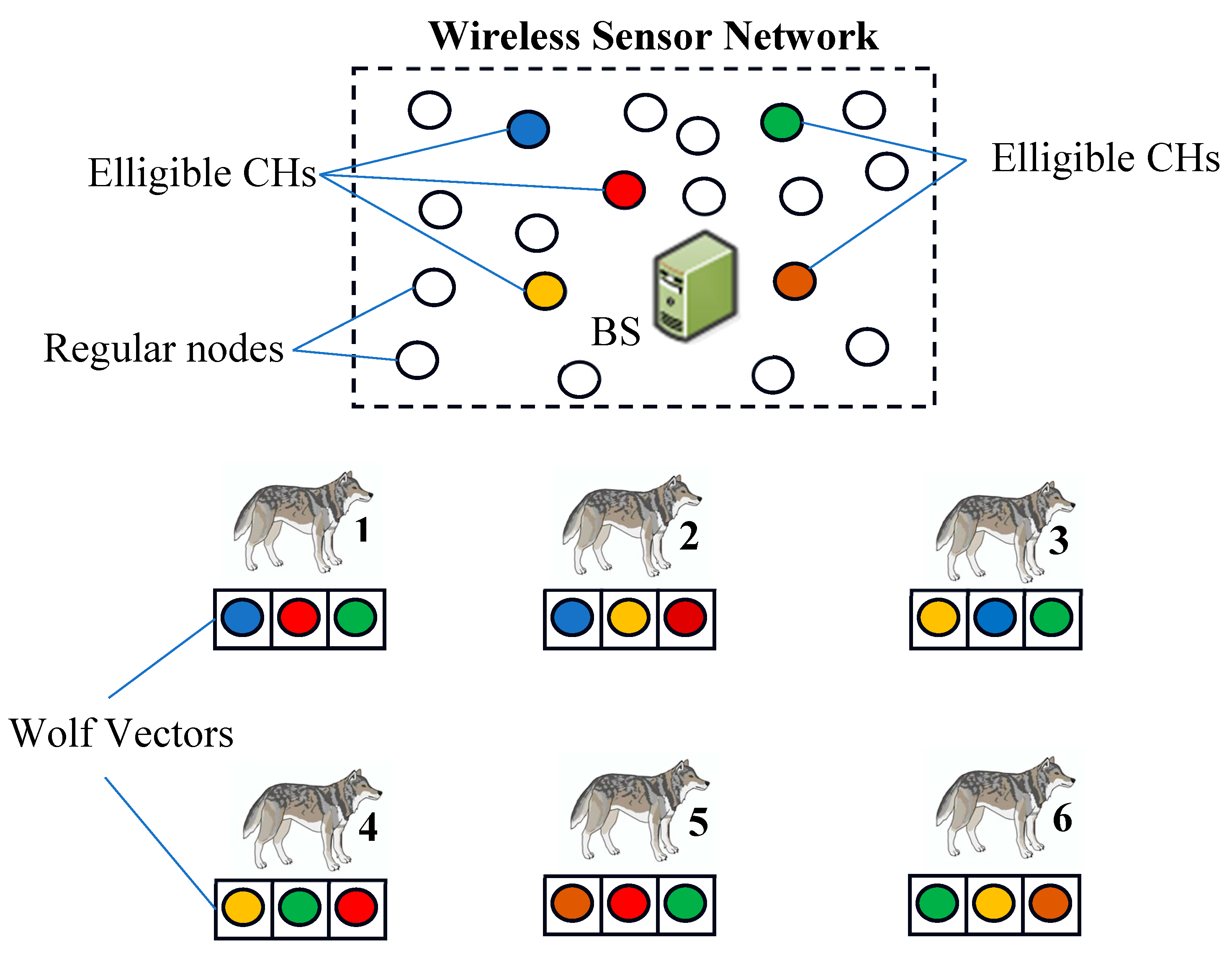
Before the start of each iteration, every node transmits its remaining energy to the BS. Upon receiving the energy levels from all nodes, the BS calculates ARE and selects nodes with probability higher than
to become candidate CHs. The BS then implements our proposed EOAMRCL approach, forming a set of wolf vectors from the group of nodes with probability above
. These wolf vectors consist solely of nodes eligible to be CHs, as shown in
Figure 5.
The fitness value of each wolf vector is then calculated using Equation (5).
Thus, the best wolf is the one with the lowest fitness value. In this context, , , and are constants in a user-defined function, with the requirement that , used to determine the contribution of each sub-objective, , , and . In our experiments, we set the weight values as follows: . These weights ensure equal importance is given to both inter-cluster and intra-cluster distances, while using energy as a tie-breaker in case of equal distances.
The sub-objective
is calculated as the normalized sum of the distances between each CH in the wolf vector and all other nodes in the network, as shown in Equation (6):
Where:
- -
represents the maximum distance between two sensors,
- -
represents the number of CHs in the wolf vector,
- -
represents the total number of nodes.
- -
represents the clusterhead.
- -
represents the regular sensor node.
To calculate
, we use the Euclidean distance between two nodes A and B as shown in the following Equation (6).
Where , are the coordinates of A and B, respectively.
The sub-objective
represents the normalized sum of the distances between each CH in the packet and the BS, as shown in Equation (8):
The sub-objective
represents the negative normalized total remaining energy of the CHs within the wolf vector, as shown in Equation (9):
Where represents the remaining energy of .
Our process of updating and calculating new wolf vector is systematically guided by GWO. This connection to a proven optimization algorithm lends our work credibility and relevance within the field of optimization [
40].
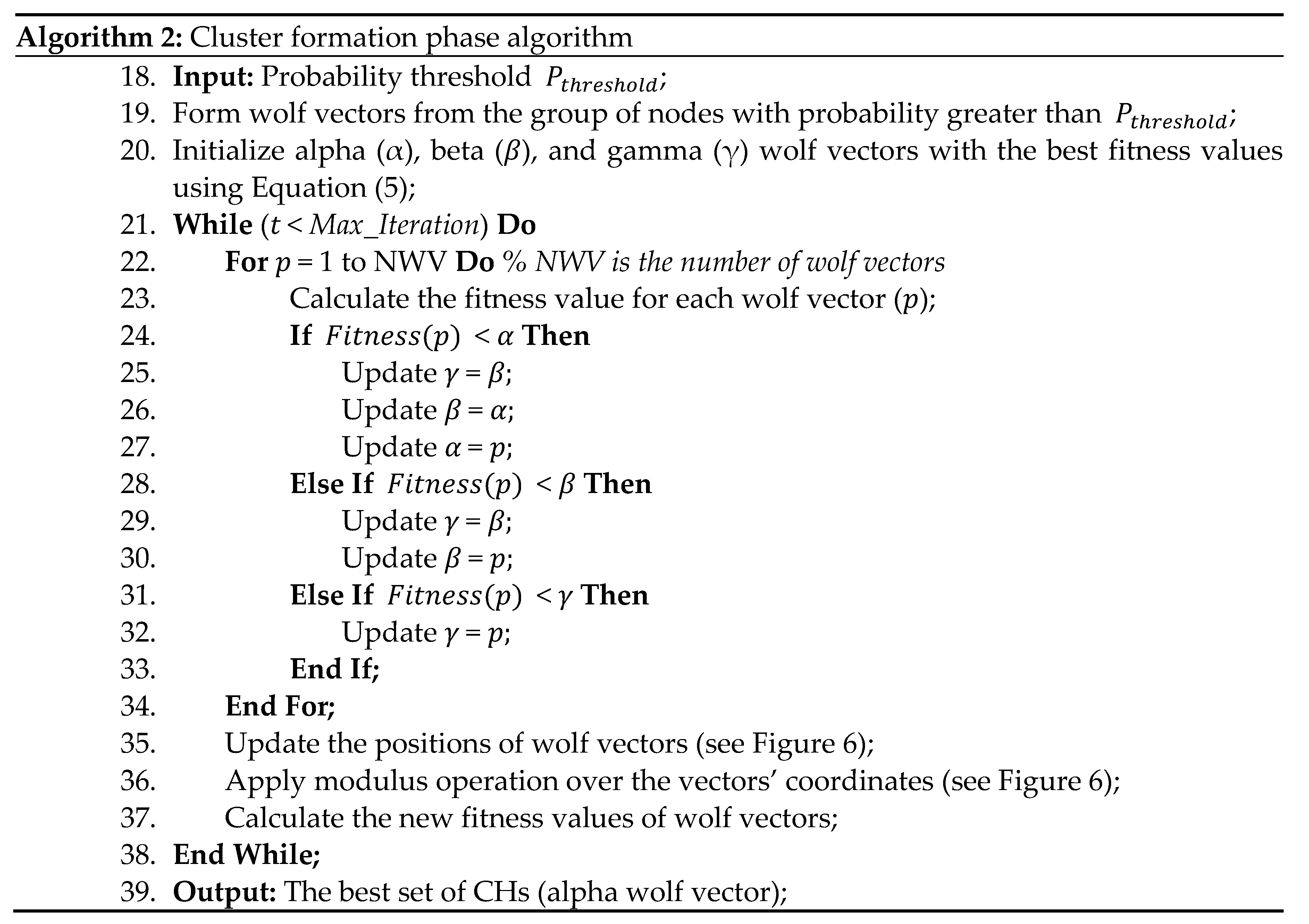
Figure 6.
Example of wolf vectors update.
Figure 6.
Example of wolf vectors update.
5.4. Transmission Phase (MAC and Network Layer)
Upon being chosen as the CH, the node broadcasts a message across the network. Only nodes in active mode can hear these messages sent out by various CHs. These active nodes then choose their CHs based on the Received Signal Strength Indication (RSSI). During their NAV time slots, active mode nodes transmit their detected data to the CH. Nodes in sleep mode conserve energy by switching off their transceivers and do not transmit any data.
After receiving data from its members, each CH aggregates and combines this data with its own. According to their allocated NAV time slots, each cluster node forwards the gathered data directly to the BS. Data aggregation and compression are essential data processing tasks carried out by CHs after receiving data from every cluster member. These processes maximize energy usage efficiency and extend the network's lifetime.
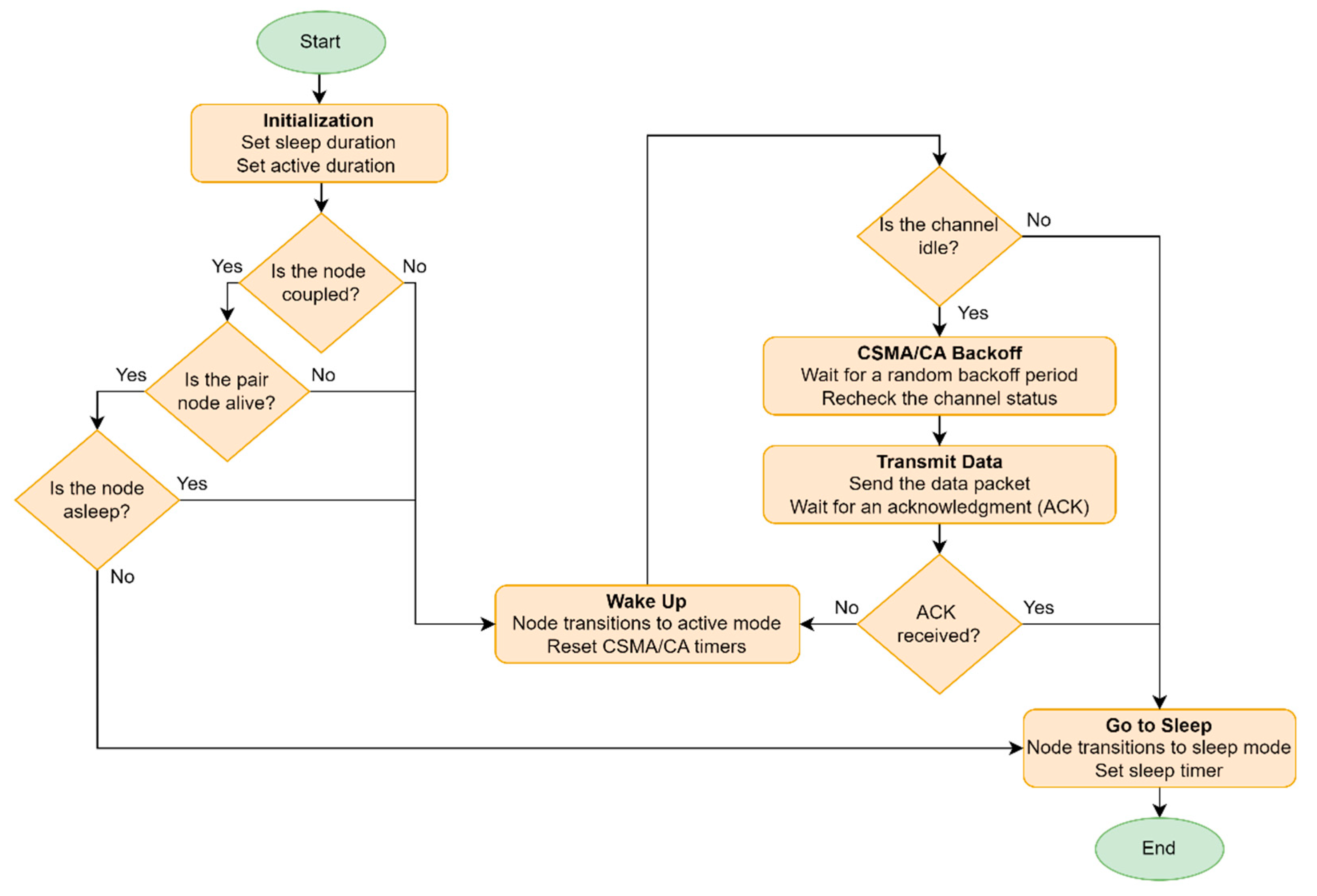
In the next iteration, each node adjusts or maintains its mode (active or sleep) based on its state (paired or isolated), residual energy, and the residual energy of neighboring nodes. The flowchart shown in
Figure 7 illustrates the node mode configuration for the upcoming iteration. When a node becomes a CH, it uses its broadcast capability to inform the entire network of its status. This broadcast is a critical step, as it ensures that all active mode nodes are aware of their new CH and can make informed decisions about which CH to connect to base on the strength of the RSSI. The active nodes then engage in data transmission during their assigned NAV time slots, ensuring that their data is efficiently communicated to the CH.
The role of the MAC layer cannot be overstated in this process. It ensures that nodes operate in a synchronized manner, with precise timing for data transmission and reception. This coordination prevents data collisions and optimizes the use of the network's limited energy resources. By carefully managing the active and sleep modes of nodes, the MAC layer helps to prolong the operational lifespan of the network.
Once the CH collects data from its cluster members, it performs data aggregation and compression, which are vital for reducing the volume of data that needs to be transmitted to the BS. These tasks help in conserving energy, as smaller data packets require less power to transmit. The efficiency of this process directly impacts the network's overall energy consumption and longevity. In each new iteration, nodes reassess their modes based on several factors, including their own residual energy and that of their neighbors. This dynamic adjustment is crucial for maintaining a balanced energy consumption across the network, ensuring that no single node depletes its energy resources too quickly. By constantly adapting to the network's state, the nodes can optimize their energy usage and contribute to the network's sustainability.
6. Simulation Results
In this section, we compare the efficiency of EOAMRCL to peer protocols: EEUC [
41], DWEHC [
42], and CGA-GWO [
32]. In order to perform simulation, we created many network configurations with hundreds of randomly placed sensor nodes. Each result represents the average of twenty separate simulations.
6.1. Radio Energy Model
In the simulation section, we employ the same first-order radio model for energy consumption presented in [
43]. In this concept, a radio transmits an L-bit data to a receiver situated a distance of
meters from it by dissipating an amount of energy
. A sensor node's radio has to use
energy in order to receive an L-bit message. The multi-path (
) channel is utilized in short distance transmission; the free space (
) channel is used when the distance between two nodes or between a node and the SB is higher than certain distance
. Radios can use the least amount of energy required to reach their intended receivers. To prevent unwanted transmissions, the radios have the capability to be switched into sleep mode. Equation 10 presents the amount of energy needed to transmit a packet of
bits across a distance d [
43]:
Where:
- -
represents the energy expended by the transmitter across a -meter distance in order to send a packet of bits.
- -
is the energy needed to transfer a single bit over meters, both ways.
- -
is the transmission packet's size.
The distance at which the amplification factors begin to shift is known as
:
For the receiver to receive a packet of
bits, energy
must be consumed as follows:
6.2. Simulation Parameters
The selection of simulation parameters in
Table 4 aims to create a realistic and comprehensive environment for evaluating the clustering protocols. The network zone is set to 100 x 100 m², balancing sufficient coverage and computational feasibility, while the number of sensors ranges from 50 to 250 to test the protocol's scalability under different network densities. The base station (BS) is located at coordinates (90,90) to simulate real-world scenarios where the BS is positioned at the network's edge, challenging the protocol's data routing efficiency. A clusterhead percentage (
) of 5% ensures the effectiveness of selecting optimal CHs for energy efficiency and load balancing. Incorporating 20% advanced nodes with an additional energy factor (
) of 1 tests the protocol's ability to leverage these nodes for prolonged network operation. The initial energy (
) of 3 J/node provides a reasonable starting point for observing energy consumption patterns and the protocol's impact on network lifetime. Transmission energy (
) of 50 nJ/bit and a packet size (L) of 4000 bits reflect typical WSN energy consumption, crucial for assessing data transmission efficiency. Propagation energy values (
= 15 pJ/bit/m² and
= 0.0015 pJ/bit/m⁴) account for energy loss during data transmission over varying distances, essential for realistic wireless communication simulation. Data aggregation energy (
) of 5 nJ/bit/signal evaluates the protocol's effectiveness in reducing energy consumption through data aggregation. Limiting the node pairing distance to less than 2 meters ensures close proximity for efficient sleep/active mode coordination. Fitness function weights (
) of 0.45, 0.45, and 0.1 balance the importance of intra-cluster distances, inter-cluster distances, and residual energy, ensuring a comprehensive performance evaluation. These parameters collectively create a realistic and challenging simulation environment, enabling a thorough assessment of the EOAMRCL protocol's ability to enhance energy efficiency, extend network lifetime, and improve overall network performance in WSNs.
6.3. Evaluation Metrics
The evaluation metrics used in the experimentations are described as follows:
- a.
-
Network Residual Energy:
Measures the remaining energy in the network over time.
Indicates the efficiency of energy management by each protocol.
Higher residual energy implies better energy conservation and longer network lifespan.
- b.
-
Clustering Iteration Performance:
Assessed using First Node Dead (FND), Half of Nodes Dead (HND), and Last Node Dead (LND).
FND: Iteration count when the first node dies.
HND: Iteration count when half of the nodes are dead.
LND: Iteration count when the last node dies.
Higher values indicate better energy distribution and prolonged network operation.
- c.
-
Percentage of Live Nodes:
Represents the percentage of nodes remaining active over time.
Higher percentages indicate better energy management and network sustainability.
Critical for assessing the protocol's ability to maintain network functionality.
- d.
-
Clustering Overhead:
Measures the communication and computational costs associated with cluster formation and maintenance.
Lower overhead indicates more efficient clustering mechanisms, reducing strain on network resources.
Essential for evaluating the protocol's impact on network performance and energy consumption.
- e.
-
Percentage of Packets Received:
Indicates the reliability of data transmission by measuring the percentage of packets successfully received.
Higher percentages suggest better data integrity and communication efficiency.
Crucial for ensuring consistent and accurate data flow within the network.
6.4. Experimental Results and Interpretation
This section presents the experimental results and a detailed analysis of the performance of four protocols: DWEHC, EEUC, CGA-GWO, and EOAMRCL. The experiments were conducted to evaluate various aspects of network efficiency, including energy management, node longevity, clustering overhead, and data transmission reliability. By comparing these protocols across multiple metrics, we aim to highlight the strengths and weaknesses of each and demonstrate the superior performance of EOAMRCL in enhancing the operational lifespan and efficiency of WSNs. The subsequent figures and their interpretations provide insights into the effectiveness of these protocols under different conditions and performance criteria.
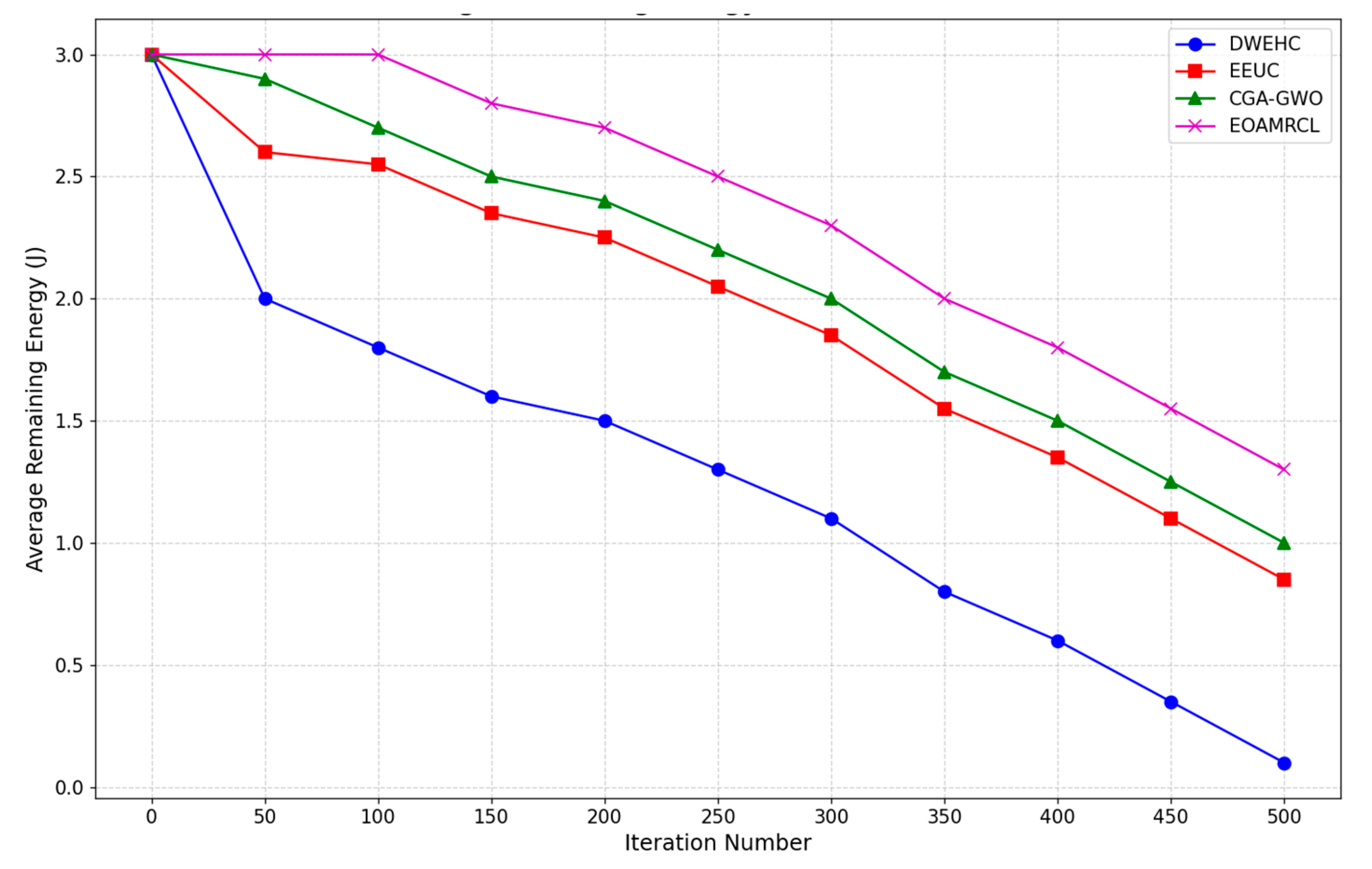
Figure 8 compares the average remaining energy over 500 iterations. The graph highlights each protocol's energy management and network longevity. The DWEHC protocol exhibits the steepest decline in average remaining energy, indicating a higher rate of energy consumption compared to other protocols. By around 100 iterations, the average remaining energy drops significantly and continues to decline steadily. This can be attributed to DWEHC's lack of an optimized energy management strategy, resulting in faster depletion of nodes' energy reserves and a shorter network lifespan.
In comparison, the EEUC protocol performs better than DWEHC but still shows a considerable drop in energy levels as iterations progress. The energy consumption is more controlled, but by approximately 300 iterations, the average remaining energy is substantially reduced. EEUC’s strategies help prolong network life to some extent, but they are not as effective as more advanced protocols, lacking the optimization needed for longer durations. The CGA-GWO protocol demonstrates a more balanced energy consumption pattern, with a slower decline in average remaining energy. The integration of GWO algorithm allows for more efficient clustering and routing decisions, conserving energy and extending the network's lifespan. CGA-GWO achieves better longevity and sustained performance over extended periods.
EOAMRCL outperforms all other protocols, maintaining the highest average remaining energy throughout the 500 iterations. This superior performance is due to its effective cross-layer optimization approach, integrating the MAC and network layers for enhanced energy efficiency. By leveraging GWO, EOAMRCL optimally selects cluster heads and routes, minimizing energy consumption during data transmission. The protocol's duty-cycle scheduling at the MAC layer allows nodes to switch between active and sleep modes, further conserving energy. This results in a significantly extended network lifetime and consistent energy levels, showcasing EOAMRCL’s effectiveness in managing energy consumption efficiently.
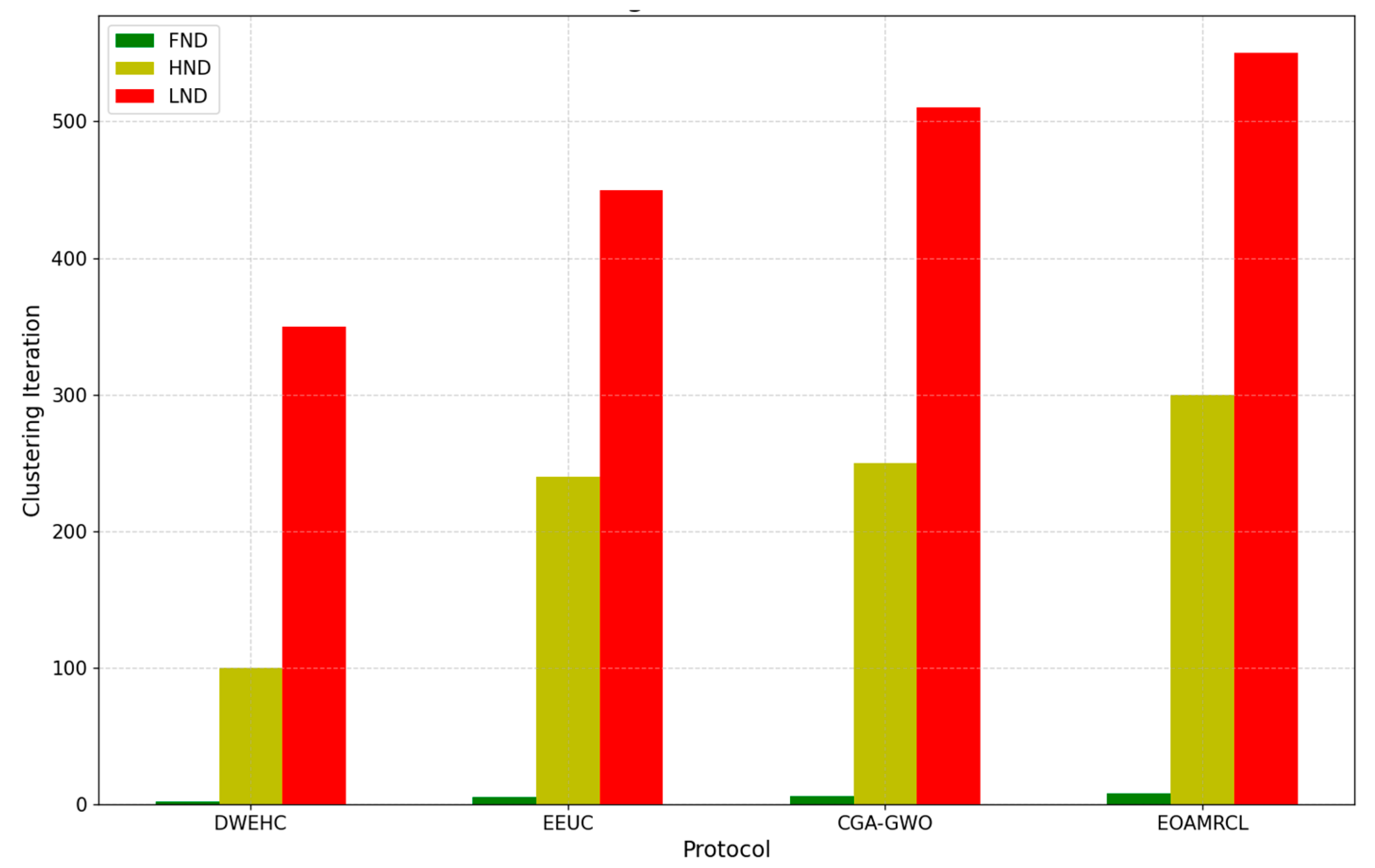
In
Figure 9, the DWEHC protocol shows a rapid progression from FND to LND. The FND occurs relatively early, indicating that the energy consumption among nodes is not well balanced. As a result, nodes begin to die off quickly, leading to a shorter network lifespan. The HND and LND metrics further confirm this, with a significant number of nodes dying earlier compared to the other protocols. This suggests that DWEHC lacks effective mechanisms for managing energy consumption and distributing load evenly across nodes.
The EEUC protocol demonstrates better performance than DWEHC, with a delayed FND and a more gradual progression to HND and LND. This indicates that EEUC has more effective clustering and energy management strategies, which help in prolonging the network's operational period. However, by the time half the nodes are dead, the network starts to decline rapidly, showing that while EEUC is better than DWEHC, it still falls short in maintaining node energy levels uniformly over extended periods.
The CGA-GWO protocol further improves on the EEUC performance, with the FND occurring later and a slower progression to HND and LND. This improvement can be attributed to the integration of the GWO algorithm, which enhances the selection of cluster heads and routing paths, leading to more balanced energy consumption among nodes. The prolonged periods before reaching HND and LND indicate that CGA-GWO manages to maintain network stability and efficiency for a longer duration compared to DWEHC and EEUC.
EOAMRCL exhibits the best performance among all the protocols, with the FND occurring much later and a very gradual progression to HND and LND. This is due to the effective cross-layer optimization approach, which integrates the MAC and network layers to enhance energy efficiency. By leveraging GWO, EOAMRCL optimally selects cluster heads and routes, minimizing energy consumption during data transmission. Additionally, the duty-cycle scheduling at the MAC layer allows nodes to switch between active and sleep modes, further conserving energy. The result is a significantly extended network lifetime, with nodes remaining functional for longer periods, thus delaying the FND, HND, and LND milestones.
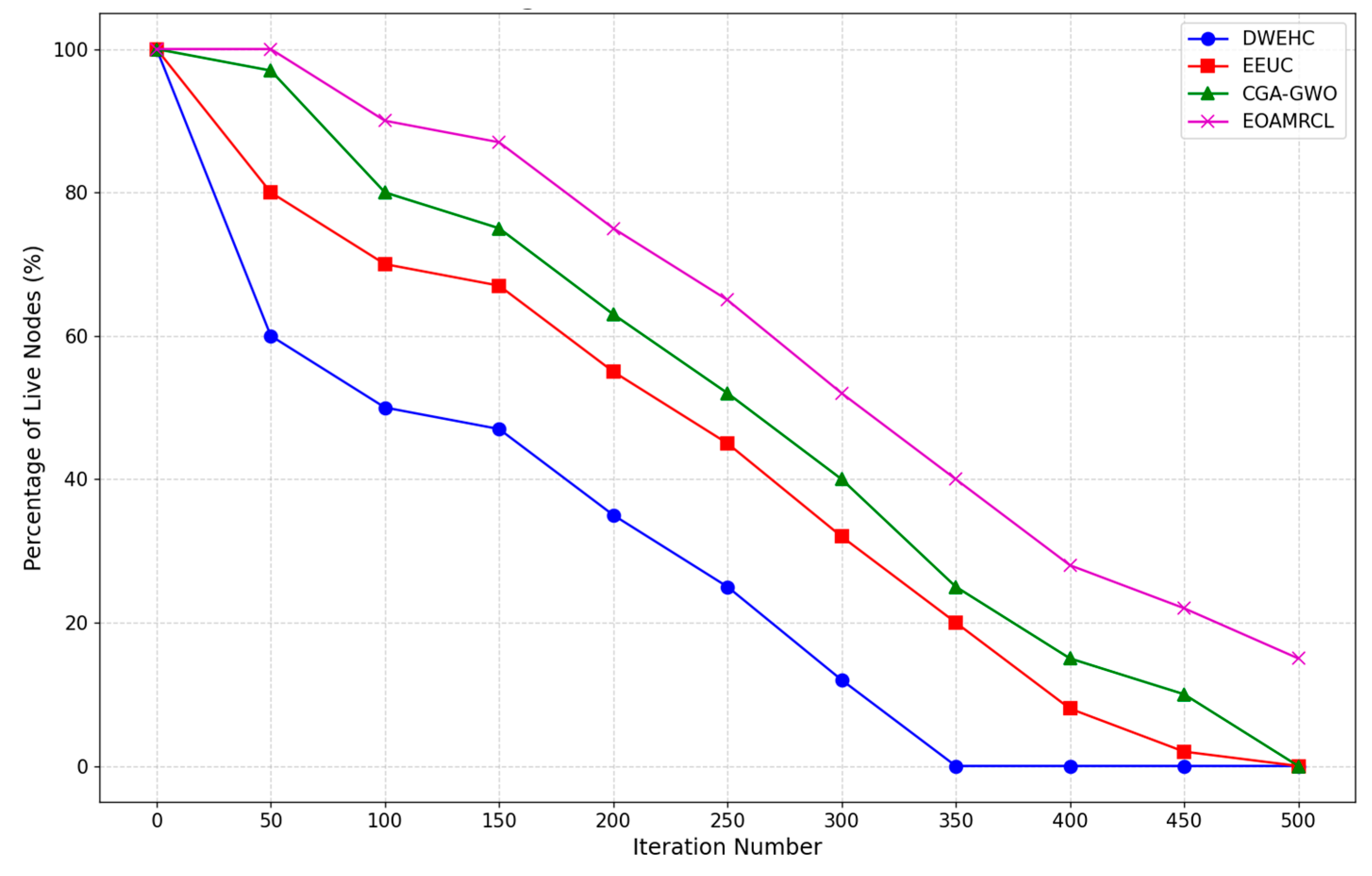
Figure 10 compares the percentage of live nodes over 500 iterations. The DWEHC protocol shows a rapid decline in the percentage of live nodes, with a significant drop occurring early in the iterations. By around 150 iterations, less than half of the nodes remain alive, indicating inefficient energy management. The steep decline continues, and by 400 iterations, almost all nodes are dead. This pattern suggests that DWEHC's approach to clustering and routing is not effective in conserving node energy, leading to a shorter network lifespan.
In contrast, the EEUC protocol performs better than DWEHC, but still shows a steady decline in the percentage of live nodes. The drop is less steep initially, with around 60% of nodes remaining alive by 150 iterations. However, the decline accelerates after this point, and by around 400 iterations, the network is nearly depleted. This indicates that while EEUC improves energy efficiency compared to DWEHC, it is still not sufficient to sustain long-term network operations.
The CGA-GWO protocol demonstrates a more gradual decline in the percentage of live nodes. By leveraging the GWO algorithm, CGA-GWO achieves better clustering and routing decisions, which help in distributing the energy consumption more evenly across nodes. As a result, the percentage of live nodes remains higher for a longer duration, with around 50% of nodes still alive at 250 iterations. This indicates that CGA-GWO is more effective in managing energy consumption and extending network life compared to DWEHC and EEUC.
EOAMRCL shows the best performance among all protocols, maintaining the highest percentage of live nodes throughout the 500 iterations. The decline in live nodes is the most gradual, with over 60% of nodes still alive at 250 iterations. This superior performance can be attributed to the cross-layer optimization approach of EOAMRCL, which integrates the MAC and network layers for enhanced energy efficiency. By using GWO to optimally select cluster heads and routes, and incorporating duty-cycle scheduling at the MAC layer to alternate nodes between active and sleep modes, EOAMRCL effectively conserves energy. As a result, the network maintains a higher percentage of live nodes for a significantly extended period.
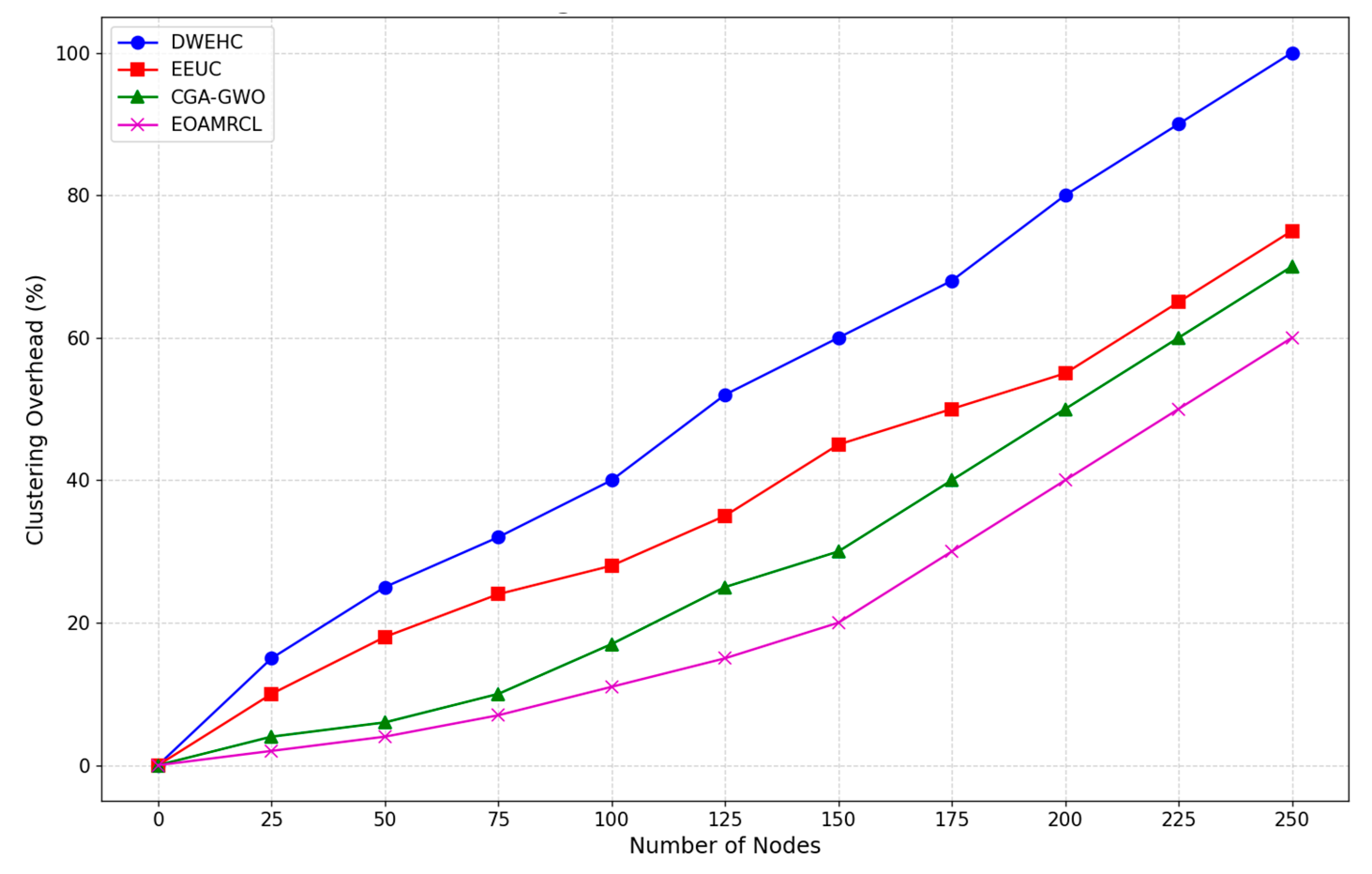
Figure 11 compares the clustering overhead as a function of the number of nodes. The DWEHC protocol shows the highest clustering overhead, which increases sharply as the number of nodes grows. Starting from a small number of nodes, the overhead rises steeply and continues to climb consistently. By the time the network reaches 225 nodes, the clustering overhead approaches 90%. This high overhead can be attributed to DWEHC's less efficient clustering and routing mechanisms, which require more frequent updates and higher communication costs. This inefficiency can significantly drain network resources and reduce overall performance.
In contrast, the EEUC protocol demonstrates better performance, with a slower increase in clustering overhead compared to DWEHC. However, the overhead still grows steadily as the number of nodes increases, reaching more than 60% at 225 nodes. While EEUC manages resources more effectively than DWEHC, the clustering overhead remains substantial, indicating room for improvement in clustering efficiency and resource management.
The CGA-GWO protocol shows a further reduction in clustering overhead, with a more gradual increase as the number of nodes grows. The overhead remains below 60% even at 225 nodes, demonstrating the benefits of integrating the GWO algorithm. GWO enhances clustering efficiency by making more informed and balanced decisions about cluster formation and maintenance, thereby reducing the frequency and cost of cluster updates.
EOAMRCL exhibits the lowest clustering overhead among all the protocols. The increase in overhead is the most gradual, remaining well below 50% at 225 nodes. This superior performance can be attributed to EOAMRCL's effective cross-layer optimization approach, which integrates the MAC and network layers to enhance energy efficiency and reduce communication costs. By leveraging GWO for optimal cluster head selection and routing, and incorporating duty-cycle scheduling to alternate nodes between active and sleep modes, EOAMRCL minimizes the clustering overhead. This efficient management of network resources ensures that the protocol can scale effectively with the number of nodes without incurring excessive overhead.
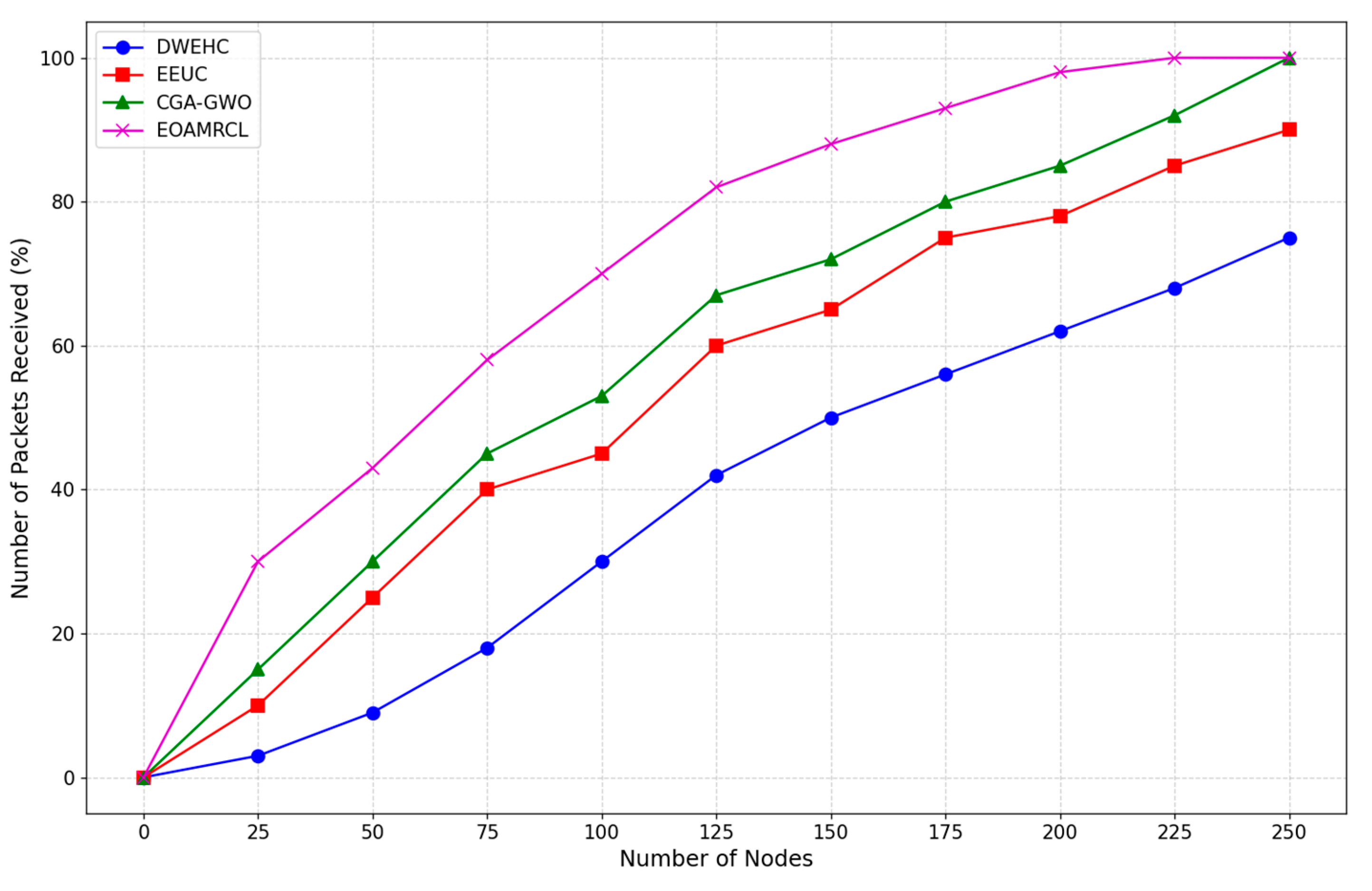
Figure 12 compares the number of packets received as a function of the number of nodes. The DWEHC protocol exhibits the lowest number of packets received, showing a gradual increase as the number of nodes grows. Starting from a minimal percentage, the packets received slowly climb but remain significantly lower compared to other protocols throughout the range. By the time the network reaches 175 nodes, the percentage of packets received is still below 60%. This indicates that DWEHC struggles with efficient data transmission, likely due to higher packet loss and less effective routing mechanisms, leading to poorer network performance.
The EEUC protocol performs better than DWEHC, with a steeper increase in the number of packets received as the number of nodes increases. However, the growth is still moderate, and by the time the network reaches 175 nodes, the packets received are below 80%. While EEUC improves data transmission efficiency compared to DWEHC, it still experiences limitations in routing and clustering efficiency, which affect its overall performance.
The CGA-GWO protocol shows a further improvement, with a higher percentage of packets received compared to EEUC and DWEHC. The increase is more pronounced, and by 175 nodes, the packets received are around 80%. The integration of the GWO algorithm enhances the protocol’s ability to make efficient routing and clustering decisions, leading to better data transmission and reduced packet loss. This results in a more reliable and efficient network performance.
EOAMRCL demonstrates the best performance among all protocols, maintaining the highest percentage of packets received throughout the range of node counts. The increase is the most rapid, with over 90% of packets received by 175 nodes. This superior performance can be attributed to EOAMRCL’s effective cross-layer optimization approach, which integrates the MAC and network layers for enhanced energy efficiency and data transmission. By leveraging GWO for optimal cluster head selection and routing, and incorporating duty-cycle scheduling to alternate nodes between active and sleep modes, EOAMRCL minimizes packet loss and maximizes successful data delivery. This efficient management of data transmission ensures that the protocol can handle increasing network sizes without compromising performance.
5.5. Discussion
The analyses of the five figures collectively highlight the advantages and disadvantages of different energy optimization approaches for WSNs. DWEHC consistently shows the poorest performance across all metrics, indicating inefficient energy management and high overhead costs. The rapid depletion of energy, early node deaths, high clustering overhead, and low packet reception rates all underscore DWEHC's inadequacies in sustaining network performance. EEUC performs better but still experiences significant limitations in maintaining energy efficiency and network performance. While it shows improvements in energy consumption and node longevity compared to DWEHC, the protocol's steady decline in live nodes and moderate clustering overhead reveal its insufficient optimization for extended network operations. CGA-GWO demonstrates notable improvements in energy management, node lifetimes, clustering overhead, and data transmission efficiency. The integration of the GWO algorithm allows for more efficient clustering and routing decisions, enhancing overall network performance. This is evidenced by the balanced energy consumption, delayed node deaths, and higher packet reception rates, indicating that CGA-GWO is effective in extending network life and reliability.
However, EOAMRCL outperforms all other protocols, showcasing the benefits of its cross-layer optimization approach. By integrating the MAC and network layers and leveraging GWO, EOAMRCL achieves superior energy efficiency, prolonged node lifetimes, reduced clustering overhead, and improved data transmission efficiency. The protocol maintains the highest average remaining energy, delays node deaths significantly, and ensures the highest percentage of live nodes across all iterations. Its low clustering overhead highlights its efficient resource management, while the high packet reception rates demonstrate its robustness in data transmission. The duty-cycle scheduling at the MAC layer, which alternates nodes between active and sleep modes, further conserves energy and extends the network's operational life. This multifaceted optimization ensures that EOAMRCL not only addresses the limitations of single-layer protocols but also sets a new standard for energy-efficient management in WSNs.
Overall, EOAMRCL proves to be the most effective solution for energy optimization in WSNs. Its comprehensive approach, which combines cross-layer optimization with advanced algorithms like GWO, highlights the importance of integrating multiple layers and techniques to achieve optimal network performance. The protocol's ability to manage energy consumption efficiently, maintain network stability, and ensure reliable data transmission underscores its superiority. The findings from the analyses reinforce the critical role of advanced optimization methods in enhancing the sustainability and performance of wireless sensor networks, making EOAMRCL a benchmark for future developments in this field.