1. Introduction
Since Satoshi Nakamoto proposed the concept of blockchain [
1], blockchain technology has realized a decentralized shared general ledger, which can be understood as a large-scale and decentralized distributed database, which is traceable, verifiable and not easy to be tampered with [
2].
Recently, blockchain develops really fast, a large number of blockchain projects and their unique chain structures and tokens have been created, such as bitcoin blockchain [
1] based on proof-of-work, Ethereum blockchain [
3] transitioning from Proof-of-Work to Proof-of-Stake, the use of Proof-of-Stake [
4,
5,
6], the use of Proof-of-Authority [
7,
8], and web3.0's hot consortium blockchains such as Hyperledger fabric, Corda, Quorum, which use consensus protocols such as PBFT [
9,
10] and Raft [
11]. These chains do not communicate with each other in structure, which leads to great obstacles to the application and development of blockchain technology. Token and application data on the chain may form the data islanding effect of blockchain, so different blockchains need a unified method to transfer data and asset. Therefore, researchers put forward the concept of "cross-chain", which breaks the islanding effect among different blockchain projects and realizes interoperability between chains.
The current mainstream projects of cross-chain technology include Cosmos [
12], Polkadot [
13], Lightning Network [
14], Fusion [
15], Interledger [
16], etc. The purpose is to realize asset exchange, information interaction and application collaboration between different blockchain platforms, reduce the difficulty of blockchain users and reduce the cross-chain transmission process.
Table 1 shows the key attributes of some cross-chain projects.
The Problem. At present, cross-chain still relies on third-party centralized nodes and Relays. Even though Cosmos, Polkadot and cross-chain bridges [
17,
18] are proposed, which solve the inter-chain consensus protocol and some security problems, there is still the possibility of bridging chains doing evil. In 2019, Cosmos was found to have a re-entrustment loophole, which could immediately redeem guaranty tokens by replacing the Validator of parallel chain, resulting in early redemption of 7,250 Atom tokens with a value of about 43,500 US dollars, this event destroyed the fairness of the transaction. The Grandpa Consensus (GHOST-based Recursive Ancestor Deriving Prefix Agreement) Protocol used by Polkadot cannot tolerate Dos attacks. And there is the possibility that Nominators will do evil together [
13]. In 2022, Lightning Network had a malicious channel attack problem, and after the uplink timed out. Malicious traders can still send bitcoin under the chain, causing theft.
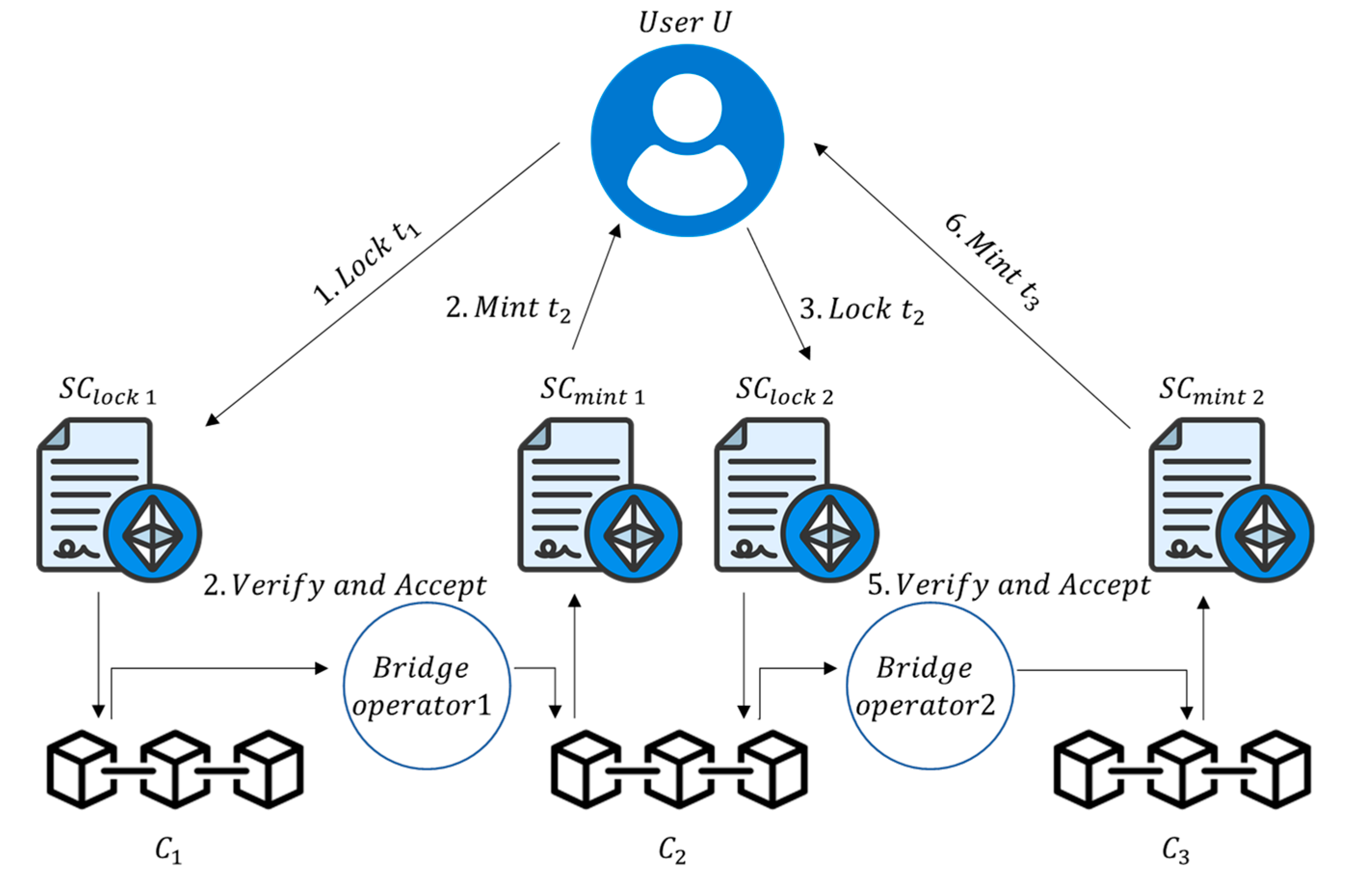
And cross-chain bridge solutions focus on Two-blockchain interoperability, which doesn't suit the complex cross-chain requirements in multi-chain ecosystems. As depicted in
Figure 1, suppose a user
, driven by investment motives, intends to exchange their assets
held on blockchain
for equivalent assets
on another blockchain
. However, given that both
and
aren’t stable currencies (potentially speculative coins), it requires converting
through cross-chain bridge
to obtain
on blockchain
(e.g., Ethereum's ETH). Subsequently, through
, converting
to
via cross-chain transfer. It's evident in this operational flow that
engages in two separate cross-chain transactions, resulting in a cumbersome process, and the multiple transactions incur additional operational costs.
Our approach. In blockchain cross-chain scenarios, involving collaboration among multiple parties may require computations involving sensitive information. Secret sharing can be employed to securely execute computations among multiple parties, ensuring that no private information from any party is disclosed. We propose SMPTC
3 (Secure Multi-party Protocol Based Trusted Cross-chain Contracts) to implement a secure cross-chain interaction protocol, which is mainly aimed at large amount token transfer and cross-chain transmission of important private data. SMPTC
3 does not need to trust any central committee or third-party node. It uses and improves the SMC [
19,
20,
21,
22,
23] (secure multi-party computation) proposed by Yao to establish the trust between the participating chains, and defines the participating nodes as semi-honest adversaries to prevent the participating chain from doing evil. Meanwhile, participants can prove their identities without providing too much private data to ensure the privacy of cross-chain transactions. SMPTC
3 embeds the improved SMC into the smart contract, and the cross-chain initiator C1 initiates the smart contract (SC) of the relay chain, and SC verifies whether the identities of C1 and other participants in the chain are true and reliable.
The SMPTC
3 deploys a group of contracts, each situated on various participating chains, referred to as validator contracts. These validator contracts can invoke the validator contracts of other participating chains for cross-chain validation. They can also invoke sender and receiver contracts deployed across different chains to perform application-specific tasks. Depending on the application scenario, validator contracts may also require participating nodes to provide transaction information and Merkle proofs of smart contract states to ensure the atomicity of asset exchanges and the correctness of smart contracts.
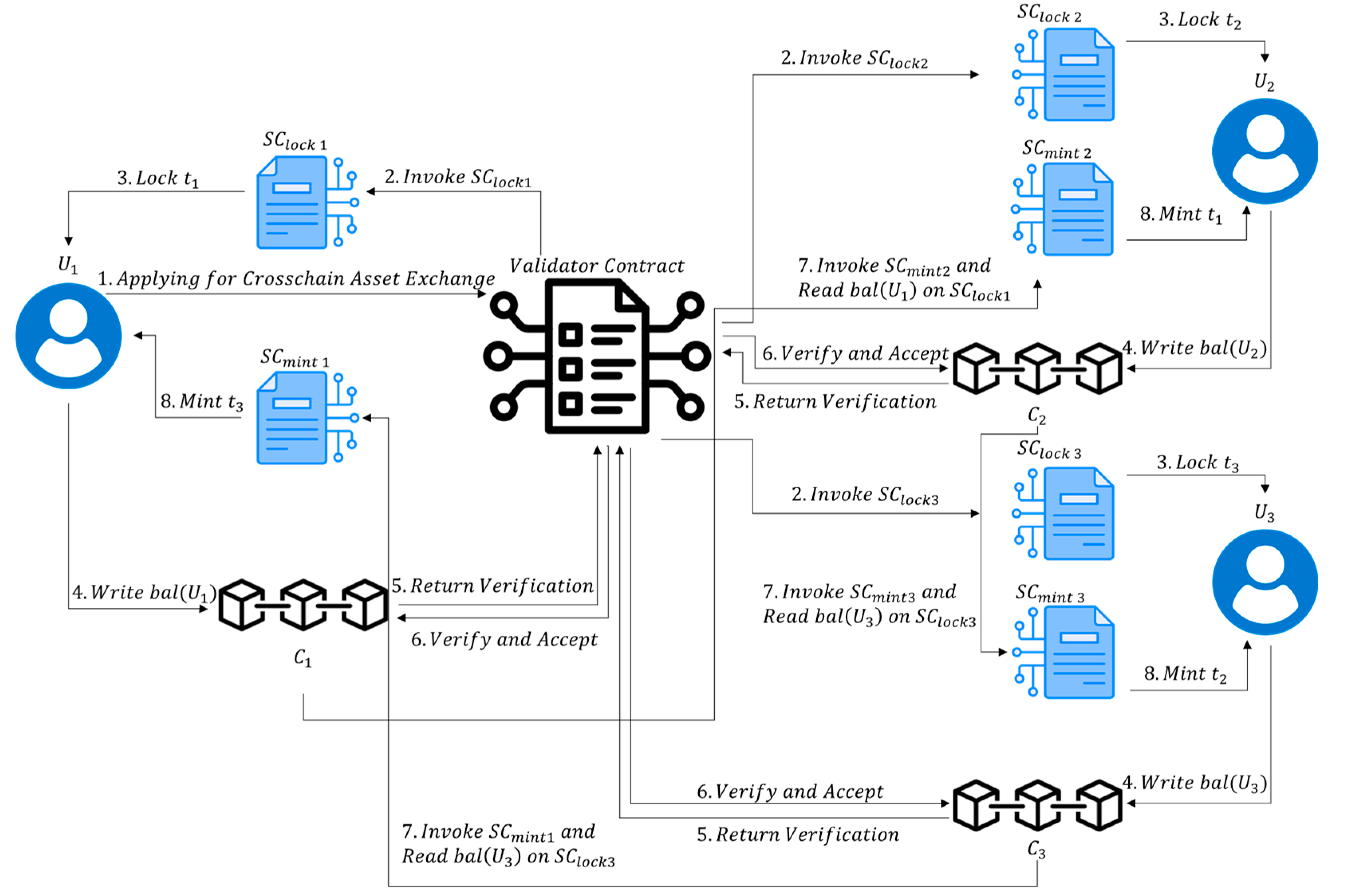
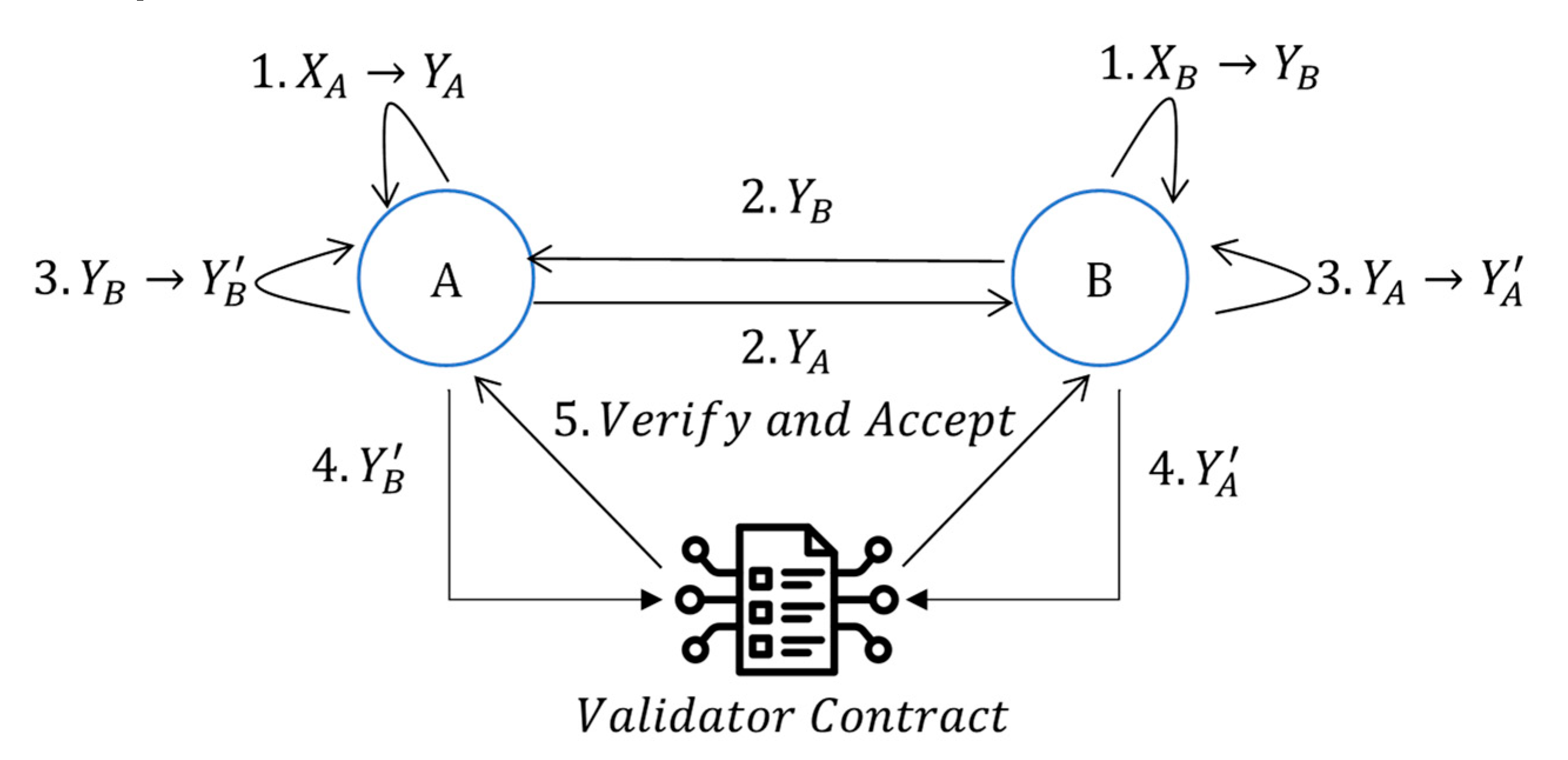
Figure 2 illustrates a hypothetical scenario of multi-chain asset exchange facilitated by SMPTC
3. Initially, User U1 requests the validator contract to initiate a cross-chain transaction (step 1). To transfer asset, the validator contract invokes SClock and notifies participating users to lock their respective assets (step 2 and 3). Subsequently, the validator contract verifies the correctness and atomicity of the cross-chain transaction (step 5 and 6). Upon successful validation, it invokes SCmint to issue assets. To ensure transaction atomicity, SCmint can issue new assets only when users have locked assets on the chain. This necessitates SCmint to read the state of SClock (balance of U, step 4) from the relevant blockchain, which is not directly accessible in cross-chain transactions. This is achieved through validator contracts facilitating the transmission of block headers, transaction information, and correctness proofs between chains (step 5 and 6). SCmint can verify the correctness of user balances through the validator contract (step 7) and, upon successful verification, issue new assets to each user (step 8).
Apart from the aforementioned multi-chain asset transfer, SMPTC3 can also support applications such as multi-chain message interaction and multi-chain voting.
This design offers four benefits.
For large-amount token transfer and transmission of important private data in cross-chain, there is no need to verify its offline identity repeatedly, and its reliability is ensured through strict identity verification on the chain;
In multi-chain ecology, confidential information sharing or anonymous voting can be carried out for mutual distrust among members;
Prevent various types of attacks and avoid possible losses caused by loopholes in consensus protocol in the participating chain;
Due to the reliability of SMPTC3, there is no need for any additional security requirements beyond security logic of underlying blockchains, especially the third-party centralized nodes or the security committees in the relay chain;
Technical challenges. Although there are many theoretical researches [
23,
24] on secure multi-party computation at present, SMC is rarely used for blockchain cross-chain. Secondly, the two-party secure computation model is mostly used in the privacy protection methods on the chain, and whether the multi-party can resist collusion attack is an important problem for protocol security. Thirdly, the execution efficiency of complex computation tasks on ciphertext is very low and the communication cost is high. How to simplify the computation and communication cost in the cross-chain process has become a research challenge. Finally, when using SMC and blockchain, it should be noted that the participating nodes of the two technologies may overlap. Therefore, in practical application, it is necessary to consider that these overlapping situations can meet the security assumptions of the two technologies at the same time.
It is obviously infeasible to directly extend the inter-chain communication of secure two-party secure computation to multi-party, so we propose a novel scheme based on the original research results [
19,
20,
25,
26,
27], presently available schemes include garbled circuit method [
20,
28,
29], secret sharing method [
30,
31,
32] and homomorphic encryption method [
27,
33]. We transform the private information of each participant into a secret set, and use the secret set for SMC. We find that in cross-chain, the set elements are regularly verifiable (traceability and immutability of blockchain), so the secure set is encoded into a special array, and the homomorphic encryption method is combined to solve the problem of SMC, to reduce the high computing cost and communication cost of traditional SMC. Then we use smart contract in EVM or chaincode in privacy channel by Fabric to ensure the information security of the computing process. Therefore, a secure cross-chain protocol with lower computation and communication cost is realized.
Our contribution. In this paper, we make the following contributions:
- 5.
In order to resist malicious attacks such as Sybil and Dos, we improve the homomorphic encryption method (P-ElGamal) and threshold signature method, and combine with the improved secure multi-party computation method (SMPTC3). The improved combination method can resist a variety of irresistible attacks of the original blockchain.
- 6.
We propose an improved multi-party security computation method (SMPTC3) for blockchain. Compared with the original method, it significantly reduces the computational complexity and communication complexity, so the SMPTC3 in this paper is efficient. And SMPTC3 can be applied to a variety of environments except blockchain.
- 7.
We convert the private data of multiple participants in different chains into secure sets. This method has great application value in cross-chain interaction, and can also provide a new secure transmission scheme for other cross-chain methods.
- 8.
SMPTC3 uses secure multi-party computation to solve collusion attacks and avoid relying on third-party central nodes or security committees for authentication. SMPTC3 is a novel cross-chain interaction protocol.
- 9.
Based on fabric, Ethernet and cosmos systems, we implement the multi-party participation model of SMPTC3 and verify it. Experiments show that this protocol has high performance.
3. Confidential Set and Secure Multi-party Computation for Cross-Chain
Firstly, the proposed solution in this paper does not require on-chain participants to encrypt transaction information in their sets using cryptographic algorithms. Since cryptographic algorithms consume significant computational power and communication costs, they are not suitable for cross-chain interactions. Therefore, the solution presented in this paper no longer employs cryptographic algorithms. Instead, it leverages mathematical methods for confidential computation, where participants communicate with each other only twice, establishing inter-chain trust locally. An essential feature of this solution is the elimination of the need to obtain and store public keys of other participants, preventing malicious activities by centralized transaction nodes or relay chains. This approach significantly reduces both computational and communication overhead.
3.1. Constructing Transaction Set
Assuming there are n participants on different chains, denoted as , collectively participating in a cross-chain transaction T, they collectively sign the transaction elements, including transaction signatures, sender identities, locked assets, transaction order, etc., denoted as . These elements are hashed and packaged into sets:
In order to ensure the confidentiality of the set information, each participant converts their set into polynomial form. They construct a quadratic secret polynomial by taking each element (hash value) of their set as a root parameter for the polynomial. The quadratic secret polynomials constructed by participants
can be represented as:
When , iff .
3.2. First Round of Participant Communication
The quadratic secret polynomials for participant
can be organized as follows:
The secret polynomials are then randomly divided into non-zero
shares such that:
Even if an adversary S on a certain chain obtains
shares of the secret polynomial
,
:
From formula (3), it can be seen that cannot obtain the complete secret polynomial. It is crucial to note that each share of the polynomial is non-zero and random, making equation (4) an indeterminate equation. Therefore, it is impossible to construct the complete quadratic secret polynomial . Even if possesses the ability to reverse hash or use rainbow tables [40], they cannot obtain any element of the secret set .
Due to the possibility of collusion attacks such as Sybil attacks and conspiracy attacks in a multi-chain environment, to enhance security, we introduce random sending and random number strategies.
Random Sending Strategy: As the sender, participant randomly sends shares of the polynomial to recipients among the participants , and t may include the sender itself. Thus, is not fixed, and the recipients are not certain whether other recipients have received the shares from the sender. This approach can also be used for cross-chain methods with relay chains and notary groups. In such cases, shares of the polynomial are randomly sent to relay chain nodes, forming a notary group, which then verifies and publicly discloses on the relay chain. The random sending strategy implies that even in a multi-chain environment, a witch attack or collusion attack cannot obtain the complete quadratic secret polynomial. Moreover, common consensus protocols have tolerances of 49% or 33%, while this scheme has a tolerance of 0%. Therefore, the tolerance of this scheme is lower than that of the consensus protocols used by each chain, eliminating the need for security guarantees at the underlying blockchain level.
Random Number Strategy [41]: To further enhance the security of this scheme, we introduce a random number strategy. Specifically, each share of the polynomial is assigned a random number
. To reduce the difficulty of verification and computational overhead in smart contracts, it is necessary to ensure:
From formulas (3), (4), and (5), it can be observed that with the introduction of the random number strategy, if obtains an incomplete secret polynomial, the sum of some random numbers must be non-zero. This will significantly increase the decryption cost, greatly enhancing the security of the secret polynomial.
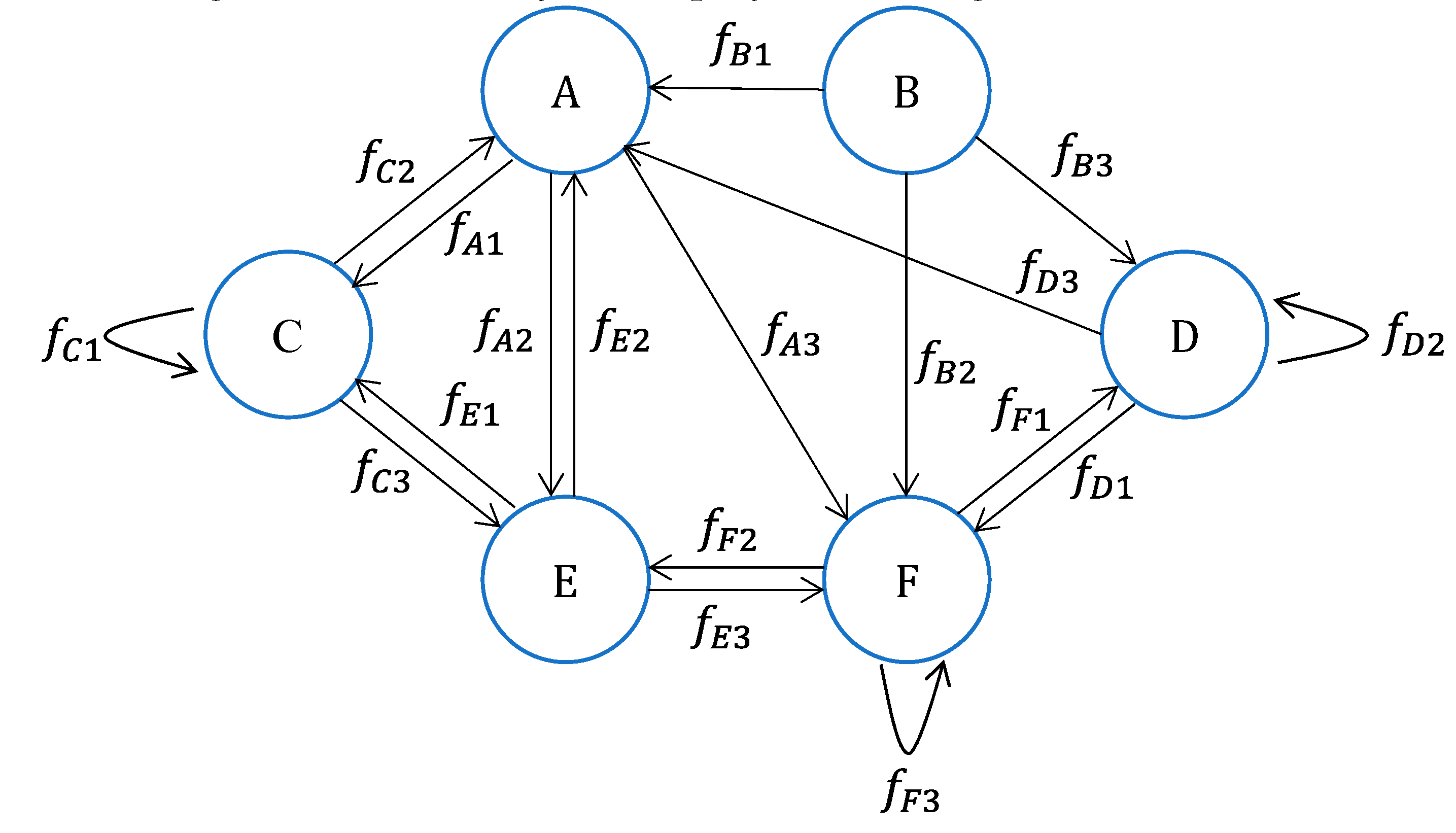
The first-round communication example among participant nodes is illustrated in
Figure 3, involving six participant nodes labeled as A, B, C, D, E, F. In this initial communication round, each node divides its quadratic secret polynomial into three parts:
Then each node randomly sends them to the cross-chain participant nodes.
The participants randomly distribute their respective secret polynomial fragments. As evident from nodes C, D, and F in the diagram, it's possible for a participant to distribute a fragment randomly to themselves. Meanwhile, as node B indicates, due to the random transmission strategy, a participant node might not receive any secret polynomial fragments.
3.3. Second Round of Participant Communication
After the first communication round, each participant
adds up all the partial polynomials they possess to form a new secret polynomial
. Due to the random sending strategy,
may be zero. After forming
, the second communication protocol is initiated. Participant
sends the
they own to every participant node involved in the cross-chain transaction. Upon receiving
, participant
adds them up to create a new secret polynomial
.
From formulas (3), (5), and (6), the following computation process can be derived, resulting in formula (7).
We provided the construction process of the secret polynomial in Protocol 1.
|
Protocol 1 Protocol 1 Constructing the Secret Polynomial |
Input: Transaction Elements from each Participant
Output: Secret Polynomial
1: Each participant hashes and compiles their transaction elements into a secret set .
2: constructs quadratic secret polynomials based on the elements in the secret set .
3: randomly divides into parts. For each participant and each polynomial fragment , generate a random number such that . These random numbers enhance security and ensure that .
4: randomly sends the t polynomial fragments to participating nodes.
5: Participants collectively add up all the polynomial fragments to obtain , then broadcast it to all cross-chain participants.
6: Each node adds up all received polynomials to construct . |
After the first round of communication, each participant consolidates all the secret polynomial fragments they own into a new secret polynomial, denoted as:
After the consolidation, each participant broadcasts the secret polynomial they possess to the participant network, ensuring that eventually, each participant has the complete secret polynomial F. Specially, as in the case of node B shown in
Figure 3,
is zero, for the integrity and security of the protocol, B also needs to broadcast
to the network.
3.4. Secure Comparison
When the element
represents transaction verification information collectively possessed by all participants,
can be transformed into the following form:
where
is a
-degree polynomial obtained by dividing
by
. Substituting e_i into equation (8), we get
, implying
. If a transaction element
is not a shared element, then
, and it follows that
, which implies
.
Each participant can substitute their transaction elements into equation (7). If , then represents transaction information collectively owned by all participants. The smart contract can then make decisions based on predefined elements for comparison.
If the transaction elements possessed by each participant are accurately compared, operations such as cross-chain transfers are executed.
In Protocol 2, a secure multiparty computation scheme for transaction elements is provided.
|
Protocol 2 Secure Comparison Protocol |
Output: Verification Result
Procedure CompareElements (F(x), e_i)
For i=1 to m
If F(e_i)!=0
Then return False // Verification failed, indicating data tampering, terminate the cross-chain contract
Else
Continue
End if
End
Send transactions to Pools // Execute cross-chain transfer |
5. Trusted Cross-Chain Protocol for Two Participants
In this section, we aim to extend SMPTC3 to accommodate two participants and demonstrate through an example and security analysis that this approach is ineffective. Subsequently, we introduce a two-participant cross-chain verification method based on discrete logarithms.
5.1. Direct Extension of TMPC3 to Two Participants
In SMPTC
3, the fundamental security assumption is
, signifying multiple participants collectively executing cross-chain verification tasks. It allows participants to conceal data within secret polynomials and share them among other participants while ensuring the secrecy of data. However, a majority of cross-chain interaction scenarios are concentrated on two participants across two chains, i.e.,
, from section 3.1, resulting in t=2, which can be derived from Equation (3):
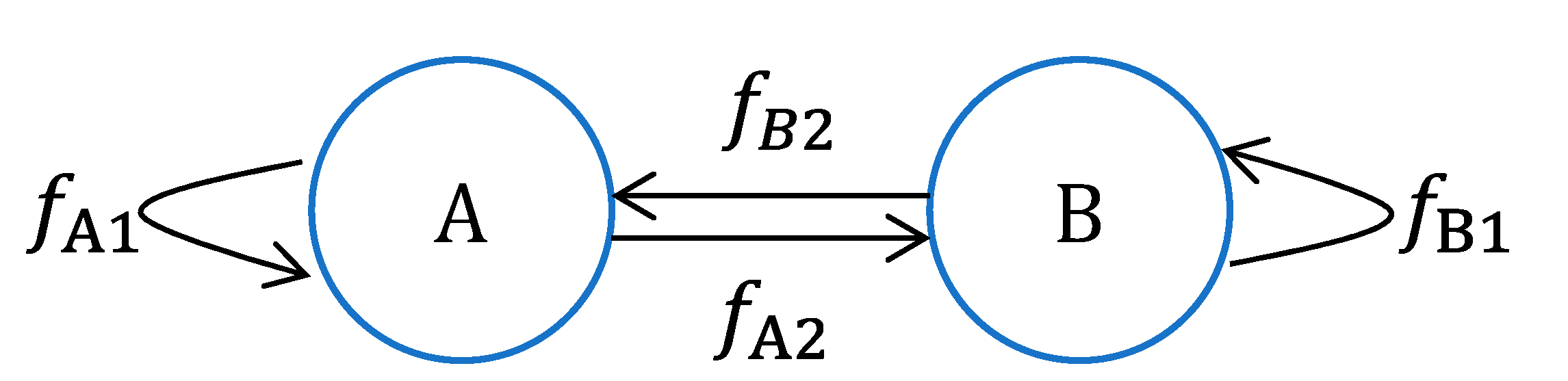
The execution of the first round of communication leads to the transformation of
Figure 3 into
Figure 4:
From equation (9), it can be observed that B can directly compute the complete quadratic secret polynomial of A. This makes Secret information of A highly susceptible to direct deduction, rendering the direct extension of SMPTC3 to two-party computation ineffective.
5.2. Two-Participant Cross-Chain Verification Method Based on Discrete Logarithms
In practical cross-chain scenarios involving two participants, the data source is determinate. Therefore, relying on random transmission based on quadratic secret polynomials becomes ineffective. Hence, leveraging discrete logarithms [41], we have designed a verification method (2PC3) tailored for Two-participant cross-chain scenarios.
Two participants, A and B, first collectively agree on a large prime number . Subsequently, each generates a large random number, and , respectively. Then, based on their respective sets and , they create and through the first round of discrete logarithm encryption and exchange these (steps 1 and 2). Following this, A and B individually perform the second round of discrete logarithm encryption to obtain and (step 3) and send these results to the verification contract (step 4). Upon successful comparison by the verification contract, a verification success message is sent to A and B (step 5).
The first round of discrete logarithm encryption is represented as:
The second round of discrete logarithm encryption is represented as:
Derived from equations (9) and (10):
From equation (11), if
, then
, where the exponents
and
along with the large prime number p are randomly generated. Hence, the encryption verification method used in this paper ensures semantic security. Due to the complexity of the discrete logarithm problem, deducing xi is almost impossible. Even in the presence of curious nodes on the chain or among participants, access to confidential information is unattainable.
|
Protocol 3 2PC3 Protocol |
Input: Transaction Elements Set and from Participants and
Output: Verification Result
1: Participants and jointly generate a large prime number .
2: and each generate a large random number and .
3: and respectively perform the first round of discrete logarithm encryption on elements from set and from set , denoted as, where , then forming confidential sets and .
4: and mutually exchange and .
5: and respectively perform the second round of discrete logarithm encryption on and , denoted as , forming sets and .
6: and send and to the validator contract. After verification by the validator contract, the verification result is sent to the participants. |
6. Implementation and Evaluation
The experiments for SMPTC3 are based on Fabric and the Ethereum test version Rinkeby (Geth) systems. The cross-chain contracts are implemented using Go and Solidity 3multi-party cross-chain algorithm from Chapter 3 and the two-party cross-chain algorithm from Chapter 5. Depending on the number of participants, the contract will automatically select the corresponding cross-chain solution(2PC or MPC). Based on the characteristics of blockchain cross-chain transactions (cross-chain information transmission also falls under cross-chain transactions), we use methods such as hashing and feature extraction to compute the transaction features, forming a verifiable high-privacy secret set. Then, based on the concept of Multi-Party Secure Computation (MPC) and combined with the communication characteristics of blockchain, we achieve communication and secure computation.
6.1. Experiment Setup
We conducted experimental tests using an Intel(R) Xeon(R) Gold 6354 CPU @ 3.00GHz and 504GB RAM. In accordance with requirements and industry standards, we report the average execution time and fees. The reported results are derived from the average of ten executions.
6.3. Security Test
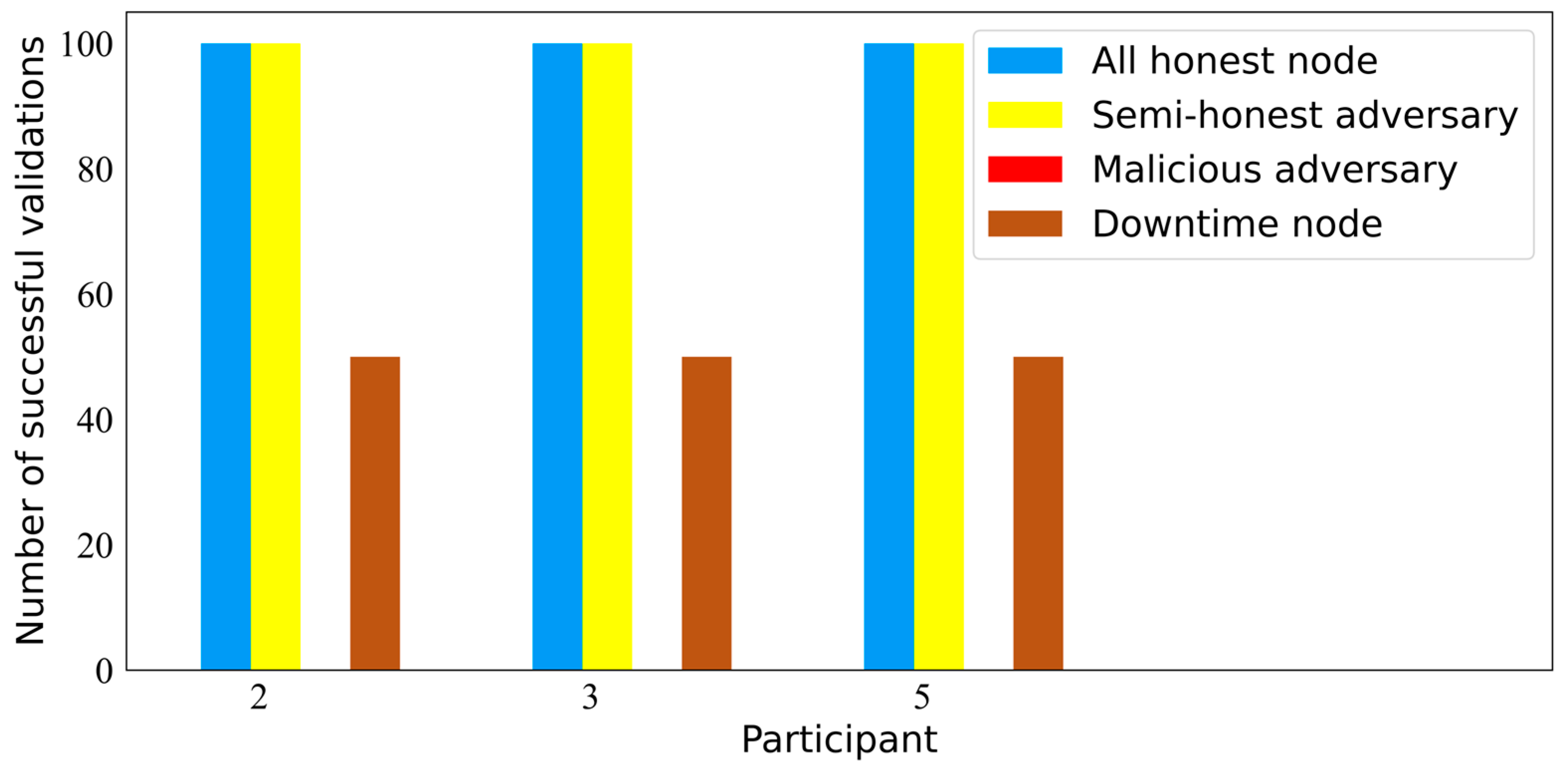
We divided the participant nodes into four types: honest nodes, semi-honest adversaries, malicious adversaries, and downtime nodes. Based on these classifications, we set up four test scenarios: all honest nodes, an unspecified number of semi-honest adversaries, mostly honest nodes with one malicious adversary, and mostly honest nodes with one downtime node. Security testing was conducted with
participants, each scenario undergoing 100 actual tests, resulting in
Figure 6.
From
Figure 6, we can see that SMPTC
3 can operate normally when all participants are honest nodes or when there are semi-honest adversaries. According to formulas (4-8), the semi-honest adversary model can only obtain partial fragments of the secret set and cannot acquire effective secret information. When there is a malicious adversary among the participants, SMPTC
3 cannot pass the verification, and the cross-chain transaction will be abandoned, strictly ensuring the safety of cross-chain assets and information. Therefore, in malicious adversary environment, the number of successful verifications is zero. In the downtime node test environment, we divided it into two scenarios: one where the node downtime time exceeds the verification waiting time, and the other where the node recovers and re-responds to verification. Experimental tests show that if the node recovers from the crash and promptly responds and continues to participate honestly in verification, the verification task can still be successfully completed. This experiment demonstrates that SMPTC
3 has good security and robustness, ensuring the safety of cross-chain assets and information.
6.3. Verify Time of SMPTC3
We measured the time overhead required for cross-chain transactions. For comparison with SMPTC
3, we deployed conventional multi-signature notary mechanisms and sidechain mechanisms as control groups in the same experimental environment. Due to the complexity of multi-chain cross-chain scenarios, we designed the control group to achieve optimal experimental results, as shown in
Figure 7. This ideal situation assumes there are only
cross-chain operations (with
cross-chain participants, the maximum number of cross-chain operations could be
, and the minimum is
).
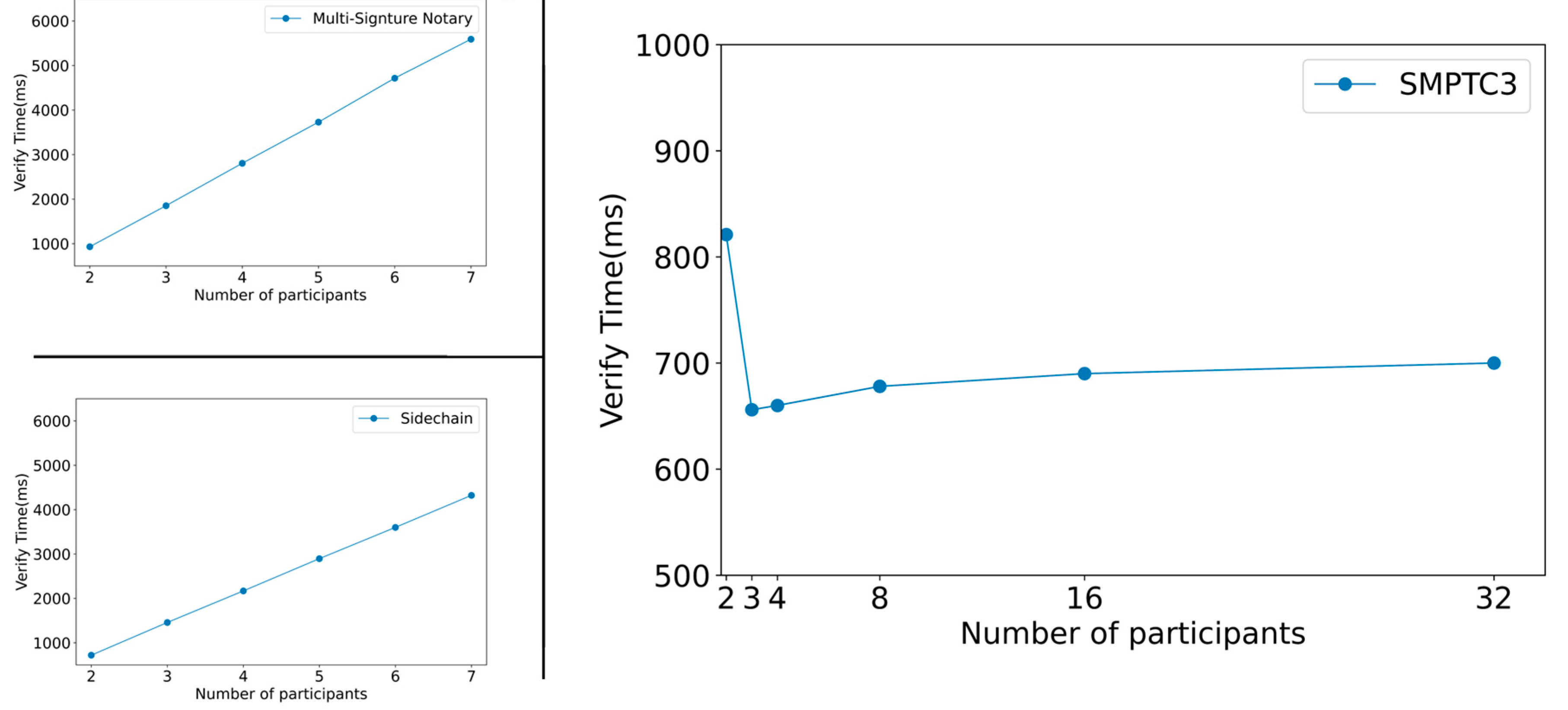
After executing each set of experiments ten times and averaging the results, we obtained the data presented in
Figure 8. As shown in
Figure 8, the ideal verify time for the multi-signature notary mechanism and the sidechain mechanism increases linearly (
) with the number of participants. Given that the maximum number of cross-chain operations could be
, it is evident that the worst-case scenario will show a quadratic increase (
).
In contrast, for SMPTC3, the horizontal axis range of participants is , and the overall trend remains horizontal. It is worth noting that with only two participants, verify time of SMPTC3 is slightly higher than in the multi-participant scenario. According to formulas (10-12), this is likely due to the computation time for exponential and modular operations. For multiple participants, as the number of participants increases, SMPTC3 verify time generally remains stable. However, when there are too many participants, such as , the verify time slightly increases. As indicated by protocols 1 and 2, this is due to the increased communication and computation costs caused by the larger number of elements involved in the computation. But such situations are uncommon in practical applications and do not hold significant practical value.
In summary, SMPTC3 can effectively solve the complex problem of cross-chain interactions among multiple participants in practical applications. It also satisfactorily meets the basic requirements for two-party interactions.