Submitted:
27 July 2024
Posted:
29 July 2024
You are already at the latest version
Abstract
Keywords:
Introduction
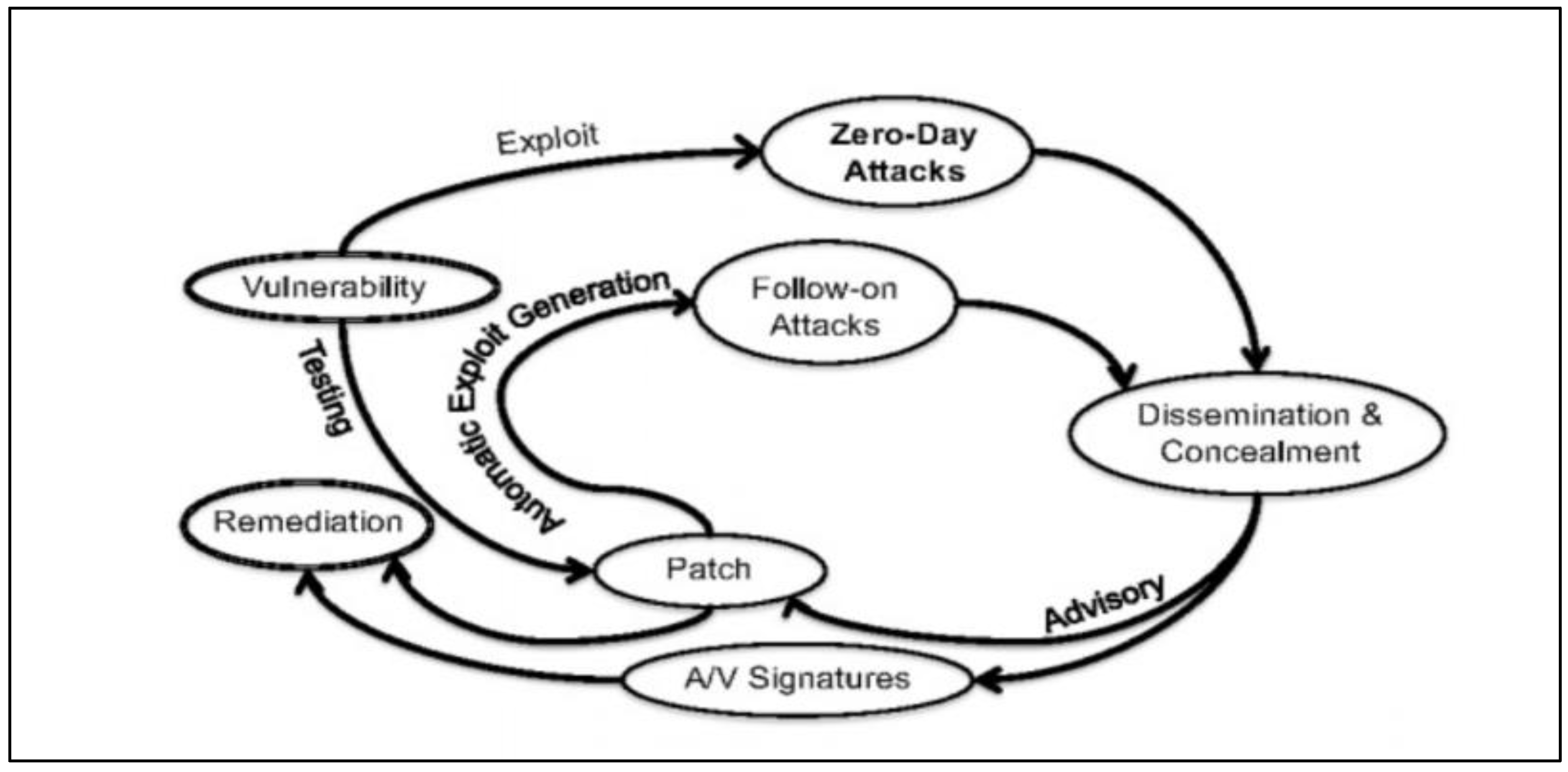
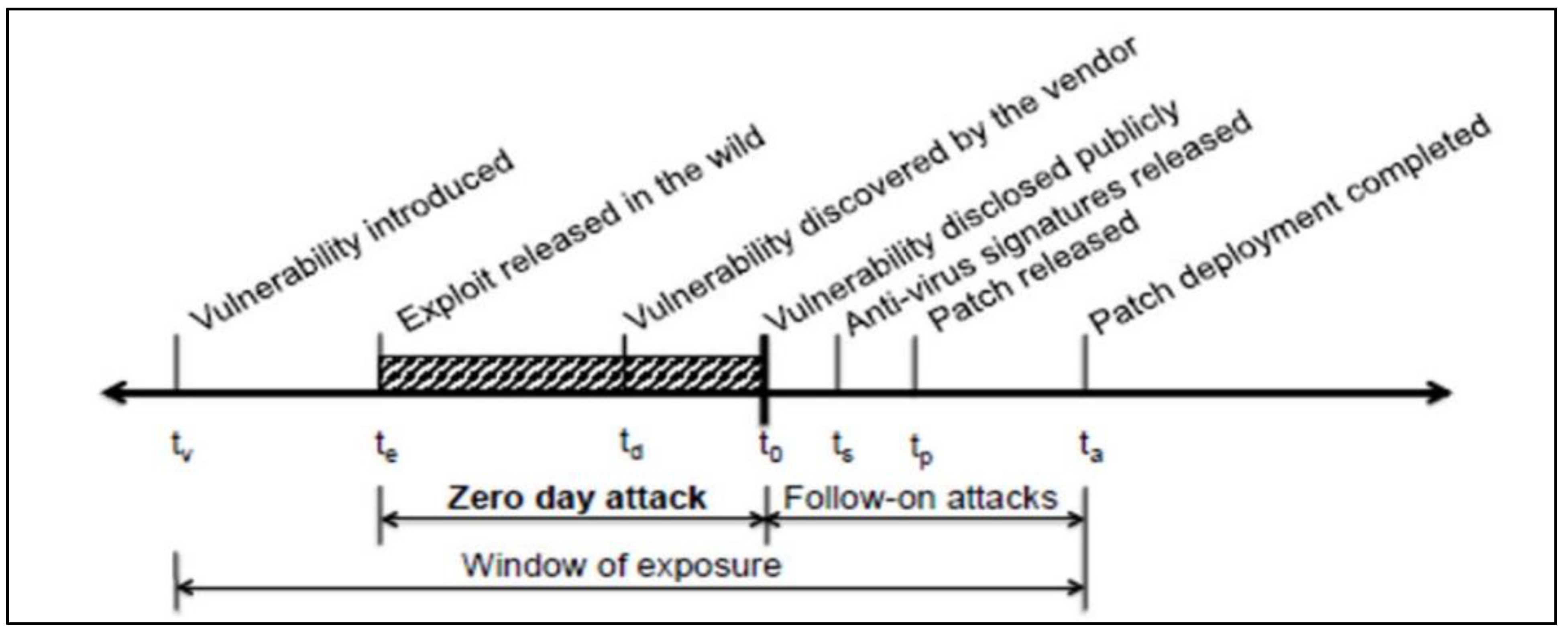
Lifecycle Of a Zero-Day Vulnerability
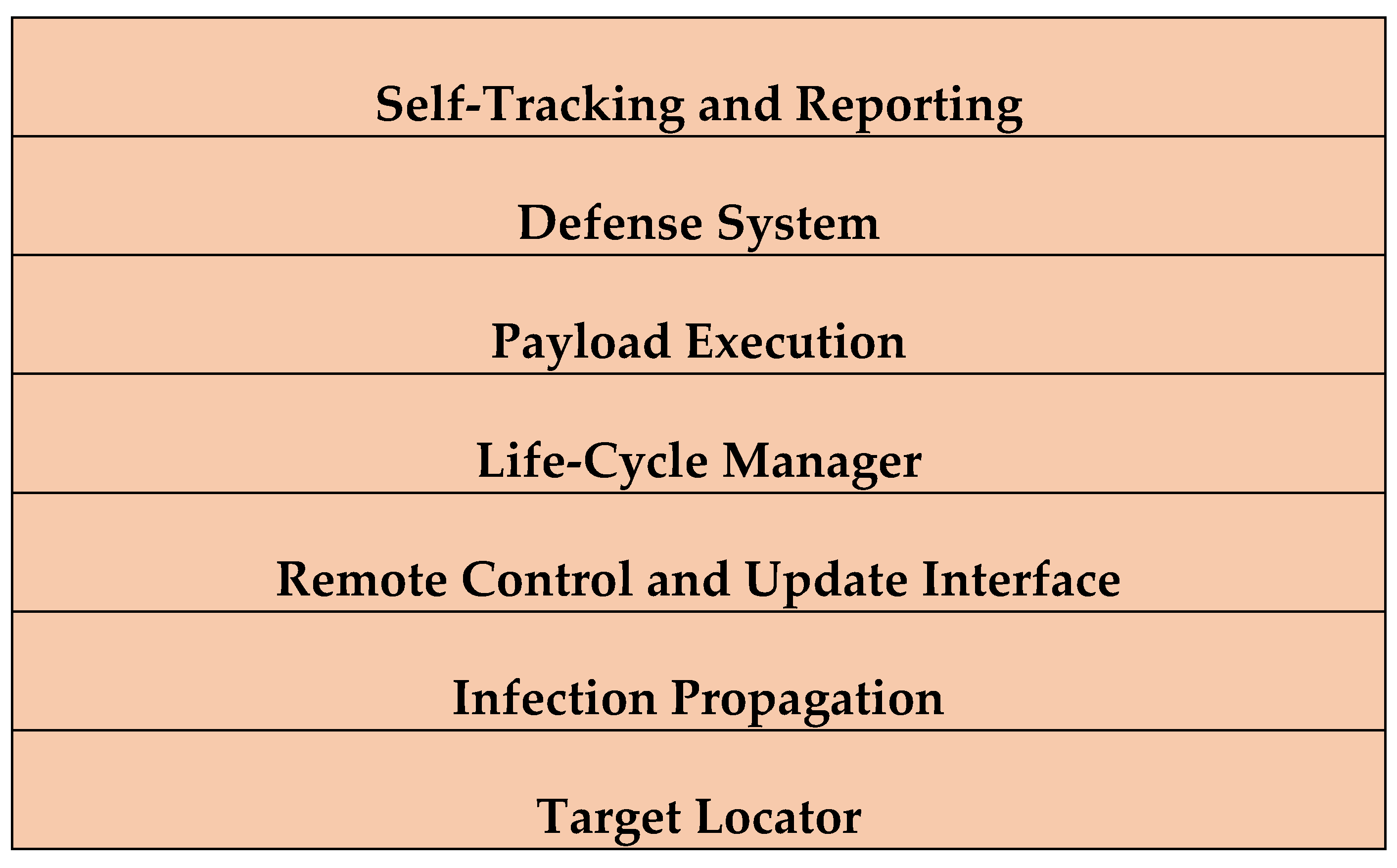
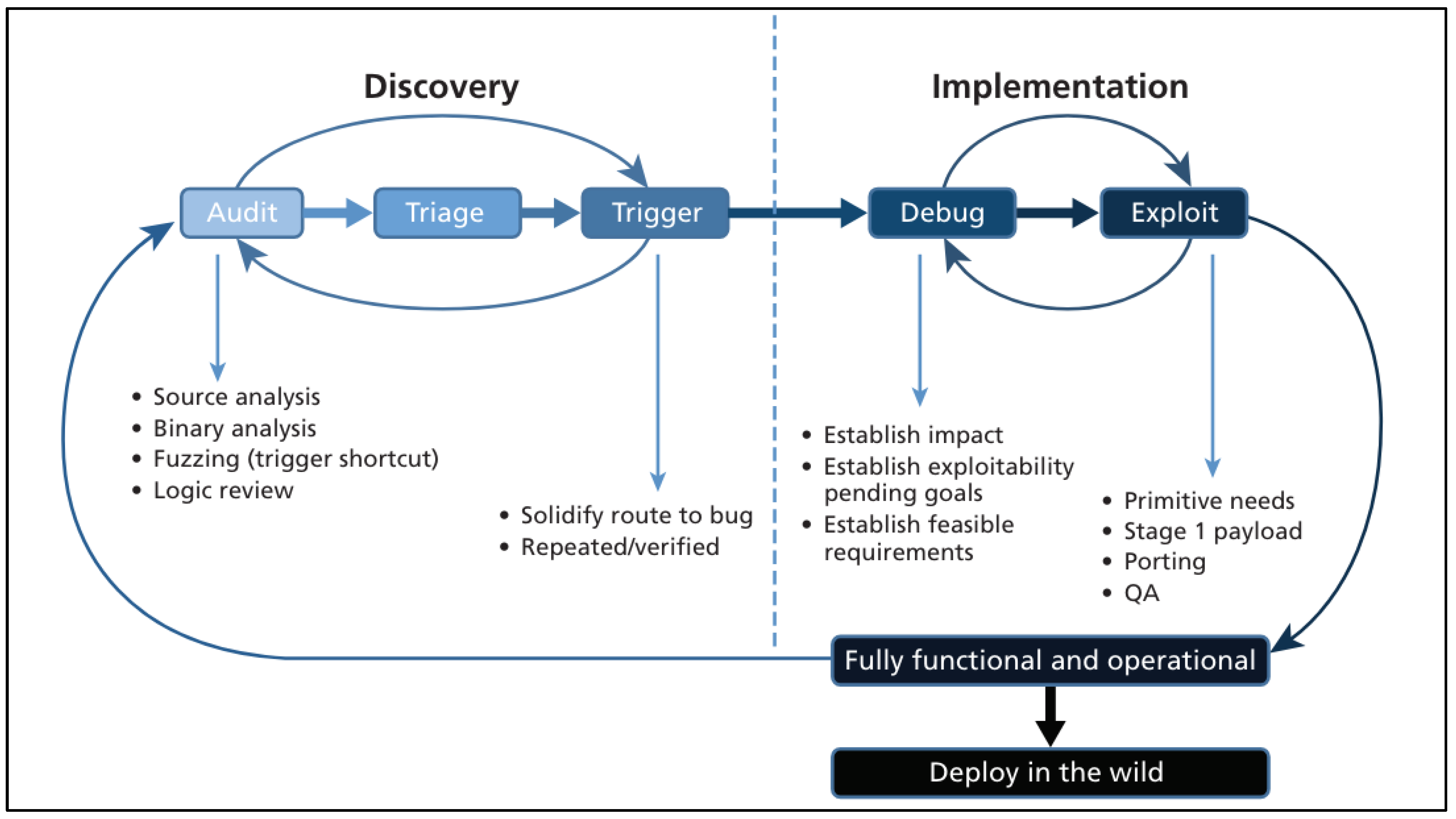
Technologies and Phases of Zero-Day Exploit
Discussion on Security Issues and Countermeasures
Case 1: HAFNIUM targeting Exchange Servers with 0-Day Exploits
Case Overview
Security Issues
| CVE | Vulnerability Type |
|---|---|
| CVE-2021-26855 | Server-Side Request Forgery (SSRF) |
| CVE-2021-26857 | Insecure Deserialization |
| CVE-2021-26858 | Arbitrary File Write |
| CVE-2021-27065 | Arbitrary File Write |
Threats Posed by Security Issues
Case 2: Log4Shell: An Arbitrary Code Execution Zero-Day in Log4j
Case Overview
Security Issues
Threats Posed by Security Issues
Discussion on Security Countermeasures
Case 1: HAFNIUM Targeting Exchange Servers with 0-Day Exploits
Countermeasures Taken
- CVE-2021-26855 exploitation can be detected via some Exchange HttpProxy logs detailed in the script.
- CVE-2021-26858 exploitation can be detected via the Exchange log files detailed in the script.
- CVE-2021-26857 exploitation can be detected via the Windows Application event logs.
- CVE-2021-27065 exploitation can be detected via the detailed Exchange log files.
Case 2: Log4Shell: An Arbitrary Code Execution Zero-Day in Log4j
Countermeasures Taken
- Log4j 2.15.0: The initial fix disabled the JNDI lookups by default for log messages.
- Log4j 2.16.0: This version removed support for message lookups and limited JNDI functionality to only the localhost by default, to further reduce the attack surface.
- Log4j 2.17.0 and 2.17.1: Additional fixes and improvements were made to address related issues and ensure more comprehensive protection.
- Set the system property log4j2.formatMsgNoLookups to true to disable the message lookups function completely.
- Remove the JndiLookup class from the classpath by deleting it from the JAR file (e.g., using the zip command).
Countermeasures Proposed
Conclusions
Key Takeaways
- Rapid Patch Deployment: The immediate release and application of patches were crucial in countering the impacts of these exploits.
- Advanced Detection Systems: Implementing sophisticated intrusion detection systems (IDS) can help in early identification of exploits.
- Proactive Security Posture: Encouraging a proactive security approach through regular audits, constant monitoring, and the use of behavioral analytics is essential.
- Network Segmentation and Access Controls: Reducing the amount of damage that may be caused by the exploit through network segmentation and strict access controls is vital.
References
- Ablon, L. and Bogart, A. (n.d.). Zero Days, Thousands of Nights The Life and Times of Zero-Day Vulnerabilities and Their Exploits. [online] Available at: https://web.archive.org/web/20180720224154id_/https://www.rand.org/content/dam/rand/pubs/research_reports/RR1700/RR1751/RAND_RR1751.pdf [Accessed 10 Jun. 2024].
- Adair, S. (2021) Operation Exchange Marauder: Active exploitation of multiple Zero-Day Microsoft Exchange vulnerabilities.
- Adepu, S.; et al. (2019) 'Attacks on smart grid: power supply interruption and malicious power generation,' International Journal of Information Security, 19(2), pp. 189–211. [CrossRef]
- Akello, N.B.O. (2024) 'Organizational information security threats: Status and challenges,' World Journal of Advanced Engineering Technology and Sciences, 11(1), pp. 148–162. [CrossRef]
- Alferidah, D.K. and Jhanjhi, N. (2020) 'Cybersecurity Impact over Bigdata and IoT Growth,' 2020 International Conference on Computational Intelligence (ICCI) [Preprint]. [CrossRef]
- Alkinani, M.H.; et al. (2021) '5G and IoT Based Reporting and Accident Detection (RAD) System to Deliver First Aid Box Using Unmanned Aerial Vehicle,' Sensors, 21(20), p. 6905. [CrossRef]
- Ali, I., Jhanjhi, N. Z., Amsaad, F., & Razaque, A. (2022). The role of Cutting-Edge Technologies in Industry 4.0. Chapman and Hall/CRC eBooks, 10, 9781003203087-4.
- Ashfaq F, Ghoniem RM, Jhanjhi NZ, Khan NA, Algarni AD. Using Dual Attention BiLSTM to Predict Vehicle Lane Changing Maneuvers on Highway Dataset. Systems. 2023; 11(4):196. [CrossRef]
- Attaullah, M.; et al. (2022) 'Initial stage COVID-19 detection system based on patients’ symptoms and chest X-Ray images,' Applied Artificial Intelligence, 36(1). [CrossRef]
- Azam, H. , Dulloo, M.I., Majeed, M.H., Wan, J.P.H., Xin, L.T. and Sindiramutty, S.R. (2023) 'Cybercrime Unmasked: Investigating cases and digital evidence,' International Journal of Emerging Multidisciplinaries. Computer Science and Artificial Intelligence, 2(1). [CrossRef]
- Azam, H. , Dulloo, M.I., Majeed, M.H., Wan, J.P.H., Xin, L.T., Tajwar, M.A., et al. (2023) 'Defending the digital Frontier: IDPS and the battle against Cyber threat,' International Journal of Emerging Multidisciplinaries. Computer Science and Artificial Intelligence, 2(1). [CrossRef]
- Azam, H. , Tajwar, M.A., et al. (2023) 'Innovations in Security: A study of cloud Computing and IoT,' International Journal of Emerging Multidisciplinaries. Computer Science and Artificial Intelligence, 2(1). [CrossRef]
- Azeem, M.; et al. (2021) 'FOG-Oriented secure and lightweight data aggregation in IOMT,' IEEE Access, 9, pp. 11 1072–111082. [CrossRef]
- Badyal, N. (2024) Scalable techniques for risk assessment of open-source libraries. [CrossRef]
- Bilge, L. and Dumitraş, T. (2012) 'Before we knew it,': Proceedings of the 2012 ACM Conference on Computer and Communications Security [Preprint]. [CrossRef]
- Bompos, K. (2020). Naval Postgraduate School Monterey, California Thesis Development Time Of Zero-Day Cyber Exploits In Support Of Offensive Cyber Operations.
- Changsan, U. and Boonyopakorn, P. (2023) 'Log4shell Investigate Based On Generic Computer Forensic Investigation Model,' 2023 20th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON) [Preprint]. [CrossRef]
- Chesti, I.A.; et al. (2020) 'Evolution, Mitigation, and Prevention of Ransomware,' 2020 2nd International Conference on Computer and Information Sciences (ICCIS) [Preprint]. [CrossRef]
- Conti ransomware threat group adopts Log4j exploit to compromise VMware vCenter servers (no date). https://www.broadcom.com/support/security-center/protection-bulletin/conti-ransomware-threat-group-adopts-log4j-exploit-to-compromise-vmware-vcenter-servers.
- Dell (2022) How to remove JndiLookup class from the log4j-2.x core jar file. https://www.dell.com/support/kbdoc/en-us/000194596/how-to-remove-jndilookup-class-from-the-log4j-2-x-core-jar-file.
- Elmo, D. , II (2023) The Open Charge Point Protocol (OCPP) version 1.6 Cyber Range a training and testing platform. https://corescholar.libraries.wright.edu/etd_all/2788/.
- en-us (no date). https://help.minecraft.net/hc/en-us/articles/4416199399693-Security-Vulnerability-in-Minecraft-Java-Edition.
- Fadolalkarim, D. and Fadolalkarim, D. (2024) 'DCAFixer: an automatic tool for bug detection and repair for database Java client applications,' IEEE Transactions on Dependable and Secure Computing/IEEE Transactions on Dependable and Secure Computing, pp. 1–16. [CrossRef]
- Fatima-Tuz-Zahra, N.; et al. (2020) 'Proposing a Hybrid RPL Protocol for Rank and Wormhole Attack Mitigation using Machine Learning,' 2020 2nd International Conference on Computer and Information Sciences (ICCIS) [Preprint]. [CrossRef]
- Fidler, M. (2024) Zero progress on Zero days: How the last ten years created the modern spyware market. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4626426.
- Fleury, M. and Reverbel, F. (2003) 'The JBoss extensible server,' in Lecture notes in computer science, pp. 344–373. [CrossRef]
- GeeksforGeeks. (2020). Zero-day Exploit (Cyber Security Attack). [online] Available at: https://www.geeksforgeeks.org/zero-day-exploit-cyber-security-attack/.
- Gill, S.H.; et al. (2022) 'Security and privacy aspects of cloud Computing: A Smart Campus case study,' Intelligent Automation and Soft Computing/Intelligent Automation & Soft Computing, 31(1), pp. 117–128. [CrossRef]
- Goni, A. (2020) 'International Journal of Research and Scientific Innovation,' International Journal of Research and Scientific Innovation [Preprint]. [CrossRef]
- Gopi, R.; et al. (2021) 'Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things,' Multimedia Tools and Applications, 81(19), pp. 2 6739–26757. [CrossRef]
- Gouda, W.; et al. (2022) 'Detection of COVID-19 based on chest x-rays using deep learning,' Healthcare, 10(2), p. 343. [CrossRef]
- Grigutytė, M. and Grigutytė, M. (2024) Microsoft Exchange zero-day vulnerability explained. https://nordvpn.com/blog/microsoft-exchange-exploits/.
- He, Y.; et al. (2022) 'A survey on Zero Trust architecture: Challenges and future trends,' Wireless Communications and Mobile Computing, 2022, pp. 1–13. [CrossRef]
- Humayun, M.; et al. (2022) 'A Transfer Learning Approach with a Convolutional Neural Network for the Classification of Lung Carcinoma,' Healthcare, 10(6), p. 1058. [CrossRef]
- Hurst, W. and Shone, N. (2024) 'Critical infrastructure security: Cyber-threats, legacy systems and weakening segmentation,' in Elsevier eBooks, pp. 265–286. [CrossRef]
- Hussain, K.; et al. (2024) 'Threats and Vulnerabilities of Wireless Networks in the Internet of Things (IoT),' 2024 IEEE 1st Karachi Section Humanitarian Technology Conference (KHI-HTC) [Preprint]. [CrossRef]
- Kaspersky (2018). What is Zero Day Exploit? [online] www.kaspersky.com. Available at: https://www.kaspersky.com/resource-center/definitions/zero-day-exploit.
- Kumar, M.S.; et al. (2021) 'Blockchain based peer to peer communication in autonomous drone operation,' Energy Reports, 7, pp. 7925–7939. [CrossRef]
- Lyu, M. , Gharakheili, H.H. and Sivaraman, V. (2024) 'A survey on Enterprise Network Security: asset behavioral monitoring and Distributed attack Detection,' IEEE Access, p. 1. [CrossRef]
- M. Lim, A. M. Lim, A. Abdullah, N. Z. Jhanjhi, M. Khurram Khan and M. Supramaniam, "Link Prediction in Time-Evolving Criminal Network With Deep Reinforcement Learning Technique," in IEEE Access, vol. 7, pp. 184797-184807, 2019. [CrossRef]
- Muhammad, Ibrahim, Humayun Mamoona, N. Z. Jhanjhi, and M. N. Talib. "Intelligent Computing and Innovation on Data Science." (2021): 425-434.
- Möller, D.P.F. (2023) 'Threats and threat intelligence,' in Advances in information security, pp. 71–129. [CrossRef]
- Msrc (2021) Guidance for responders: Investigating and remediating on-premises Exchange Server vulnerabilities | MSRC Blog | Microsoft Security Response Center.
- Nair, D. and Mhavan, N. (2023) 'Augmenting Cybersecurity: A survey of intrusion detection systems in combating zero-day vulnerabilities,' in Contemporary studies in economic and financial analysis, pp. 129–153. [CrossRef]
- Narang, S. (2021). CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065: Four Zero-Day vulnerabilities in Microsoft Exchange Server exploited in the Wild. https://www.tenable.com/blog/cve-2021-26855-cve-2021-26857-cve-2021-26858-cve-2021-27065-four-microsoft-exchange-server-zero-day-vulnerabilities.
- Nathaniel, H. (2022) Defense Technical Information Center. https://apps.dtic.mil/sti/citations/trecms/AD1200567.
- Nguyen, T.G.; et al. (2023) 'Multi-Granularity detector for vulnerability fixes,' IEEE Transactions on Software Engineering, 49(8), pp. 4035–4057. [CrossRef]
- owasp.org. (n.d.). Fuzzing | OWASP. [online] Available at: https://owasp.org/www-community/Fuzzing#:~:text=A%20fuzzer%20is%20a%20program.
- Pauley, E. , Barford, P. and McDaniel, P. (2023a) 'The CVE Wayback Machine: Measuring Coordinated Disclosure from Exploits against Two Years of Zero-Days,' ACM [Preprint]. [CrossRef]
- Pratama, A. and Adi Rafrastara, F. (2012). Computer Worm Classification. International Journal of Computer Science and Information Security, [online] 10(4), pp.21–24. Available at: https://www.researchgate.net/publication/299580232_Computer_Worm_Classification.
- Rains, T. (2020) Cybersecurity Threats, malware Trends, and Strategies, Packt Publishing eBooks. http://uh2.scholarvox.com/catalog/book/88897769.
- Rhodes, C. and Bettany, A. (2016) Windows installation and update troubleshooting, Apress eBooks. [CrossRef]
- Riegler, M.; et al. (2023) 'A model-based mode-switching framework based on security vulnerability scores,' Journal of Systems and Software/the Journal of Systems and Software, 200, p. 11 1633. [CrossRef]
- Riofrío, X. , Astudillo-Salinas, F., Tello-Oquendo, L. and Merchan-Lima, J. (2021). The Zero-day attack: Deployment and evolution. Latin-American Journal of Computing, [online] 8(1), pp.38–53. Available at: https://lajc.epn.edu.ec/index.php/LAJC/article/view/208/148 [Accessed 22 Apr. 2024].
- Robinson, P. (2024) Microsoft Exchange Server attack: The Hafnium Breach. https://www.lepide.com/blog/the-hafnium-breach-microsoft-exchange-server-attack/.
- Saurabh, K.; et al. (2024) 'HMS-IDS: threat intelligence integration for Zero-Day exploits and advanced persistent threats in IIoT,' Arabian Journal for Science and Engineering [Preprint]. [CrossRef]
- Security, M. 365 and Intelligence, M.T. (2023) HAFNIUM targeting Exchange Servers with 0-day exploits.
- Shah, I.A. , Jhanjhi, N.Z. and Laraib, A. (2022) 'Cybersecurity and blockchain usage in contemporary business,' in Advances in information security, privacy, and ethics book series, pp. 49–64. [CrossRef]
- Shahine, M. (2023). CCleaner vs BleachBit: A Deep Dive. [online] Internet Safety Statistic.
- Shandilya, S.K.; et al. (2024) 'Achieving Digital Resilience with Cybersecurity,' in EAI/Springer Innovations in Communication and Computing, pp. 43–123. [CrossRef]
- Sharifonnasabi Fatemeh, Jhanjhi Noor Zaman, John Jacob, Obeidy Peyman, Band Shahab S., Alinejad-Rokny Hamid, Baz Mohammed, Hybrid HCNN-KNN Model Enhances Age Estimation Accuracy in Orthopantomography, Frontiers in Public Health, VOLUME 10, 2022, DOI=10.3389/fpubh.2022.879418.
- Sindiramutty, S.R. (2024) 'Autonomous Threat Hunting: a future paradigm for AI-Driven Threat intelligence,' arXiv (Cornell University) [Preprint]. [CrossRef]
- Sindiramutty, S. R. , Jhanjhi, N. Z., Tan, C. E., Khan, N. A., Shah, B., & Gaur, L. (2024). Securing the Digital Supply Chain Cyber Threats and Vulnerabilities. In N. Jhanjhi & I. Shah (Eds.), Cybersecurity Measures for Logistics Industry Framework (pp. 156-223). IGI Global. [CrossRef]
- Sindiramutty, S.R.; et al. (2024) 'Cybersecurity measures for logistics industry,' in Advances in information security, privacy, and ethics book series, pp. 1–58. [CrossRef]
- Singh, N. , Buyya, R. and Kim, H. (2024) 'Securing Cloud-Based Internet of Things: Challenges and mitigations,' arXiv (Cornell University) [Preprint]. [CrossRef]
- Spafford, E. , Metcalf, L. and Dykstra, J. (2023) Cybersecurity myths and misconceptions: Avoiding the Hazards and Pitfalls That Derail Us. Addison-Wesley Professional.
- Ray, S. K. , Sinha, R., & Ray, S. K. (2015, June). A smartphone-based post-disaster management mechanism using WiFi tethering. In 2015 IEEE 10th conference on industrial electronics and applications (ICIEA) (pp. 966-971). IEEE.
- Ray, S. K., Pawlikowski, K., & Sirisena, H. (2009). A fast MAC-layer handover for an IEEE 802.16 e-based WMAN. In AccessNets: Third International Conference on Access Networks, AccessNets 2008, Las Vegas, NV, USA, October 15-17, 2008. Revised Papers 3 (pp. 102-117). Springer Berlin Heidelberg.
- Tamayo, J. , López, L.I.B. and Caraguay, Á.L.V. (2024) 'Detection of distributed denial of service attacks carried out by botnets in Software-Defined networks,' arXiv (Cornell University) [Preprint]. [CrossRef]
- Touré, A.; et al. (2024) 'A framework for detecting zero-day exploits in network flows,' Computer Networks, p. 11 0476. [CrossRef]
- Wan, M.; et al. (2012) 'Locator/Identifier Separation: Comparison and analysis on the mitigation of worm propagation,' the International Journal of Computational Intelligence Systems/International Journal of Computational Intelligence Systems, 5(5), p. 868. [CrossRef]
- Wang, Y.; et al. (2014) 'Modeling the Propagation of worms in networks: A survey,' IEEE Communications Surveys and Tutorials/IEEE Communications Surveys and Tutorials, 16(2), pp. 942–960. [CrossRef]
- Wen, B.O.T.; et al. (2023) 'Detecting cyber threats with a Graph-Based NIDPS,' in Advances in logistics, operations, and management science book series, pp. 36–74. [CrossRef]
- www.ibm.com. (n.d.). What is a Zero-Day Exploit? | IBM. [online] Available at: https://www.ibm.com/topics/zero-day#:~:text=A%20zero%2Dday%20exploit%20is.
- Xu, G. and Meng, L. (2023) 'A novel algorithm for identifying influential nodes in complex networks based on local propagation probability model,' Chaos, Solitons & Fractals/Chaos, Solitons and Fractals, 168, p. 113155. [CrossRef]
- Zerdoumi, S., Hashem, I.A.T. & Jhanjhi, N.Z. A new spatial spherical pattern model into interactive cartography pattern: multi-dimensional data via geostrategic cluster. Multimed Tools Appl 81, 22903–22952 (2022). [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





