Submitted:
11 August 2024
Posted:
12 August 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- Provide a comparative study of the pre-quantum and post-quantum IoT security architectures.
- Analyze the Challenges and Future Directions of Post – quantum cryptograph on IoT.
2. Overview of the Technology Principles
2.1. Cryptographic Fundamental
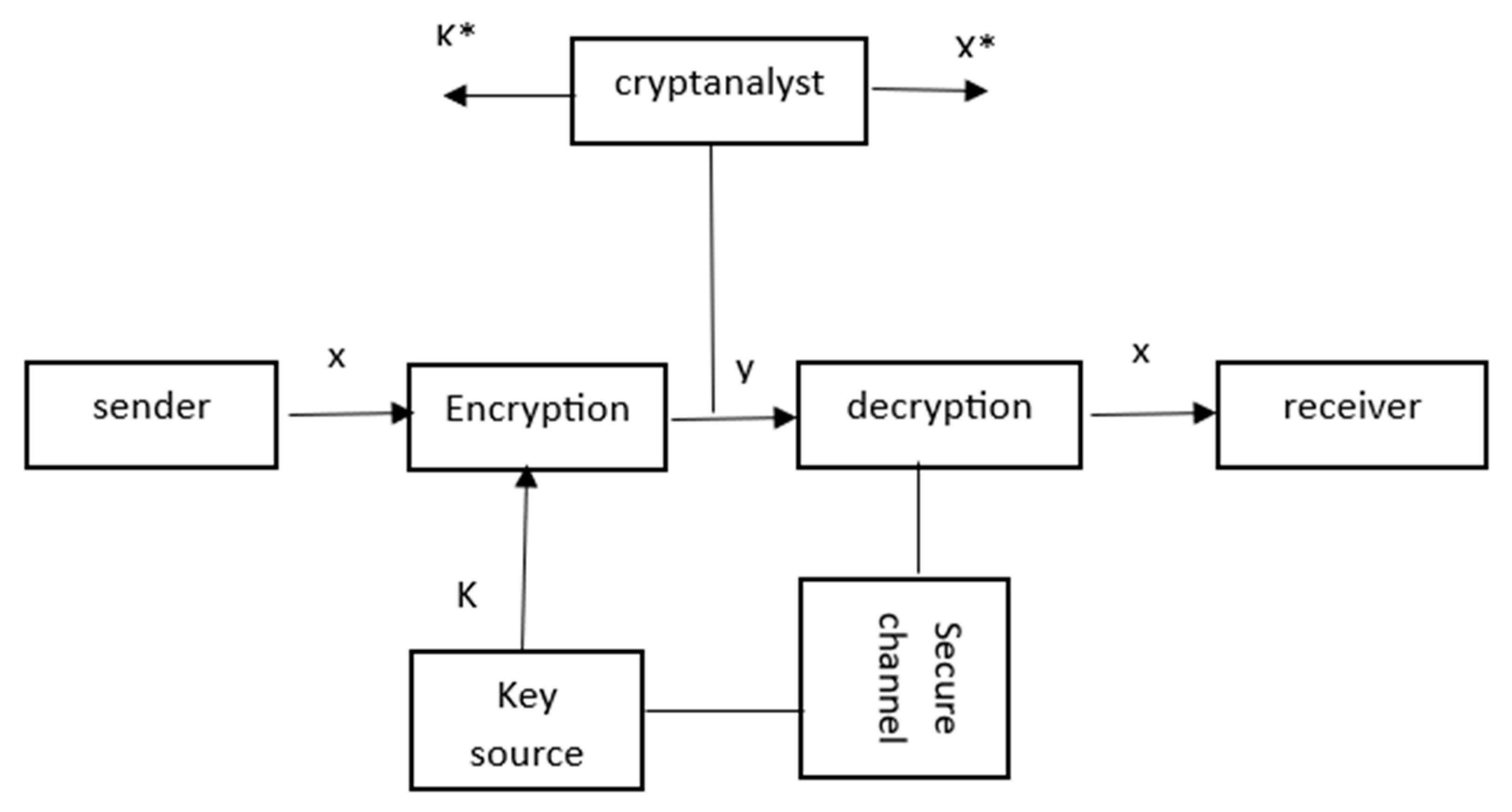
2.2. Pre – Postquantum Cryptographic Methods
- Integer Factorization: RSA relied on mathematical calculation. It relied on the difficulty of factoring large composite numbers into their prime factors. But due to the advancements in factorization algorithms, such as the General Number Field Sieve (GNFS), have reduced the security of RSA (May, A. (2003)). The emergence of quantum computers with the powerful process which contained algorithm which known by with Shor's algorithm broke RSA, as it could efficiently factor large numbers.
- Low Key Generation: all the methods used public key which can be generated to different key. If the random number generator used to generate RSA keys is flawed or the entropy source is weak, it can lead to the generation of weak keys that are susceptible to attacks like brute force or factorization (May, A. (2003)).
- Side-Channel Attacks: RSA implementations can be vulnerable to side-channel attacks, such as timing attacks, power analysis (May, A. (2003)). These attacks exploit information leaked during the execution of the algorithm to recover the private key.
- Elliptic Curve Discrete Logarithm Problem (ECDLP): ECC relied on the hardness of solving the ECDLP, which involves finding the scalar value 'd' given a point on an elliptic curve and the result of multiplying that point by 'd'. If a sufficiently powerful quantum computer is developed, it could potentially solve the ECDLP and break ECC-based cryptographic systems (Rahnama, B., Sari, A., & Ghafour, M. Y. (2016)).
- Choice of Curve Parameters: ECC required careful selection of curve parameters. If the parameters are poorly chosen or generated with insufficient randomness, it can weaken the security of ECC and make it vulnerable to attacks (Rahnama, B., Sari, A., & Ghafour, M. Y. (2016)).
- Implementation Flaws: Vulnerabilities in the implementation of ECC algorithms or protocols can lead to security flaws (Gabsi, S., Beroulle, V., Kieffer, Y., Dao, H. M., Kortli, Y., & Hamdi, B. (2021)). These vulnerabilities can be exploited by attackers to recover private keys or launch attacks, such as invalid curve attacks or point compression attacks.
2.3. Post – Quantum Cryptography Fundamental:
- Quantum Key Distribution (QKD): QKD is a quantum cryptographic protocol that enables two parties, often referred to as Alice and Bob, to exchange a shared secret key over an insecure communication channel, while detecting any potential eavesdropping attempts (Yavuz, A. A., Nouma, S. E., Hoang, T., Earl, D., & Packard, S. (2022, December). Examples of QKD protocols include BB84 (Bennett and Brassard 1984) and E91 (Ekert 1991).
- New Hope: New Hope is a post-quantum key exchange algorithm based on lattice-based cryptography. It is designed to provide security against both classical and quantum adversaries. New Hope is considered a candidate for use in Transport Layer Security (TLS) to secure internet communications Yavuz, A. A., Earl, D., Packard, S., & Nouma, S. E. (2022, June)
- ●
- Code-based Cryptography:
- ●
- Lattice-based Cryptography:
- ●
- Hash-based Cryptography:
- ●
- Multivariate Polynomial-based Cryptography:
2.4. Post – Quantum Cryptography Challenges:
- Signature Size and Efficiency: Hash-based signatures typically have larger signature sizes compared to other signature schemes (Srivastava, V., Baksi, A., & Debnath, S. K. (2023).). This can result in increased bandwidth and storage requirements, making them less practical in some scenarios.
- Collision Resistance: Hash functions used in hash-based signatures must be collision-resistant to prevent attackers from finding two different inputs that produce the same hash value (Srivastava, V., Baksi, A., & Debnath, S. K. (2023).).The security of hash-based signatures depends on the strength of the underlying hash function.
- Post-Quantum Security: As quantum computers advance, many traditional cryptographic schemes, including hash-based signatures, are at risk of being broken. The development of post-quantum secure hash-based signature schemes is an active area of research to address these concerns (Kichna, A., & Farchane, A. 2023).
- Key Size and Signature Size: it requires larger key and signature sizes compared to other cryptographic algorithms. This can have implications for storage, transmission, and computational efficiency (Dey, J., & Dutta, R. 2023). Progress in Multivariate Cryptography:).
- Key Generation and Distribution: generating and distributing keys in multivariate cryptography can be computationally expensive and time-consuming, particularly for large systems (Dey, J., & Dutta, R. 2023).
- Security margins: it relies on the difficulty of solving large systems of polynomial equations. Ensuring an appropriate security margin against attacks is challenging, as advancements in algebraic and computational techniques could reduce the security level of these schemes.
2.5. Post – Quantum Cryptography Future Directions:
- Efficient Implementations: Future research should focus on developing efficient implementations of code-based cryptography specifically tailored for IoT devices, considering their resource limitations (Akter, M. S. (2023).
- Lightweight Code-Based Schemes: Exploring lightweight code-based cryptographic schemes that offer a good balance between security and computational efficiency would be beneficial for IoT applications.
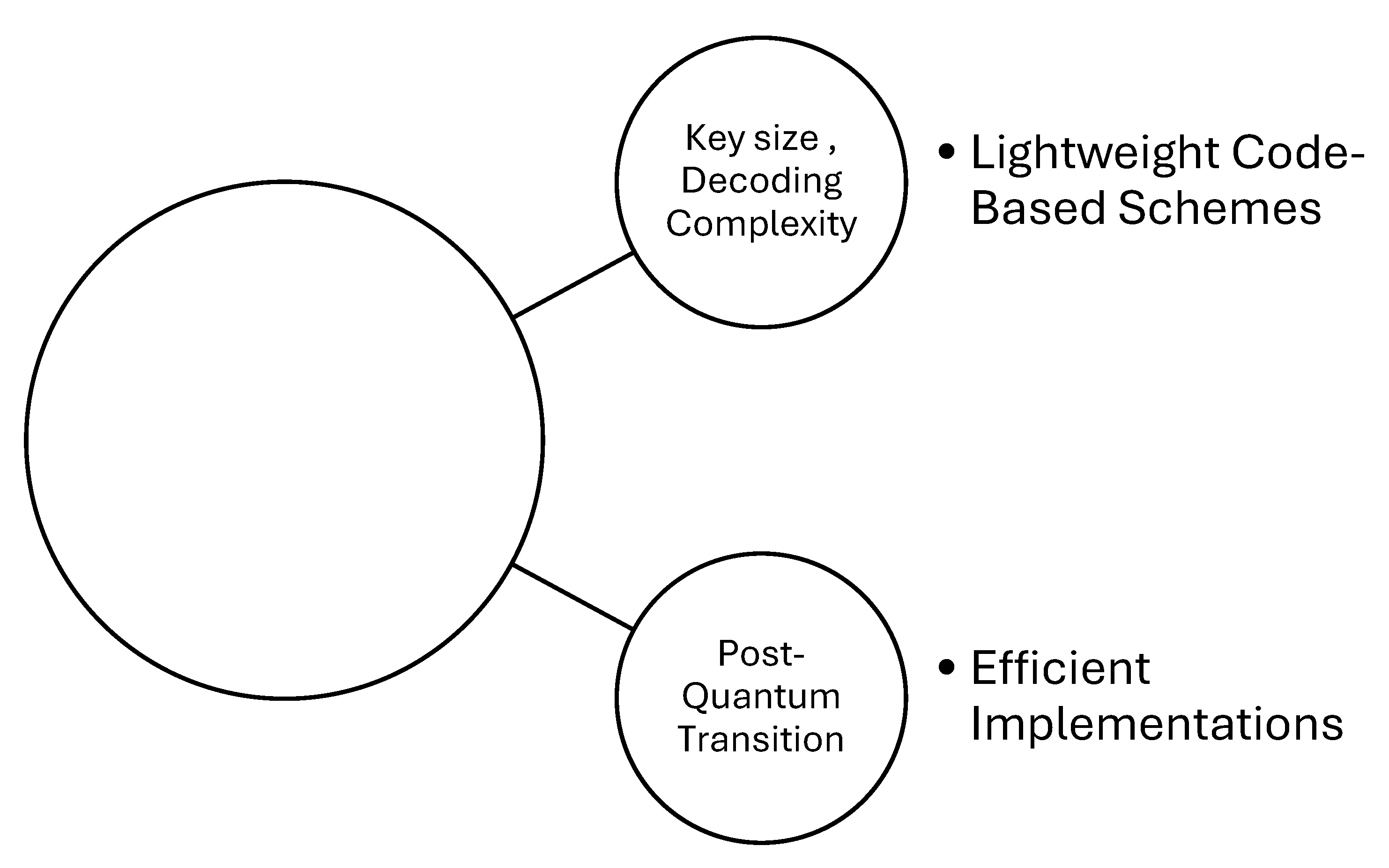
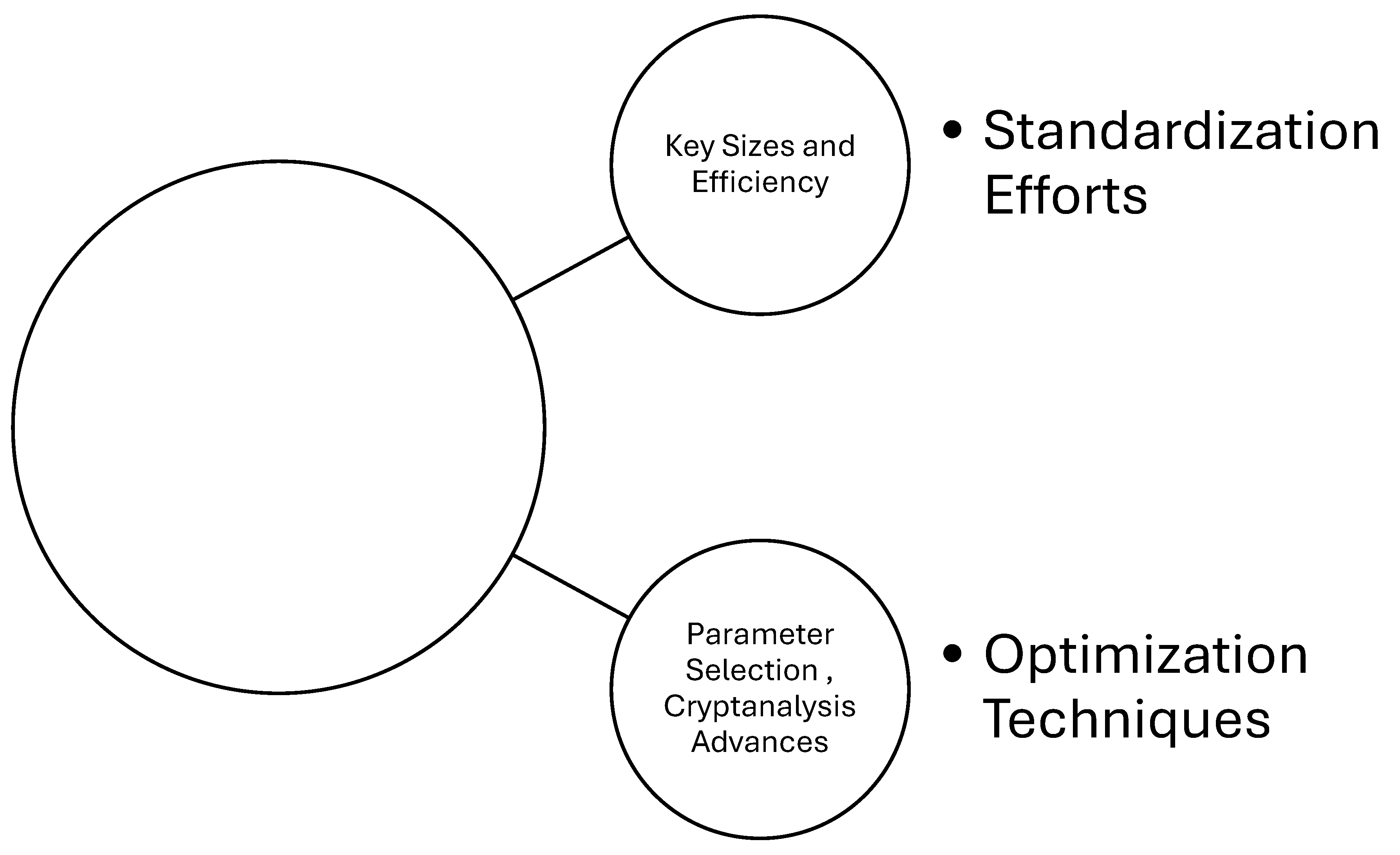
- Optimization Techniques: Research should focus on developing optimization techniques to reduce the computational and memory requirements of lattice-based cryptography, making it more feasible for IoT devices (Aikata, A., Basso, A., Cassiers, G., Mert, A. C., & Roy, S. S. (2023).
- Standardization Efforts: Collaborative efforts towards standardization and the development of efficient lattice-based cryptographic algorithms suitable for IoT environments are needed to facilitate adoption.
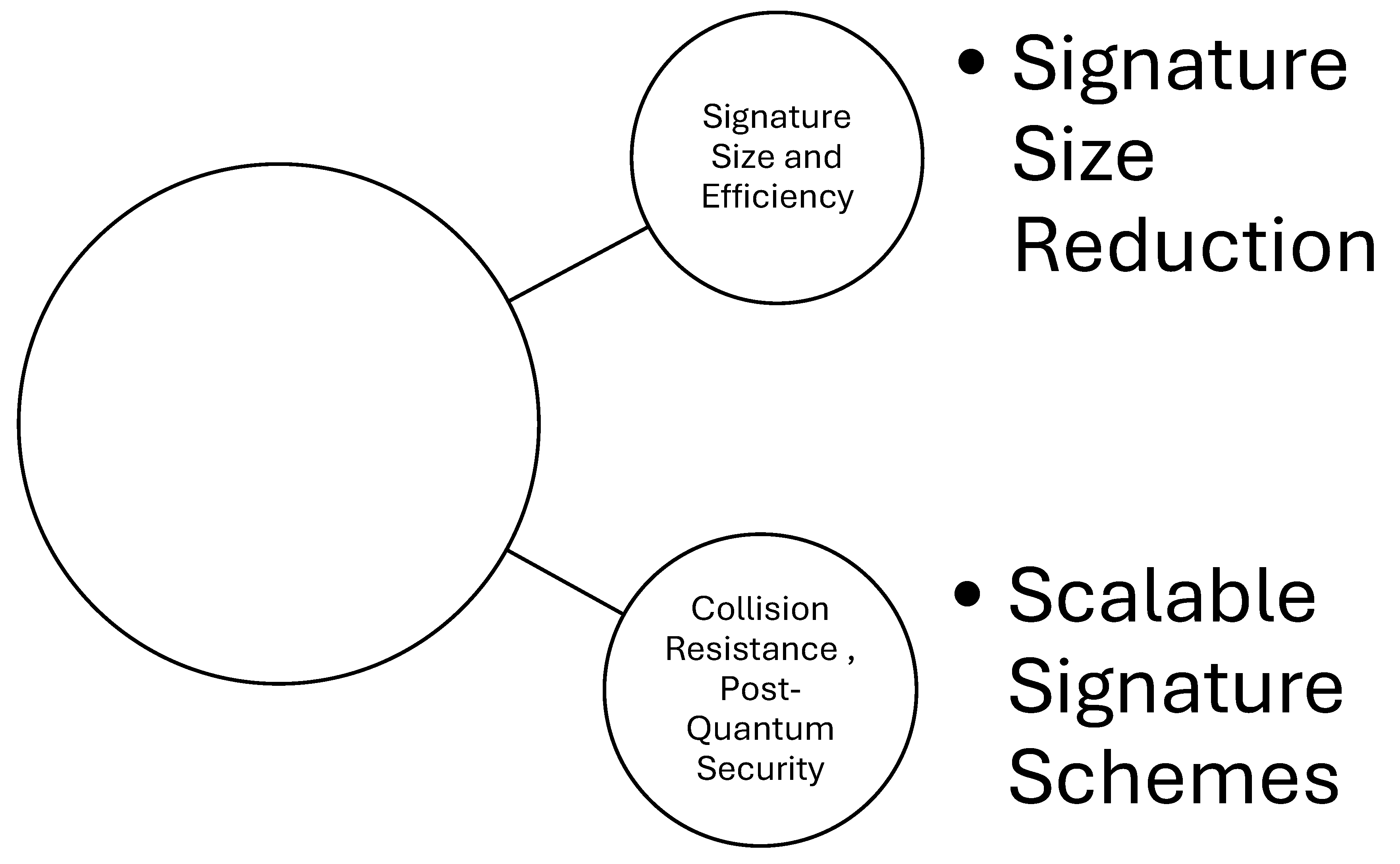
- Signature Size Reduction: Research efforts should focus on developing techniques to reduce the signature size of hash-based schemes without compromising their security (Kichna, A., & Farchane, A. (2023, May).
- Scalable Signature Schemes: Exploring scalable hash-based signature schemes that can support many signatures with a given key pair would be beneficial for IoT deployments (Akter, M. S. 2023).
- Hybrid Schemes: Hybrid cryptosystems, which combine multiple cryptographic techniques, are often used to leverage the strengths of different algorithms. Researchers may explore hybrid approaches that integrate MPBC with other post-quantum or traditional cryptographic primitives.
- Implementation and Standardization: If MPBC becomes widely adopted, there will be a need for standardized implementations and libraries to ensure interoperability and ease of integration into various software systems and devices(Dey, J., & Dutta, R. (2023). Progress in Multivariate Cryptography:)
- Formal Verification: With the increasing complexity of cryptographic algorithms, formal verification techniques may be employed to rigorously prove the correctness and security properties of MPBC schemes.
Conclusions
References
- Aguilar-Melchor, C., & Fúster-Sabater, A. (2017). Resource-constrained devices and code-based cryptography: The McEliece cryptosystem on 8-bit AVR CPUs. International Journal of Information Security, 16(3), 315-330.
- Ahn, J., Kwon, H. Y., Ahn, B., Park, K., Kim, T., Lee, M. K., ... & Chung, J. (2022). Toward quantum secured distributed energy resources: Adoption of post-quantum cryptography (pqc) and quantum key distribution (qkd). Energies, 15(3), 714. . [CrossRef]
- Aikata, A., Basso, A., Cassiers, G., Mert, A. C., & Roy, S. S. (2023). Kavach: Lightweight masking techniques for polynomial arithmetic in lattice-based cryptography. IACR Transactions on Cryptographic Hardware and Embedded Systems, 366-390.. [CrossRef]
- Akter, M. S. (2023). Quantum Cryptography for Enhanced Network Security: A Comprehensive Survey of Research, Developments, and Future Directions. arXiv preprint arXiv:2306.09248. . [CrossRef]
- Alagic, G., Alperin-Sheriff, J., Apon, D., Cooper, D., Dang, Q., Kelsey, J., ... & Smith-Tone, D. (2020). Status report on the second round of the NIST post-quantum cryptography standardization process. US Department of Commerce, NIST, 2..
- Beullens, W.; D’Anvers, J.; Hülsing, A.; Lange, T.; Panny, L.; de S. Guilhem, C.; Smart, N.P. Post-Quantum Cryptography: Current State and Quantum Mitigation; Technical Report; European Union Agency for Cybersecurity: Athens, Greece, 2021. 21.
- Buchmann, J., Dahmen, E., Göpfert, F., & Leander, G. (2017). Practical signatures for resource-constrained devices—Hash-based signatures, lattice-based signatures, and their integration. In International Conference on Cryptology and Network Security (pp. 126-145). Springer.
- Cayrel, P.L.; ElYousfi, M.; Hoffmann, G.; Meziani, M.; Niebuhr, R. Recent Progress in Code-Based Cryptography. In International Conference on Information Security and Assurance; Springer: Berlin/Heidelberg, Germany, 2014; pp. 21–32. 26.
- Chen, M.; Ding, J.; Kannwischer, M.; Patarin, J.; Petzoldt, A.; Schmidt, D.; Yang, B. Rainbow Signature. Available online: https://www.pqcrainbow.org/ (accessed on 27 August 2020). https://www-polsys.lip6.fr/Links/NIST/GeMSS.html (accessed on 8 December 2020).
- Chi, D.P.; Choi, J.W.; Kim, J.S.; Kim, T. Lattice Based Cryptography for Beginners. Available online: https://eprint.iacr.org/2015 /938 (accessed on 20 November 2020).
- Dey, J., & Dutta, R. (2023). Progress in Multivariate Cryptography: Systematic Review, Challenges, and Research Directions. ACM Computing Surveys, 55(12), 1-34. . [CrossRef]
- Gabsi, S., Beroulle, V., Kieffer, Y., Dao, H. M., Kortli, Y., & Hamdi, B. (2021). Survey: Vulnerability analysis of low-cost ECC-based RFID protocols against wireless and side-channel attacks. Sensors, 21(17), 5824. . [CrossRef]
- Kichna, A., & Farchane, A. (2023, May). Secure and Efficient Code-Based Cryptography for Multi-Party Computation and Digital Signatures. In Computer Sciences & Mathematics Forum (Vol. 6, No. 1, p. 1). MDPI. . [CrossRef]
- Kuwakado, H.; Morii, M. Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 12–18 June 2010; pp. 2682–2685. 5. [CrossRef]
- Lei, D., He, D., Peng, C., Luo, M., Liu, Z., & Huang, X. (2023). Faster Implementation of Ideal Lattice-based Cryptography Using AVX512. ACM Transactions on Embedded Computing Systems. . [CrossRef]
- May, A. (2003). New RSA vulnerabilities using lattice reduction methods (Doctoral dissertation, University of Paderborn)..
- Rahman, M., & Jahankhani, H. (2021). Security vulnerabilities in existing security mechanisms for iomt and potential solutions for mitigating cyber-attacks. Information security technologies for controlling pandemics, 307-334. . [CrossRef]
- Rahnama, B., Sari, A., & Ghafour, M. Y. (2016). Countering RSA vulnerabilities and its replacement by ECC: elliptic curve cryptographic scheme for key generation. In Network security attacks and countermeasures (pp. 270-312). IGI Global..
- Sendrier, N. (2017). Code-based cryptography: State of the art and perspectives. IEEE Security & Privacy, 15(4), 44-50.. [CrossRef]
- Sendrier, N. Code-Based Cryptography: State of the Art and Perspectives. IEEE Secur. Priv. 2017, 15, 44–50. 27. Ding, J.; Petzoldt, A. Current state of multivariate cryptography. IEEE Secur. Priv. 2017, 15, 28–36. 28.
- Srivastava, V., Baksi, A., & Debnath, S. K. (2023). An Overview of Hash Based Signatures. Cryptology ePrint Archive..
- Umana, V.G. Post Quantum Cryptography. Ph.D. Thesis, Technical University of Denmark, Lyngby, Denmark, 2011. 20.
- Yavuz, A. A., Earl, D., Packard, S., & Nouma, S. E. (2022, June). Hybrid low-cost quantum-safe key distribution. In Quantum 2.0 (pp. QTu4C-5). Optica Publishing Group..
- Yavuz, A. A., Nouma, S. E., Hoang, T., Earl, D., & Packard, S. (2022, December). Distributed Cyber-infrastructures and Artificial Intelligence in Hybrid Post-Quantum Era. In 2022 IEEE 4th International Conference on Trust, Privacy and Security in Intelligent Systems, and Applications (TPS-ISA) (pp. 29-38). IEEE.. [CrossRef]
| Code _ based cryptography | Lattice-Based Cryptography | Multivariate Cryptography | Hash-Based Signatures | |
|---|---|---|---|---|
| Differences | ||||
| Underlying Mathematical Foundations | It relies on error-correcting codes | It relies on lattice problems | It relies on multivariate polynomial equations | They rely on cryptographic hash functions |
| Security Assumptions | It is based on different assumptions. It assumes the hardness of decoding error-correcting | It assumes the hardness of lattice problems | It assumes the hardness of solving multivariate polynomial equations | They rely on the properties of cryptographic hash functions. |
| Post-Quantum Security | It is designed to resist attacks by quantum computers. | It is designed to resist attacks by quantum computers. | is not considered a post-quantum scheme, as it is vulnerable to certain algebraic attacks. | It is designed to resist attacks by quantum computers. |
| Similarities | ||||
| Public-Key Cryptography | They are a form of public key. They involve the use of public and private key pairs for encryption and decryption, digital signatures, and other cryptographic operations | |||
| Post-Quantum Candidates | They are alternatives to traditional public-key cryptosystems that may be vulnerable to attacks by quantum computers | |||
| Resistance to Quantum Attacks | They are designed to provide security even in the presence of quantum computers. Their aims to resist attacks by leveraging mathematical problems that are believed to be hard even for quantum computers. | |||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





