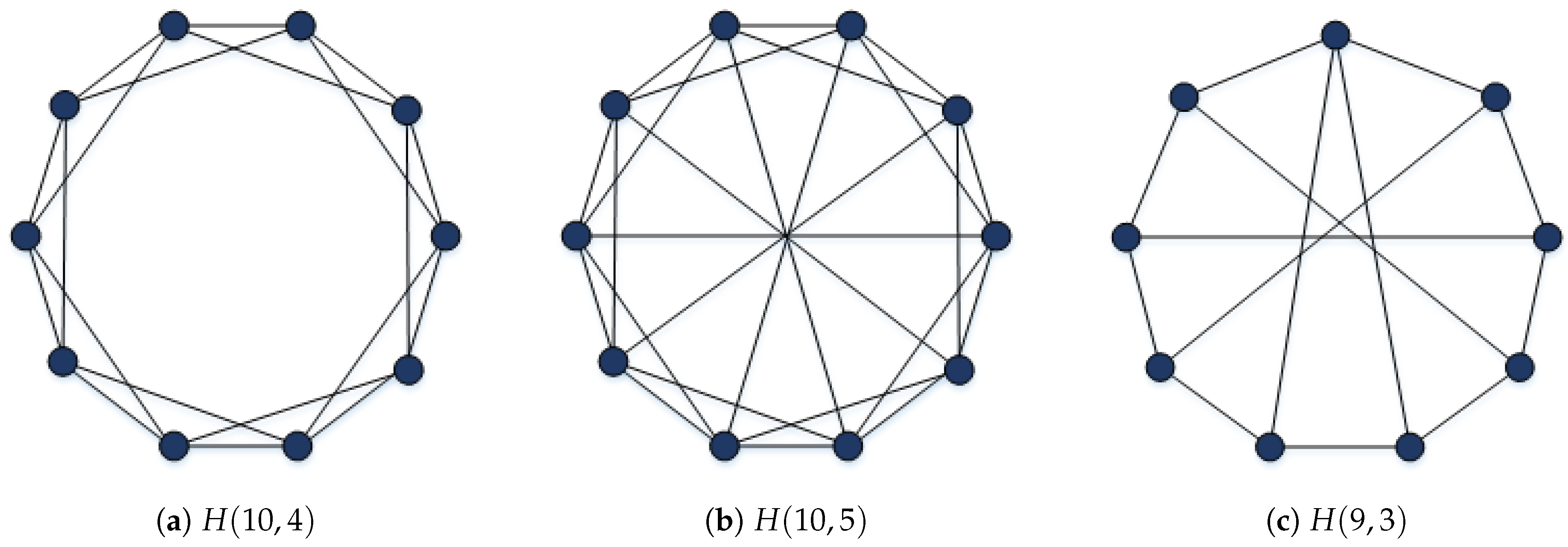
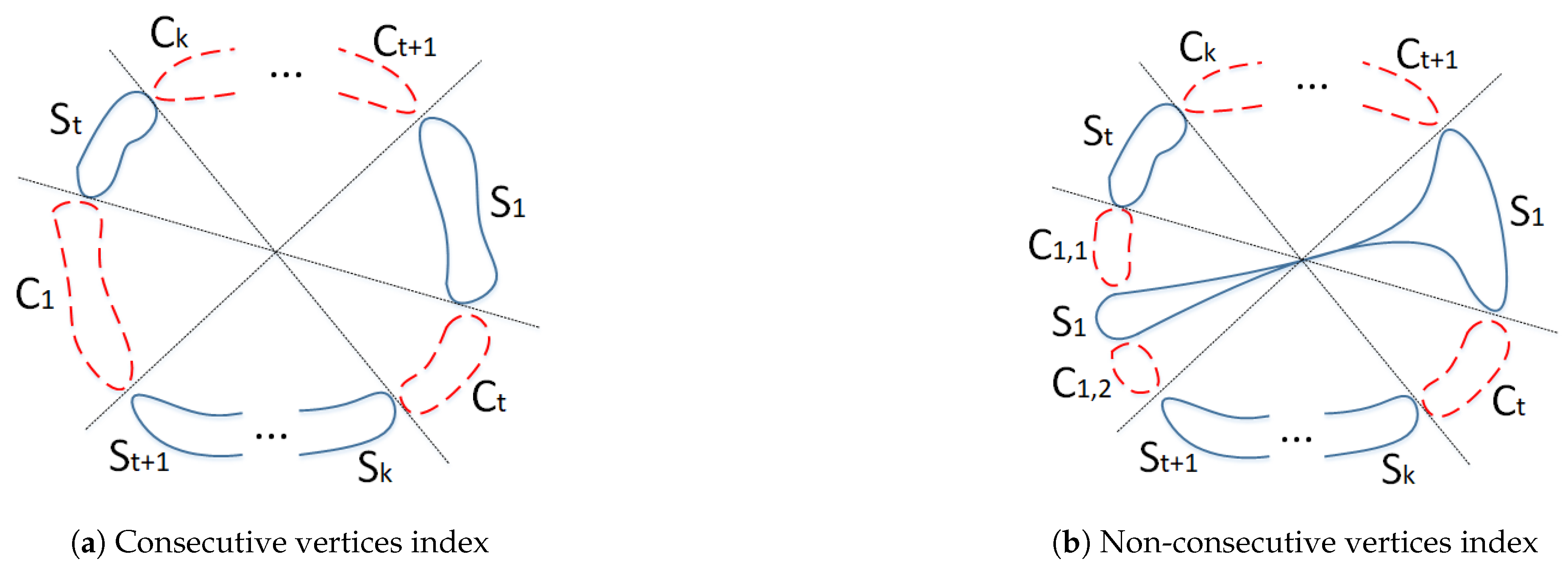In this section, we will focus on different methods for evaluating the vulnerability of Harary graphs using the tightness parameter. Due to the varying structures of the three Harary graph types, distinct approaches will be required to calculate the tightness parameter values.
The lemmas, corollaries, and methodologies presented in this section may have broader applications beyond the specific context of Harary graphs. They could potentially be useful in solving other graph-theoretic problems and expanding the understanding of the tightness metric and its relationships with other graph parameters.
Based on Lemma 1 and Theorem 1 the Corollary 1 can be derived.
The calculation of more accurate bounds can also be achieved by using the relationship between tightness and the rest of the graph parameters. For example, the connectivity of Harary graphs is equal to m. This problem shows that in order to divide the graph into two parts, we need to remove at least m vertices. Therefore, to find the upper limit, it is possible to establish a relationship between tightness and connectivity. Theorem 2 shows the relationship between tightness and connectivity.
In this section, the upper and lower bounds for tightness of Harary graphs were calculated approximately. In the following, we will take a closer look at tightness values for these types of graphs.
2.1. Tightness of Harary Graphs Type (a)
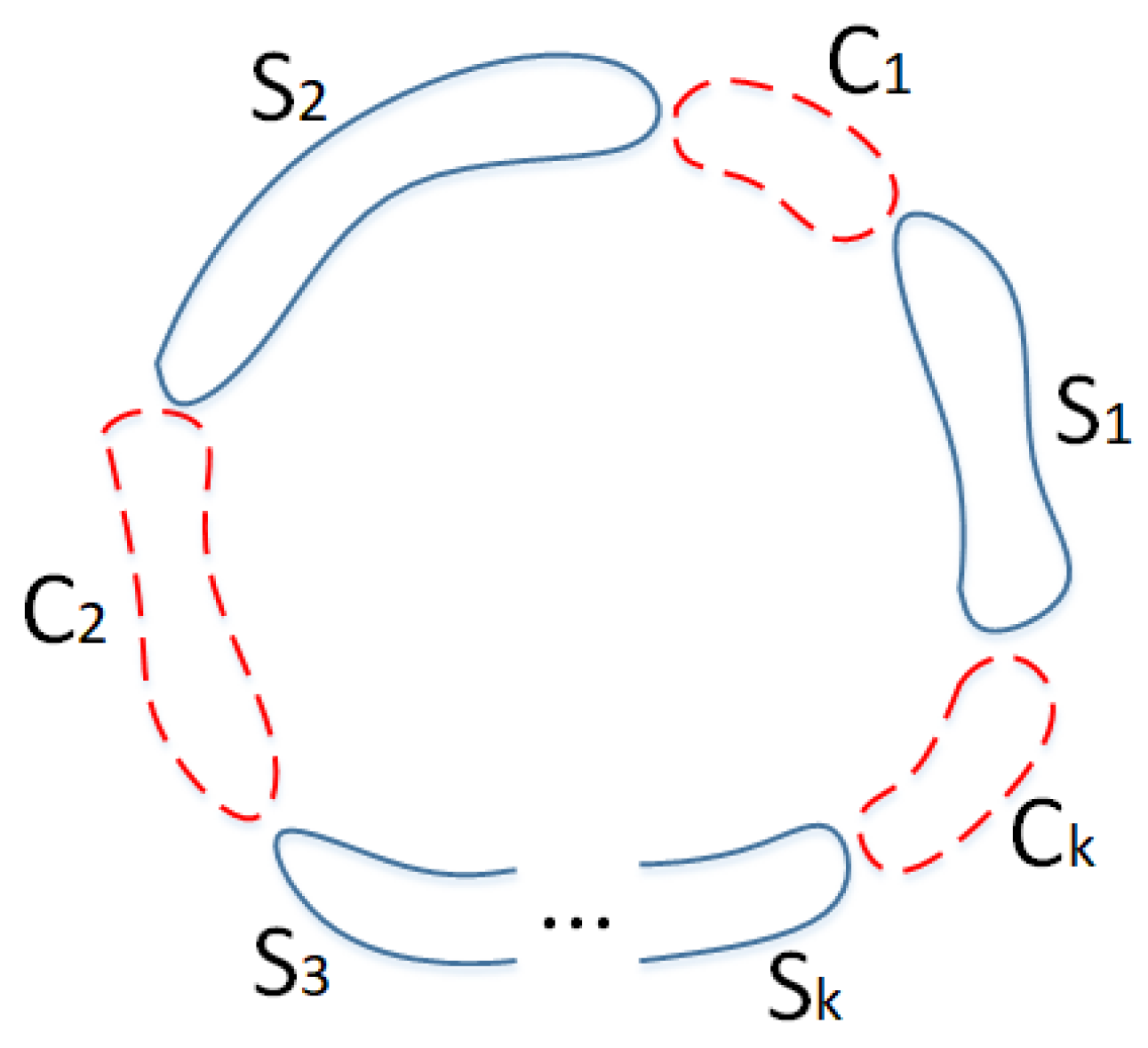
In our analysis of Harary graphs of type (a), we consider the scenario where certain sets of vertices, denoted as , are removed in order to calculate the value of the tightness parameter . Correspondingly, other sets of vertices, denoted as , remain in the graph as connected components. For the sake of simplicity, we assume that the indices of the vertices within each deleted set and each remaining component are consecutive. The validity of this approach will be established through a series of rigorous lemmas and corollaries presented in the subsequent sections. Consequently, we can define a set S comprising all the vertices belonging to the remaining components , as well as a cut set C encompassing all the deleted vertex sets . With this vertex cut in place, we can further partition the paths removed from the Harary graph of type (a) into three distinct categories: , , and . The value represents the deleted paths connecting vertices within the cut set C, denotes the deleted paths between vertices in the cut set C and the vertices in the remaining components S, and corresponds to the deleted paths between vertices within the components S.
Moreover, for the removal of a set of vertices in the Harary graphs of type (a) to successfully separate two components, the cardinality of each cut set must be greater than or equal to , where m is the desired connectivity for Harary graph.
Equations (
14) through (
17) provide the mathematical formulations of these variables, where
,
,
,
, and
k is the number of remaining components.
To determine the tightness of Harary graphs of type (a), we will seek to minimize the objective function denoted as
. This objective function can be expressed in terms of the previously defined sets
C and
S, as shown in Equation (
18).
To determine the minimum value of the function , we must first establish several foundational lemmas. Lemma 2 will demonstrate that the size of the components must be sufficiently small in order to minimize the values of . The proof of this key lemma will illuminate the underlying structure and properties of the function , providing crucial insights that will guide us towards the global minimum.
Lemma 2. If, after identifying the vertex cut set C in Harary graphs of type (a), we obtain , then the value of is not at its minimum if the size of the largest component is greater than .
Proof. Suppose that a vertex v is removed from a component . The number of new deleted paths will be at least , where . If v is a cut vertex, then the number of new deleted paths will be greater than . Therefore, to maximize the number of deleted paths, it is optimal to select this vertex from the largest component. Consequently, the ratio of the number of deleted vertices to the number of deleted paths will be equal to , where is the largest component of and .
Given that
, and denoting
and
, using relations (
19) ,we can conclude that the value of objective function
is not at its minimum.
□
Therefore, by repeatedly removing vertices from the largest component of Harary graphs type (a), when the size of the component exceeds the desired limit, we can reduce the value of the objective function.
This repetition may causes large components to be divided into smaller components. The vertices removed from this component, if they create a cut, in addition to the removed paths between C vertices, they also destroy the path between some vertices. This will lead to a decrease in the value of . Although Lemma 2 does not give us a general view of the optimal tightness value, it can be used for a superficial examination of the results obtained from the calculations.
According to Lemma 2, after reducing the objective function , if there is a cut vertex within any component , the cut vertex can be replaced with its right or left vertex and this can be done until the index of the cut vertices as well as the index of the components became consecutive. Thus, the following corollary can be derived:
Corollary 3. In Harary graphs of type (a), the indices of the vertices of each component and each cut set can be considered consecutive to find the minimum value of .
Figure 2 shows a desirable partition for Harary graphs type (a) based on mentioned lemmas and corollaries.
Considering the fixed number of cutting vertices, to minimize the objective function , must be maximized. To maximize , the size difference of the generated components should be minimized. In other words, the size difference of all created components must be at most 1. This issue has been studied under Lemma 3.
Lemma 3. With a constant number of cutting vertices in , the minimized value of occurs when , where k is the number of remaining components after the cut, and and are the sizes of the i-th and j-th components, respectively.
Proof. To minimize the objective function , must be maximized. Suppose there are two components and with sizes and , respectively, where . Without loss of generality, suppose that or .
By removing a vertex from the larger component and adding a vertex to the smaller component, we actually shift the vertices between them (cut sets and components) by one vertex towards the larger component. With this, the value of
changes in the form of Equation (
20), which indicates the increase of this value.
By repeating the operation of removing a vertex from the largest component and adding it to the smallest one, the upward trend of will continue. This operation can be done until the size of the components are almost balanced, or in other words, . This ensures the minimization of the size difference between the components, which in turn maximizes and minimizes the objective function . □
Using Lemma 3, and assuming continuous values for
c,
s, and
k, the Equation (
18) can be written as Equation (
21).
Given the fact that
, the Equation (
21) can be rewritten in terms of
c as Equation (
22).
By differentiating the continuous function in Equation (
22) with respect to the variable
c (
), the extremum value is obtained as
. However, these obtained values are not acceptable while
. Therefore, the continuous function in Equation (
22) will be either ascending or descending.
Assigning 0 and
n to the variable
c, the obtained values are 0 and
, respectively. Thus, to minimize the value of the function in Equation (
22), the value of
c must be minimized. Additionally, the minimum value of
c is achieved when the cut occurs, i.e.,
. Furthermore, the minimum value of
makes the value of
k equal to 2. Therefore, the continuous function in Equation (
22) can be written as Equation (
23).
Although the calculations of the tightness value of Herary graphs type (a) have been done accurately and by mathematical relations, we can still use Lemma 2 to re-examine the results. The size of the largest component with this cut will be
, and
. Therefore, based on Lemma 2, there is no need to add a new vertex to the cut set.
Accordingly, to calculate the tightness of Harary graphs type (a), two components, as large as possible, with minimum different sizes have to be created after cutting. Therefore, based on the previous lemmas and corollaries, having
and
,
and
can be written as Equations (
24) and (
25) in the discrete space, respectively.
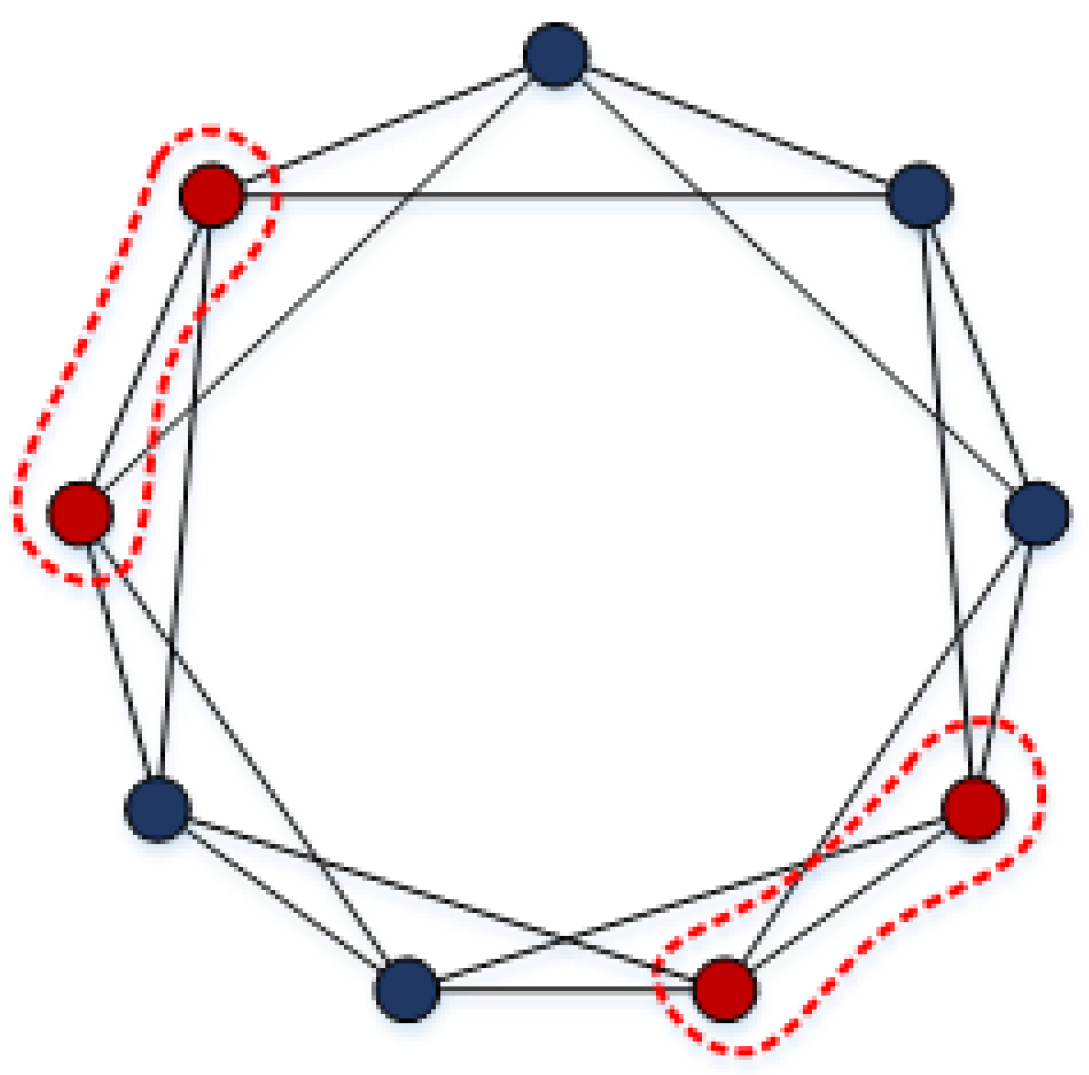
Figure 3 shows an optimal cut for calculating
.
2.2. Tightness of Harary Graphs Types (b) and (c)
Calculating the tightness value of Harary graphs type (a) required intricate mathematical relationships and theorems. In contrast, Harary graphs types (b) and (c) possess more complex structures, suggesting that determining their tightness values would be far more arduous. As illustrated in
Figure 4, obtaining an optimal vertex cut is exceptionally challenging for these two graph types, as each vertex is connected to its opposite counterpart. This cut can be executed in two ways: by either completely removing the opposite vertices, as shown in
Figure 4a, resulting in a consecutiveness vertices index for the component, or by partially removing them, as depicted in
Figure 4b, leading to a non-consecutiveness vertices index for the component. Both approaches increase the complexity of the problem significantly.
Therefore, in this section, we will endeavor to provide a suitable upper bound for the tightness value of Harary graphs types (b) and (c). Based on the calculated tightness for Harary graphs type (a), it can be concluded that this parameter does not increase the number of components in the graph.
Accordingly, to find a good upper bound for the tightness parameter in Harary graphs types (b) and (c), suppose we want to split the graph into two components. Therefore, separating one component from the graph makes the rest of the graph contain at least one other component. So, to calculate a good upper bound, we will focus on isolating a component from the graph.
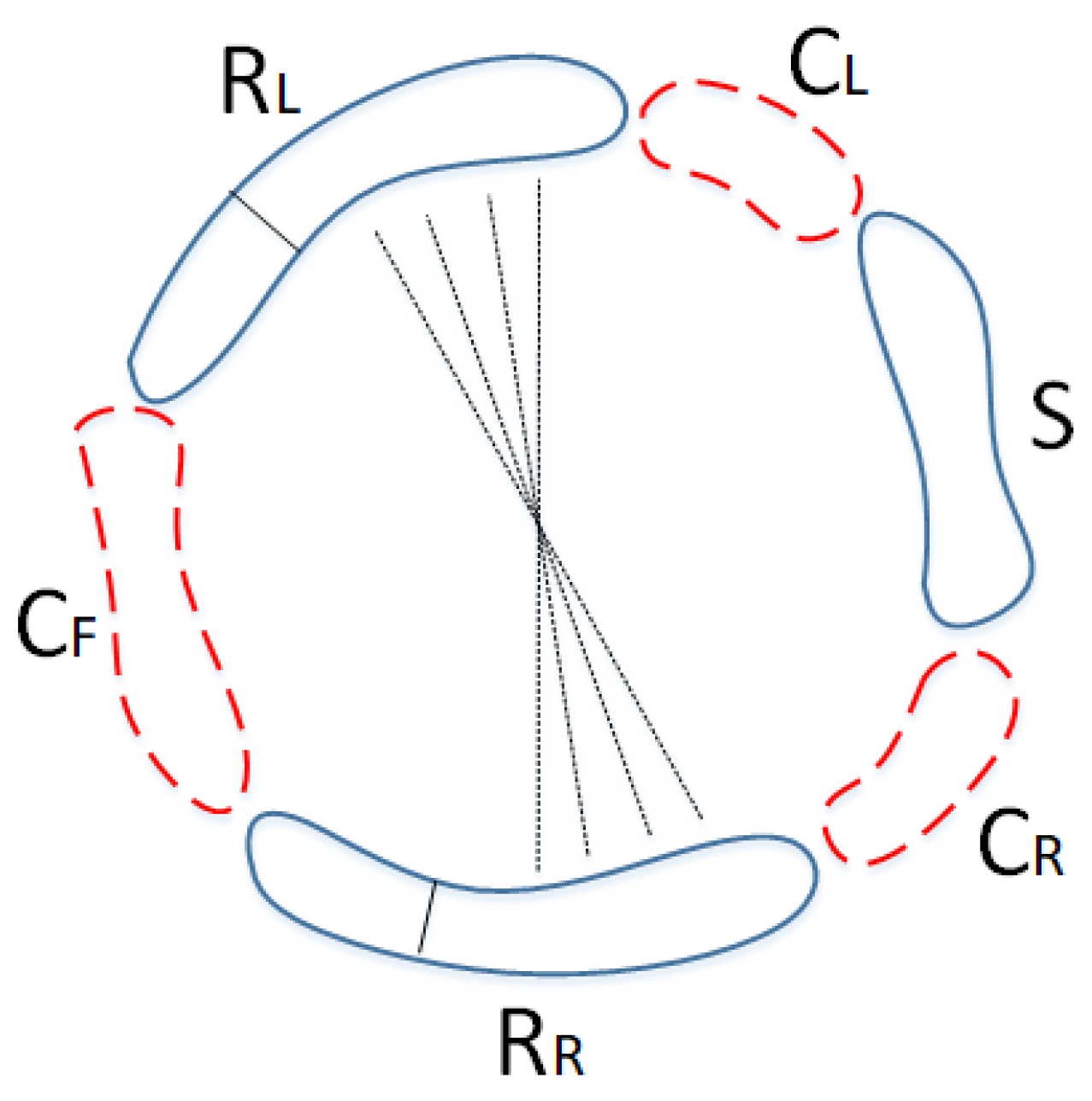
Figure 5 shows the general state of this separation, in which the set of vertices
S represents the desired component, while the sets of vertices
,
, and
are the cut vertices on the right, left, and opposite sides of the desired component, respectively.
By removing the cut vertices , , and , the removed paths are divided into three sections: , , and , where , S is the component, and R is the remaining vertices after cutting, or . In the continuation of the process of finding the upper bound for the tightness of Harary graphs types (b) and (c), we will assume that R are connected, or in other words, .
Suppose that
, then
, and to decrease the number of cut vertices (
) we can assume that
. Note that the value of
allows us to add a part of the cutting vertices of
to reduce the number of cutting vertices to the set of
S. This state is shown in
Figure 4.
In addition, to minimize the number of cutting vertices, the values of
and
must be equal to
. With these explanations, the values of
,
, and
can be written as Equations (
26), (
27), and (
28), respectively.
Therefore, the objective function can be expressed as Equation (
29).
The values of
n and
m in relation (
29) are constant. Therefore, it is possible to find the extremum point by differentiating the objective function
with respect to
s, if it exists. By this method, the extremum point will be as Equation (
30). Thus, an extremum point for
and an upper bound for
can be achieved using the rounded value of
and Equation (
29).
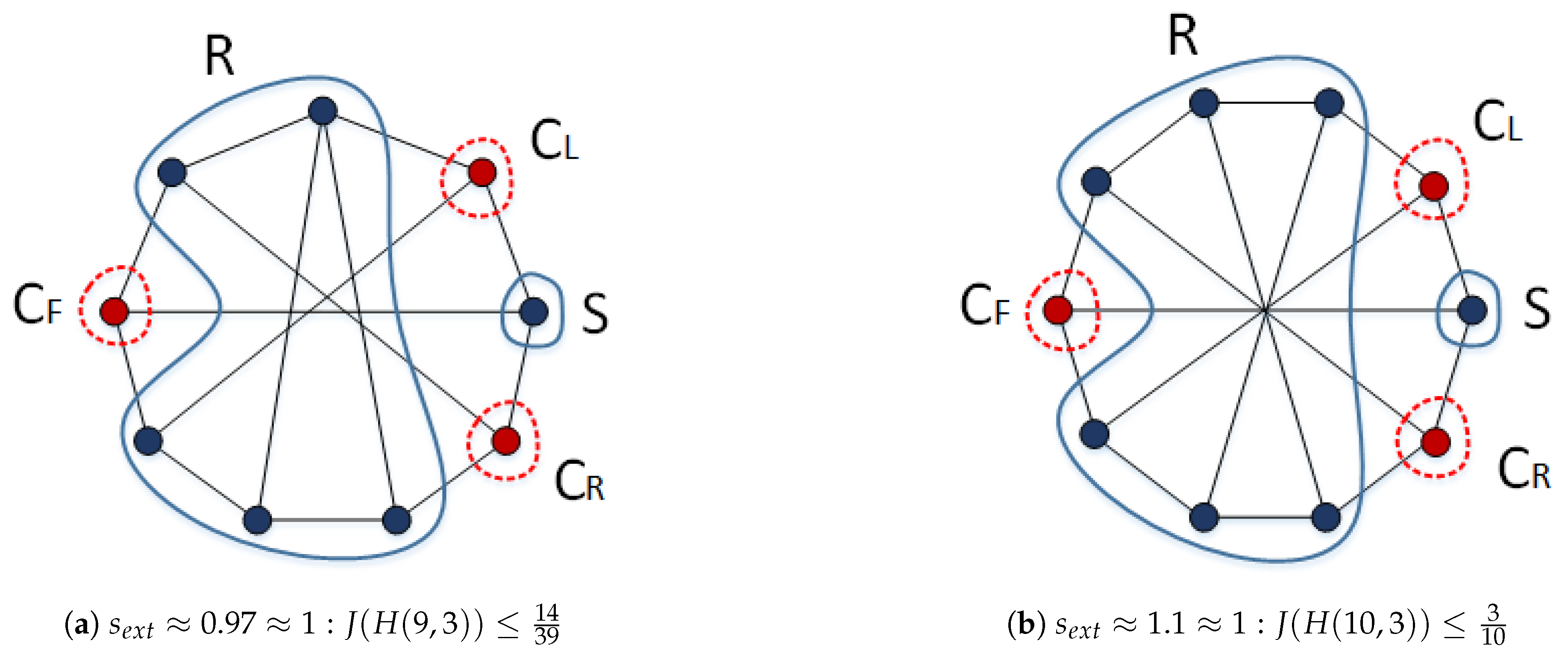
To find an upper bound of tightness for Harary graphs type (c), the results obtained for Harary graphs type (b) can be used because these results were calculated in continuous space. For this purpose, it is enough consider the condition
.
Figure 6 shows an example of the desired component
S and cutting vertices
for
and
.