Submitted:
20 August 2024
Posted:
21 August 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- What are the keywords and topics in the state-of-the-art counter-UAS research?
- What are the limitations and future research opportunities exposed in the state-of-the-art counter-UAS research?
2. Materials and Methods
2.1. Bibliometrics: Co-Word Analysis and Social Network Analysis
2.2. Scoping Review
- Objective (s)
- Category of counter-UAS technology
- Limitations and opportunities
2.3. Search Criteria
2.4. Study Selection
- Not English-written peer-reviewed journal articles (76 articles)
- Not relevant to counter-UAS/drone (99 articles)
| Journal | Number of Articles |
|---|---|
| Sensors | 27 |
| Drones | 18 |
| IEEE Access | 6 |
| Remote Sensing | 6 |
| Applied Sciences | 4 |
| Electronics | 4 |
| Journal of Physics: Conference Series | 4 |
| Information | 3 |
| Defence Science Journal, Human Factors and Mechanical Engineering for Defense and Safety, IEEE Control Systems Letters, IEEE Transactions on Aerospace and Electronic Systems, Journal of Guidance, Control, and Dynamics, Systems, Technology in Society, Wireless Communications & Mobile Computing (Online) | 2 in each journal |
| Aeronautical Journal, Aerospace, Applied Intelligence, Bulletin of “Carol I” National Defense University, Chinese Journal of Aeronautics Complexity, Computer Law & Security Review, Digital War, Discover Internet of Things, Energies, Frontiers in Signal Processing, Frontiers of Information Technology & Electronic Engineering, Geo-Spatial Information Science, IEEE Aerospace and Electronic Systems Magazine, IEEE Open Journal of The Communications Society, IEEE Robotics and Automation Letters, IEEE Sensors Journal, IEEE Transactions on Instrumentation and Measurement, IEEE Transactions on Mobile Computing, IEEE Transactions on Wireless Communications, IEEE-ASME Transactions on Mechatronics, IET Radar Sonar and Navigation, Internal Security, International Journal of Advanced Computer Science and Applications, International Journal of Aviation, Aeronautics and Aerospace, International Journal of Critical Infrastructure Protection, International Journal of Intelligent Enterprise, International Journal on Smart Sensing and Intelligent Systems, International Review of the Red Cross, Internet of Things, IOP Conference Series. Materials Science and Engineering, ISPRS International Journal of Geo-Information, Journal of Aerospace Information Systems, Journal of Electrical and Computer Engineering, Journal of Imaging, Journal of Intelligent & Robotic Systems, Journal of Strategic Security, Journal of Transportation Security, JP Journal of Heat and Mass Transfer, Mathematical Problems in Engineering, Microwave Journal, Mokslas: Lietuvos Ateitis, Neural Computing & Applications, News of the National Academy of Sciences of the Republic of Kazakhstan, Series of Geology and Technical Sciences, Operations Research Forum, Optics Express, PeerJ Computer Science, PLoS One, Robotica, SSRG International Journal of Electrical and Electronics Engineering, Sustainability, Symmetry, Systems Engineering, The Journal of Applied Business and Economics, The Visual Computer, World Electric Vehicle Journal | 1 in each journal |
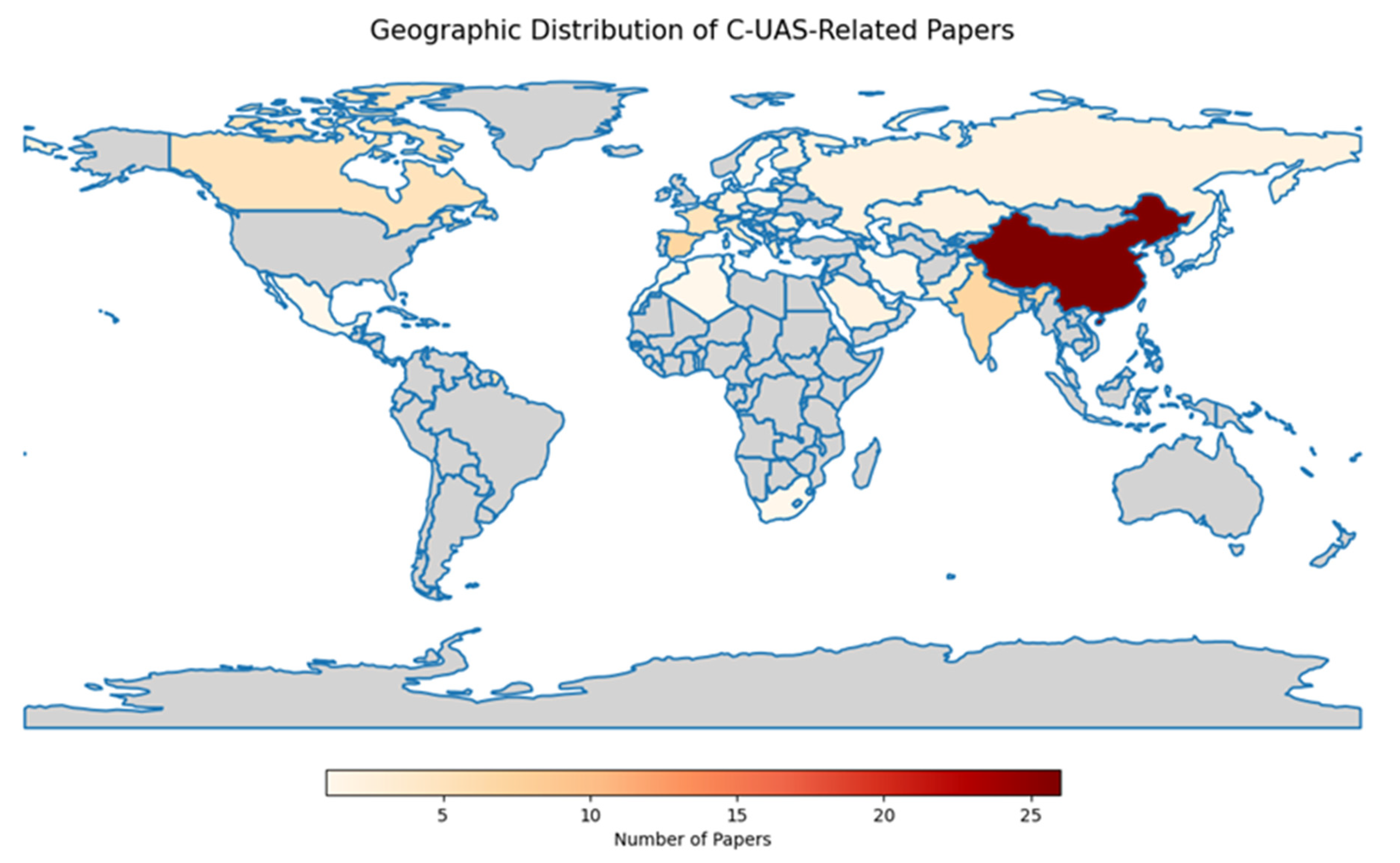
3. Co-Word Analysis and Social Network Analysis
3.1. Procedure of Analysis
3.1.1. Keyword Extraction
3.1.2. Keyword Standardization
3.2. Findings from Bibliometrics Analysis
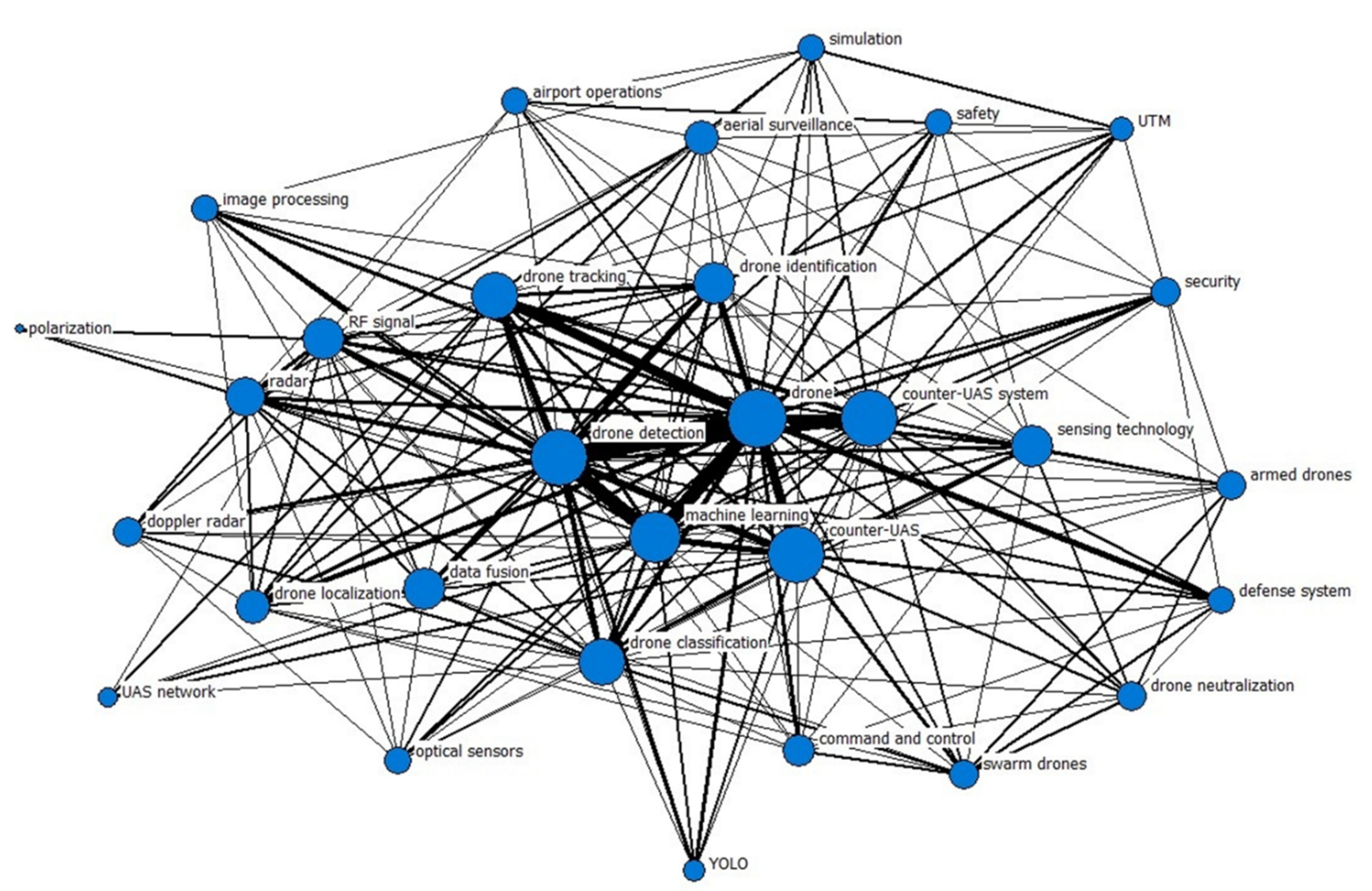
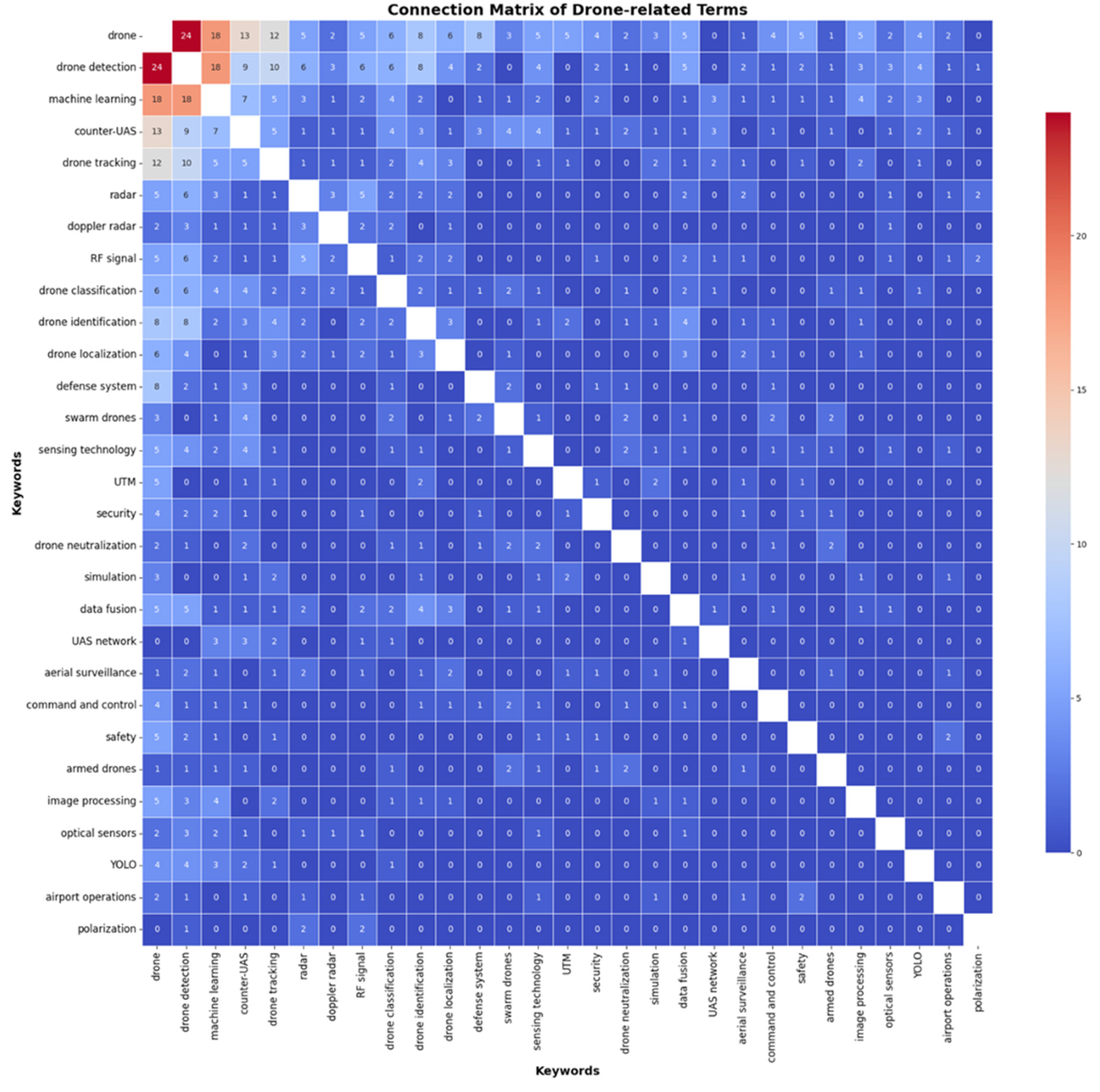
3.2.1. Drone Detection and Machine Learning: The Most Central Topics
3.2.2. Potential Research Opportunities from Central Topics and Structural Holes
- 4.
- Machine learning techniques were usually employed in drone detection studies. Given the advantages of machine learning techniques in various signal processing and analysis, machine learning integration is expected to be one of the mainstreams in counter-UAS studies, particularly those related to UAS detection, tracking, and classification.
- 5.
- Radar and radio signals were used more often for drone detection. Radar and radio frequency might be more promising and advantageous than other information, such as optical and acoustic information, especially in the case of long-distance detection with adverse background noise.
- 6.
- Drone tracking studies were usually associated with drone identification, localization, and classification functions. This type of study is critical as it yields critical information for the practical implementation of counter-UAS systems.
- 7.
- Drone classification studies were more associated with swarm drones and utilized radar, RF signals, and data fusion techniques. Drone classification provides critical information for counter-UAS systems to determine the correct mitigation strategy.
- Studies incorporating drone detection and swarm drone operations, UAS traffic management (UTM), and UAS network have not been observed but could be important.
- Machine learning or artificial intelligence lacks integrative studies supporting drone localization, neutralization, command and control for counter-UAS, and airport operation against UAS threats.
- Studies on swarm drones, command and control, drone neutralization, data fusion, and sensing technology did not closely interact with drone tracking. Integrative studies across subdomains, such as data fusion and sensing technology, might be promising to improve drone tracking capability.
- The literature on drone classification has not been observed in the areas of UTM, safety, security, command and control, and RF signal. Theoretically, different types of drones may impose different levels of risks; a good knowledge of drone classification helps with better risk assessment for drone safety and security management.
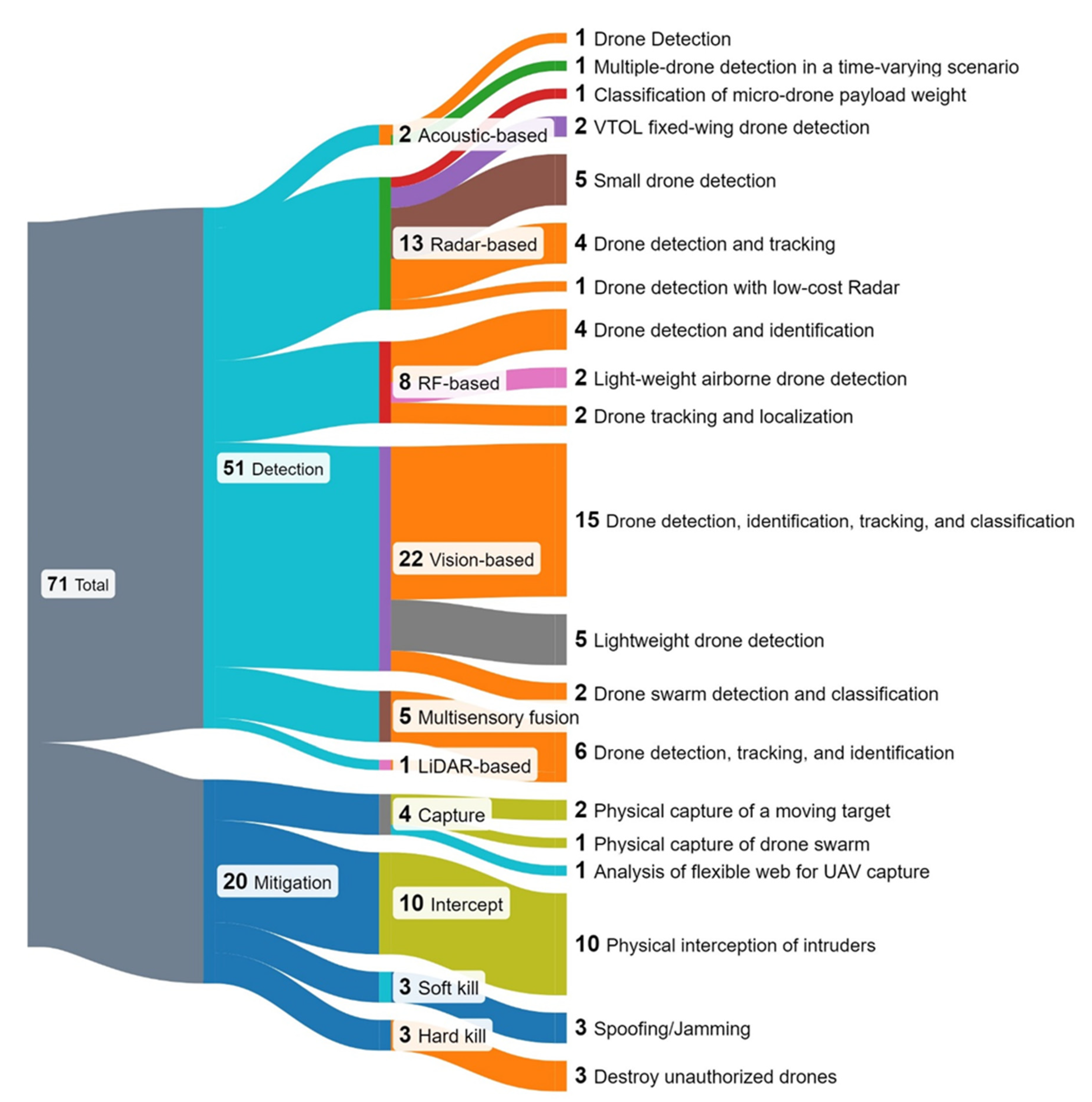
4. Scoping Review
4.1. UAS Detection
4.1.1. Objective of Studies
4.1.2. Limitations and Opportunities
| Technology | Objective(s) | Technologies/Models |
|---|---|---|
| Acoustic based | Drone detection | Apply acoustic signatures for a time-frequency representation of the beamformer’s output processing data [31] |
| Multi-drone detection in a time-varying scenario | Independent component analysis (ICA), support vector machines (SVM), k-nearest neighbors (KNN), and a time-varying drone detection technique [32] | |
| Radar-based | Classification of micro-drone payload weight | Micro-doppler signatures from radar systems [33] |
| VTOL fixed-wing drone detection | Radar signal analysis using X-band pulse-doppler phased array radar [34]; Radar cross-section signature analyses and simulations [37] | |
| Small drone detection | Doppler signal-to-clutter ratio detector [35]; statistical analyses of micro-doppler signals [54]; a ground clutter mitigation method [55]; passive radar [40]; continuous wave Doppler radar [56] | |
| Drone detection and tracking | Micro-doppler signals with different radar dwell times [36]; non-linear processing techniques (compressed sensing, principal component analysis, iterative adaptive approach, multiple-input-multiple-output) [38]; modified deep feedforward neural network [41]; Digital Video Broadcasting—Terrestrial (DVB-T) based passive radar [57] | |
| Drone detection with low-cost Radar | Low-cost solid-state marine radar, pulse-compression principles of operation [39] | |
| RF based | Drone detection and identification | RF-based UAV detection and identification using a hierarchical learning approach [22]; extraction of telemetry data through the decoding of drone ID packets [58]; physical-layer protocol statistical fingerprint [59]; detecting frequency hopping spread spectrum-Gaussian frequency-shift keying (FHSS-GFSK) drone communication signals [60] |
| Light-weight airborne drone detection | HackRF software-defined radio, deep learning neural networks (Open Neural Network Exchange), Intel Neural Compute Stick 2 [61]; C-band RF sensor, Xilinx FPGA, short-term Fourier transform, continuous wavelet transform, and smooth pseudo-Wigner Ville distribution [62] | |
| Drone tracking and localization | The received signal strength indicator (RSSI) ratio fingerprint method and the model-based RSSI ratio algorithm [14]; the Doppler VHF Omnidirectional Radio Range (DVOR) principle [42] | |
| Vision-based | Drone detection, identification, tracking, and classification | 4K camera and SOTA CNN model [43]; an upgraded YOLO with object augmentation [63]; a progressive feature fusing network, a pooling pyramid fusion, and a feature selection model [64]; YOLO v5, cross-stage partial network (CSPDarknet), feature pyramid network (FPN), path aggregation network (PANet), and CNN [45]; Spatio-temporal attention based Siamese method (SiamSTA); a framework consisting of a Siamese-based tracker, a hierarchical discriminator, a re-detection module, and a template updating module [65]; a peripheral-central vision system [66]; SAG-YOLO v5s [67]; a single camera and CNN [68]; telescope camera and YOLO v4 [69]; DeepSort algorithm coupled with Yolo v7 [44]; background subtraction, CNN [70]; YOLO v4 and MedianFlow [71]; CNN trained on synthetic images [72]; a dual capture network algorithm [73] |
| Lightweight drone detection | YOLO v4 [74]; YOLO v3 and v8 implemented on field programmable gate array (FPGA) [75]; YOLO v3, 53-layer CNN, AirSim simulator, Darknet framework [76]; double deep Q-network (DDQN), joint neural network (JNN) [77]; YOLO v3, OpenCV object trackers [78] | |
| Drone swarm detection and classification | Group target tracking improved by an automatic measurement partitioning method based on ordering points [79]; Transfer learning using pre-trained ResNet-50, VGG-16, Inception, and Xception nets [80] | |
| Multisensory Fusion | Drone detection, tracking, and identification | ADS-B, FLARM, direct telemetry reporting, and Remote ID [6]; Radio system, ADS-B, and radar equipped with four antenna arrays [48]; Audio and vision integration, CNN, SVM, Mel Frequency Cepstral Coefficients (MFCC) [49]; visual, acoustic, and magnetic field sensors, artificial intelligence, Bayesian Inference [51]; multimodal sensor fusion (standard video, microphone, thermal infrared sensor, fish-eye camera, ADS-B In, GPS receiver), YOLO v2, GMM background subtraction, Kalman filters, MFCC audio features or LSTM classifiers [53] |
| LiDAR-based | Drone detection, tracking, and identification | Continuous-wave coherent detection LiDAR capable of detecting micro-doppler signatures and raster-scan images [50] |
4.2. UAS Mitigation
4.2.1. Objective of Studies
4.2.2. Limitations and Opportunities
| Technology | Objective(s) | Technologies/Models |
|---|---|---|
| Capture | Physical capture of a moving target | Apply acoustic signatures for a time-frequency representation of the beamformer’s output processing [31] data |
| Physical capture of drone swarm | Independent component analysis (ICA), support vector machines (SVM), k-nearest neighbors (KNN), and a time-varying drone detection technique [32] | |
| Analysis of flexible web for UAV capture | Field experiments [82] | |
| Intercept | Physical interception of intruders | A DRL approach based on global navigation satellite system (GNSS) deception [85]; A dominant region-based trajectory planning strategy [86]; a DRL with dueling network and prioritized experience replay trajectory planning strategy [87]; autonomous defensive drone swarm [88]; Guidance laws for intercepting directly/indirectly approaching targets [94,95]; multi-agent partial observable deep reinforcement learning for pursuer control optimization [89]; a multi-agent jamming system [90]; trajectory planning strategy from a family of time-to-capture isochrons [96]; guidelines of deploying the defensive drones [97] |
| Soft kill | Spoofing/Jamming | Hijacking device-specific communication link on a narrow RF band [91]; multi-agent coordinated close-in jamming [92]; a GNSS covert spoofing algorithm [93] |
| Hard kill | Destroy unauthorized drones | Use of EMI-based functional destruction means without damaging other radio-electronic equipment in the same environment [84]; 12-gauge counter-UAV ammunition [83]; hunter drones [98] |
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
| Author, year, and Country | Objective(s) | Strategy |
| Detection (D) | ||
| Nemer et al. (2021), Saudi Arabia & Belgium [22] | Drone identification and detection | An ensemble learning based on the hierarchical concept, along with pre-processing and feature extraction stages for RF data |
| Martinez-Carranza et al. (2020), Mexico & UK [99] | Literature review (review of detection/classification/localization methods, advantages, limitations, new threats) | Acoustic-based (audio acquisition) |
| Kashiyama et al. (2020), Japan [43] | Detect flying objects at different distances under different weather conditions. | A 4K camera and a SOTA CNN model are used to achieve real-time processing. |
| Ajakwe et al. (2022), Republic of Korea [45] | Vision-based multi-tasking anti-drone framework to detect drones, identify airborne objects, determine their harmful status through perceived threat analysis, and check their proximity in real-time prior to taking action | A vision-based model developed and validated using manually generated drone samples |
| Aouladhadj et al. (2023), France [58] | Detection and tracking | RF-based approach: The identification (ID) tags in RF signals enable the extraction of real-time telemetry data by decoding Drone ID packets. |
| Basan et al. (2021), Russia [61] | Develop a method and system to detect UAS by actively attacking communication channels. | Proposed a lightweight hardware solution with sufficient high computing power that is located on the UAV to calculate the unwanted UAV in any place |
| Besada et al. (2021), Spain [6] | 1. Review SOTA technology in this wide variety of sensors 2. Propose a set of simulation models for them | This study reviews and summarizes current SOTA active radars, passive radars, and acoustic sensors in the C-UAS field and then proposes corresponding C-UAS simulation models. |
| Besada et al. (2022), Spain [47] | Tracking and identification. This study proposes an abstracted general statistical simulation model (mainly for ADS-B, FLARM, and Remote ID) for the most used collaborative sensors and surveillance systems. | Radar and data fusion. |
| Cai et al. (2022), China [74] | Detection on a real-time basis | Vision-based: an accurate and lightweight UAV detection model based on YOLOv4 (the model was lightened and the number of parameters of the model was reduced) |
| Cecio et al. (2024), Italy [75] | Explore the application of edge computing to drone classification | Image processing/computer vision: tune YOLO (V3 and V8) and implement it on a Field Programmable Gate Array (System-on-Chip) |
| Çetin et al. (2021), Spain [76] | Proposed a low-cost real-time drone detection with a guard drone | Computer vision-based technique implemented on guard-drone |
| Chen et al. (2022), China [100] | Tracking | Optical/vision: A simple and effective spatiotemporal attention-based Siamese method (SiamSTA), which performs reliable local searching and wide-range re-detection alternatively for robustly tracking drones in the wild. |
| Chen et al. (2023), China [101] | Tracking; Group Target Tracking for Highly Maneuverable Unmanned Aerial Vehicles Swarms | GTT is enhanced by an automatic measurement partitioning method based on ordering points to identify the clustering structure (OPTICS), DL method is proposed to improve centroid tracking precision, key point extraction is applied to estimate group’s 3D shape, and optimized criteria are proposed to improve the spawning or combination of tracking groups. |
| Cheng et al. (2022), China [65] | Tracking and identification. | Image processing/computer vision: a framework consists of a Siamese-based tracker, a hierarchical discriminator, a re-detection module, and a template updating module. |
| Delleji et al. (2022), Tunisia [63] | Mini-UAV detection under low-visibility conditions | Computer vision/optical-based, deep neural networks |
| Dhulashia et al. (2021), UK [33] | Classification of micro-drone payload weight | Radar-based: the use of micro-doppler signatures from radar systems operating at three different frequency bands |
| Dudczyk et al. (2022), Poland [48] | Detection, identification, and recognition in 3D space of a UAV violating restricted airspace | Multi-sensory data fusion: a radio system, an ADS-B transponder, and a radar-equipped with four antenna arrays. |
| Gong, Li, et al. (2022), China [34] | Investigate radar signals from drones (VTOL, copters) for VTOL fixed-wing drone detection. | Radar signal analysis using X-band pulse-Doppler phased array radar |
| Gong, Yan, et al. (2023), China [35] | Improve radar detection of small drones because of small radar cross-section values. | Apply a Doppler signal-to-clutter ratio detector in a radar system. |
| Gong, Yan, et al. (2022), China [36] | Drone detection by detecting the micro-doppler signals using radar systems with different radar dwell times | Radar detection with different radar dwell times |
| Han et al. (2023), China [64] | Drone detection in infrared images | Image processing/data fusion: a Progressive Feature Fusion Network, a Pooling Pyramid Fusion, and a Feature Selection Model. |
| Itare et al. (2022), France [31] | Drone detection and localization based on acoustic features (not identification) | The UAV’s acoustic signature is used for a time-frequency representation of the beamformer’s output processing. |
| Jačionis et al. (2020), Lithuania [102] | Literature review (review of detection methods, advantages, limitations, and new threats) | Literature review |
| Jamil et al. (2020), Pakistan, Canada, USA, & Qatar [49] | Drone detection | This novel framework consists of a hybrid of handcrafted and deep features to detect and localize malicious drones from their sound and Image information. |
| Kang et al. (2021), USA [66] | A peripheral-central vision system to detect, localize, and classify an airborne UAV | Vision-based |
| Kapoulas et al. (2023). Greece and South Africa [37] | Radar detection of small fixed-wing UAVs partially fills the gap that exists regarding the Radar cross section signatures and identification distances of fixed-wing UAVs. | Radar cross-section analysis through simulations |
| Khawaja et al. (2022), Pakistan, Finland, & USA [103] | Literature review (review of detection/localization/annihilation methods, advantages, limitations, new threats) It also includes unmanned underwater vehicles (UUVs). | Literature review |
| Kumar et al. (2023), USA [38] | Non-linear processing techniques to enhance UAV detection using a portable radar system | Signal processing techniques used for radar systems: compressed sensing, principal component analysis, iterative adaptive approach, and multiple-input-multiple-output |
| Kumawat et al. (2022), India [62] | An RF sensor and a digital circuit built inside the FPGA (field-programable gate array) are described. | RF-based solution. An innovative approach is proposed with the SP-WVD and adaptive decomposition filter bank. |
| Liu et al. (2021), China [68] | UAV detection and identification | Trajectory and image-based; vision/optical based using a single camera; convolution neural network classifier used to recognize objects |
| Lv et al. (2022), China [67] | Detection in high-resolution images with fixed cameras. | Vision-based (a detection method combining background difference and lightweight network SAG-YOLOv5s is proposed) |
| Morge-Rollet et al. (2022), France [59] | Detection and classification using a low-cost RF recorder | RF-based approach: The proposed method exploits the same protocol statistical fingerprint byte at the physical layer, compared to Wi-Fi, thus becoming protocol agnostic. |
| Mototolea et al. (2020), Romania & France [60] | Drone detection | Radio frequency-based: detect frequency hopping spread spectrum—Gaussian frequency—shift keying (FHSS-GFSK) drone communication signals in a non-cooperative scenario. |
| Ojdanić et al. (2023), Austria [69] | Feasibility analysis of optical UAV detection over long distances using robotic telescopes | Optical/Vision (telescope)- based detection: a high-precision mount and a telescope with a camera; YOLOv4. |
| Park et al. (2023), Republic of Korea [104] | Detection and tracking (multi-object tracking) with edge-computing environment and low-frame-rate Short-Wave Infrared (SWIR) images | Optical/Vision (SWIR images of city-surveillance scenarios); a fast and effective multi-object tracking method (Multi-Class Distance-based Tracking) (MCDTrack) in a low-power and low-computation edge-computing environment is proposed. |
| Ghazlane et al. (2024), Morocco [44] | Detection and tracking | Software: DeepSort algorithm coupled with Yolov7 |
| Pittu et al. (2023), India [80] | Multi-class drone classification and detection | Transfer learning-based techniques using pre-trained ResNet-50, VGG-16, Inception and Xception nets |
| Rodrigo et al. (2023), Denmark [50] | Detection of small UAV | LiDAR-based: continuous-wave coherent detection lidar capable of detecting micro-doppler signatures and acquiring raster-scan images of small drones. |
| Rojhani and Shaker (2024), Canada [105] | Review the effectiveness of MIMO and beamforming technologies in detecting low RCS UAVs. | Literature review |
| Rudys et al. (2022), Lithuania [39] | Detection | Low-cost solid-state marine radar working on FMCW and pulse-compression principles of operation. |
| Saadaoui et al. (2023), Algeria [51] | Drone detection using multiple sensors | Multisensory: visual, acoustic, and magnetic field sensors; artificial intelligence; and Bayesian Inference techniques to optimize decision-making in cases where conflict occurs among multisensory. |
| Sahay et al. (2022), USA [106] | Improve C-UAS (detection) reliability by quantifying the uncertainty while applying deep learning classifiers on electro-optical sensor data. | Developed an epistemic uncertainty quantification framework that utilizes the advantages of DL while simultaneously producing uncertainty estimates on both in-distribution and OOD input samples. |
| Seidaliyeva et al. (2020), Kazakhstan & USA [70] | Real-time drone detection with high accuracy | Moving object detection is based on background subtraction, while classification is performed using a CNN. |
| Seidaliyeva et al. (2023), Kazakhstan & USA [107] | Literature review (Detection and identification) | literature review |
| Shoufan and Damiani (2023), United Arab Emirates [52] | Protocols to formalize the interaction between the counter-drone system and relevant agents to clarify possible failures and violations. to complement current DRI systems, mitigating the effect of erroneous drone identification and supporting reliable decision-making | Contingency clarification protocols relying on the UTM system |
| Son et al. (2023), Republic of Korea [71] | Detection and tracking, and updating the target’s features online while tracking | Vision-based approach: a robust drone-tracking approach that integrates detecting (YOLOv4) and tracking (MedianFlow) algorithms based on an online learning classifier |
| Svanström et al. (2022), Sweden [53] | Drone detection and tracking in real-time | Sensor fusion of different sensing modalities (standard video, microphone, thermal infrared sensor, fish-eye camera, ADS-B In, and GPS receiver), software used YOLOv2, GMM background subtraction, Kalman filters, MFCC audio features or LSTM classifiers. |
| Uddin et al. (2022), Pakistan & Saudi Arabia [32] | Detect multiple drones with a time-varying technique using acoustic signals. | Acoustic signals, signal processing |
| Varshosaz et al. (2020), Iran [108] | Detection of UAS spoofing | Using visual odometry |
| Wang et al. (2023), Singapore [14] | Localization | Two received signal strength indicator (RSSI) ratio-based approaches are proposed to localize drones: the RSSI ratio fingerprint method and the model-based RSSI ratio algorithm. |
| Wisniewski et al. (2022), UK [72] | Drone model classification | Computer vision/image processing: Use CNN trained on synthetic images to classify drone models. |
| Xu et al. (2023), China [41] | Drone tracking for multistatic passive radar | Improve passive radar system for target tracking accuracy using a modified deep feedforward neural network (MDFNN). |
| J. Yan et al. (2023), China [54] | Recognize/identify drone types using radar micro-Doppler signatures | Analyze the micro-doppler signals produced by different drone blades to aid in radar-based target recognition of small drones (quantify the radar signatures using statistical measures—signal-to-noise ratio, signal-to-clutter ratio, doppler speed, doppler frequency difference, and Doppler magnitude ratio. |
| X. Yan et al. (2023), China [109] | UAV detection and tracking in urban environments using passive sensors | Literature review |
| Yang et al. (2022), China & UK [55] | Detection of low, slow, and small targets, as well as small drones, using radar with ground clutter. Investigate the feasibility and performance of a ground clutter mitigation method. | A ground clutter mitigation method combining slow-time multiple-input multiple-output (st-MIMO) waveforms and independent component analysis (ICA) in a ground-based MIMO radar focusing on LSS target detection |
| You et al. (2023), China [73] | Low-altitude drone attitude detection and tracking | Designed two capture networks with different resolutions. Computer vision based |
| Yousaf et al. (2022), United Arab Emirates [110] | LR of the trends and challenges of the most recent UAV detection methods | Literature review |
| Zhang et al. (2023), China [24] | drone remote control signal detection based on cyclic spectrum features | Signal processing and detection: A remote-control signal UAV-CYC set dataset is constructed, and a network architecture is proposed based on improved AlexNet. |
| Zhu et al. (2021), China [40] | Small drone detection through passive radar | Digital television terrestrial multimedia broadcasting (DTMB) based passive radar |
| Kyritsis et al. (2023), Greece [56] | Provide early warning for flying-by small UAS by applying a continuous wave Doppler radar. | Doppler radar-based technology by applying fast Fourier transform to the returned signal’s Doppler frequency. |
| Martelli et al. (2020). Italy [57] | DVB-T-based passive radar for simultaneous short-range surveillance against drones and long-range monitoring of aircraft at airport terminal area | DVB-T-based passive radar |
| Mitigation (M) | ||
| Ameloot et al. (2022), Belgium [83] | Investigate the multi-projectile behavior of 12-gauge counter-UAV ammunition. | Hard kill/destroy; 2D point mass model for the trajectory of the considered projectile, complemented with empirical assessment of the model |
| Belousov et al. (2022), Russia [84] | Counter-UAS using EMI-based functional destruction means avoiding damaging other radio-electronic equipment in the same complex environment. | This study focuses on the use of hollow and thin passive conductors, the use of a magnetodielectric in a reaction-symmetric modal filter, the use of reaction-symmetric structures for decomposing the train of ultrashort pulses (USP), and the use of a meander line as a protective means against USPs. |
| Brust et al. (2021), Luxembourg [88] | Intercept and escort intruders relying on an autonomous defense UAV swarm. | An autonomous defense UAV swarm |
| Çetin et al. (2022), Spain [87] | Counter a drone in a 3D space with another drone | A DRL with a dueling network and prioritized experience replay has been proposed to counter a drone in 3D space, and the experiences are loaded from the previous training by filtering the experiences. |
| Chae et al. (2024), Republic of Korea [85] | Counter fixed-wing drone system that can respond to fixed-wing drones in autonomous flight with soft kills. The system redirects fixed-wing drones to a designated target position using the GNSS deception based on the drone’s position and speed measured by radar. | Reinforcement learning, GNSS, radar, and Markov decision processes are defined to enable redirection. |
| Chakravarthy and Ghose (2020), USA & India [111] | Capture a swarm of intruder drones using a net manipulated by a team of defense UAVs | Physical capture with a net manipulated by a team of defense UAVs |
| Fu and Liu (2021), Canada [97] | Target defense game (defender intercepts an invading drone) with a slow defender | Trajectory planning for defenders, guidelines on how to deploy the defenders to ensure the target area is protected |
| Fu and Liu (2022), Canada [96] | Target defense game against a faster invader | Solve the saddle point strategy from a family of time-to-capture isochrons. |
| Fu and Liu (2020), Canada [86] | A dominant region-based strategy for a group of defenders to intercept an intruder | Dominant region-based strategy |
| Gao & Li (2023), China [93] | Spoofing | GNSS spoofing technology, a GNSS covert spoofing algorithm, is proposed to convert directional spoofing on UAV equipped with tightly coupled GNSS and IMU, which includes a fixed-point four-step spoofing strategy and avoidance of the least-squares residual receiver autonomous integrity monitoring (LSR-RAIM) of UAV |
| Lee et al. (2022), USA [91] | Conduct C-UAS by performing cyber-attacks on adversarial UAS by hijacking the device-specific communication link on a narrow RF band without the need for broad-spectrum RF energy bursts | 1. Validate the cyber-attack C-UAS concept by reviewing recent C-UAS operational experimental scenarios and analyzing the collected data. 2. A simulation model is constructed to analyze and validate the mission scenarios. 3. A comparison of energy efficiency and trade-offs of different C-UAS approaches |
| Liu et al. (2022), China [82] | Analysis of traction and unfolding dynamics of flexible webs for UAV capture | Physical intercepting and capture |
| Luo et al. (2023), China [95] | Provide a special cooperative guidance law for intercepting a cluster of UAVs using mother-son missiles. | Cooperative guidance law |
| Ma et al. (2024), China [112] | Capture illegal drones | Vision-based (YOLO-v5) techniques for drone identification establish a visual-servo system to determine the relative position, an extended Kalman filter algorithm for flight trajectory prediction, and a robotic arm for capturing. |
| Pärlin et al. (2024), Finland, Belgium & Germany [113] | UAS reliability/robustness against counter-UAS system | Radio technology (full duplex vs. half duplex) jamming. |
| Pierre et al. (2023), USA [89] | Pursue and intercept a faster UAS or evader. | AI/machine learning: multi-agent partial observable deep reinforcement learning for pursuer control optimization |
| Siddhardha and Ratnoo (2023), India [94] | Present guidance laws that aid a protective drone moving on a closed circular boundary to intercept a rogue drone attempting to penetrate that boundary | Guidance laws for intercepting directly/indirectly approaching targets |
| Souli et al. (2023), Cyprus [90] | Rogue drone interception | Jamming: multi-agent jamming system (a group of cooperative autonomous agents employ various algorithms: detection, tracking, jamming, and self-localization) to counter unauthorized drone operations |
| Tan et al. (2021), USA [114] | The systematic step-by-step evaluation process for the counter-UAS system | Model-based systems engineering tools (MBSE) |
| Valianti et al. (2022), Cyprus [92] | Disable a rogue drone | Multi-agent coordinated close-in jamming |
| Vidyadhara et al. (2022), India [81] | A novel passive single-degree-of-freedom manipulator design and its integration on an autonomous drone to capture a moving target. | A full capturing system |
| Su et al. (2022), China [115] | Framework to optimize the false target jamming to decrease the probability of being detected by UAVs on the battlefield. | An evolutionary framework implemented with four popular evolutionary algorithms |
| Detection and Mitigation (D&M) | ||
| Castrillo et al. (2022), Italy [8] | Evaluate the concept of a multiplatform counter-UAS system based on a team of mini drones acting as a cooperative defensive system. | A literature review of the available technologies for sensing, mitigation, and command and control systems that comprise a C-UAS, focusing on their applicability and suitability for mini drones. |
| Çetin et al. (2020), Spain [77] | The learning drone is trained to detect stationary and moving obstacles and to counter and catch the target drone without crashing with any other obstacle inside the neighborhood. | The full state, composed of the image and the auxiliary data, is processed with a neural network. The image is the input of a CNN, followed by a flattened layer. Then, a concatenation layer joints the flattened output of the CNN with the scalar auxiliary data of the state |
| Cline & Dietz (2020), USA [116] | What are the effects of a threat UAV’s speed on the detection and interdiction of a C-UAS designed to protect a 40-acre facility from threat UAS overflights given hypothetical C-UAS sensor performance data and fixed interdiction characteristics? | Agent-based modeling software (AnyLogic modeling software) |
| Espada (2020), Spain [117] | Review the study of the existing counter-UAS systems and their use considering international law. | Review work, position paper |
| Chiper et al. (2022), Romania [118] | The literature review (review of detection/localization/annihilation methods, advantages, limitations, and new threats) emphasizes RF-based systems implemented using software-defined radio (SDR) platforms. PRISMA is referred to. | RF-based solutions. The DronEnd system (RF-based and SDR platform) is presented. |
| Fortune et al. (2022), Estonia & Germany [119] | A position paper to justify the need for counterterrorist UAS | Literature review |
| Hao et al. (2020), China [120] | Research on anti-UAV swarm control system | Literature review |
| Kang et al. (2020), South Korea [4] | Provides a comprehensive survey of C-UAS, describing its key technologies and providing sufficient information to comprehend this system. | Survey/review |
| Kim et al. (2023), South Korea & China [78] | A vision-based UAV chasing system can be embedded in a pursuer UAV to protect it from attacks by an evader UAV. | Computer vision-based, deep learning-based (YOLOv3) |
| Kootala et al. (2023), USA [121] | Literature review (review of detection methods, advantages, limitations, and new threats). | Drone Jammers, Directed Energy Weapons, Net Guns, Surveillance Cameras, Patrolling Drones |
| Lykou et al. (2020), Greece [3] | A survey of drone incidents near airports and a literature review of sensor technologies able to prevent, detect, identify, and mitigate rogue drones. | A resilience action plan is proposed to support airport operators and stakeholders to increase the robustness of critical assets and infrastructures against airborne malicious threats. |
| Nallamalli et al. (2023), India [122] | Counter UAV swarms | Analyze the problems, identify the demand and requirements, and propose a conceptual design. |
| Park et al. (2021), South Korea [7] | A comprehensive survey on anti-drone systems for civilian facilities. | A survey study |
| Pascarella et al. (2023), Italy, France & Spain [123] | Evaluation of a resilience-driven operational concept to counter-UAS in airports | Propose a concept based on the evaluation of simulations and event tree analysis. |
| Rahman et al. (2024), Republic of Korea [30] | Describe the recent use of various UAV detection and classification technologies based on ML and deep learning algorithms. | A survey study |
| Rudys et al. (2022), Lithuania [39] | Propose a concept of an airborne counter-UAS platform consisting of several vehicles with radar to overcome the short-range limitation of existing countermeasures. | Using a low-cost marine radar with a high-resolution 2 m wide antenna embedded into the wing and a small rotorcraft UAV carried by a bigger fixed-wing as countermeasures. |
| Su et al. (2021), China [124] | Operational effectiveness evaluation for anti-UAV system | Fuzzy analytic hierarchy process |
| Tianfeng et al. (2023), China [125] | Review the current development status of anti-UAV swarm systems | A review/position paper |
| Wang et al. (2021), USA [1] | Present a systematic introduction of C-UAS technologies, thus fostering a research community committed to the safe integration of UAS into the airspace system. | Literature review (comprehensive survey of existing literature in C-UAS) |
| Kashi et al. (2024), India [126] | Scenario-based comparative analysis and discussion of drone detection systems | A survey study |
References
- Wang, J.; Liu, Y.; Song, H. Counter-unmanned aircraft system (s)(C-UAS): State of the art, challenges, and future trends. IEEE Aerospace and Electronic Systems Magazine 2021, 36, 4–29. [Google Scholar]
- Herrera, G.J.; Dechant, J.A.; Green, E.; Klein, E.A. Technology trends in small unmanned aircraft systems (suas) and counter-uas: A five-year outlook; Institute for Defense Analyses.: 2022.
- Lykou, G.; Moustakas, D.; Gritzalis, D. Defending airports from UAS: A survey on cyber-attacks and counter-drone sensing technologies. Sensors 2020, 20, 3537. [Google Scholar] [CrossRef] [PubMed]
- Kang, H.; Joung, J.; Kim, J.; Kang, J.; Cho, Y.S. Protect your sky: A survey of counter unmanned aerial vehicle systems. Ieee Access 2020, 8, 168671–168710. [Google Scholar]
- Chamola, V.; Kotesh, P.; Agarwal, A.; Gupta, N.; Guizani, M. A comprehensive review of unmanned aerial vehicle attacks and neutralization techniques. Ad hoc networks 2021, 111, 102324. [Google Scholar] [PubMed]
- Besada, J.A.; Campaña, I.; Carramiñana, D.; Bergesio, L.; de Miguel, G. Review and simulation of counter-UAS sensors for unmanned traffic management. Sensors 2021, 22, 189. [Google Scholar] [CrossRef]
- Park, S.; Kim, H.T.; Lee, S.; Joo, H.; Kim, H. Survey on anti-drone systems: Components, designs, and challenges. IEEE access 2021, 9, 42635–42659. [Google Scholar]
- Castrillo, V.U.; Manco, A.; Pascarella, D.; Gigante, G. A review of counter-UAS technologies for cooperative defensive teams of drones. Drones 2022, 6, 65. [Google Scholar] [CrossRef]
- Ronda-Pupo, G.A.; Guerras-Martin, L.Á. Dynamics of the evolution of the strategy concept 1962–2008: a co-word analysis. Strategic management journal 2012, 33, 162–188. [Google Scholar]
- Bem, D.J. Writing a review article for Psychological Bulletin. Psychological Bulletin 1995, 118, 172. [Google Scholar]
- Donthu, N.; Kumar, S.; Mukherjee, D.; Pandey, N.; Lim, W.M. How to conduct a bibliometric analysis: An overview and guidelines. Journal of business research 2021, 133, 285–296. [Google Scholar]
- Page, M.J.; Moher, D.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E. PRISMA 2020 explanation and elaboration: updated guidance and exemplars for reporting systematic reviews. bmj 2021, 372. [Google Scholar]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E. The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. bmj 2021, 372. [Google Scholar]
- Wang, Y.; Zeng, Y.; Sun, S.; Tan, P.H.; Ma, Y.; Kurniawan, E. Drone Controller Localization Based on RSSI Ratio. Sensors 2023, 23, 5163. [Google Scholar] [CrossRef]
- Callon, M.; Courtial, J.P.; Laville, F. Co-word analysis as a tool for describing the network of interactions between basic and technological research: The case of polymer chemsitry. Scientometrics 1991, 22, 155–205. [Google Scholar]
- Wang, Z.-Y.; Li, G.; Li, C.-Y.; Li, A. Research on the semantic-based co-word analysis. Scientometrics 2012, 90, 855–875. [Google Scholar]
- Zupic, I.; Čater, T. Bibliometric methods in management and organization. Organizational research methods 2015, 18, 429–472. [Google Scholar]
- Ding, Y.; Chowdhury, G.G.; Foo, S. Bibliometric cartography of information retrieval research by using co-word analysis. Information processing & management 2001, 37, 817–842. [Google Scholar]
- Burt, R.S. Structural holes. In Social stratification; Routledge: 2018; pp. 659-663.
- Okamoto, K.; Chen, W.; Li, X.-Y. Ranking of closeness centrality for large-scale social networks. In Proceedings of the International workshop on frontiers in algorithmics, 2008; pp. 186-195.
- Basak, S.; Rajendran, S.; Pollin, S.; Scheers, B. Combined RF-based drone detection and classification. IEEE Transactions on Cognitive Communications and Networking 2021, 8, 111–120. [Google Scholar]
- Nemer, I.; Sheltami, T.; Ahmad, I.; Yasar, A.U.-H.; Abdeen, M.A. RF-based UAV detection and identification using hierarchical learning approach. Sensors 2021, 21, 1947. [Google Scholar] [CrossRef]
- Mo, Y.; Huang, J.; Qian, G. Deep learning approach to UAV detection and classification by using compressively sensed RF signal. Sensors 2022, 22, 3072. [Google Scholar] [CrossRef]
- Zhang, H.; Li, T.; Li, Y.; Li, J.; Dobre, O.A.; Wen, Z. RF-based drone classification under complex electromagnetic environments using deep learning. IEEE Sensors Journal 2023, 23, 6099–6108. [Google Scholar]
- Alam, S.S.; Chakma, A.; Rahman, M.H.; Bin Mofidul, R.; Alam, M.M.; Utama, I.B.K.Y.; Jang, Y.M. Rf-enabled deep-learning-assisted drone detection and identification: An end-to-end approach. Sensors 2023, 23, 4202. [Google Scholar] [CrossRef] [PubMed]
- Ashush, N.; Greenberg, S.; Manor, E.; Ben-Shimol, Y. Unsupervised drones swarm characterization using RF signals analysis and machine learning methods. Sensors 2023, 23, 1589. [Google Scholar] [CrossRef] [PubMed]
- Sohal, R.S.; Grewal, V.; Singh, K.; Kaur, J. Deep learning approach for investigation of temporal radio frequency signatures of drones. International Journal of Communication Systems 2023, 36, e5377. [Google Scholar]
- Mandal, S.; Satija, U. Time–frequency multiscale convolutional neural network for RF-based drone detection and identification. IEEE Sensors Letters 2023, 7, 1–4. [Google Scholar]
- Lofù, D.; Di Gennaro, P.; Tedeschi, P.; Di Noia, T.; Di Sciascio, E. URANUS: Radio Frequency Tracking, Classification and Identification of Unmanned Aircraft Vehicles. IEEE Open Journal of Vehicular Technology 2023. [Google Scholar]
- Rahman, M.H.; Sejan, M.A.S.; Aziz, M.A.; Tabassum, R.; Baik, J.-I.; Song, H.-K. A Comprehensive Survey of Unmanned Aerial Vehicles Detection and Classification Using Machine Learning Approach: Challenges, Solutions, and Future Directions. Remote Sensing 2024, 16, 879. [Google Scholar]
- Itare, N.; Thomas, J.-H.; Raoof, K.; Blanchard, T. Acoustic estimation of the direction of arrival of an unmanned aerial vehicle based on frequency tracking in the time-frequency plane. Sensors 2022, 22, 4021. [Google Scholar] [CrossRef]
- Uddin, Z.; Qamar, A.; Alharbi, A.G.; Orakzai, F.A.; Ahmad, A. Detection of Multiple Drones in a Time-Varying Scenario Using Acoustic Signals. Sustainability 2022, 14, 4041. [Google Scholar] [CrossRef]
- Dhulashia, D.; Peters, N.; Horne, C.; Beasley, P.; Ritchie, M. Multi-frequency radar micro-doppler based classification of micro-drone payload weight. Frontiers in Signal Processing 2021, 1, 781777. [Google Scholar]
- Gong, J.; Li, D.; Yan, J.; Hu, H.; Kong, D. Comparison of radar signatures from a hybrid VTOL fixed-wing drone and quad-rotor drone. Drones 2022, 6, 110. [Google Scholar] [CrossRef]
- Gong, J.; Yan, J.; Hu, H.; Kong, D.; Li, D. Improved radar detection of small drones using doppler signal-to-clutter ratio (DSCR) detector. Drones 2023, 7, 316. [Google Scholar] [CrossRef]
- Gong, J.; Yan, J.; Li, D.; Kong, D. Detection of micro-Doppler signals of drones using radar systems with different radar dwell times. Drones 2022, 6, 262. [Google Scholar] [CrossRef]
- Kapoulas, I.K.; Hatziefremidis, A.; Baldoukas, A.; Valamontes, E.S.; Statharas, J. Small fixed-wing UAV radar cross-section signature investigation and detection and classification of distance estimation using realistic parameters of a commercial anti-drone system. Drones 2023, 7, 39. [Google Scholar] [CrossRef]
- Kumar, M.; Kelly, P.K. Non-Linear Signal Processing methods for UAV detections from a Multi-function X-band Radar. Drones 2023, 7, 251. [Google Scholar] [CrossRef]
- Rudys, S.; Ragulis, P.; Laučys, A.; Bručas, D.; Pomarnacki, R.; Plonis, D. Investigation of UAV detection by different solid-state marine radars. Electronics 2022, 11, 2502. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Liu, M. Using DTMB-Based Passive Radar for Small Unmanned Aerial Vehicle Detection. Wireless Communications and Mobile Computing 2021, 2021, 9987992. [Google Scholar]
- Xu, B.; Yi, J.; Cheng, F.; Gong, Z.; Wan, X. High-accuracy target tracking for multistatic passive radar based on a deep feedforward neural network. Frontiers of Information Technology & Electronic Engineering 2023, 24, 1214–1230. [Google Scholar]
- Češkovič, M.; Kurdel, P.; Gecejová, N.; Labun, J.; Gamcová, M.; Lehocký, M. A Reasonable Alternative System for Searching UAVs in the Local Area. Sensors 2022, 22, 3122. [Google Scholar] [CrossRef]
- Kashiyama, T.; Sobue, H.; Sekimoto, Y. Sky monitoring system for flying object detection using 4K resolution camera. Sensors 2020, 20, 7071. [Google Scholar] [CrossRef]
- Ghazlane, Y.; Hilali Alaoui, A.E.; Medomi, H.; Bnouachir, H. Real-Time Airborne Target Tracking using DeepSort Algorithm and Yolov7 Model. International Journal of Advanced Computer Science & Applications 2024, 15. [Google Scholar]
- Ajakwe, S.O.; Ihekoronye, V.U.; Kim, D.-S.; Lee, J.M. DRONET: Multi-tasking framework for real-time industrial facility aerial surveillance and safety. Drones 2022, 6, 46. [Google Scholar] [CrossRef]
- Zhang, Z.; Ouyang, W.; Gao, H.; Jing, X. Edge UAV Detection Based on Cyclic Spectral Feature: An Intelligent Scheme. Wireless Communications and Mobile Computing 2023, 2023, 3770982. [Google Scholar]
- Besada, J.A.; Carramiñana, D.; Bergesio, L.; Campaña, I.; Bernardos, A.M. Modelling and simulation of collaborative surveillance for unmanned traffic management. Sensors 2022, 22, 1498. [Google Scholar] [CrossRef]
- Dudczyk, J.; Czyba, R.; Skrzypczyk, K. Multi-sensory data fusion in terms of UAV detection in 3D space. Sensors 2022, 22, 4323. [Google Scholar] [CrossRef] [PubMed]
- Jamil, S.; Rahman, M.; Ullah, A.; Badnava, S.; Forsat, M.; Mirjavadi, S.S.; Fawad. Malicious UAV detection using integrated audio and visual features for public safety applications. Sensors 2020, 20, 3923. [Google Scholar] [CrossRef]
- Rodrigo, P.J.; Larsen, H.E.; Pedersen, C. CW coherent detection lidar for micro-Doppler sensing and raster-scan imaging of drones. Optics Express 2023, 31, 7398–7412. [Google Scholar]
- Saadaoui, F.Z.; Cheggaga, N.; Djabri, N.E.H. Multi-sensory system for UAVs detection using Bayesian inference. Applied Intelligence 2023, 53, 29818–29844. [Google Scholar]
- Shoufan, A.; Damiani, E. Contingency Clarification Protocols for Reliable Counter-Drone Operation. IEEE Transactions on Aerospace and Electronic Systems 2023. [Google Scholar]
- Svanström, F.; Alonso-Fernandez, F.; Englund, C. Drone detection and tracking in real-time by fusion of different sensing modalities. Drones 2022, 6, 317. [Google Scholar] [CrossRef]
- Yan, J.; Hu, H.; Gong, J.; Kong, D.; Li, D. Exploring Radar Micro-Doppler Signatures for Recognition of Drone Types. Drones 2023, 7, 280. [Google Scholar] [CrossRef]
- Yang, F.; Guo, J.; Zhu, R.; Le Kernec, J.; Liu, Q.; Zeng, T. Ground clutter mitigation for slow-time MIMO radar using independent component analysis. Remote Sensing 2022, 14, 6098. [Google Scholar]
- Kyritsis, A.; Makri, R.; Uzunoglu, N. Detection of Low RCS Unmanned Air Systems Using K-Band Continuous Wave Doppler Radar. Journal of Electrical and Computer Engineering 2023, 2023, 5683661. [Google Scholar]
- Martelli, T.; Colone, F.; Cardinali, R. DVB-T based passive radar for simultaneous counter-drone operations and civil air traffic surveillance. IET Radar, Sonar & Navigation 2020, 14, 505–515. [Google Scholar]
- Aouladhadj, D.; Kpre, E.; Deniau, V.; Kharchouf, A.; Gransart, C.; Gaquière, C. Drone Detection and Tracking Using RF Identification Signals. Sensors 2023, 23, 7650. [Google Scholar] [CrossRef] [PubMed]
- Morge-Rollet, L.; Le Jeune, D.; Le Roy, F.; Canaff, C.; Gautier, R. Drone detection and classification using physical-layer protocol statistical fingerprint. Sensors 2022, 22, 6701. [Google Scholar] [CrossRef] [PubMed]
- Mototolea, D.; Youssef, R.; Radoi, E.; Nicolaescu, I. Non-cooperative low-complexity detection approach for FHSS-GFSK drone control signals. IEEE Open Journal of the Communications Society 2020, 1, 401–412. [Google Scholar]
- Basan, E.; Pshikhopov, V.; Lapina, M.; Mecella, M. Analysis of methods and systems for detecting and countering uavs. In Proceedings of the IOP Conference Series: Materials Science and Engineering; 2021; p. 012034. [Google Scholar]
- Kumawat, H.C.; Raj, A.A.B. SP-WVD with adaptive-filter-bank-supported RF sensor for low RCS targets’ nonlinear micro-Doppler signature/pattern imaging system. Sensors 2022, 22, 1186. [Google Scholar] [CrossRef] [PubMed]
- Delleji, T.; Slimeni, F.; Fekih, H.; Jarray, A.; Boughanmi, W.; Kallel, A.; Chtourou, Z. An upgraded-yolo with object augmentation: Mini-uav detection under low-visibility conditions by improving deep neural networks. In Proceedings of the Operations Research Forum, 2022; p. 60.
- Han, Z.; Zhang, C.; Feng, H.; Yue, M.; Quan, K. PFFNET: A Fast Progressive Feature Fusion Network for Detecting Drones in Infrared Images. Drones 2023, 7, 424. [Google Scholar] [CrossRef]
- Cheng, F.; Liang, Z.; Peng, G.; Liu, S.; Li, S.; Ji, M. An anti-UAV long-term tracking method with hybrid attention mechanism and hierarchical discriminator. Sensors 2022, 22, 3701. [Google Scholar] [CrossRef] [PubMed]
- Kang, C.; Chaudhry, H.; Woolsey, C.A.; Kochersberger, K. Development of a peripheral–central vision system for small unmanned aircraft tracking. Journal of Aerospace Information Systems 2021, 18, 645–658. [Google Scholar]
- Lv, Y.; Ai, Z.; Chen, M.; Gong, X.; Wang, Y.; Lu, Z. High-resolution drone detection based on background difference and SAG-Yolov5s. Sensors 2022, 22, 5825. [Google Scholar] [CrossRef]
- Liu, Y.; Liao, L.; Wu, H.; Qin, J.; He, L.; Yang, G.; Zhang, H.; Zhang, J. Trajectory and image-based detection and identification of UAV. The Visual Computer 2021, 37, 1769–1780. [Google Scholar]
- Ojdanić, D.; Sinn, A.; Naverschnigg, C.; Schitter, G. Feasibility analysis of optical UAV detection over long distances using robotic telescopes. IEEE Transactions on Aerospace and Electronic Systems 2023, 59, 5148–5157. [Google Scholar]
- Seidaliyeva, U.; Akhmetov, D.; Ilipbayeva, L.; Matson, E.T. Real-time and accurate drone detection in a video with a static background. Sensors 2020, 20, 3856. [Google Scholar] [CrossRef]
- Son, S.; Lee, I.; Cha, J.; Choi, H. Online Learning-Based Hybrid Tracking Method for Unmanned Aerial Vehicles. Sensors 2023, 23, 3270. [Google Scholar] [CrossRef]
- Wisniewski, M.; Rana, Z.A.; Petrunin, I. Drone model classification using convolutional neural network trained on synthetic data. Journal of Imaging 2022, 8, 218. [Google Scholar]
- You, J.; Ye, Z.; Gu, J.; Pu, J. UAV-Pose: A Dual Capture Network Algorithm for Low Altitude UAV Attitude Detection and Tracking. IEEE Access 2023, 11, 129144–129155. [Google Scholar]
- Cai, H.; Xie, Y.; Xu, J.; Xiong, Z. A lightweight and accurate uav detection method based on yolov4. Sensors 2022, 22, 6874. [Google Scholar] [CrossRef]
- Di Cecio, G.; Manco, A.; Gigante, G. On-board drone classification with Deep Learning and System-on-Chip implementation. In Proceedings of the Journal of Physics: Conference Series, 2024; p. 012059.
- Çetin, E.; Barrado, C.; Pastor, E. Improving real-time drone detection for counter-drone systems. The Aeronautical Journal 2021, 125, 1871–1896. [Google Scholar]
- Çetin, E.; Barrado, C.; Pastor, E. Counter a drone in a complex neighborhood area by deep reinforcement learning. Sensors 2020, 20, 2320. [Google Scholar] [CrossRef] [PubMed]
- Kim, K.; Kim, J.; Lee, H.-G.; Choi, J.; Fan, J.; Joung, J. UAV chasing based on YOLOv3 and object tracker for counter UAV systems. IEEE Access 2023, 11, 34659–34673. [Google Scholar]
- Chen, C.; Zheng, Z.; Xu, T.; Guo, S.; Feng, S.; Yao, W.; Lan, Y. Yolo-based uav technology: A review of the research and its applications. Drones 2023, 7, 190. [Google Scholar] [CrossRef]
- Pittu, V. S. R.; Nelakuditi, U. R.; Bandla, P.; Thotakura, Y. DL based multi-class drone classification for counter drone detection applications. SSRG International Journal of Electrical and Electronics Engineering 2023, 10(11), 21–30. [Google Scholar]
- Vidyadhara, B.; Tony, L.A.; Gadde, M.S.; Jana, S.; Varun, V.; Bhise, A.A.; Sundaram, S.; Ghose, D. Design and integration of a drone based passive manipulator for capturing flying targets. Robotica 2022, 40, 2349–2364. [Google Scholar]
- Liu, Y.; Xiong, Z.; Qiu, Y.; Yan, F.; Ma, C. Analysis of Traction and Unfolding Dynamics of Space-Symmetric Flexible Webs for UAV Interception and Capture. Symmetry 2022, 14, 1915. [Google Scholar] [CrossRef]
- Ameloot, C.; Robbe, C.; Papy, A.; Hendrick, P. Modeling complex behavior of multi-projectile counter UAV 12 gauge ammunition. Human Factors and Mechanical Engineering for Defense and Safety 2022, 6, 3. [Google Scholar]
- Belousov, A.O.; Zhechev, Y.S.; Chernikova, E.B.; Nosov, A.V.; Gazizov, T.R. UAVs protection and countermeasures in a complex electromagnetic environment. Complexity 2022, 2022, 8539326. [Google Scholar]
- Chae, M.-H.; Park, S.-O.; Choi, S.-H.; Choi, C.-T. Reinforcement Learning-Based Counter Fixed-Wing Drone System Using GNSS Deception. IEEE Access 2024. [Google Scholar]
- Fu, H.; Liu, H.H.-T. Guarding a territory against an intelligent intruder: Strategy design and experimental verification. IEEE/ASME Transactions on Mechatronics 2020, 25, 1765–1772. [Google Scholar]
- Çetin, E.; Barrado, C.; Pastor, E. Countering a drone in a 3d space: Analyzing deep reinforcement learning methods. Sensors 2022, 22, 8863. [Google Scholar] [CrossRef] [PubMed]
- Brust, M.R.; Danoy, G.; Stolfi, D.H.; Bouvry, P. Swarm-based counter UAV defense system. Discover Internet of Things 2021, 1, 1–19. [Google Scholar]
- Pierre, J.-E.; Sun, X.; Fierro, R. Multi-agent partial observable safe reinforcement learning for counter uncrewed aerial systems. IEEE Access 2023. [Google Scholar]
- Souli, N.; Kolios, P.; Ellinas, G. Multi-agent system for rogue drone interception. IEEE Robotics and Automation Letters 2023, 8, 2221–2228. [Google Scholar]
- Lee, C.H.; Thiessen, C.; Van Bossuyt, D.L.; Hale, B. A systems analysis of energy usage and effectiveness of a counter-unmanned aerial system using a cyber-attack approach. Drones 2022, 6, 198. [Google Scholar] [CrossRef]
- Valianti, P.; Papaioannou, S.; Kolios, P.; Ellinas, G. Multi-agent coordinated close-in jamming for disabling a rogue drone. IEEE Transactions on Mobile Computing 2021, 21, 3700–3717. [Google Scholar]
- Gao, Y.; Li, G. A GNSS instrumentation covert directional spoofing algorithm for UAV equipped with tightly-coupled GNSS/IMU. IEEE Transactions on Instrumentation and Measurement 2023, 72, 1–13. [Google Scholar]
- Siddhardha, K.; Ratnoo, A. Intercepting Intruder on a Circular Boundary. Journal of Guidance, Control, and Dynamics 2023, 46, 186–197. [Google Scholar]
- Luo, R.; He, G.; Bu, X.; Shi, J. Cooperative Guidance Law for the Mother-Cabin of the Anti-UAV Cluster Mother-Son Missile. Applied Sciences 2023, 13, 5397. [Google Scholar]
- Fu, H.; Liu, H.H.-T. An isochron-based solution to the target defense game against a faster invader. IEEE Control Systems Letters 2021, 6, 1352–1357. [Google Scholar]
- Fu, H.; Liu, H.H.-T. Defending a target area with a slower defender. IEEE Control Systems Letters 2022, 7, 661–666. [Google Scholar]
- Rudys, S.; Laučys, A.; Ragulis, P.; Aleksiejūnas, R.; Stankevičius, K.; Kinka, M.; Razgūnas, M.; Bručas, D.; Udris, D.; Pomarnacki, R. Hostile UAV detection and neutralization using a UAV system. Drones 2022, 6, 250. [Google Scholar] [CrossRef]
- Martinez-Carranza, J.; Rascon, C. A review on auditory perception for unmanned aerial vehicles. Sensors 2020, 20, 7276. [Google Scholar] [CrossRef]
- Chen, J.; Huang, B.; Li, J.; Wang, Y.; Ren, M.; Xu, T. Learning spatio-temporal attention based siamese network for tracking UAVs in the wild. Remote Sensing 2022, 14, 1797. [Google Scholar]
- Chen, Y.; Jiao, Y.; Wu, M.; Ma, H.; Lu, Z. Group Target Tracking for Highly Maneuverable Unmanned Aerial Vehicles Swarms: A Perspective. Sensors 2023, 23, 4465. [Google Scholar] [CrossRef] [PubMed]
- Jačionis, T. Modern methods for detection of unmanned aerial vehicles. Mokslas–Lietuvos ateitis/Science–Future of Lithuania 2020, 12. [Google Scholar]
- Khawaja, W.; Semkin, V.; Ratyal, N.I.; Yaqoob, Q.; Gul, J.; Guvenc, I. Threats from and countermeasures for unmanned aerial and underwater vehicles. Sensors 2022, 22, 3896. [Google Scholar] [CrossRef] [PubMed]
- Park, J.; Hong, J.; Shim, W.; Jung, D.-J. Multi-object tracking on swir images for city surveillance in an edge-computing environment. Sensors 2023, 23, 6373. [Google Scholar] [CrossRef]
- Rojhani, N.; Shaker, G. Comprehensive Review: Effectiveness of MIMO and Beamforming Technologies in Detecting Low RCS UAVs. Remote Sensing 2024, 16, 1016. [Google Scholar]
- Sahay, R.; Stubbs, J.J.; Brinton, C.G.; Birch, G.C. An uncertainty quantification framework for counter unmanned aircraft systems using deep ensembles. IEEE Sensors Journal 2022, 22, 20896–20909. [Google Scholar]
- Seidaliyeva, U.; Ilipbayeva, L.; Taissariyeva, K.; Smailov, N.; Matson, E.T. Advances and challenges in drone detection and classification techniques: A state-of-the-art review. Sensors 2023, 24, 125. [Google Scholar] [CrossRef] [PubMed]
- Varshosaz, M.; Afary, A.; Mojaradi, B.; Saadatseresht, M.; Ghanbari Parmehr, E. Spoofing detection of civilian UAVs using visual odometry. ISPRS International Journal of Geo-Information 2019, 9, 6. [Google Scholar]
- Yan, X.; Fu, T.; Lin, H.; Xuan, F.; Huang, Y.; Cao, Y.; Hu, H.; Liu, P. UAV Detection and Tracking in Urban Environments Using Passive Sensors: A Survey. Applied Sciences 2023, 13, 11320. [Google Scholar]
- Yousaf, J.; Zia, H.; Alhalabi, M.; Yaghi, M.; Basmaji, T.; Shehhi, E.A.; Gad, A.; Alkhedher, M.; Ghazal, M. Drone and controller detection and localization: Trends and challenges. Applied Sciences 2022, 12, 12612. [Google Scholar]
- Chakravarthy, A.; Ghose, D. Collision cone-based net capture of a swarm of unmanned aerial vehicles. Journal of Guidance, Control, and Dynamics 2020, 43, 1688–1710. [Google Scholar]
- Ma, J.; Chen, P.; Xiong, X.; Zhang, L.; Yu, S.; Zhang, D. Research on Vision-Based Servoing and Trajectory Prediction Strategy for Capturing Illegal Drones. Drones 2024, 8, 127. [Google Scholar] [CrossRef]
- Pärlin, K.; Riihonen, T.; Le Nir, V.; Adrat, M. Physical-layer reliability of drones and their counter-measures: Full vs. half duplex. IEEE Transactions on Wireless Communications 2023. [Google Scholar]
- Tan, C.S.; Van Bossuyt, D.L.; Hale, B. System analysis of counter-unmanned aerial systems kill chain in an operational environment. Systems 2021, 9, 79. [Google Scholar] [CrossRef]
- Su, Z.-L.; Jiang, X.-L.; Li, N.; Ling, H.-F.; Zheng, Y.-J. optimization of false target jamming against UAV detection. Drones 2022, 6, 114. [Google Scholar] [CrossRef]
- Cline, T.L.; Dietz, J.E. Agent based modeling for low-cost counter UAS protocol in prisons. International Journal of Aviation, Aeronautics, and Aerospace 2020, 7, 2. [Google Scholar]
- Espada, C.G. Counter-Drone Defense Systems in the Light of International Law. The Journal of Applied Business and Economics 2020, 22, 105–118. [Google Scholar]
- Chiper, F.-L.; Martian, A.; Vladeanu, C.; Marghescu, I.; Craciunescu, R.; Fratu, O. Drone detection and defense systems: Survey and a software-defined radio-based solution. Sensors 2022, 22, 1453. [Google Scholar] [CrossRef]
- Fortune, D.; Nitsch, H.; Staniforth, A. Countermeasures for combatting the terrorist use of aerial drones—Bringing research and innovation to operational reality. Internal Security 2022, 14, 173–181. [Google Scholar]
- Hao, Q.; Li, W.; Qiu, Z.; Zhang, J. Research on anti UAV swarm system in prevention of the important place. In Proceedings of the Journal of Physics: Conference Series, 2020; p. 052020.
- Kootala, A.; Mousa, A.; Pong, P.W. Drones are Endangering Energy Critical Infrastructure, and How We Can Deal with This. Energies 2023, 16, 5521. [Google Scholar] [CrossRef]
- Nallamalli, R.; Singh, K.; Kumar, I.D. Technological perspectives of countering uav swarms. Defence Science Journal 2023, 73. [Google Scholar]
- Pascarella, D.; Gigante, G.; Vozella, A.; Sodano, M.; Ippolito, M.; Bieber, P.; Dubot, T.; Martinavarro, E. Evaluation of a Resilience-Driven Operational Concept to Manage Drone Intrusions in Airports. Information 2023, 14, 239. [Google Scholar] [CrossRef]
- Su, B.; Liu, H.; Zhang, G. Anti-UAV group effectiveness evaluation based on fuzzy analytic hierarchy process. In Proceedings of the Journal of Physics: Conference Series, 2021; p. 022098.
- Tianfeng, F.; Xiaojing, M.; Chi, Z. Development status of anti UAV swarm and analysis of new defense system. In Proceedings of the Journal of Physics: Conference Series, 2023; p. 092011.
- Kashi, R.N.; Prashanth, A.; Kashi, S.R.; Prabhakara, G. A survey and analysis of drone detection systems using a systems approach superposed on scenarios. Systems Engineering 2024, 27, 598–636. [Google Scholar]
| Category | Keywords | Closeness Centrality |
|---|---|---|
| Core | Drone | 0.935 |
| Drone detection | 0.879 | |
| Counter-UAS | 0.879 | |
| Counter-UAS system | 0.879 | |
| Machine learning | 0.829 | |
| Drone tracking | 0.763 | |
| Drone classification | 0.763 | |
| Semi-periphery | RF signal | 0.725 |
| Drone identification | 0.725 | |
| Sense technology | 0.707 | |
| Data fusion | 0.707 | |
| Radar | 0.690 | |
| Drone localization | 0.659 | |
| Aerial surveillance | 0.659 | |
| Command and control | 0.63 | |
| Periphery | Doppler radar | 0.617 |
| Swarm drones | 0.617 | |
| Security | 0.617 | |
| Drone neutralization | 0.617 | |
| Armed drones | 0.617 | |
| Defense system | 0.604 | |
| Optical sensors | 0.604 | |
| Airport operations | 0.604 | |
| Simulation | 0.592 | |
| safety | 0.592 | |
| Image processing | 0.592 | |
| UTM | 0.58 | |
| YOLO | 0.569 | |
| UAS network | 0.558 | |
| Polarization | 0.500 |
| Core Keywords | Drone detection | Machine learning | Drone tracking | Drone classification |
|---|---|---|---|---|
| Other keywords | Machine learning | Drone tracking | Drone identification | Radar |
| Drone tracking | Drone classification | Drone localization | RF signal | |
| Drone identification | Image processing | Drone classification | Swarm drones | |
| Drone classification | Data fusion | |||
| Radar | ||||
| RF signal | ||||
| Data fusion |
| Core Keywords | Drone detection | Machine learning | Drone tracking | Drone classification |
|---|---|---|---|---|
| Other keywords | Swarm drones | Drone identification | Swarm drones | UTM |
| UTM | Drone neutralization | Command and control | Safety | |
| UAS network | Command and control | Drone neutralization | Security | |
| Airport operations | Data fusion | Command and control | ||
| RF signal |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





