1. Introduction
The best guard against cyber security incidents involving threats is a machine-literate individual, according to research. The people listed in this investigation as being the most likely to stick in your memory are recruits inside the company, particularly when it comes to intruders asking for personally identifiable information from target persons. This review adds to the body of evidence supporting the psychological elements that contribute to user and network insecurity. [
1] According to this research, human behavior patterns that may be affected by education, human actions, and human wants all remain complex and fragile, even while innovation has a significant role to play in reducing the effects of hacking
. Although hacking assaults can be decreased, a comprehensive strategy to deal with specific cybersecurity problems has not yet been proposed. Numerous disciplines, including but not limited to information technology and computer science, engineering, organizational performance, economics, psychology, political science, sociology, decision-making, global affairs, and the legal system, are required for the diverse problem of cyber security. Although policy professionals and many others may find it easy to become bogged down in technical details, cyber
defense is more than just a technical matter, even though analytical measures are an important component. [
1] On the other hand, cybersecurity knowledge is often divided along disciplinary boundaries, which restricts the variety of interconnected viewpoints that may be obtained. A cyber-attack is an orchestrated attempt to gain control of computer systems, networks, and businesses that rely on technology. Cyberattacks employ malicious code to alter computer files, coding, or logic, which commonly results in identity or knowledge theft, as well as data breaches. Another term for a cyber-attack is a computer network assault or CNA. Cybercriminals also use strategies when company technology and security systems are evolving. Businesses have lost
$2.7 billion worldwide as a result of cybercrime, and study indicates that this amount will increase each year. These damages include the costs of lost business and reputation, ransoms paid to hackers, fines, maintenance and upgrade expenses, and other expenditures.
2. Importance Of Cyber Security
On computers and other devices, the government, the armed forces, businesses, the financial industry, and medical institutions gather, store, and process enormous amounts of data. This
emphasizes how important cyber security is. Considerable quantities of these data could include private information. such as financial information, intellectual property, or other types of data for which exposure to or illegal access to the data may have
unfavorable consequences (Gutlapalli et al., 2019).
Organizations move sensitive data to other devices and across networks in the course of conducting business. Cyber security is the research area that focuses on protecting data and the systems that manage or store it (Khan, 2011). [
2]
Businesses and
organizations need to take security measures to safeguard their sensitive business and financial data, especially those in charge of maintaining data related to national security, health records, or financial records. people’s information as cyberattacks get more frequent and sophisticated. The nation’s highest-ranking intelligence officials warned as early as March 2013 that threats to national security from cyberattacks and digital surveillance have surpassed even those from terrorism (Shukla et al. 2023). [
3]
Software applications, computers, networks, and other electronic devices are all having a big impact on how human society is becoming more digital. This is beneficial to every aspect of our lives.
Utilizing digital devices like tablets and smartphones as well as PCs is essential to the functioning of all essential infrastructure, such as government agencies, financial institutions, healthcare systems, and manufacturing sectors (Reddy et al., 2020). The vast majority of the gadgets have internet connections. Threat actors are now more motivated than ever to figure out how to get into those computer systems, whether it’s for simple vandalism, political or social motivations (also known as hacktivism), extortion, or financial gain. Over the past 20 years, cyberattacks against vital infrastructure have been launched against every developed country, resulting in countless enterprises suffering catastrophic losses. Over 2,000 confirmed data breaches occur globally each year, with an average cost of over
$3.9 million (or
$8.1 million within the US). Almost 3.5 billion people, or half of the world’s population, have had their personal information stolen by cybercriminals since 2000 (Mandapuram, 2017a). [
4]
3. Evolution Of The Cyber Security Threat
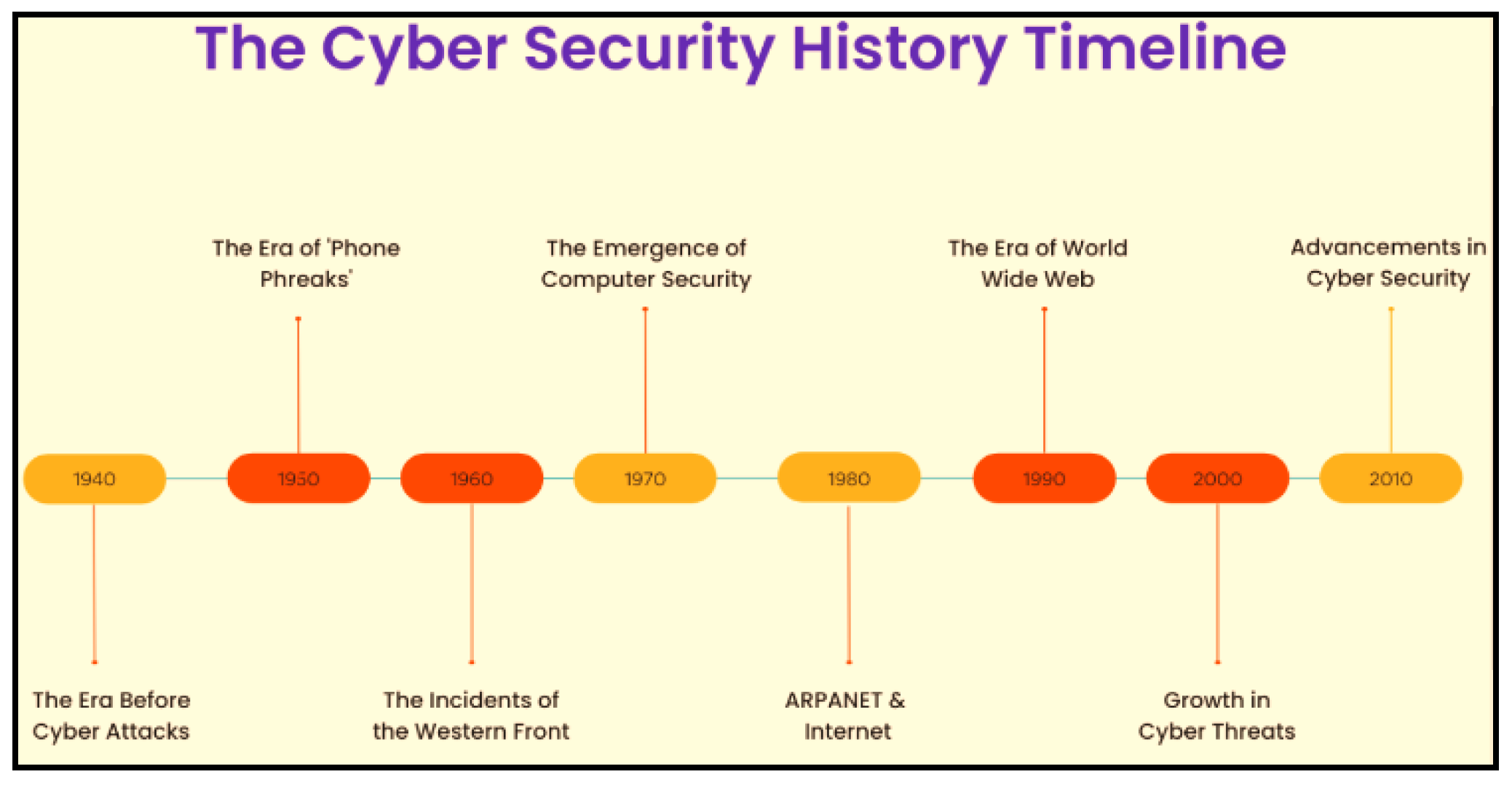
The sophistication of cyber threats was not even close to reaching its peak a few years ago. Since the nature of cyber threats is always evolving, businesses require protection against hackers’ current and future tools and techniques.
Figure 1.
Cyber security history timeline.
Figure 1.
Cyber security history timeline.
Gen V Assaults
As a result of these improvements, new generations of cyber threats emerge regularly, altering the ever-changing landscape of cybersecurity hazards. So far, we’ve seen five generations of cyber threats and remedies. Among them are the following.
Gen I (Virus): In the late 1980s, virus attacks on stand-alone PCs led to the development of the first antivirus programs.
Gen II (Network): A firewall was built to detect and neutralize cyberattacks that attempted to infiltrate the system over the internet.
Generation III (Applications): The extensive exploitation of vulnerabilities included in Generation III (Applications) application software led directly to the widespread use of intrusion prevention systems (IPS). [
4]
Ransomware
Despite being there for a while, ransomware has only recently come to be seen as the main threat. Since WannaCry proved that ransomware assaults might be profitable, their prevalence has increased. Taking into account Ransomware has changed dramatically since then. According to Mandapuram et al. (2018), ransomware has shifted from encrypting files to gathering data for use in double- and triple-extortion assaults against victims and consumers. Certain ransomware gangs use DDoS assaults or threats to get money from their victims. Another aspect fueling the spread of ransomware is the concept of "ransomware as a service," or "RaaS," when the makers of the virus rent out their infection to "affiliates" in exchange for a fee. Many cybercrime groups receive advanced software using RaaS, which raises the possibility of sophisticated attacks. Because of this, Preventing ransomware is crucial to an organization’s online security. [
4]
Supply Chain Assault
Many firms’ security efforts have been centered on apps and systems (Bodepudi et al., 2019). The corporate perimeter is protected, meaning that only authorized users and programs may access it. prevent the penetration of enterprise networks by cyber criminals. The vulnerabilities in this approach, as well as the ability and motivation of hackers to exploit them, have been made clear by an upsurge in supply chain attacks. The attacks of SolarWinds, Kaseya, and Microsoft Exchange Server showed how a company’s trusted partnerships with other companies may compromise its cyber security. A cyber threat actor can get access to all consumer networks by exploiting one organization and misusing trust connections (Gutlapalli, 2017a). To prevent supply chain assaults, use zero trust security. Alliances and vendor partnerships are advantageous to the company, but software and users from third parties should only be utilized with permission. [
5]
Malware
Malware creation has characterized decades of cyberattacks. Using the newest
defense technology, virus producers and cyber defenders engage in a never-ending game of cat and mouse to deceive one another. Successful cyberattacks often catalyze new ones (Chen et al., 2019). These days, malware is nimble, crafty, and intelligent. Security analysts often respond to threats after they have already materialized, and there may be less risk with more antiquated security solutions like signature-based detection. It is no longer "good enough" for detection to thwart malware attacks. Gen V malware mitigation requires cyber security solutions that thwart attacks before they have a chance to cause harm. [
6]
4. Cyber Attack Classification
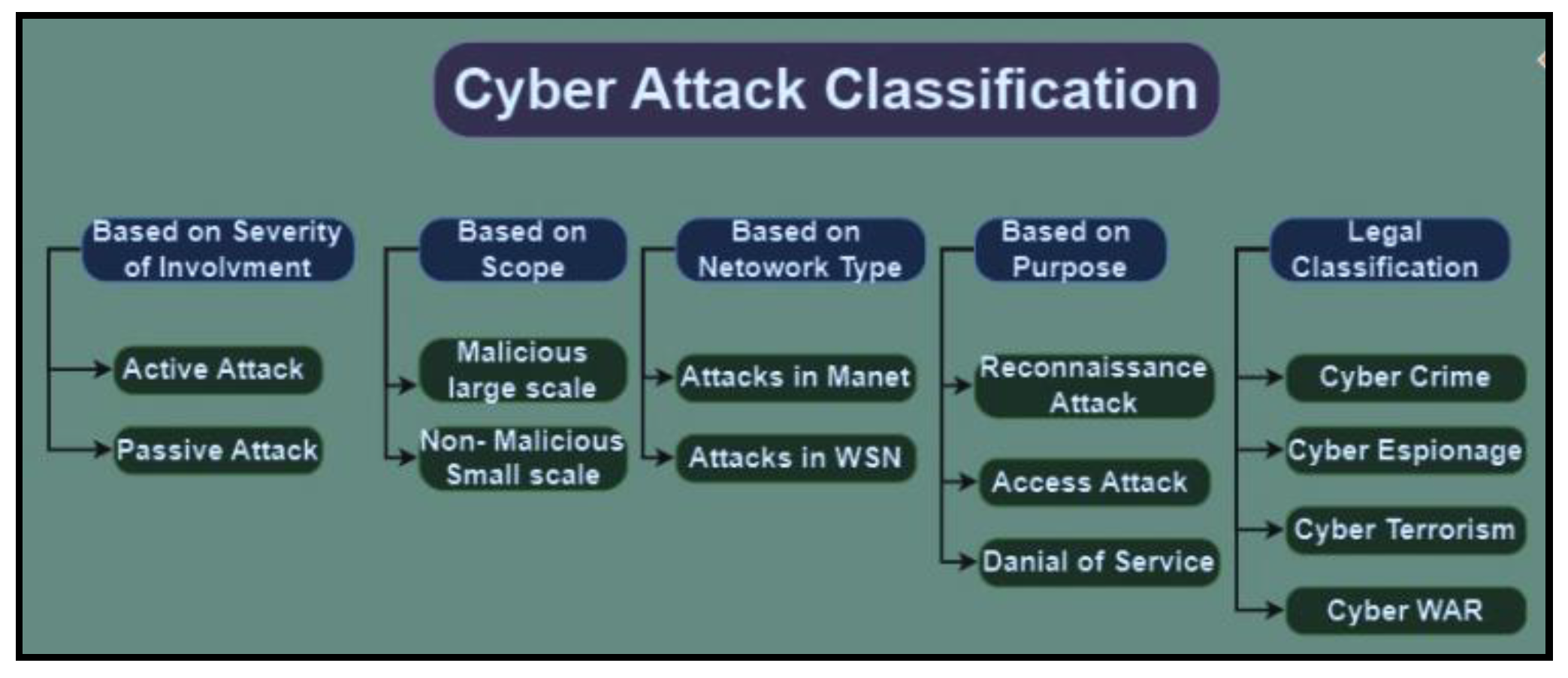
Figure 2.
Classification of cyber attack.
Figure 2.
Classification of cyber attack.
1. Based On Severity Of Involvement
Depending on the severity and relevance of the offense, strikes may be divided into several categories. Passive and Active Attacks may be examined in two sections.
- (i)
Passive Attack: The intruder is passively listening to the two parties’ conversation to play the data stored in the device by call hearing. In contrast, a breach may have been attempted even when the database was not accessed, unlike in an ongoing assault.
- (ii)
Active attacks: they include the attacker causing packets to be sent unidirectionally or bidirectionally to other parties or obstructing data transit—an examination of research studies on cyberterrorism’s passive attacks. [
6]
2. Based On Scope
- (i)
Moreover, classify cyberattacks according to their focus. There are two types of big-range malware: malicious and non-malicious.
- (ii)
Dubious Broad Spectrum Attackers in this category aim to gain benefits for themselves or their organization or undermine the system’s effectiveness. Attacks that interfere with the intended device or disturb the social order include some Attacks that interfere with the target device or disturb the social order.
- (iii)
Mild-mannered Small-Scale These are threats that cause minimal damage to property, minimal impact to the target infrastructure, or minimal loss of recoverable data. It is executed by inexperienced assailants or staff members with inexperience [
6]
3. Based On Network Type
- (i)
Attacks on the MANET Numerous assaults exist in this range, such as the Black Hole Attack, the Byzantine Assault, and the Flood Rushing Research Studies.
- (ii)
WSN-related attacks This kind consists of two assaults. Among them are: Attacks based on network layers as well as attacks about and unrelated to cryptography. The regional character of certain cyberattacks raises concerns about global security, and methodological and ideological approaches are examined in connection to these challenges. Data and research on cyber security throughout this phase point to a conceptual trend about the rise in cyberterrorism. Increased reliance on cyberspace yields different scores in the terror domain. This categorization of cyberattack and terrorism gives rise to a cyberwarfare phenomenon. [
7]
4. Based On Purpose
- (i)
Attack of Reconnaissance Results from system mapping studies were included for resources and locations that were not authorized. Examples of reconnaissance attacks are port scanning and packet sniffing.
- (ii)
Attack on Access Without access privileges, an attacker can break into the system or take advantage of a vulnerability to get data. Examples of this kind of assault include phishing, social engineering, and man-in-the-middle attacks.
- (iii)
DoS stands for denial of service, or slowing down or interrupting a system. Additionally, records can be corrupted or erased using this. [
7]
5. Legal Classification
- (i)
Cybercrime An alternative way to put it is "use of IT to encourage the handling of unlawful behavior or offenses." Any act that includes, in the widest sense, the use of IT is referred to as computer crime. Within this category are worms, malware, and logical bombs. Cybercriminals, IT criminals, high-tech criminals, web-based criminals, and electronic criminals are also used interchangeably. 184 An analysis of Research Reports on Cyber Terror.
- (ii)
Cyber-spying or cyber-espionage This community includes well-known programs like spyware and Trojan horses in addition to techniques for capturing target devices. Cyber theft or spying is the illegal use of instruments or methods and the gathering of important data from unapproved or secret sites. In particular, these exercises may be carried out by paid spies, hostile invaders, or coders.
- (iii)
Cybercrime Another issue that has evolved in the twenty-first century is cyber terror. It has grown over time. These kinds of terrorist assaults are quite easy to carry off and inflict unimaginable harm. It is only a sensation of worry that is incredibly difficult to overcome. According to the FBI definition, cyber terror is any incident that has the potential to cause chaos by impairing essential infrastructure and organizational functions. Cyberwarfare or Cyberwar Cyber warfare is defined as state-performed infiltration activities intended to disrupt or damage the computer systems or networks of another state.
5. Current Trends in Cybersecurity Information Systems
Cybersecurity Information Systems (CIS) are at the forefront of protecting digital assets in today’s interconnected world. With the rapid evolution of technology, the threat landscape is constantly changing, requiring organizations to stay ahead of emerging risks and trends in cybersecurity. [
7]
Definition of CIS: Cybersecurity Information Systems encompass a range of technologies, processes, and practices designed to protect networks, systems, and data from cyber threats.
Importance of CIS: With the increasing frequency and sophistication of cyber attacks, CIS plays a crucial role in safeguarding organizations’ digital assets and ensuring business continuity. [
8]
Security Hardware: Includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), routers, switches, and other network devices designed to enforce security policies and protect against unauthorized access and malicious activities. [
9]
Security Software: Encompasses antivirus software, anti-malware solutions, encryption tools, vulnerability scanners, security information and event management (SIEM) systems, and other software applications used to detect, prevent, and respond to cyber threats. [
10]
Threat Detection: CIS continuously monitors networks, systems, and applications for signs of suspicious activity or potential security breaches. This involves analyzing network traffic, log files, and system behavior to identify indicators of compromise (IOCs) and security incidents.
Threat Prevention: CIS employs various security controls and mechanisms to prevent cyber attacks and unauthorized access to digital assets. This includes implementing access controls, firewalls, intrusion detection/prevention systems, antivirus software, and encryption technologies.
Security Awareness and Training: CIS educates users and employees about cybersecurity best practices, policies, and procedures to promote a culture of security awareness and compliance. This includes conducting security awareness training sessions, phishing simulations, and promoting good cyber hygiene practices. [
11]
Blockchain: Blockchain technology is being leveraged in CIS for secure data storage, authentication, and tamper-proof transaction logging, enhancing data integrity and transparency.
Cloud Computing: Cloud-based security solutions offer scalability, flexibility, and cost-effectiveness for organizations seeking to protect their digital assets. This includes cloud-based firewalls, antivirus software, encryption services, and security-as-a-service (SECaaS) offerings.
Internet of Things (IoT) Security: With the proliferation of IoT devices, securing interconnected devices and networks has become a critical component of CIS. This involves implementing security controls, encryption, and access management for IoT endpoints and gateways.
IoT Security: The proliferation of Internet of Things (IoT) devices introduces new security challenges, including device vulnerabilities, data privacy concerns, and network segmentation issues.
Edge Computing: Edge computing brings processing power closer to IoT devices, enabling real-time data analysis and reducing latency, but also necessitating enhanced security measures to protect edge networks and devices. [
12]
Blockchain Principles: Blockchain technology, known for its decentralized and immutable nature, is being leveraged in CIS to enhance data integrity, transparency, and security.
Secure Data Storage: Blockchain-based solutions provide secure and tamper-proof data storage, reducing the risk of unauthorized access, data breaches, and data manipulation.
Identity and Access Management: Blockchain facilitates decentralized identity and access management systems, enhancing authentication and authorization processes while reducing the reliance on centralized authorities. [
13]
6. Integration of AI and Machine Learning
Because AI offers sophisticated capabilities for threat detection, response, and mitigation, cybersecurity is being revolutionized. Artificial intelligence (AI) technologies, including machine learning and deep learning, allow cybersecurity systems to examine enormous volumes of data, spot trends, and pinpoint abnormalities that might be signs of possible security risks. The following are some essential uses of AI in cybersecurity:
Figure 3.
Strategy of using AI in cybersecurity.
Figure 3.
Strategy of using AI in cybersecurity.
Threat Detection: AI-powered cybersecurity solutions can detect and identify malicious activities, including malware, phishing attempts, and insider threats, by analyzing network traffic, user behavior, and system logs in real time.
Behavioural Analysis: To create baselines and identify variations that can point to suspicious or unusual activities, AI systems can examine user and entity behavior. This strategy assists in locating advanced persistent threats (APTs) and insider threats that elude conventional signature-based detection techniques.
Automated Response: AI enables automated response capabilities, allowing cybersecurity systems to take immediate action to mitigate security threats, such as quarantining infected devices, blocking suspicious IP addresses, or triggering alerts for further investigation.
Spoofing
Attacks known as spoofing aim to impersonate the authentication layer. The purpose of the authentication layer is to shield reputable nodes from malicious insiders and outsiders. An effective method of authenticating usually guards against several threats, including replay attacks, GPS signal spoofing, and black hole attacks. This technique aims to restrict access to the resources and services to authorized users exclusively.
Manipulation
Attacks known as "tampering" aim to alter or introduce harmful code or messages while the program is running. This might interfere with how the transport network, OBUs, and RSUs as a result of their recurring modifications. We can refer to [103], for instance, which discusses a misconfiguration attack that makes use of the country string field.
Denial of Service
In a denial-of-service attack, the attacker tries to overload or bring down the communication channel by flooding the nodes or jamming signals at the physical layer, which results in channel jamming and prevents the vehicle nodes from connecting to the network. In a denial of service attack, the attacker’s primary goal is to stop authorized cars from connecting to the V2X network and communicating with other vehicles via messages. A denial-of-service (DoS) attacker can target individual cars (OBUs) or network units (RSUs).
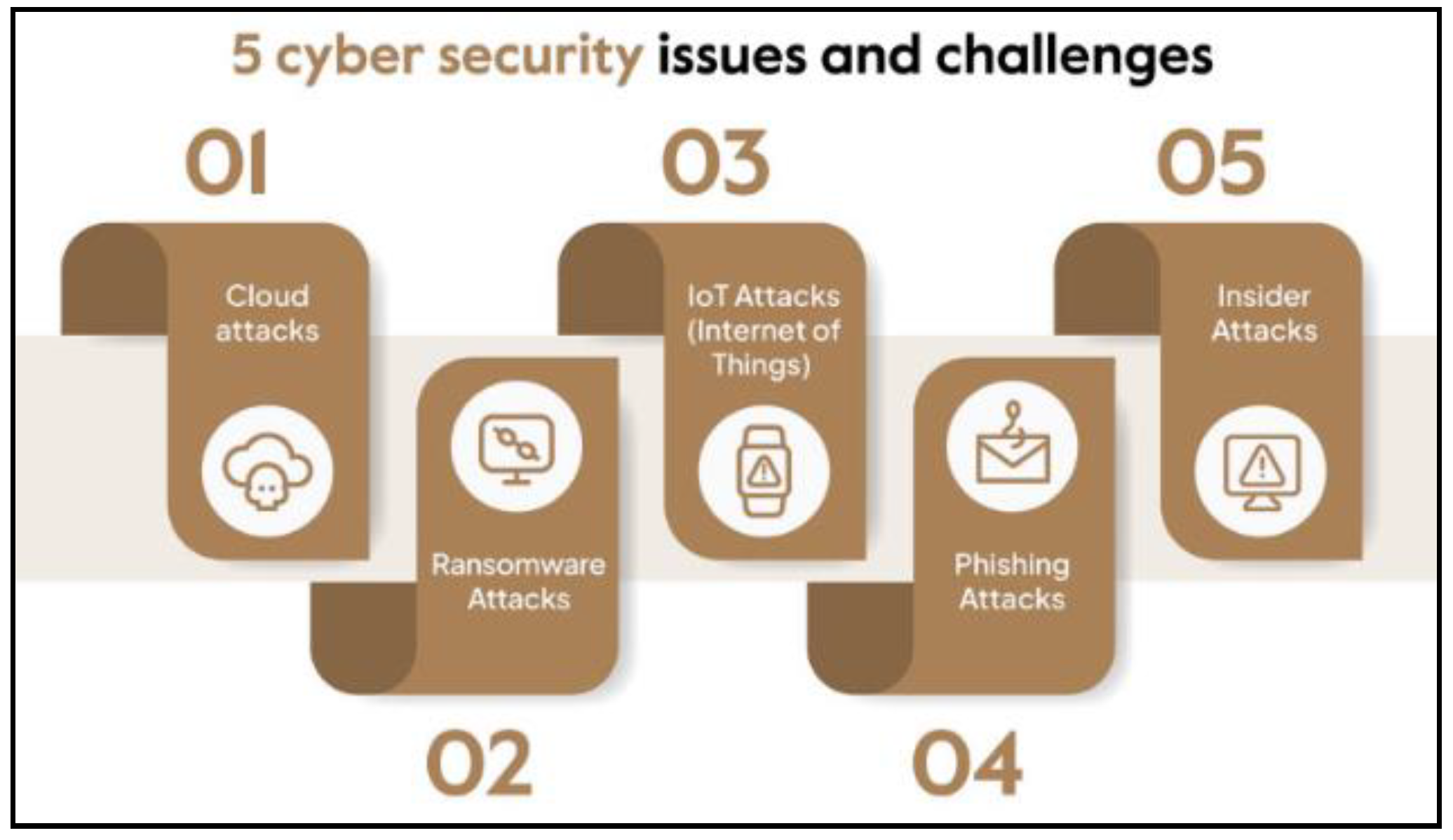
7. Challenges and Opportunities
The rapidly evolving landscape of cybersecurity presents both challenges and opportunities for organizations and individuals. Challenges include the sophistication of cyber-attacks, remote work security concerns, regulatory compliance pressures, and the shortage of skilled professionals. However, opportunities arise from advancements in AI-driven cybersecurity solutions, the adoption of Zero Trust Architecture, increased focus on security awareness training, and the potential for cybersecurity to become a business enabler. [
14]
Figure 4.
Some issues and challenges of cyber security.
Figure 4.
Some issues and challenges of cyber security.
Rapid Technological Advancement: Technological advancements like as cloud computing, artificial intelligence (AI), and the Internet of Things (IoT) have created new weaknesses that hackers may take advantage of.
Sophisticated Cyber Attacks: Cybercriminals are becoming increasingly sophisticated, employing advanced techniques such as ransomware, supply chain attacks, and zero-day exploits to breach systems and steal sensitive data. [
14]
Skills Shortage: Because of the severe lack of qualified cybersecurity specialists, it is difficult for businesses to hire and keep personnel who can effectively protect against changing threats. [
15]
Emergence Of AI in Cybersecurity: Both offensive and defensive cybersecurity strategies are increasingly using artificial intelligence and machine learning, which presents chances to automate threat detection and response procedures. [
16]
8. Conclusion
In this comprehensive study, we have looked at the most current advancements and new paradigms impacting cybersecurity information systems (CIS). Our study has brought to light the dynamic nature of the area, which is characterized by rapid advancements, shifting threats, and inventive solutions. Companies must understand these trends and prepare for future challenges as they navigate an increasingly digitalized and interconnected world to maintain a solid cybersecurity posture.
Key Findings:
Technological Advancements: The study highlights the transformative impact of technological advancements on cybersecurity, particularly in areas such as artificial intelligence (AI), machine learning (ML), blockchain, and quantum computing. These technologies offer both opportunities and challenges, empowering defenders with advanced threat detection capabilities while simultaneously introducing new attack vectors and complexities.
Paradigm Shifts in Defense Strategies: We have identified paradigm shifts in defense strategies, notably the adoption of Zero Trust Architecture (ZTA), DevSecOps practices, and a proactive approach to threat intelligence sharing and collaboration. These strategies reflect a departure from traditional perimeter-based security models towards more holistic, adaptive, and intelligence-driven defense mechanisms.
Regulatory Landscape and Compliance Challenges:
The study underscores the growing regulatory landscape governing cybersecurity, including GDPR, CCPA, and industry-specific regulations. Compliance with these regulations poses significant challenges for organizations, necessitating robust data governance frameworks, privacy-enhancing technologies, and proactive risk management strategies.
Implications And Future Directions:
Our findings have several implications for cybersecurity practitioners, policymakers, and researchers:
Investment In Emerging Technologies: Prioritising investments in cutting-edge technologies like blockchain, AI, and ML may help Organizations improve their capabilities for data protection, threat detection, and incident response.
Adoption Of Zero Trust Principles: The adoption of Zero Trust principles should be accelerated to address the limitations of perimeter-based security and mitigate the risks associated with insider threats and lateral movement by adversaries.
References
- Diwan and T. Dhar, "An investigation and analysis of cyber security information systems: latest trends and future suggestion,". Information Technology in Industry 2021, 2, 477–492.
- G. N. G. J. R. Reddy, "A study of cyber security challenges and its emerging trends on latest technologies,". arXiv 2014, arXiv:1402.1842.
- R. B. e. a. Kshiteesh, "A review on challenges and latest trends on cyber security using text cryptography," In Proceedings of the 3rd International Conference on Integrated Intelligent Computing Communication & Security (ICIIC 2021), 2021.
- T. Fadziso, "Evolution of the cyber security threat: an overview of the scale of cyber threat,". Digitalization & Sustainability Review 2023, 3, 1–12.
- N. Kaja, "Artificial intelligence and cybersecurity: Building an automotive cybersecurity framework using machine learning algorithms," Doctoral dissertation, 2019.
- K. M. C. S. D. a. E. S. Rajasekharaiah, "Cyber security challenges and its emerging trends on latest technologies,". IOP Conference Series: Materials Science and Engineering 2020, 981.
- S. K. M. M. K. &. F. Y. Takemoto, "Trends in Cybersecurity and Latest Countermeasures,". Hitachi Review 2014, 63, 264.
- S. M. Tisdale, "Cybersecurity: Challenges from a Systems, Complexity, Knowledge Management and Business Intelligence Perspective," . Issues in Information Systems 2015, 16, 3.
- G. C. A. D. A. P. Wilshusen, "Cybersecurity: Continued efforts are needed to protect information systems from evolving threats,". United States Government Accountability Office, 2009.
- H. S. Alqahtani, "Latest Trends and Future Directions of Cyber Security Information Systems,". Journal of Information Engineering and Applications 2016, 6, 11.
- A.M. Y. M. a. K. M. N. W. Sandar, "Fundamental areas of cyber security on the latest technology,". International Journal of Trend in Scientific Research and Development 2019, 3.
- M. Himmat, "The Current Trends, Techniques, and Challenges of Cybersecurity,". European Journal of Information Technologies and Computer Science 2023, 3, 1–5.
- A. M. K. S. S. &. C. S. R. Tonge, "Cyber security: challenges for society-literature review," . IOSR Journal of Computer Engineering 2013, 2, 67–75.
- E. A. Fischer, "Cybersecurity issues and challenges: In brief,". 2014.
- D. Ghelani, "Cyber security, cyber threats, implications and future perspectives: A Review," Authorea Preprints, 2022.
- J. a. K. R. R. Kaur, "The recent trends in cyber security: A review,". Journal of King Saud University-Computer and Information Sciences 2022, 38, 5766–5781.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).