I. Introduction
Cyber security is essential in today's digital age to protect companies from a wide range of risks that exist online. The dynamic landscape of cyber security is changing annually due to the advancement of technology and the evolution of threat vectors. The field of cyber security is at the center of previously unheard-of opportunities and difficulties as we head into 2024. This preface establishes the scene for a look at the newest innovations and trends influencing cyber security in 2024. Never before have the stakes been higher or the methods more complex, from the fundamental redesign of network security through Zero Trust Architecture (ZTA) to the incorporation of state-of-the-art Artificial Intelligence (AI) and Machine Learning (ML) algorithms for threat detection. A deeper comprehension of new trends becomes crucial as organizations struggle with the challenges of safeguarding cloud environments, containerization technologies, and the Internet of Things (IoT). Furthermore, the immediate need for quantum-resistant cryptography to ensure future-proof data protection measures is highlighted by the impending threat posed by quantum computing. In this piece, we explore the cutting edge of cyber security, identifying the major themes that will transform defensive tactics and resilience in the face of dynamic online dangers. Organizations may strengthen their defenses and come out stronger in the constantly changing cybersecurity landscape of 2024 by navigating these trends with knowledge and foresight.
In summary, maintaining an advantage in the continuous fight against cybercrime requires the use of AI and ML technologies into cyber security operations. Organizations may strengthen their defenses, reduce risks, and protect their digital assets in an increasingly hostile cyber landscape by utilizing the power of these cutting-edge technologies.
II. Zero Trust Architecture (zta)
A growing collection of cyber security paradigms known as "zero trust" shifts defenses away from static, network-based perimeters and toward a focus on users, assets, and resources. Industrial and enterprise infrastructure and workflows are planned using zero-trust principles using zero-trust architecture (ZTA). The concept of zero trust presupposes that no implicit trust is given to assets or user accounts based just on the assets' physical location (local area networks versus the internet), their ownership status (personal or enterprise), or their network location. Prior to establishing a session to access an enterprise resource, separate processes of authentication and authorization are carried out (both for the device and the subject). Zero trust is a reaction to changes in enterprise networks, such as cloud-based assets that are being used by remote users, bring your own device (BYOD), and not contained within a network perimeter owned by the company.
A. Verify Identity
In addition to authentication, it's also important to have proper authorization and access controls in place. This ensures that users and devices are only able to access the resources that they are authorized to access. Regular security audits and updates to security protocols are also necessary to ensure that the system remains secure against emerging threats. Finally, it's important to educate users on best security practices to help prevent unauthorized access and other security breaches.
B. Least Privilege Access
Implementing the least privilege principle is a crucial aspect of maintaining a secure network environment. It is important to regularly review and update access privileges to ensure that they align with the user's current role and responsibilities. By doing so, organizations can effectively reduce the risk of unauthorized access and minimize the impact of any potential security incidents. Implementing the least privilege principle is a crucial aspect of maintaining a secure network environment. It is important to regularly review and update access privileges to ensure that they align with the user's current role and responsibilities. By doing so, organizations can effectively reduce the risk of unauthorized access and minimize the impact of any potential security incidents.
C. Micro-Segmentation
In addition to segmenting the network, it's also important to regularly update and patch all software and devices on the network. This helps to address any known vulnerabilities and prevent attackers from exploiting them. It's also crucial to implement strong authentication and access controls, such as multi-factor authentication and least privilege access, to further protect the network from unauthorized access and potential breaches. Regular security training and awareness for all employees can also help to reduce the risk of human error and improve overall cybersecurity hygiene.
D. Continuous Monitoring and Analysis
Implementing Zero Trust Architecture can significantly reduce the risk of data breaches, cyberattacks, and other security incidents. This approach ensures that every user, device, and application is continuously authenticated and authorized, enhancing overall security posture.
E. Encryption
In today's digital age, where data is a valuable asset, protecting confidential information from potential threats is a crucial aspect of any business. Therefore, implementing effective security measures is not only a legal requirement but also a moral obligation for companies that handle sensitive data.
Multi-factor authentication is one such security measure that adds an extra layer of protection to the traditional username-password login process. It requires users to provide additional information, such as a code sent to their phone or email, to confirm their identity.
Regular security audits are also critical to identify vulnerabilities in the organization's security infrastructure and address them before they can be exploited by cybercriminals. These audits should be conducted by qualified professionals who can assess the system's security posture and recommend improvements where necessary.
By prioritizing data security, organizations can ensure that their customers' information remains confidential and their trust is maintained. It also helps to minimize the risk of reputational damage, financial losses, and legal penalties resulting from data breaches.
F. Dynamic Policy Enforcement
By taking into account various factors and continuously monitoring the system, these security policies ensure that only authorized users have access to sensitive information and that any suspicious activities are detected and prevented in real-time. This proactive approach to security helps to maintain the integrity and confidentiality of important data, providing peace of mind to both the users and the system administrators.
III. Artificial Intelligence (AI) and Machine Learning
By supplementing human capabilities and enhancing threat intelligence, the integration of AI and ML algorithms in cyber security helps enterprises to detect and respond to threats in real time. This section explores the many uses of AI and ML in cyber security, ranging from anomaly detection to predictive analytics, and discusses the limitations and ethical issues surrounding these technologies.
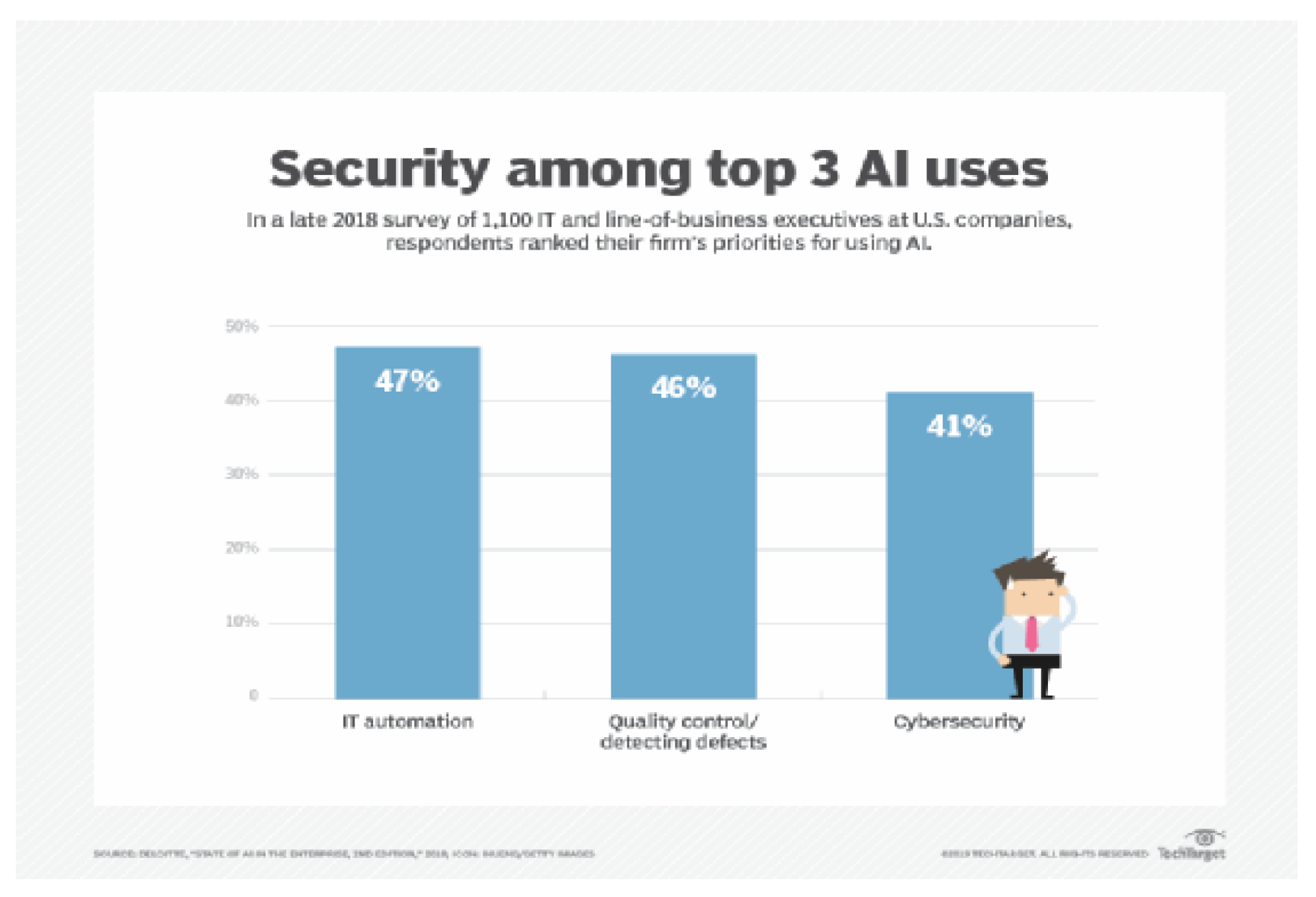
The terms artificial intelligence (AI) and machine learning are most frequently used by security companies to set themselves apart from the competition. Artificial intelligence and machine learning in cyber security products are bringing significant value for the security teams searching for ways to identify malware, attacks, and other risks. These phrases also reflect genuinely practical technology [
1].
Figure 1.
AI, machine learning in cyber security focused on behavior [
2].
Figure 1.
AI, machine learning in cyber security focused on behavior [
2].
A. Artificial Intelligence (AI)
The goal of artificial intelligence (AI) is to grant machines the same level of mental responsiveness as humans. Numerous additional disciplines, such as deep learning and machine learning, are grouped under this one.
B. Machine Learning (ML)
There are various applications of machine learning in cyber security, including detecting and preventing cyber-attacks, identifying vulnerabilities in systems, and improving incident response. With the increasing volume and complexity of cyber threats, machine learning can help organizations stay ahead of potential attacks by quickly identifying patterns and anomalies in data.
Despite the benefits of machine learning in cyber security, there are also potential risks and challenges. For example, machine learning algorithms may have biases or make incorrect decisions if they are trained on incomplete or inaccurate data. Additionally, there is a shortage of skilled professionals who can effectively develop and implement machine learning models for cybersecurity purposes.
To address these challenges, organizations need to invest in both technology and talent. They should ensure that their machine learning models are continuously monitored and refined to improve accuracy and effectiveness. And they should also prioritize hiring and training experts in machine learning and cyber security to ensure that these technologies are used safely and responsibly.
C. Deep Learning (DL)
While machine learning and deep learning both base judgments on historical patterns, deep learning (DL) makes independent modifications. Since machine learning now encompasses deep learning in cyber security, we'll mostly concentrate on ML in this section.
Although it is seen as a superset of fields such as machine learning and deep learning, artificial intelligence in cyber security is not without its uses. The primary focus of artificial intelligence is "success," with "accuracy" receiving less weight. The ultimate goal in complex issue-solving is to arrive at natural replies. Real autonomous decisions are being made in a true AI implementation. Instead, then only returning the dataset's hard, logical conclusion, its programming aims to discover the best answer possible in a given scenario. It's best to comprehend how contemporary AI and its supporting disciplines operate to provide further clarification. Particularly in the realm of cyber security, autonomous systems do not fall under the purview of broadly deployed systems. These self-governing frameworks are what many AIS is frequently associated with people. AI systems that complement or support our security services, however, are useful and readily accessible.
The understanding of the patterns created by machine learning algorithms is the optimal use of AI in cyber security. Naturally, current AI is still unable to analyze data in a way that is comparable to that of a person. While efforts are being made to advance this field in the direction of human-like frameworks, genuine artificial intelligence (AI) is still a ways off, requiring machines to take abstract notions and reinterpret them in different contexts. Put another way, this is not as near to this degree of creativity and critical thinking as the AI speculations would have you believe. In cyber security, machine learning (ML) is important for threat identification, prevention, and response, among other areas. Here are a few applications for machine learning.
IV. Extended Detection and Response (xdr)
In order to offer comprehensive threat detection and response capabilities across endpoints, networks, and cloud environments, Extended Detection and Response (XDR) systems integrate several security products. The design of XDR platforms, their function in expediting incident response procedures, and the difficulties enterprises encounter in successfully deploying and overseeing XDR solutions are all covered in this part.
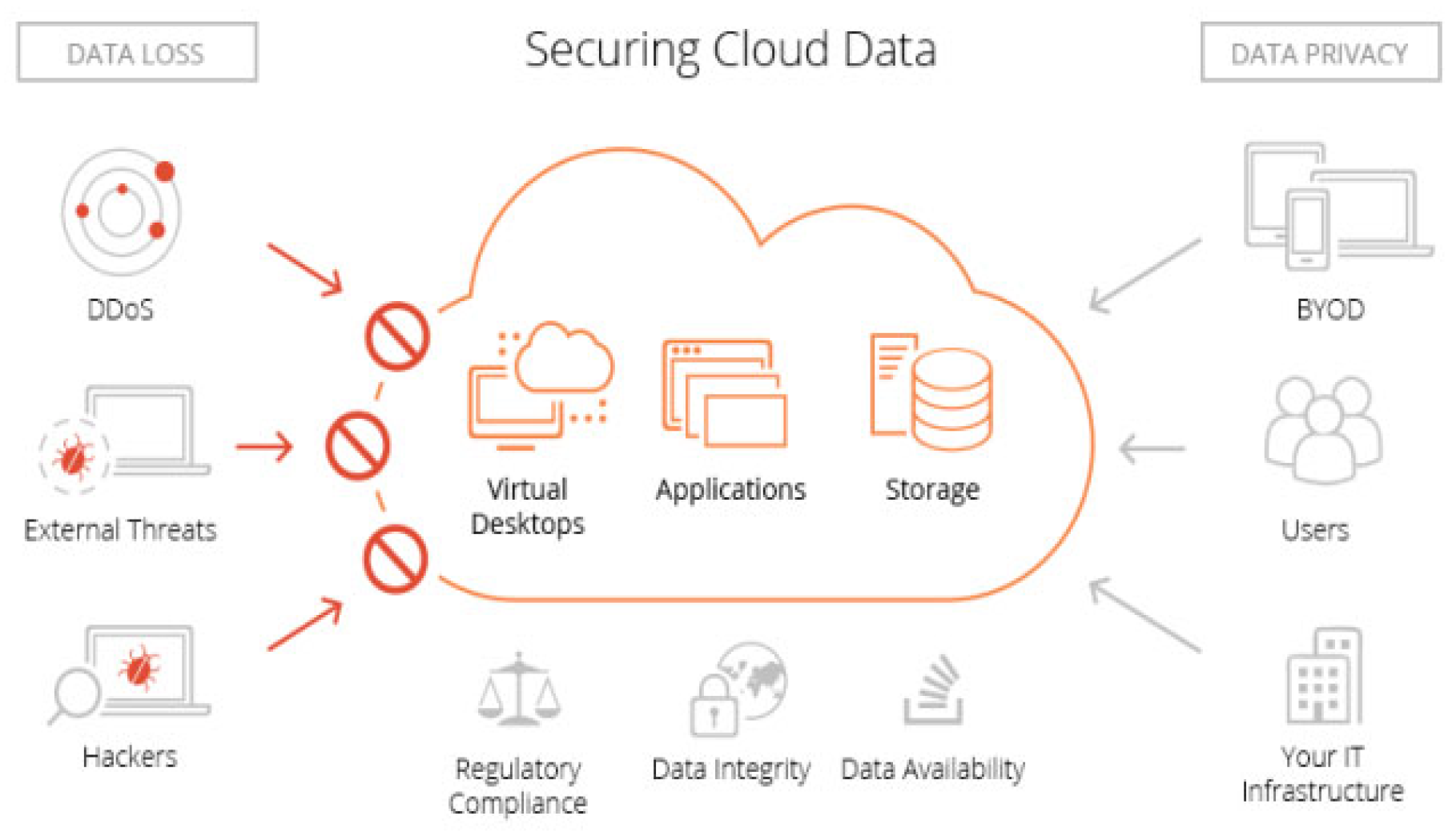
Figure 2.
Securing cloud data [
9].
Figure 2.
Securing cloud data [
9].
Cyber security experts are always coming up with new defensive tactics because cyber threats have increased exponentially in the digital sphere. Extended detection and response (XDR) is one of the most significant improvements to have appeared in recent years. XDR, which is a comprehensive and integrated approach to threat detection, response, and mitigation, is a paradigm shift in cybersecurity, evolving from its predecessor, endpoint detection and response (EDR) [
3].
The complexity of modern threats proved too much for traditional cybersecurity solutions to handle. XDR helps security teams gain comprehensive visibility into potential threats and their broader context by gathering and correlating diverse data from multiple sources across an organization's entire IT ecosystem, including endpoints, networks, cloud environments, and applications. This contextual understanding is essential for accurately identifying sophisticated, multistage attacks that might otherwise go undetected and for considerably cutting down on the time between threat identification and mitigation [
4].
XDR fills in these gaps by unifying security data and enabling real-time analysis, threat detection, and rapid response. XDR not only improves an organization's ability to thwart threats but also offers a more streamlined and efficient security operation, freeing up valuable resources that would otherwise be spent on manual investigation and response tasks. Adversaries have progressed beyond single-vector attacks to orchestrating complex, multisector campaigns that exploit vulnerabilities across multiple entry points. Legacy security measures, often focused on isolated layers of defense, cannot keep up with these advanced attacks [
5].
V. Cloud Security
There are several challenges that organizations face when moving to the cloud. One of the main concerns is data security. Since cloud computing involves storing data on remote servers, there is always the risk of data breaches and cyberattacks. Another concern is data privacy, as sensitive information may be exposed if not handled properly. In addition, cloud environments are highly dynamic, making it difficult to keep track of all the changes and configurations that are made. This can lead to misconfigurations and vulnerabilities that can be exploited by attackers.
To address these challenges, organizations need to adopt a comprehensive approach to cloud security. This involves implementing a range of security measures, such as encryption, access controls, and monitoring tools. It also requires regular audits and assessments to identify and address any security gaps or vulnerabilities.
One of the key advantages of cloud computing is scalability, which allows organizations to quickly and easily expand their infrastructure as needed. However, this can also create security challenges, as it can be difficult to maintain consistent security across a large, distributed environment. To address this, organizations need to implement a centralized security management system that can monitor and manage security across all cloud resources.
Overall, securing cloud infrastructures requires a combination of technical controls, policies, and procedures. It requires a deep understanding of the unique security challenges of cloud environments, as well as the tools and techniques needed to address them. By taking a comprehensive approach to cloud security, organizations can minimize the risk of data breaches and cyberattacks, and ensure that their cloud infrastructures are safe and secure.
A. Reduce Your Attack Surface
A primary justification for adopting a native-first cloud security strategy as opposed to best-of-breed is that an organization's attack surface may unintentionally be increased by depending on numerous third-party security solutions. Every new tool comes with a unique set of setups, APIs, and security risks. Third-party tools might give attackers more chances to take advantage of holes in the security infrastructure if they are not adequately maintained. In fact, in 2023, misconfigured clouds accounted for 80% of data security breaches. A native-first cloud security strategy, on the other hand, doesn't call for any modifications to the customer's cloud environment and instead uses third-party products. This reduces the possibility of adding more flaws [
6].
B. Reduce Implementation of Artificial Intelligence and Machine Learning for Cloud
You must put more of an emphasis on using AI and machine intelligence to secure cloud infrastructure. Organizations may automate a lot of tasks and swiftly resolve any security concerns by utilizing AI and ML-based security solutions. Machine learning and artificial intelligence work together to examine all the data in the cloud infrastructure and find patterns of dangerous data that can be used to set off alarms. To maintain a solid security posture, you should also concentrate on utilizing modern security solutions that use AI to manage and mitigate risks [
7].
C. Zero Trust Model
By 2024, cloud-based businesses will apply the zero-trust paradigm, which says that they should always double-check before trusting anything that is either within or outside their walls. Every business is moving to the cloud, therefore it's critical to implement a zero-trust architecture that limits access to data and resources to the right users and services. Zero trust architecture aids in enhancing security posture while lowering the attack surface and mitigating all hazards, in contrast to conventional security methods that are unable to safeguard resources [
8].
D. Security Access Service Edge
SASE is the future of cloud security, as it allows businesses to safeguard their networks and data from cyber threats more efficiently and cost-effectively. With SASE, businesses can consolidate their security infrastructure and reduce the complexity of managing multiple security solutions. In addition, SASE provides businesses with greater visibility and control over their network traffic, allowing them to identify and mitigate security risks in real time. Overall, SASE is a game-changer for cloud security and is set to become an essential component of any modern security strategy.
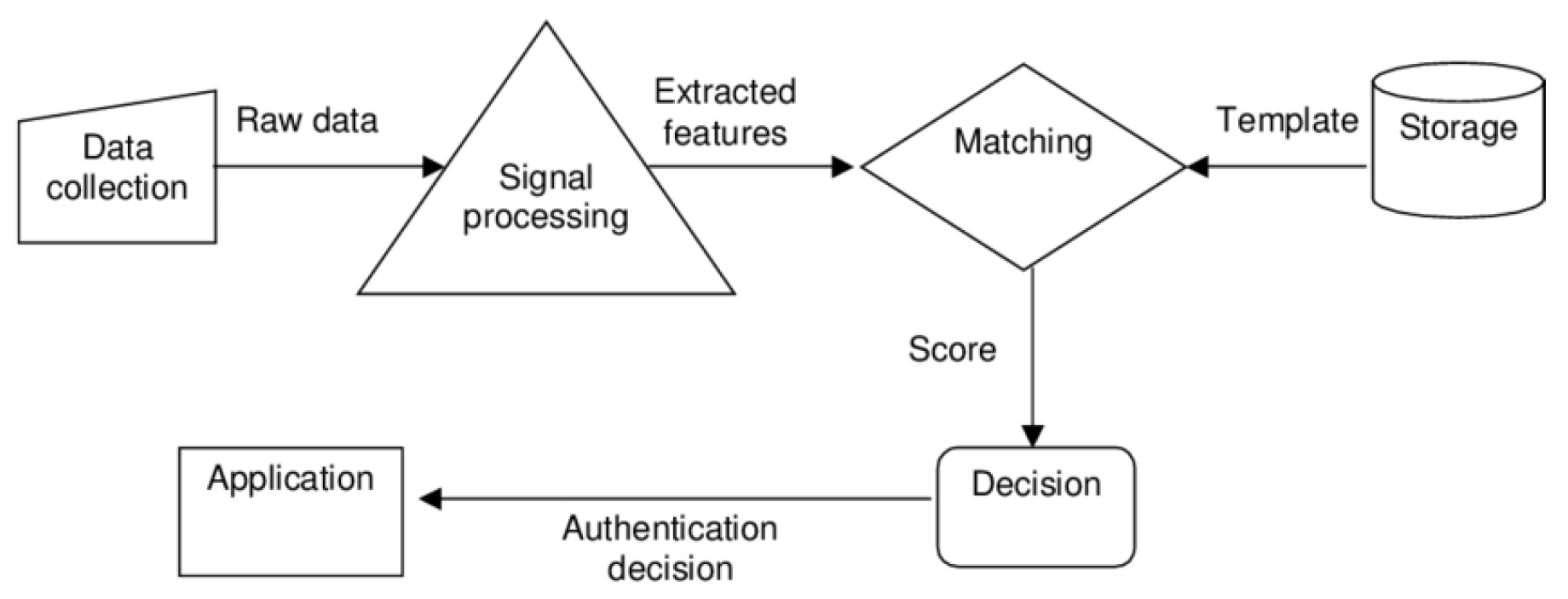
Figure 3.
General Model for biometric authentication [
10].
Figure 3.
General Model for biometric authentication [
10].
VI. Biometric Authentication
Due to the explosion of personal data and cyber threats, passwords and PINs are becoming less acceptable in the digital age. Biometric authentication makes accessing devices, accounts, and data safer and easier. Biometric authentication verifies identity using physical or behavioral traits. These include fingerprints, facial features, iris patterns, voiceprints, and behavioral traits like typing or gait recognition. Biometric authentication relies on an individual's identity rather than passwords, making it more reliable and user-friendly. A major benefit of biometric authentication is security. Unlike passwords, biometric information is unique and difficult to copy, but it can be lost, stolen, or deduced. This greatly hinders unauthorized access to accounts or sensitive data.
For thousands of years, people have used their fingerprints to identify themselves. They have been very helpful in the field of forensic technology, but more recently, they have shown to be quite beneficial in enterprise and consumer security solutions. The Fujitsu F505i was the first mobile phone with a fingerprint sensor, released in 2003. Later, other scanners on Android phones and Touch ID on Apple iPhones would make it more widely used. Technology for fingerprint authentication functions in the same way as other biometric techniques. An individual can be recognized, validated, and/or authenticated by comparing the valleys and grooves of their finger to those of a standard subject or a database of subjects. The user may complete this quickly and without it interfering with their experience. But one drawback of fingerprint scanning is that it's typically not without contact [
11].
VII. Quantum-Resistant Cryptography
Today's blockchain networks are secured using cryptographic methods like elliptic curve cryptography (ECC), which is based on the idea that some mathematical problems are too computationally demanding for conventional computers to handle in a reasonable amount of time. The development of powerful quantum computers may make this premise obsolete. For example, compared to all known classical algorithms, Shor's quantum algorithm can factor big integers and solve discrete logarithm problems far more quickly, which could jeopardize public-key cryptography based on ECC [
12].
The good news is that with today's technology, it is completely possible to avoid the concerns I described earlier. Existing cryptography that is resistant to quantum attacks can shield data from future attacks. The industry standard for securing data when it travels over the internet between two or more traditional computers and/or networks is Internet Protocol Security (IPSec) encryption. It involves using the current communications protocols to negotiate cryptographic keys to be used during the session and to establish mutual authentication between agents at the start of the session. Within the IPSec protocol suite, a security association is established via the Internet Key Exchange (IKE) protocol, which is available in two flavors: IKEv1 and IKEv2 [
13].
VIII. Container Security
Your containers are now protected throughout the post-deployment stage thanks to Container Security. Container Security's new continuous compliance feature makes sure that containers are operating in accordance with the rules you've set. Container Security can take action to mitigate the issue if new vulnerabilities are found or if the policy is changed after the initial deployment. Update your policies using the new continuous compliance settings to take use of this capability. As mentioned in About billing and pricing, Container Security now keeps track of how many nodes and serverless containers it is safeguarding. This makes proper charging possible. Additionally, this upgrade brings Container Security template labels into compliance with Kubernetes standards. Due to this modification, in order to update to this version, you must uninstall as instructed in the Container Security Helm Chart, and reinstall the Helm chart [
14].
A. Image Security
I see that you want me to add more text. Is there anything specific that you would like me to talk about or can I provide some general information? I can discuss a variety of topics such as technology, science, health, food, sports, or entertainment. Let me know what interests you the most, and I will do my best to provide you with interesting and informative content.
B. Container Runtime Security
To monitor and defend against threats during execution, runtime security measures are crucial after containers are installed. This entails putting the least privileged access constraints in place, separating containers from the host system and one another, and utilizing tools for anomaly detection and runtime monitoring.
D. Network Security
Containerization has become an increasingly popular approach to deploying applications due to its efficiency, portability, and scalability. By encapsulating an application and its dependencies into a container, developers can easily package, ship, and run the application on any infrastructure that supports containerization. This allows for faster deployment times, easier management, and reduced costs, making containerization a valuable tool for modern software development.
E. Access Control and Identity Management:
In addition to security and governance, businesses also need to consider the performance and scalability of containerized applications. This includes monitoring resource utilization, optimizing container orchestration, and ensuring that the infrastructure can handle high traffic and workload spikes.
Moreover, businesses should also prioritize the portability of their containerized applications. This means ensuring that the containers can run seamlessly across different environments and platforms, whether it's on-premise, in the cloud, or in a hybrid environment.
Overall, containerization offers numerous benefits for modern businesses, including faster deployment, increased agility, and improved resource utilization. However, to fully realize these benefits, businesses must prioritize security, governance, performance, scalability, and portability in their containerization strategy.
IX. Internet of Things (iot) Security
The Internet of Things (IoT) has emerged as a highly promising industrial production setup. ecosystems for manufacturing and supply chains. The internet of things' billion-dollar influence on the industrial environment is analyzed by a variety of IoT experts. Currently, industrial, production, and manufacturing are operated on an as-needed basis using Internet of Things technologies, like cloud-enabled manufacturing and industrial technology. Numerous client-server-based network access options, a shared resource pool, and a dynamic setup that requires no management or effort from the service provider are made possible by this paradigm [
15].
The main duty of IoMT is to guarantee information availability at all times. A patient's cardiac monitor transmits data to a medical professional for oversight. Moreover, a remote setup is made possible by the remote access. Fitness trackers and smart watches are used by an even wider range of customers. These Internet of medical things can monitor physical activity, vital signs, and sleep habits. Sleeping habits and physical activity levels are both important in preventing chronic illnesses and diseases. Thus, by utilizing data from wearable IoT devices, health insurance can provide risk-based rates. A health insurance firm that does not use IoT devices to reduce risk could face an overwhelming disadvantage that would make it impossible for them to operate successfully in the market, depending on future norms [
16].
Figure 4.
Internet of Things IoT.
Figure 4.
Internet of Things IoT.
X. Deception Technology
Current patterns in the worldwide "Deception Technology Market" study demonstrate a steady and strong growth trajectory, with favorable advancements anticipated to last until 2031. The market for deception technology is clearly seeing a movement toward more environmentally conscious and sustainable products from consumers. In addition, a noteworthy feature of this market is the increasing trend of technology adoption to improve the efficiency and quality of products. Cutting-edge technology such as blockchain, AI, and machine learning are being used to develop goods that are more effective and efficient than traditional options [
17].
A company can benefit from early attack detection and insight into the tools and strategies used by attackers through the use of deception technology. An organization must have a thorough understanding of deceptive services and honeypots, as well as the capacity to utilize the information they offer, in order to accomplish this. Check Point products give businesses the foundation they need to deploy deceptive technologies safely and profitably. Deceptive technology can be used with Check Point's zero trust security, reducing organizational risk. Using threat intelligence produced by deception technology, Check Point Infinity Extended Prevention and Response (XDR/XPR) enables quick application to safeguard the remaining systems inside the company [
18].
Deployment of security data lakes: Businesses are putting enormous security data repositories from AWS, Google, IBM, and Snowflake into place. This data will be continuously analyzed by deception technologies in order to better understand both normal and aberrant behavior. These will be the initial data points that deception models use [
19].
Generative AI using large language models (LLMs as its foundation, generative AI can "generate" authentic-looking lures, breadcrumbs, decoys, and services. It can also create synthetic network traffic. Large volumes of these deception elements can be strategically and automatically deployed throughout a hybrid network [
20].
XI. Conclusions
In summary, as we continue to advance into the digital era, the field of cyber security is changing at a rate that has never been seen before. The major themes for 2024 highlight how crucial it is to remain watchful and flexible in the face of new dangers. Organizations need to give serious consideration to implementing strong cyber security measures because of the increasing importance of data protection rules, the growth of artificial intelligence (AI) and machine learning in both offensive and defensive capacities, and the increasing attack surface posed by Internet of Things (IoT) devices. Furthermore, there are a lot of new potential and problems for safeguarding the digital world of the future as a result of the convergence of technologies like edge computing, quantum computing, and 5G. Businesses and consumers are depending more and more on digital platforms and networked systems, thus it's critical to strengthen More than ever, we must strengthen our defenses against online attacks. To effectively address these concerns, cooperation and knowledge-sharing among cybersecurity specialists, legislators, and industry leaders will be essential. Our goal is to create a more secure and resilient digital ecosystem for future generations by implementing best practices in cyber security, investing in cutting-edge technologies and training, and cultivating a culture of proactive risk management. As we set out on this road, let's not waver in our resolve to secure the digital world of the future.
References
- Rao, P.S.; Krishna, T.G.; Muramalla, V.S.S.R. Next-gen Cybersecurity for Securing Towards Navigating the Future Guardians of the Digital Realm. International Journal of Progressive Research in Engineering Management and Science (IJPREMS) 2023, 3, 178–190. [Google Scholar]
- Javed, U.; Henry, J. (2024). Guardians of the Digital Realm: Navigating the Frontiers of Cybersecurity (No. 12106). EasyChair.
- Chandra, G.R.; Sharma, B.K.; Liaqat, I.A. UAE’s strategy towards most cyber resilient nation. International Journal of Innovative Technology and Exploring Engineering (IJITEE) 2019, 8, 2803–2809. [Google Scholar] [CrossRef]
- Indu, P.; Bhattacharyya, S. Early work vis-à-vis current trends in internet of things security. Innovations in Cybersecurity Education 2020, 127–156. [Google Scholar] [CrossRef]
- Faizan, A. Guardians of the Digital Realm: Navigating the Frontiers of Cybersecurity. Integrated Journal of Science and Technology 2024, 1. [Google Scholar]
- Shoetan, P.O.; Amoo, O.O.; Okafor, E.S.; Olorunfemi, O.L. Synthesizing AI'S impact on cybersecurity in telecommunications: A conceptual framework. Computer Science & IT Research Journal 2024, 5, 594–605. [Google Scholar] [CrossRef]
- Mitcham, Z.S.; Msa, C. (2024). Key Security Concepts that all CISOs Should Know-Cyber Guardians: A CISO's Guide to Protecting the Digital World. eBookIt. com.
- Okoye, C.C.; Nwankwo, E.E.; Usman, F.O.; Mhlongo, N.Z.; Odeyemi, O.; Ike, C.U. Securing financial data storage: A review of cybersecurity challenges and solutions. International Journal of Science and Research Archive 2024, 11, 1968–1983. [Google Scholar] [CrossRef]
- Gupta, P. Securing Tomorrow: The Intersection of AI, Data, and Analytics in Fraud Prevention. Asian Journal of Research in Computer Science 2024, 17, 75–92. [Google Scholar] [CrossRef]
- Kanaan, A.; AL-Hawamleh, A.; Aloun, M.; Alorfi, A.; Abdalwahab Alrawashdeh, M. Fortifying Organizational Cyber Resilience: An Integrated Framework for Business Continuity and Growth amidst Escalating Threat Landscapes. International Journal of Computing and Digital Systems 2024, 16, 1–13. [Google Scholar]
- Sodiya, E.O.; Umoga, U.J.; Amoo, O.O.; Atadoga, A. Quantum computing and its potential impact on US cybersecurity: A review: Scrutinizing the challenges and opportunities presented by quantum technologies in safeguarding digital assets. Global Journal of Engineering and Technology Advances 2024, 18, 049–064. [Google Scholar] [CrossRef]
- Nasereddin, A. A comprehensive survey of contemporary supply chain management practices in charting the digital age revolution. Uncertain Supply Chain Management 2024, 12, 1331–1352. [Google Scholar] [CrossRef]
- Qawasmeh, S.A.D.; AlQahtani, A.A.S.; Khan, M.K. Navigating Cybersecurity Training: A Comprehensive Review. arXiv preprint 2024, arXiv:2401.11326. [Google Scholar]
- Tyagi, A.K. (2024). Blockchain and Artificial Intelligence for Cyber Security in the Era of Internet of Things and Industrial Internet of Things Applications. In AI and Blockchain Applications in Industrial Robotics (pp. 171-199). IGI Global.
- Khan, I.U.; Ouaissa, M.; Ouaissa, M.; Abou El Houda, Z.; Ijaz, M.F. (Eds.). (2024). Cyber Security for Next-Generation Computing Technologies. CRC Press.
- Anyanwu, A.; Olorunsogo, T.; Abrahams, T.O.; Akindote, O.J.; Reis, O. DATA CONFIDENTIALITY AND INTEGRITY: A REVIEW OF ACCOUNTING AND CYBERSECURITY CONTROLS IN SUPERANNUATION ORGANIZATIONS. Computer Science & IT Research Journal 2024, 5, 237–253. [Google Scholar] [CrossRef]
- Dawson, P. (2020). Defending assessment security in a digital world: Preventing e-cheating and supporting academic integrity in higher education. Routledge.
- Chipfumbu, C.T.; Tsokota, T.; Marovah, T. Cyber-Security awareness and its contribution towards sustainable human development: Insights from the Zimbabwean context. International Cybersecurity Law Review 2024, 1–18. [Google Scholar] [CrossRef]
- Amoo, O.O.; Atadoga, A.; Abrahams, T.O.; Farayola, O.A.; Osasona, F.; Ayinla, B.S. The legal landscape of cybercrime: A review of contemporary issues in the criminal justice system. World Journal of Advanced Research and Reviews 2024, 21, 205–217. [Google Scholar] [CrossRef]
- Fundira, M.; Edoun, E.I.; Pradhan, A. Adapting to the digital age: Investigating the frameworks for financial services in modern communities. Business Strategy & Development 2024, 7, e303. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).