1. Introduction
Within the field of design studies, the development of AI drawing software has attracted a great deal of attention. Not only does AI drawing software offer new possibilities for artistic creativity, it also fulfils important roles in the process of design. Through advanced techniques such as Generative Adversarial Networks (GAN), these software can automatically generate photorealistic images and artworks in a variety of forms, including landscapes, people, and abstract art. This functionality allows designers to create art more easily, and it also brings new thinking and challenges to the development and practice of design studies. The AI painting software based on generative adversarial networks is a group of image generation tools that utilise deep learning techniques. These tools enable automatic image generation by training two neural network models containing generator and discriminator [
3]. There has been a significant development in recent years in the technology and applications of ai painting software based on generative adversarial networks. The present researchers have investigated four dimensions of AI painting software based on Generative Adversarial Networks, which are functionality, ease of use, system performance, and security of the software. For example, Qiu, Yungen, Cao, et al. suggested that the relevant institutions should charge royalties for all the use of a particular AI ‘creation’ and distribute them to the relevant people [
4]. Hu Yin investigated the functionality of the software that designed an AIGC cue card to quickly place predefined keywords during the text-to-image process so that creators could quickly generate the desired design through Midjourney [
5]. Nervana Osama Hanafy studied the ease of use of the software. It was found that the AI drawing software using MidJourney fell short in its ease of use, and its interface was more complex and reliant on precise keywords [
6]; Zhang Bin and Zhou Yuechuan et al. investigated the system performance of software and pointed out that the difficulty of GAN lies in the crashing problem of software [
7].
Besides, there are some problems in the current study. For example, there is a lack of some important functions in terms of functionality, while in terms of ease of use, the coherence of the interface content has not been sufficiently considered, resulting in an inadequate overall experience of the software. If these issues are not addressed, it will negatively impact the development of AI painting software based on generative adversarial network techniques. However, few software can fully satisfy the requirements of the four aspects of functionality, ease of use, system performance and security. Therefore, it is necessary to introduce new ideas to solve the above problems.
The objectives of this study are:
(1) To optimise the AI painting software based on generative adversarial network technology in terms of functionality, ease of use, system performance and security, so as to make it more rich in functionality, more convenient in operation, more stable in performance and more reliable in security.
(2) To establish an evaluation system for AI painting software based on generative adversarial network technology to ensure that the software can fully integrate the four requirements of functionality, ease of use, system performance and security.
(3) To rank the functionality, ease of use, system performance and security of the software in order of importance through further research, which will help companies to invest more R&D time in the more important aspects.
2. LITERATURE REVIEW
2.1. Early studies on AI drawing software
AI painting software in the earlier times used an example of an image generation model based on a self-encoder mechanism. In 1986, Rumelhart et al first introduced the concept of AutoEncoder (AE) [
8]. Kingma et al introduced the Variational Auto-Encoders (VAE) [
9]. Vincent et al introduced a degradation process based on AE that proposed Denoising AutoEncoders (DAEs) which are designed to be more robust in terms of the extracted features by ameliorating the effect of noise [
10]. Aaron et al suggested Vector Quantized Variational Autoencoder (VQ-VAE) [
11]. It is advantageous that models for image generation based on self-encoder structures have no need for labelled data, only the input image, and can improve the quality of reconstruction, and robustness or diversity of implied representations. Weakness is that they do not guarantee the continuity and interpretability of the implicit representation.
2.2. Current status of AI drawing software
There are a number of highly regarded AI painting software such as DALL-E 2, Midjourney and Stable Diffusion that are widely known and influential in the field of artistic creativity. DALL-E 2 by OpenAI developed AI painting software based on GAN technology. Radford, Alec showed that DALL-E 2 can generate graphics from written descriptions by integrating naturally linguistic processing and computer vision algorithms [
12].A. Ramesh studied that DALL-E 2 has a very simple interface with great ease of use, which allows people with little or no expertise in AI techniques that can quickly and easily make beautiful photographs [
13];O'Meara noted that Dall-E 2 was highly artistic in creating surrealist works that were [
14];There are, however, problems with gender stereotyping in Dall-E 2 as noted by Garcia-Ull [
15]. This shows that the software has both advantages and disadvantages in terms of functionality. Midjourney which is a GAN-based AI mapping software that generates images based on text, was developed by the Midjourney Laboratory in San Francisco, California, USA which entered public beta testing on 12 July 2022. Liu, Vivaian pointed out that MidJourney is widely used to help designers and artists with quickly outlining concepts that can help people with visual impairments understand typographic content [
16].Sukkar, Ahmad W. indicated that Midjourney has undertaken many explorations in the functionality of the software [
17]. For example, users can use this software that easily generates highly realistic Islamic architecture, whether it's a grandiose complex or a beautifully detailed example of a fascinating old city, from famous mosques to ornate palaces, all of which are perfectly reproduced in this software. Moreover, Zhang, Yanbo pointed out that when using the software, users need to enter precise keywords into the programme, together with a series of complicated operating steps, in order to generate a picture that meets the user's needs [
18]. This shows that the ease of use of the software needs to be improved; Stable Diffusion which is an AI painting software developed by startups Stability AI, CompVis and Runway. Although it uses a diffusion model rather than GAN technology, it is still a useful guide for the development of AI painting software based on Generative Adversarial Network technology. Zeyu Zhang showed that Stable Diffusion has better security [
19]. The software adds an NSFW filter from LAION, which filters out pornographic content while protecting the copyrights of human artists. Stabilised diffusion is likely to leave much to be desired in terms of system performance as it requires longer sampling times and more complex optimisation, which potentially leads to inefficiencies or instability. In summary, there are advantages and disadvantages of the current AI painting software based on generative adversarial network technology in terms of functionality, ease of use, system performance and security. During the optimisation of software, we not only need to improve functionality, ease of use, system performance and security, but also be good at integrating the strengths of all aspects. Furthermore, we can incorporate the best of various types of software on the market in order to enhance the user experience and the comprehensive performance of the system.This not only makes full use of existing resources, but also avoids the shortcomings of the software on the market, thereby providing users with a more complete solution.
3. RESEARCH DESIGN AND METHOD
3.1. Introduction to the theory
3.1.1. Generating Adversarial Networks
Generative Adversarial Network(GAN) is that an implicit density generation model based on the direct approach, whose key structures are a generator G and a discriminator D: G is responsible for randomly sampling from the noisy distribution of the input data, while D is responsible for recognising and judging the authenticity of the samples generated by G, in conjunction with the real data. GANs contain various variants such as conditioned generative adversarial networks, deep convolutional generative adversarial networks, semi-supervised generative adversarial networks, informative generative adversarial networks, etc. [
20]. The future research direction of GAN should focus on replacing traditional GAN with CGAN models, solving the semi-supervised learning problem [
21], improving the training efficiency of GAN, and exploring the possibility of combining GAN with other models [
22].
3.1.2. AI drawing software
The AI painting software is a tool that utilises artificial intelligence techniques to automatically generate realistic images and artworks, including landscapes, people and abstract art . Through technologies such as Generative Adversarial Networks (GAN), Variational Auto-Encoder (VAE), and Neural Style Migration, users can mimic the styles of famous artists, preview and adapt their works in real time, which plays an important role in the fields of creative design, education and learning, entertainment and social interaction. In contrast to traditional computer art tools, AI painting software focuses more on computer intelligence or autonomy [
23]. There is a wide variety of these AI painting software such as Midjourney, Stable Diffusion, and DALL-E 2 with Disco Diffusion based on the Discord community [
24]. With the continuous emergence and rapid updating of new AI drawing software, the progress of the software exhibits a dramatic growth. This phenomenon has triggered a wide-ranging discussion about the potential that AI has shown in the field of art creation [
25].
3.1.3. Evaluation system
An evaluation system is a set of indicators containing rules for assessing, measuring or comparing things or behaviours. It usually consists of multi-level indicators, from the whole to the details, which are used to assess various aspects or characteristics of an object and provide a quantitative or qualitative evaluation of it. The construction of the evaluation system involves synthesising the data processing results of the multi-round consultation questionnaires and the suggestions made by the experts, modifying the initially established evaluation indicators, which subsequently leads to the formation of a sound system of evaluation indicators [
26]. This process of questionnaire is usually carried out on the grounds of literature analysis, taking into account the attributes of the subject in the study, through the initial formulation of the evaluation indicators and the use of back-to-back correspondence between experts which ensures the independence of their opinions [
27]. Scholars usually construct the evaluation model and design the index of evaluation system by means of the Delphi method, and then use the hierarchical analysis method to determine the weights of the evaluation indexes of IT the quality of service [
28]. For example, when constructing an evaluation system for information security, the guideline layer can be divided into five parts: hardware security, information security, software security, management security and environmental security. While for the evaluation system of creative open data competition works, the first-level indicators are set as information content, functional design, interface design, system performance, open data development and utilisation, and the degree of compliance with the competition rules [
29]. Zhao et al. pointed out that for the evaluation of creative competition entries, they have the following first-level indicators: information content, functional design, interface design, system performance, data development, competition rules, etc. [
30].The design of such an evaluation system can reflect the characteristics and quality requirements of the evaluation object more comprehensively and improve the accuracy and credibility of the evaluation.
3.2. Research architecture
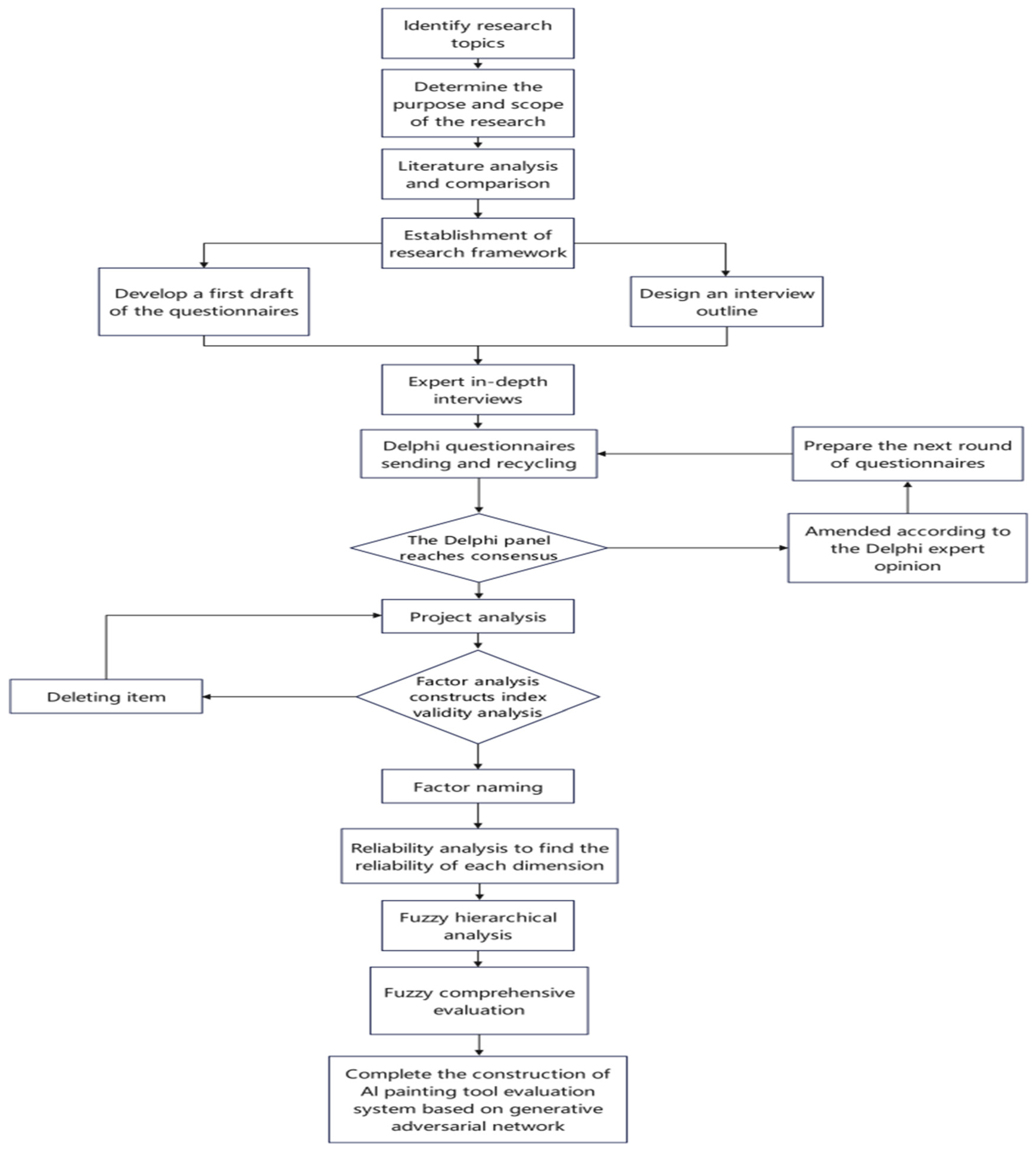
This study aims to construct an evaluation system for AI painting software based on Generative Adversarial Networks. The subjects of the study included three executives of domestic AI technology companies and five full-time professors in the department of computer science of undergraduate colleges and universities. Based on relevant theories, researches and literature, the questionnaire was constructed in a qualitative and quantitative parallel approach, including conducting individual in-depth interviews with experts, Delphi questionnaire survey method, and exploratory factor analysis method. the architecture of the questionnaire is shown in
Figure 1. Following a discussion with the supervising professor, a research topic was identified. Various types of literature related to generative adversarial networks and AI painting software were summarised. To understand the function of AI drawing software, The characteristics and elements of Generative Adversarial Networks were used to form the basis for the first draft of the Delphi questionnaire and the outline of the interviews, and then development of the Delphi questionnaire for Round 1.As mentioned above, the results of the evaluation and comments on each of the items for the first round of questionnaires were analyzed which resulted in the second round of questionnaires. The questionnaire of this study was based on a Likert scale, with ‘1’ denoting ‘very unimportant’, ‘2’ denoting ‘unimportant’, ‘3’ denoting ‘not necessarily’, ‘4’ denoting ‘important’, and ‘5’ denoting ‘very important’, and ‘5’ denoting ‘very important’, and ‘5’ denoting ‘very important’. The degree of authority of the experts was used to assess the professionalism of the experts, which was represented by the authority coefficient Cr, Cr = (Ca + Cs) / 2, where Ca indicates the basis of judgement when experts score, and Cs indicates the familiarity of the experts with the issue. The quantitative scale of the basis of judgment and the familiarity are shown in
Table 1. Coefficient of authority Cr between 0 and 1, Cr ≥ 0.7, indicating that the results of the expert opinion is reliable; Cr> 0.8, indicating that the experts have a greater grasp of the choice of content. The judgement of the degree of authority of experts is based on self-evaluation. In this study, the authority coefficient of expert opinion is 0.81, which indicates that the results are highly reliable. Further, it was confirmed by exploratory factor analysis and reliability test that each of the three-level indicators had met the criteria for retention in this study, whereby the evaluation system of ai painting software based on generative adversarial network was constructed. Finally, through the fuzzy hierarchical analysis and fuzzy comprehensive evaluation method, the weight and importance of each index are calculated. Further, it was confirmed by exploratory factor analysis and reliability test that each of the three-level indicators had met the criteria for retention in this study, whereby the evaluation system of ai painting software based on generative adversarial network was constructed. Finally, through the fuzzy hierarchical analysis and fuzzy comprehensive evaluation method, the weight and importance of each index are calculated.
3.3. Implementing procedures
The implementation procedure for the establishment of the indicators in this study is shown in
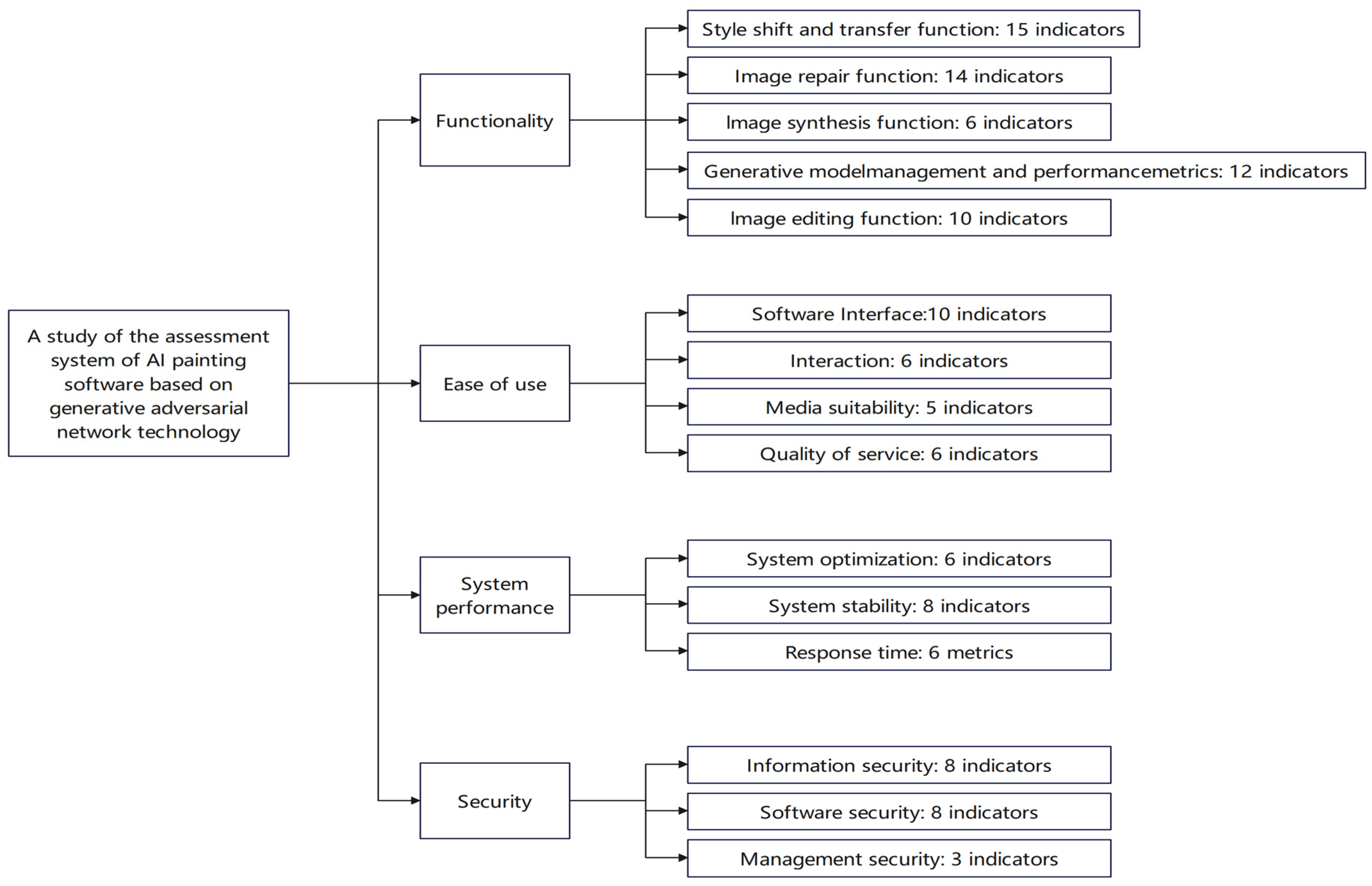
Figure 2, which is summarized.Through literature collection and in-depth interviews with three experts, the results of the interviews were organized and analyzed. The information of the questionnaire was extracted and modified according to the suggestions of the supervising professors in order to fulfill the first round of the Delphi questionnaire. The Delphi Expert Panel consisted of 8 experts, including 3 executives from domestic AI technology companies and 5 full-time faculty members from computer science departments of undergraduate colleges and universities, who revised the Delphi questionnaire 2 times before distributing the first round of Delphi questionnaires. In response to the environmental protection and energy saving, the researcher used an email for the electronic questionnaire which was sent to each expert. Delphi questionnaires for Round 1 were mailed on August 31st with collections done on September 23rd. Round 2 Delphi questionnaires were mailed on October 1st to be collected on October 31st.There are 123 indicators in 4 dimensions of ai painting software based on generative adversarial network, including 57 indicators in functional dimension, 27 indicators in ease of use dimension, 20 indicators in system performance dimension and 19 indicators in safety dimension.
3.4. Implementing procedures
In this study, the results of the second questionnaire were analyzed using factor analysis, and exploratory factor analysis was implemented to screen the items, while principal component analysis was chosen to delete the items with low explanatory strength, and to extract the common factors. Thus, a reduction in the number of variables was achieved. The criteria for deleting items include: items with factor loadings less than 0.5; items covering two common factors; items containing less than two items and items with low reliability, which are all deleted; That is, the large number of variables is reduced to a smaller number of components and the smaller loadings are eliminated, while the distribution and accumulation of loadings for each latent common factor is understood; The maximum variance method was chosen to simplify the factor loading matrix, which allows us to understand the distribution and accumulation of variances for each factor, while allowing us to understand the correlation between individual items and the factors. This allowed us to assess the strength of the individual items using the Cronbach's alpha coefficient that is used to analyze the internal consistency of the dimensions. In short, the Delphi method is used to explore the opinions of experts on the evaluation indexes of AI drawing software based on generative adversarial network. Therefore, the evaluation system based on generative adversarial network can be established for the ai painting software in this study.
3.5. Fuzzy Hierarchy Analysis
3.5.1. To establish the complementary judgment matrix
We invite professionals to quantify the relative importance of the indicators at each level based on the scale of 0.1 to 0.9 as shown in
Table 2. On the basis of the obtained scale value of each indicator, the complementary judgment matrix R of the next level relative to the previous level is constructed R:
In Eq. (1), the matrix R consists of the rij composition, rij is the ith row and jth column scale values and satisfies the conditions: 0≤rij≤1, rij + rji =1, rii=0.5, i, j=1, 2,..,n.
3.5.2. Determining the weights of complementary judgment matrices
Let(i=1, 2, ... , n) be the sum of the nth row of the judgment matrix in the dimension layer. (i=1, 2,... , n) (j=1, 2, ... , m) is the sum of the mth row of the nth judgment matrix in the criterion layer.
Let(i=1, 2,... , n) be the nth weight for indicator for primary layer , (j=1,2,...,m) is the mth weight for secondary layer in the nth primary indicator.
There are more than 10 methods for calculating the weights of fuzzy judgment matrices, and the use of equations 2-3 demonstrated in the literature [
31] can reduce the amount of calculation while obtaining reasonable and effective results. Subsequently,
and
are obtained according to equations 2-3.
Let W1 be the vector of primary indicator weights, be the vector of secondary indicator weights., .
Finally, a consistency test was performed on the complementary judgment matrix. The consistency test helps to confirm that the expert's judgments are consistent when comparing the factors in pairs. For example, if the expert believes that A is more important than B and that B is more important than C, it is reasonable that A should be more important than C. In this study, if the difference between any row and the corresponding indicator data of other rows is the same constant then it is a consistency matrix, i.e., it passes the consistency test.
3.6. Calculation of fuzzy integrated evaluation
Fuzzy Comprehensive Evaluation (FCE) is a comprehensive evaluation method based on fuzzy mathematics. which transforms qualitative into quantitative evaluation according to the membership theory of fuzzy mathematics, that is, using fuzzy mathematics to make an overall evaluation of things or objects limited by multiple factors. It has the characteristics of clear results and strong systematicity, which is suitable for the evaluation of various multi-level and multi-factor uncertainty problems, such as the optimization of the program and the selection of important factors of influence on the project. For a complex system, there are often a large number of factors affecting the system, each of which has a different level of hierarchy. It is difficult to solve the problem by using simple evaluation to get reasonable judgment results, therefore, multilevel fuzzy comprehensive evaluation is proposed; Fuzzy comprehensive evaluation involves utilizing the principle of fuzzy linear transformation and the principle of maximum membership to make a reasonable comprehensive evaluation of the objects to be evaluated by taking into account the various factors related to them. As a rule, multi-layer fuzzy comprehensive evaluation was carried out on the basis of fuzzy comprehensive evaluation. It can also be used repeatedly as many times as needed. The architecture of this system includes objective hierarchies, conformation hierarchies and criterion hierarchies. The detailed processing steps of this system are as follows:
3.6.1. Establishment of indicator set
The indicator set is a collection of n indicators that affect the object of assessment, denoted by U, i.e. U = ( u1, u2, …, un).
3.6.2. Establish the evaluation set
An evaluation set is a collection of q possible evaluation results made by a reviewer who assesses an object, usually denoted by V, i.e. V=(v1, v2, …, vq).
3.6.3. Determining the vector of weights for primary and secondary indicators to establish the complementary judgment matrix
Since the measure of the degree of influence of each indicator on the assessment of things is not similar, some indicators may have a greater degree of influence in the total evaluation, while others may be smaller, therefore, the weight of each indicator in the total evaluation must be given when making a synthesized evaluation and form a vector of weights. In this study, the fuzzy hierarchical analysis method is used to obtain the weight vector of first-level indicators W1 and the weight vector of second-level indicators .
3.6.4. The construction of a fuzzy evaluation matrix
Based on the opinions of experts or evaluators, the indicators are scored using fuzzy language, which is then converted into fuzzy numbers to form a fuzzy evaluation matrix Ri , expressed as follows:
where
denotes the menbership function of the nth factor corresponding to the mth evaluation level.
3.6.5. Deriving the matrix of fuzzy integrated evaluation
(i=1,2,...,n)is the second level fuzzy integrated evaluation matrix and B1 is the first level fuzzy integrated evaluation matrix.
The weight vector
is subjected to fuzzy operation with the fuzzy evaluation matrix R
i which yields
, expressed as follows:
The weight vector W
1 consisting of
and the weights of the first-level indicators is subjected to the synthesis operation of the fuzzy matrix that gives B
1, which is expressed as follows:
3.6.6. Calculation of the scoring results
The weighted average method was used to carry out the calculations, which were carried out as follows:
where b
j is the jth value in the fuzzy comprehensive evaluation matrix (
,
, ...,
)and(
,
, ...,
) , v
j is the jth value in the evaluation set V, and q represents the number of evaluation factors in the evaluation set.
4. RESULTS AND DISCUSSION
4.1. Research results
4.1.1. Establishment of integrated evaluation system
As shown in
Table 3, a total of 76 indicators were deleted and 47 were retained by applying principal component analysis in factor analysis in order to reduce the indicators.The four subscales include 16 indicators in the "functionality" dimension with an alpha coefficient of 0.912, 16 indicators in the "ease of use" dimension with an alpha coefficient of 0.923, 7 indicators in the "system performance" dimension with an alpha coefficient of 0.931, and 8 indicators in the "safety" dimension with an alpha coefficient of 0.929. The alpha coefficients of the four subscales are all above 0.80, and the alpha coefficient of the whole scale is as high as 0.952, which shows a high degree of reliability.The results of factor analysis are shown in
Table 4 and
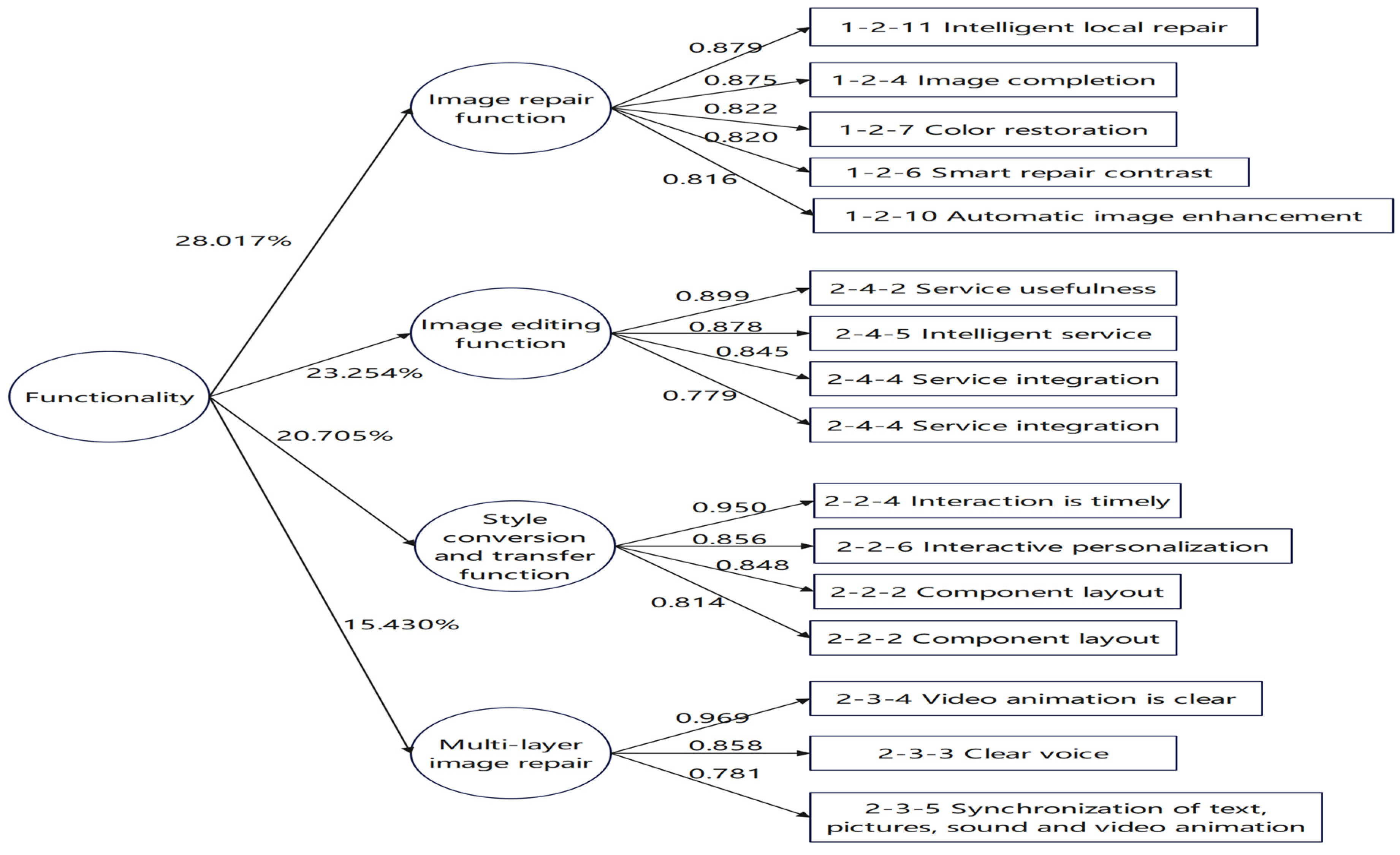
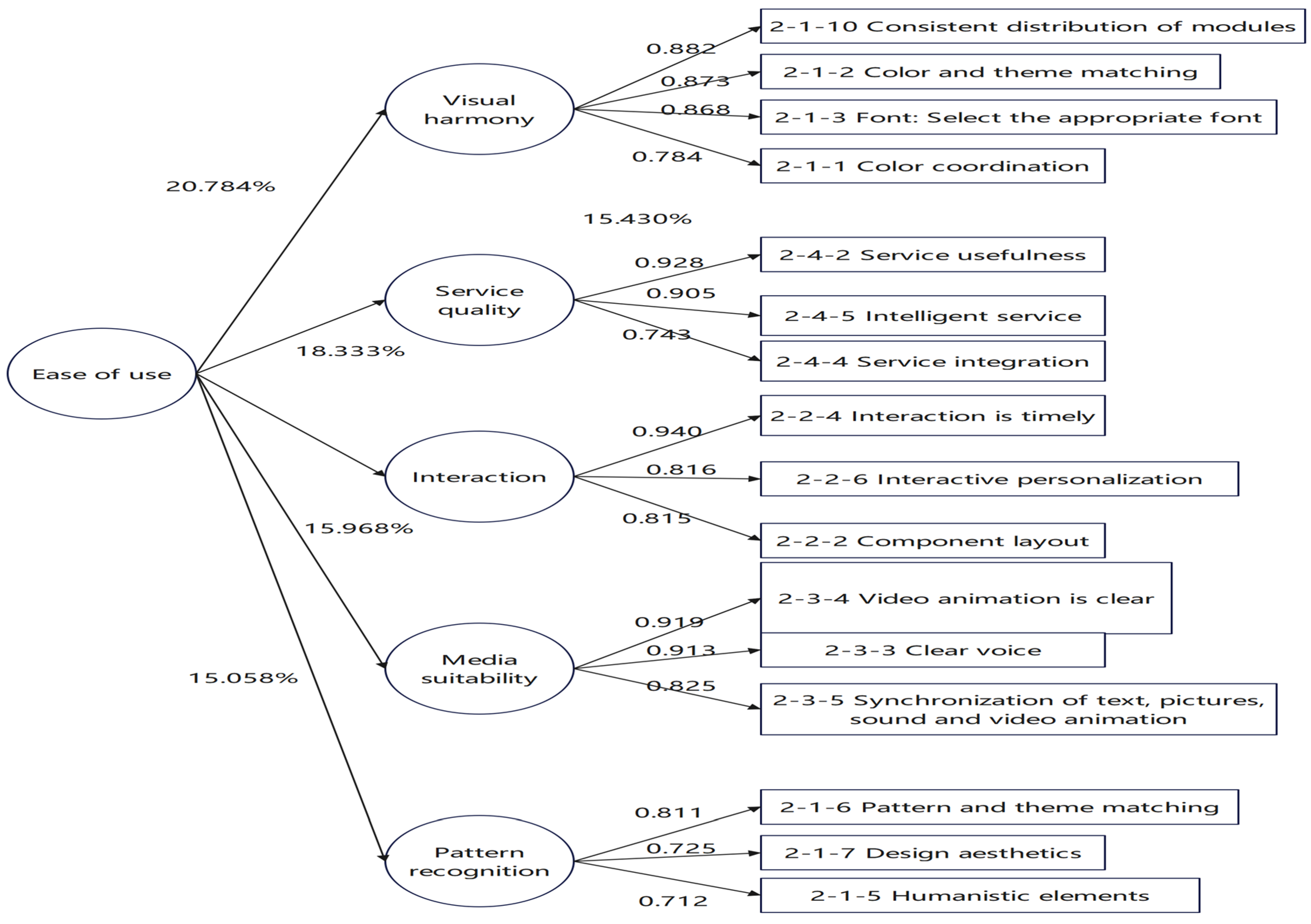
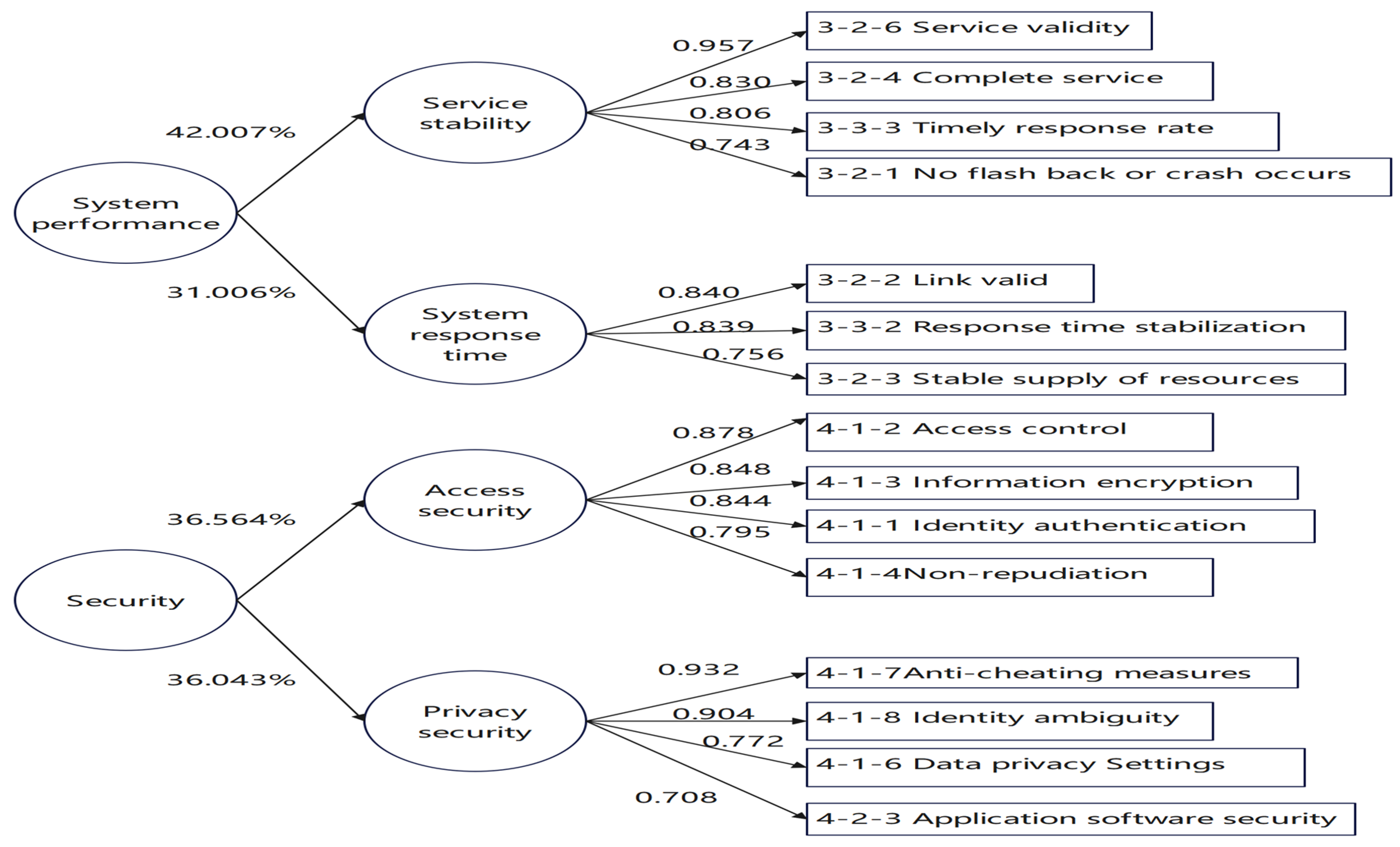
Table 5. Functionality has four subscales with 16 indicators: subscale 1 contains a1211, a1210, a124, a127, and a126 totaling 5 indicators with an alpha value of 0.927, naming as “ image restoration function”; subscale 2 contains a152, a156, a155, and a154 totaling 4 indicators with an alpha value of 866, naming as “image editing function”; subscale 3 contains a117, a116, a114, and a113 totaling 4 indicators with an alpha value of 915, naming as “style conversion and migration function”; subscale 4 contains a1214, a1212, and a158 totaling 3 indicators with an alpha value of 0.802, naming as “multi-layer image restoration”. Their eigenvalues are 7.709, 4.706, 3.147 and 2.163 respectively. The five subscales of ease of use have a total of 16 indicators: subscale 1 contains a232, a237, a239, a242, a251, and a255 with 6 indicators and an alpha value of 0.926, naming as "Visual Harmony" ; subscale 2 contains a242, a245, and a244 with 3 indicators, and an alpha value of 0.931, naming as "Service Quality"; subscale 3 contains a224, a226, a222 with 3 indicators and an alpha value of 0.811, naming as "Interaction"; subscale 4 contains a234, a233, a235 with 3 indicators and an alpha value of 0.854, naming as "Media Suitability"; subscale 5 contains a216, a215, a217 with 3 indicators and an alpha value of 0.881, naming as "Pattern Recognition". The eigenvalues were 5.006, 4.248, 2.310, 1.915 and 1.538 respectively.The two subscales of system performance have 7 indicators: Subscale 1 contains 4 indicators, a326, a324, a333, a321, with an alpha value of 0.922, which is named as "Service Stability"; Subscale 2 contains 3 indicators, a322, a332, a323, with an alpha value of 0.947, which is named as "System Response Time". The eigenvalues are 3.573 and 1.538 respectively.The two subscales of security have 8 indicators: Subscale 1 contains 4 indicators, a412, a413, a411, a414, with an alpha value of 0.932, which is named as " Access Security"; Subscale 2 contains 4 indicators, a417, a418, a416, a423, with an alpha value of 0.911, which is named as " Privacy Security". Their eigenvalues are 3.186 and 2.623 respectively.
The results of the factor analysis are shown in
Figure 3 and
Figure 4. The explained variances of image restoration function, image editing function, style transfer and migration function, and multi-layer image restoration function are 28.017%, 23.254%, 20.705%, and 15.430%, respectively, which shows that the explained variances of image restoration function are higher than those of the other three indexes; the explained variances of visual harmony, quality of service, interaction, media applicability, and pattern recognition are 20.784%, 18.333%, 15.968%, 15.058%, and 14.755%, respectively. Visual harmony, service quality, interaction, media suitability, and pattern recognition are 20.784%, 18.333%, 15.968%, 15.058%, and 14.755%, respectively, which shows that the explained variance of visual harmony is higher than that of the other four Indicators; the explained variances of service stability, and system response time are 42.007% and 31.006%, respectively, which shows that the explained variance of service stability is higher than that of system response time; the explained variances of access security, and privacy security are 36.564% and 36.043% respectively, which shows that the difference between the explained variances of access security and privacy security is not obvious. Therefore, the scales have good construct validity, and the importance of image restoration function in "functionality" is greater than that of the remaining three indicators; the importance of visual harmony in "ease of use" is greater than that of the remaining four indicators; the importance of service stability in "system performance" is greater than that of system response time; and in the area of "security", the importance of access security and privacy security is similar. Overall, the Cronbach's alpha coefficients of all the dimensions in this study are higher than 0.80, while that of the whole scale is as high as 0.952. The cumulative variance is significantly higher, which indicates that the indicators included in each factor in the factor analysis have homogeneity, and that there is a high degree of internal consistency among the indicators. This indicates that the indicators contained in each factor in the factor analysis have homogeneity. In addition, there is a high degree of internal consistency among the indicators.
4.1.2. Fuzzy analytical hierarchical process to calculate weights of indicator
Three executives of domestic AI technology enterprises and five full-time teachers of computer department are invited to make a two-by-two comparison of the first-level and second-level indicators, which give the consistency results shown in
Table 6 and
Table 7. The weight calculation of the functionality in
Table 6 is taken as an example; the matrix is a fourth-order matrix, n=4, and the calculation for weight is as follows:
The difference between any row of the data and the corresponding indicator data of other rows in this study is the identical constant, which indicates that there is a consistency test in this study.
In the case of functionality, ease of use, system performance, and security, for example, the difference between the corresponding data of the indicators of the two groups is 0.15, which has got equal values.
The results of factor analysis are shown in
Figure 3 and
Figure 4. The weights of functionality, ease of use, system performance, and security are 0.3, 0.25, 0.2, and 0.24 respectively, which shows that functionality has a stronger influence; the weights of multi-layer image restoration, style transfer and migration, image editing, and image restoration are 0.19, 0.22, 0.29, and 0.3 respectively, which shows that image restoration is more powerful than the other three indicators; media applicability, service quality, image editing, and image restoration are more important than the other three indicators. The weights of media applicability, service quality, interaction, visual harmony, and pattern recognition are 0.18, 0.2, 0.19, 0.26, and 0.17 respectively, which shows that the weights of the five indicators are not significant.
By comparing the weights, it can be seen that the importance of functionality is greater than the other indicators in the first level of indicators, because if the functions of a software cannot meet the needs of users, it will be useless to users; in the second level of indicators, the importance of image restoration function is greater than the rest of the three indicators in the second level of indicators, because the function of image restoration is not only applied to artistic creation, but also widely used in photography, medical imaging and other fields. This is because image restoration is not only applied to artistic creation, but also widely used in photography, medical imaging and other fields, and providing powerful image restoration functions can attract a wider user group; this study ranked the importance of the indicators by fuzzy hierarchical analysis and factor analysis, and the results show that the conclusions from the two methods are consistent, which reflects the stability and high credibility of the data in this study.
4.1.3. An evaluation of fuzzy integration
The evaluation set in this study consists of four evaluation results, which are represented by V, i.e., V={Important, Important, General, Unimportant}. Each evaluation result in the evaluation set was converted into a specific value, where "very important" = 100, "important" = 80, "average" = 60, "unimportant" = 50. "Not important" = 50. TheW
1 indicates the weight vector of the primary indicator and
indicates the weight vector of the secondary indicator. Above weight are determined as shown in
Table 6 and
Table 7.
The fuzzy evaluation matrix R
i is calculated for each indicator as follows. R
1, R
2, R
3 and R
4 are the fuzzy evaluation matrices for functionality, ease of use, system performance and safety, respectively.
Let
be the second layer of fuzzy integrated evaluation matrix and B1 be the first layer of fuzzy integrated evaluation matrix.
As shown in
Table 6, W
1=(0.30,0.25,0.20,0.24), B
1is obtained.
As shown in
Table 8,
,
,
, and
denote the scores of the fuzzy integrated evaluation in terms of functionality, ease of use, system performance, and safety, respectively;
1denotes the score of the fuzzy integrated evaluation of the evaluation indexes of the AI painting tool based on the generative adversarial network.The calculated results are as follows.
4.2. Integrated Discussion
4.2.1. Establishment and analysis of evaluation system
The evaluation system of AI painting software based on generative adversarial network constructed in this research is based on a large number of relevant literature at home and abroad, and combined with the actual situation in the field of AIGC to amend and transform, to formulate the initial index of the structure and indicators, after 3 experts and scholars in related fields to evaluate and provide modification opinions, and then 5 experts and scholars Delphi questionnaire correction adjustment index index, the questionnaire is completed. The questionnaire was then screened according to the plan, and principal component analysis and reliability analysis were conducted to screen out the indicators with higher explanatory power before forming the official indicators; the development process was very rigorous, so this indicator has good content validity; the Cronbach's alpha coefficients of the subscales and the full scale were all greater than 0.8, which is also a very good level of reliability.
The factor loadings of the principal components and the questionnaire items were all higher than 0.7, indicating a high degree of representativeness of the indicators. The evaluation indexes developed in this study show that excellent ai painting software should not only have rich functions, but also allow users to get a sense of coordination and aesthetics when operating, and the software should maintain stability and security during the process of users' use. Therefore, AI technology enterprises are required to meet the above indicators when developing related software.
4.2.2. Indicator importance ranking results and analysis
As can be seen from
Table 6 and
Table 7, the weights of the dimension layer are W
1=(0.30,0.25,0.20,0.24), and the weights of the criterion layer are
=(0.19,0.22,0.29,0.30),
=(0.18,0.20,0.19,0.26,0.17),
=(0.57,0.43), and
=(0.40,0.60), respectively , all judgment matrices meet consistency.
Table 8 shows that the total score of the evaluation index of AI painting tool based on generative adversarial network is 82.23, and the score corresponds to the evaluation level of "important", which indicates that the evaluation indexes constructed in this study have important reference value. Among the four first-level evaluation indexes, the score of functionality is 89.53, ranking first, and developers must prioritize the functionality indexes of the relevant software; the score of ease of use is 83.10, ranking second, which indicates that a good operating experience will have an important impact on customer selection, and it is important to pay attention to the ease of use indexes; the scores of security and system performance are 77.32 and 75.48, ranking third and fourth, which indicates the importance of these two indexes. The scores of security and system performance are 77.32 and 75.48 respectively, ranking third and fourth, which indicates that the importance of these two is far less than that of functionality and ease of use indicators. However, enterprises should fully consider system performance and security indicators when developing related software to further optimize the user experience.
5. CONCLUSIONS
Generative adversarial network is one of the important technologies in the field of artificial intelligence at present, it generates realistic data through adversarial training generator and discriminator, and has achieved great success in the fields of image generation, image restoration, image super resolution and so on. The development of ai painting software based on generative adversarial networks is of great significance, which can not only help individuals and enterprises to maintain competitiveness in related fields and improve the efficiency of creation and the quality of works, but also help the country to realize the bending of the road in the art, design and other related fields, and to promote the development of the creative industry and the enhancement of the country's soft power. The development of these tools will provide artists, designers and creators with a broader creative space, promote the integration of art and technology, and promote innovation and cultural heritage and development. This study aims to construct an evaluation system for ai painting software based on generative adversarial network, which provides more reference standards for AI technology companies that are developing related software.
Based on the results of literature exploration, in-depth interviews, questionnaire analysis of indicator construction by secondary Delphi method, exploratory factor analysis, fuzzy hierarchical analysis and fuzzy comprehensive evaluation, the evaluation system of ai painting software based on generative adversarial network includes 4 dimensions, 13 subscales and 47 indicators. 4 dimensions are: functionality, ease of use, system performance, safety; 13 subscales are: image repair function, image editing function, image editing function, image editing function, image repair function, image editing function, image editing function, image editing function and image editing function. The 13 subscales are: image restoration function, image editing function, style conversion and migration function, multi-layer image restoration, visual harmony, service quality, interaction, media applicability, pattern recognition, service stability, system response time, access security, privacy security.Based on the evaluation system of ai painting software based on generative adversarial network constructed in this research, it is found that the functionality indicators are more important than the indicators of ease of use, security, and system performance. This is because the primary criterion for users to choose software is whether its functions can solve their problems or achieve their goals. If the software lacks the necessary functionality, no matter how user-friendly the interface design is, how superior the performance is, or how high the security is, it will not be able to compensate for this fundamental flaw.
The evaluation system established in this study has unique implications in the field of ai painting. Focusing the ai drawing software on functionality, ease of use, system performance and security can make the software more competitive in the market. Rich and practical functions, intuitive and simple interface, smooth and efficient operation and safe and reliable protection will attract more users and enhance user satisfaction and loyalty, thus enhancing the market competitiveness of the software.
On the other hand, enterprises will put more R&D resources on the functionality of the software can further enhance the creativity and expressiveness of artists. Powerful functionality can provide more and richer creative tools and features to help artists better express their creativity and ideas, promote the development of artistic creation, and bring more diverse and rich works.
References
- Heidrich, D.; Schreiber, A. Visualizing source code as comics using generative AI. In Proceedings of the 2023 IEEE Working Conference on Software Visualization, Melbourne, Australia, 3-4 October 2023. [Google Scholar] [CrossRef]
- Phillips, C.; Jiao, J.; Clubb, E. Testing the capability of AI art tools for urban design. In Proceedings of the IEEE Computer Graphics and Applications Conference, Singapore, 17-19 March 2024. [Google Scholar] [CrossRef]
- Chen, F.; Zhu, F.; Wu, Q.; Zheng, J.; Zhang, X. A review of generative adversarial networks and their applications in image generation. Journal of Computer Science 2021, 44, 347–369. [Google Scholar]
- Qiu, R.; Cao, Y.; Law, S.O.; University, N. On Copyright Protection of AI Creation. Journal of Nanchang University (Humanities and Social Sciences) 2019, 2, 35–43. [Google Scholar]
- Yin, H.; Zhang, Z.; Liu, Y. The exploration of integrating the midjourney artificial intelligence generated content tool into design systems to direct designers towards future-oriented innovation. Systems 2023, 11, 566. [Google Scholar] [CrossRef]
- Hanafy, N.O. Artificial intelligence's effects on design process creativity: A study on used AI Text-to-Image in architecture. Journal of Building Engineering 2023, 80, 107999. [Google Scholar] [CrossRef]
- Zhang, B.; Zhou, Y.; Zhang, M.; Chen, H.; Li, J. Review of research on improvement and application of generative adversarial networks. Application Research of Computers 2023, 40, 649–658. [Google Scholar]
- Rumelhart, D.E.; Hinton, G.E.; Williams, R.J. Learning representations by back-propagating errors. Nature 1986, 323, 533–536. [Google Scholar] [CrossRef]
- Kingma, D.P. Auto-encoding variational bayes. arXiv Preprint 2013, arXiv:1312.6114. [Google Scholar] [CrossRef]
- Vincent, P.; Larochelle, H.; Lajoie, I.; Bengio, Y.; Manzagol, P.-A.; Bottou, L. Stacked denoising autoencoders: Learning useful representations in a deep network with a local denoising criterion. Journal of Machine Learning Research 2010, 11, 3371–3408. [Google Scholar]
- Van Den Oord, A.; Vinyals, O. Neural discrete representation learning. Advances in Neural Information Processing Systems 2017, 30. [Google Scholar] [CrossRef]
- Radford, A.; Kim, J.W.; Hallacy, C.; Ramesh, A.; Goh, G.; Agarwal, S.; Sastry, G.; et al. Learning transferable visual models from natural language supervision. In Proceedings of the International Conference on Machine Learning, Vienna, Austria, 18-24 July 2021. [Google Scholar] [CrossRef]
- Ramesh, A.; Pavlov, M.; Goh, G.; Gray, S.; Voss, C.; Radford, A.; Chen, M.; Sutskever, I. Zero-shot text-to-image generation. In Proceedings of the International Conference on Machine Learning, Vienna, Austria, 18-24 July 2021. [Google Scholar] [CrossRef]
- O'Meara, J.; Murphy, C. Aberrant AI creations: co-creating surrealist body horror using the DALL-E Mini text-to-image generator. Convergence 2023, 29, 1070–1096. [Google Scholar] [CrossRef]
- García-Ull, F.J.; Melero-Lázaro, M. Gender stereotypes in AI-generated images. Profesional de la Información 2023, 32, 5. [Google Scholar] [CrossRef]
- Liu, V.; Chilton, L.B. Design guidelines for prompt engineering text-to-image generative models. In Proceedings of the 2022 CHI Conference on Human Factors in Computing Systems, New Orleans, LA, USA, 29 April-5 May 2022. [Google Scholar] [CrossRef]
- Sukkar, A.W.; Fareed, M.W.; Yahia, M.W.; Abdalla, S.B.; Ibrahim, I.; Senjab, K.A.K. Analytical evaluation of Midjourney architectural virtual lab: defining major current limits in AI-generated representations of Islamic architectural heritage. Buildings 2024, 14, 786. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, C. Unlocking the potential of artificial intelligence in fashion design and e-commerce applications: the case of Midjourney. Journal of Theoretical and Applied Electronic Commerce Research 2024, 19, 654–670. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, T.; Guo, X.; Liu, Z.; Chen, Y. Survey of AI painting. Journal of Frontiers of Computer Science and Technology 2024, 1–22. http://kns.cnki.net/kcms/detail/11.5602.TP.20240328.1901.006.html.
- Zhang, Y. A survey on generative adversarial networks. Electronic Design Engineering 2018, 26, 34–37. [Google Scholar] [CrossRef]
- Odena, A.; Olah, C.; Shlens, J. Conditional image synthesis with auxiliary classifier GANs. In Proceedings of the International Conference on Machine Learning, Sydney, Australia, 6-11 August 2017. [Google Scholar] [CrossRef]
- Cheng, X.; Xie, L.; Zhu, J.; Chen, X. Review of Generative Adversarial Network. Computer Science 2019, 3, 74–81. [Google Scholar] [CrossRef]
- Tao, F. Artificial intelligence visual arts research. Literary Debate 2019, 7, 73–81. [Google Scholar]
- Liu, S. On the impact of AI painting on the field of cultural creativity. Contemporary Animation 2023, 2, 91–95. [Google Scholar]
- Schetinger, V.; Di Bartolomeo, S.; El-Assady, M.; McNutt, A.; Miller, M.; Passos, J.P.A.; Adams, J.L. Doom or deliciousness: Challenges and opportunities for visualization in the age of generative models. Computer Graphics Forum 2023, 42, 423–435. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Y.; Zhao, M.; Zhang, X.; Sun, X. Developing evaluative indicators for educational games. Open Education Research 2017, 2, 111–120. [Google Scholar] [CrossRef]
- Huang, B.; Yang, X.; Lu, M. Construction and application research of evaluation index system of platform education App. The Chinese Journal of ICT in Education 2019, 16, 75–81. [Google Scholar]
- Liu, Z.; Yu, Y.; Wang, Y.; Li, X.; He, Q. Design and application of enterprise IT service quality evaluation index system. Journal of Hubei University (Natural Science) 2013, 4, 527–532. [Google Scholar] [CrossRef]
- Liu, R.; Meng, X. Information system security evaluation method. Journal of Liaoning Technical University (Natural Science) 2013, 11, 1517–1522. [Google Scholar] [CrossRef]
- Zhao, Y.; Liu, Z.; Liu, W.; Sun, X.; Wang, X. Building the evaluation index for creative open data competitions: A case study on the project of digital humanities. Journal of Library Science in China 2020, 2, 75–95. [Google Scholar] [CrossRef]
- Xu, Z. Algorithm for priority of fuzzy complementary judgment matrix. Journal of Systems Engineering 2001, 4, 311–314. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).