Submitted:
25 September 2024
Posted:
25 September 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Preliminaries
2.1. Automata
2.2. Petri Nets
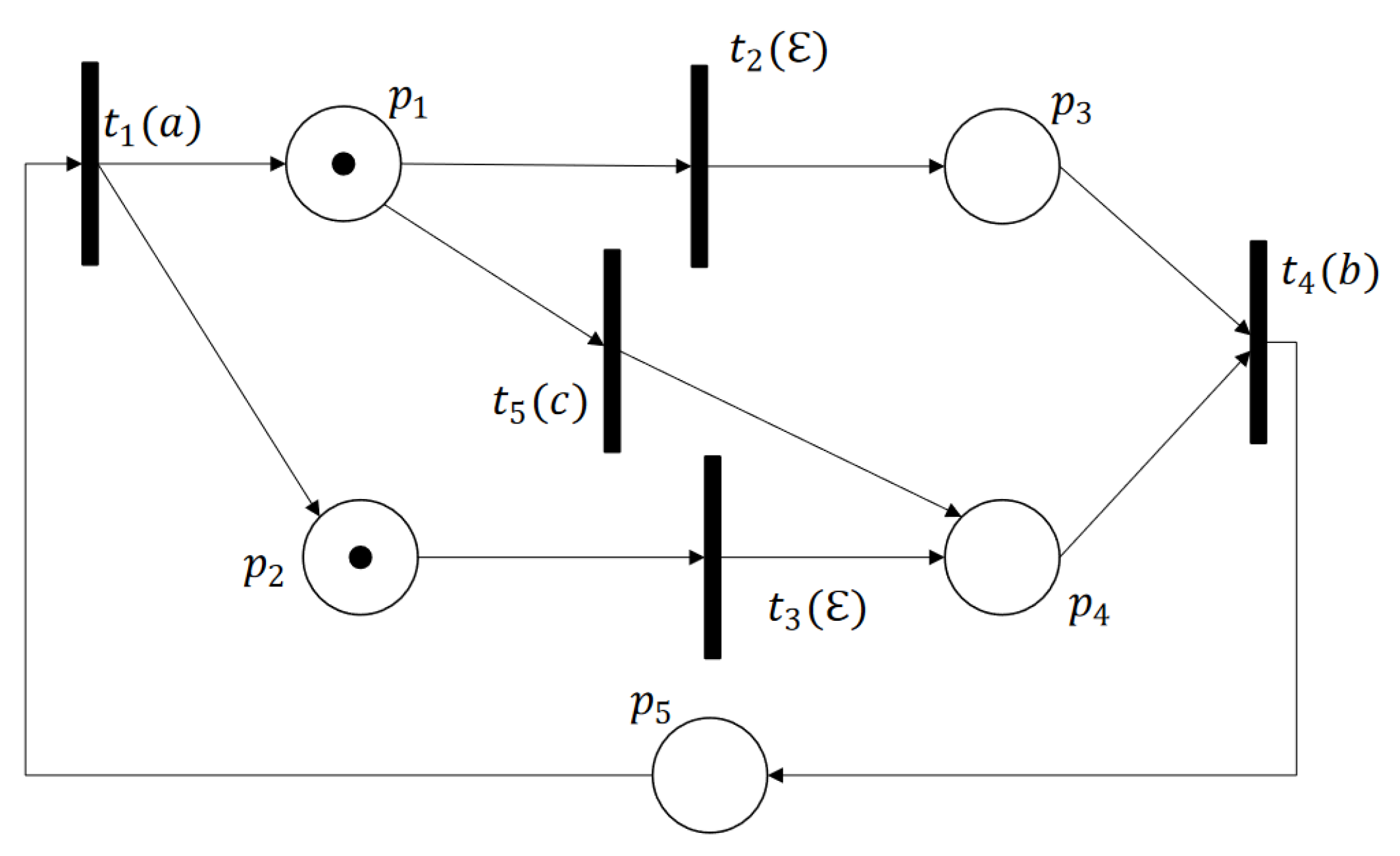
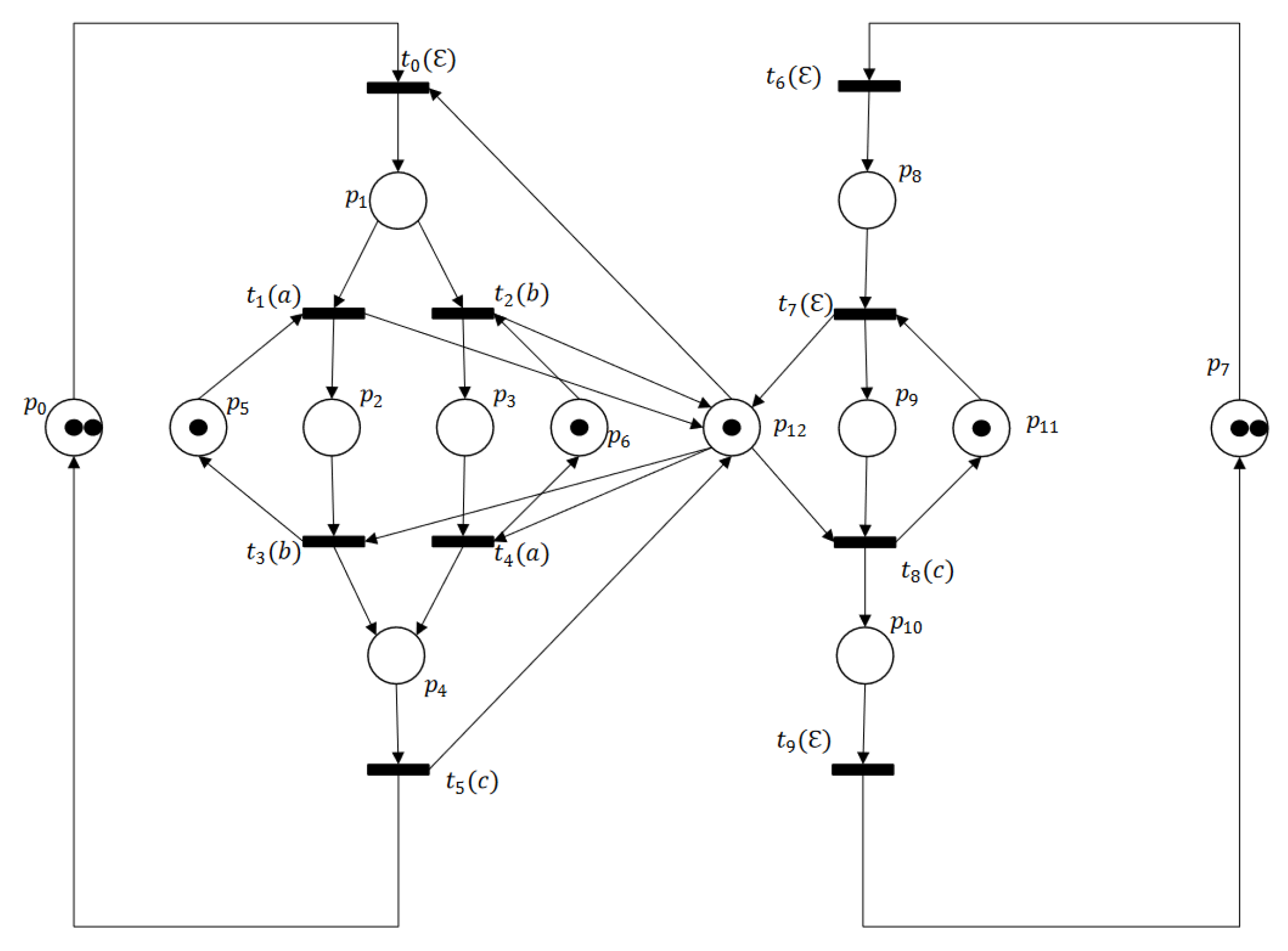
3. Labeled Petri Nets
- -
- E is the alphabet, i.e., the set of labels;
- -
- is a Petri net system;
- -
- is the labeling function that assigns to a transition either a symbol from E or the empty string .
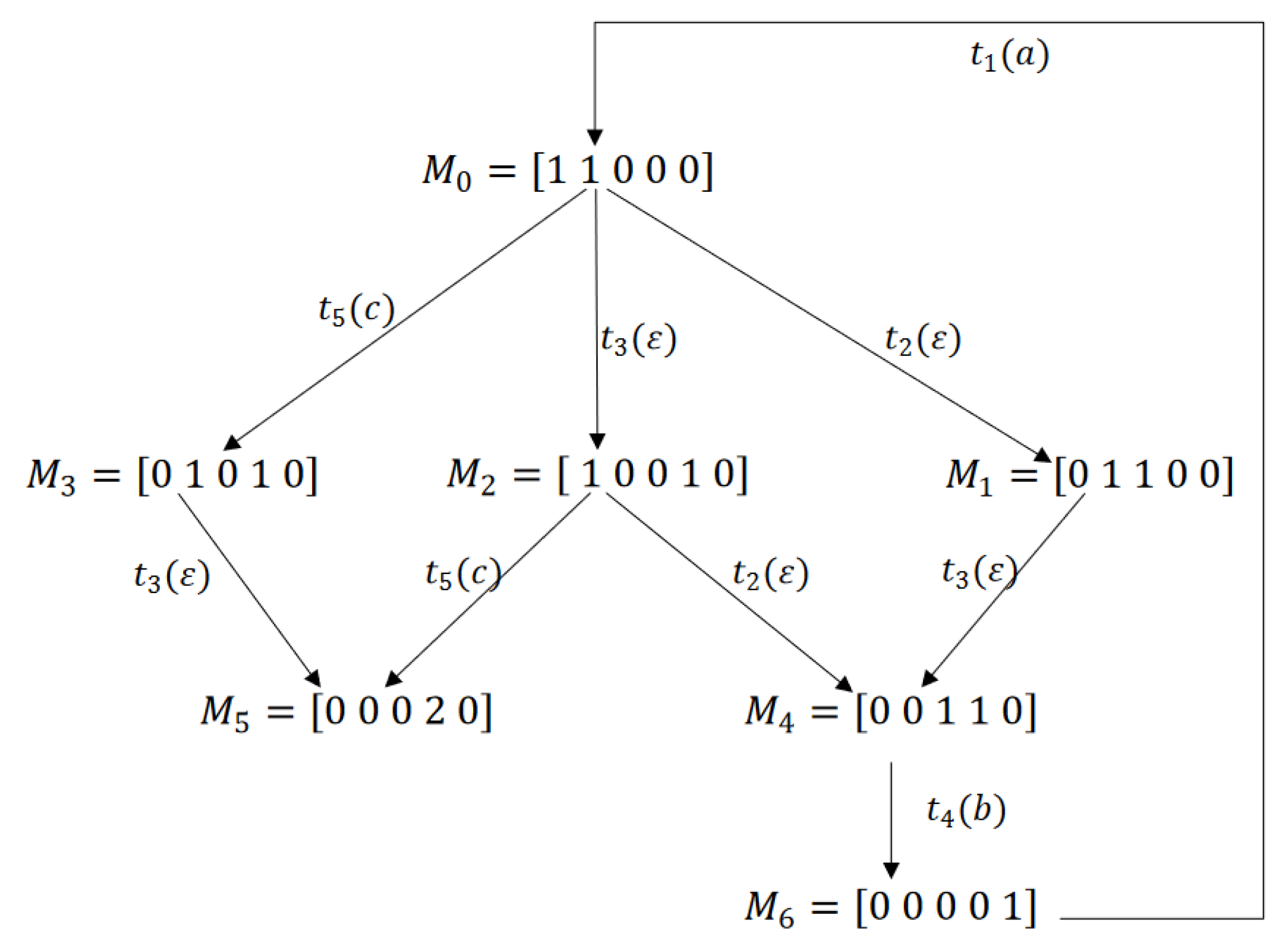
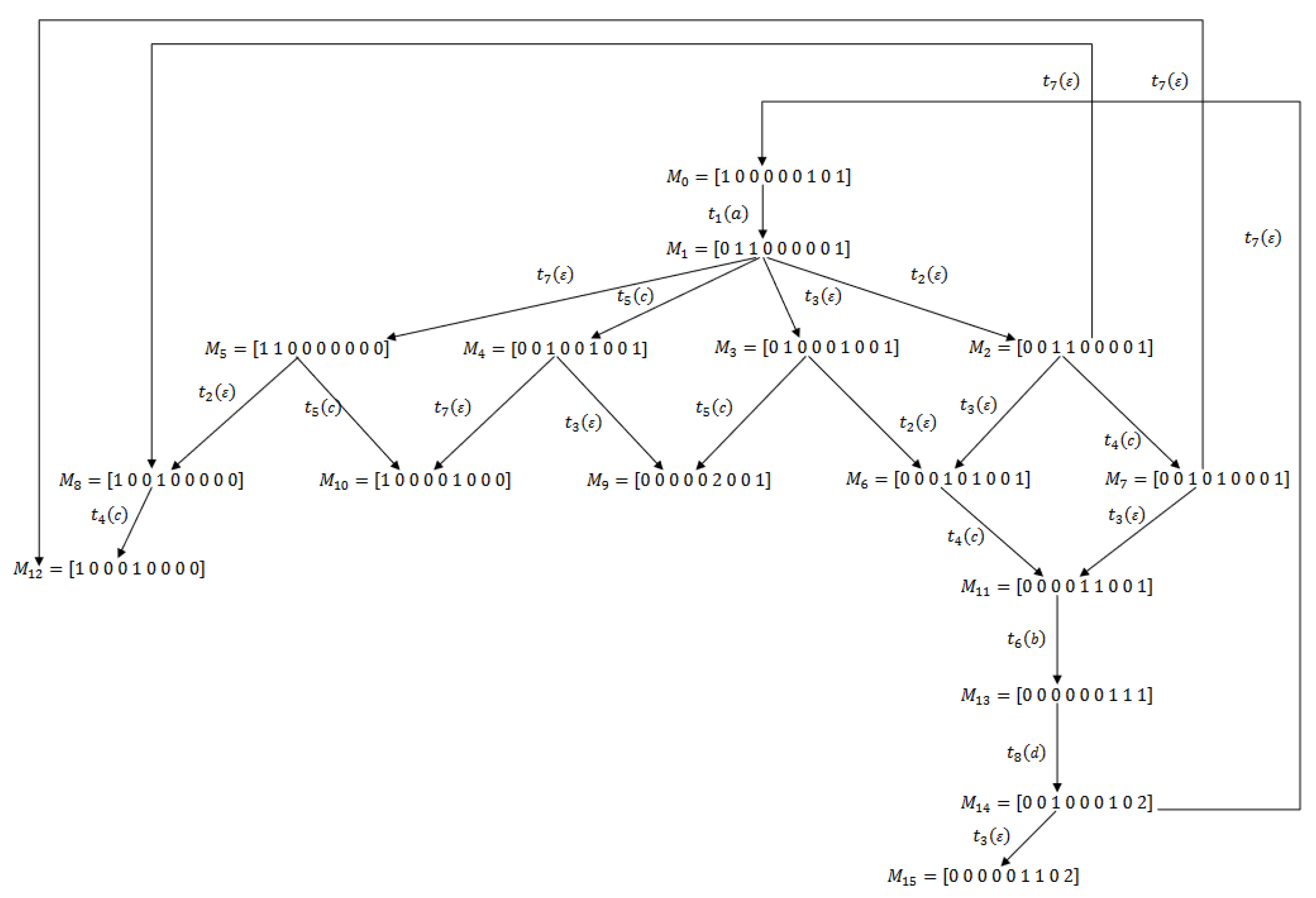
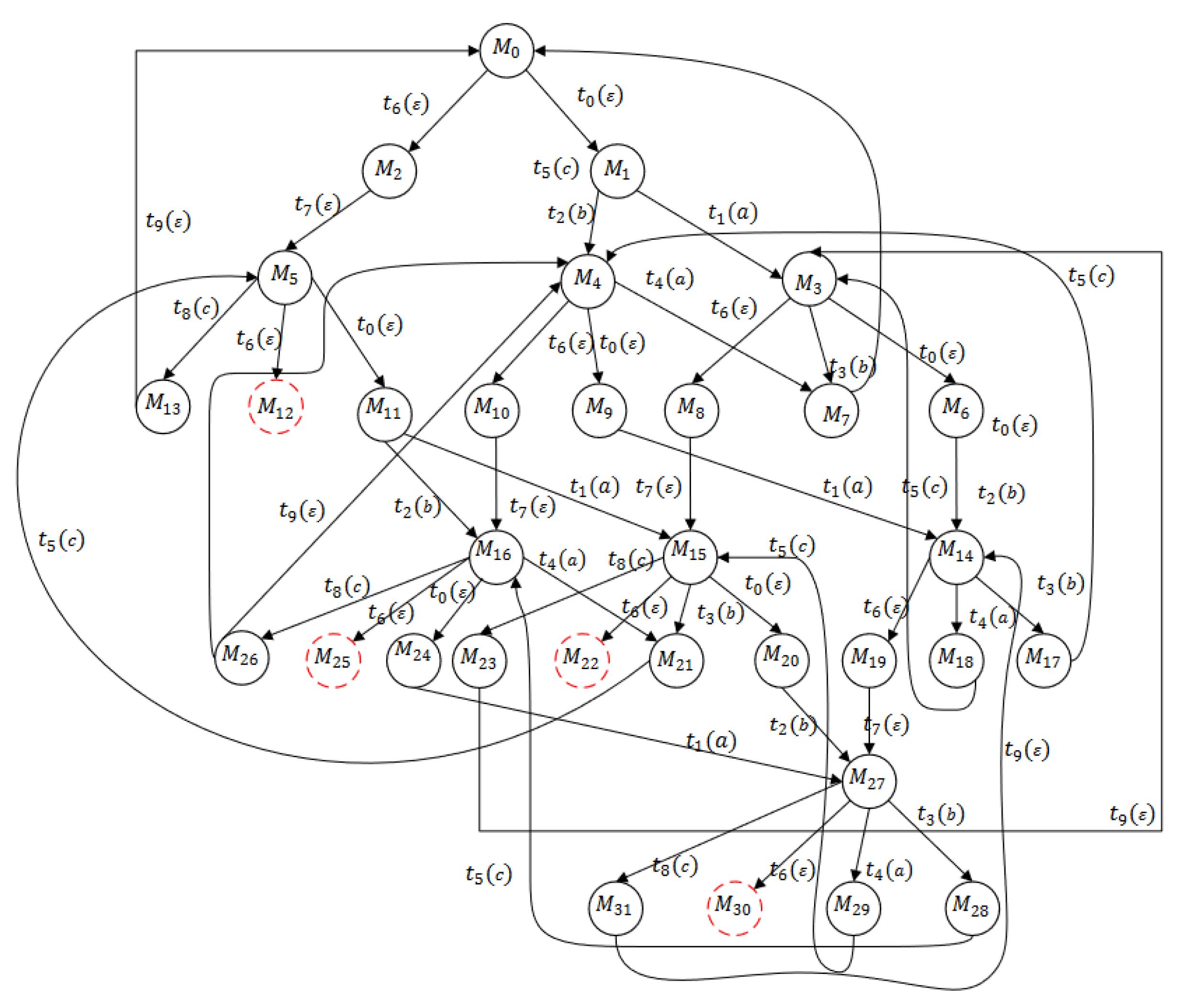
4. Minimal Explanation and Basis Reachability Graph
4.1. Minimal Explanation and Minimal E-Vector
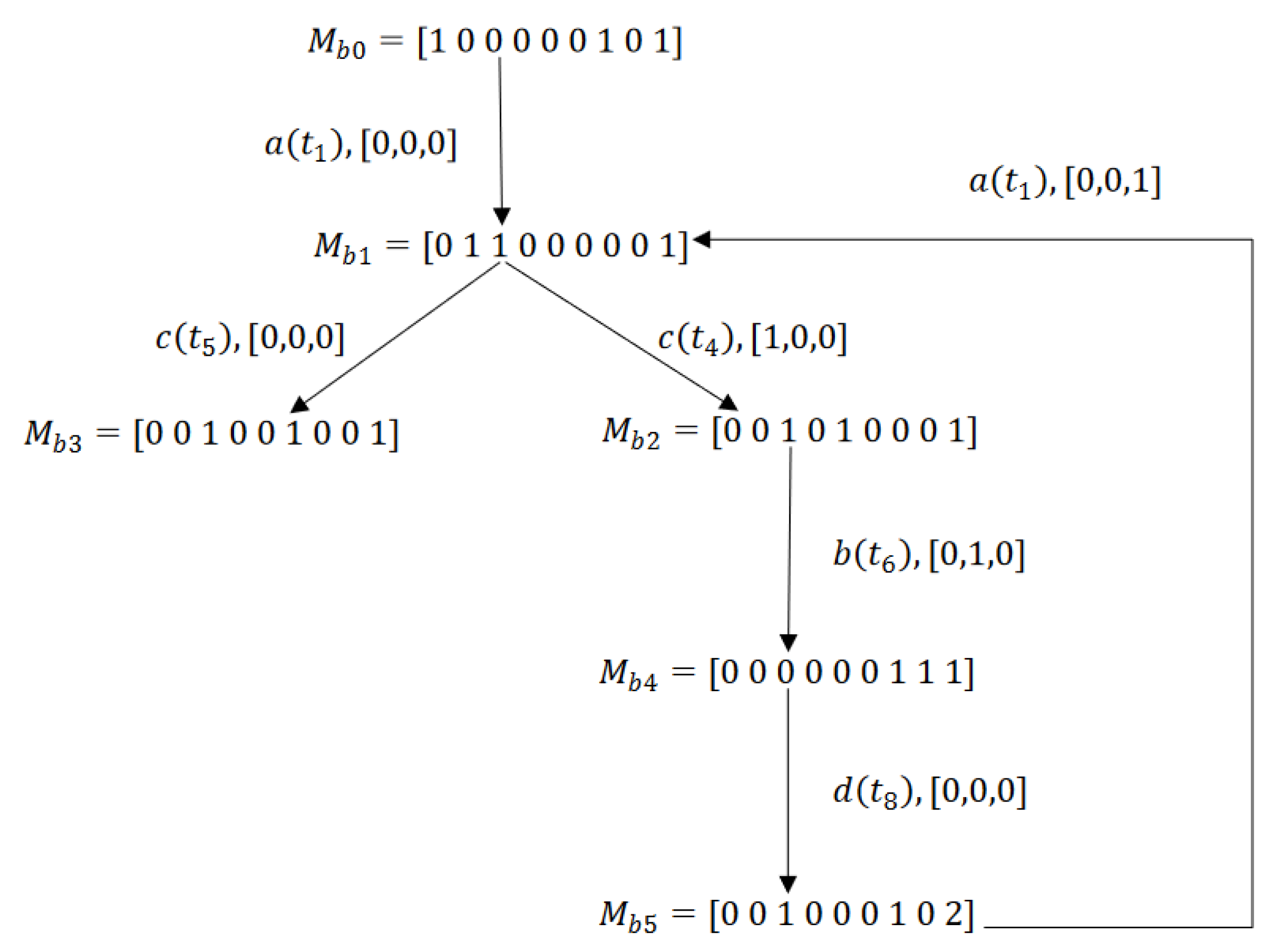
4.2. Basis Reachability Graph
- ;
- If , then the predicate holds:
- the state set is the set of basis markings;
- the event set is the set of pairs ;
- the transition relation Δ is:
- the initial state is the initial marking .

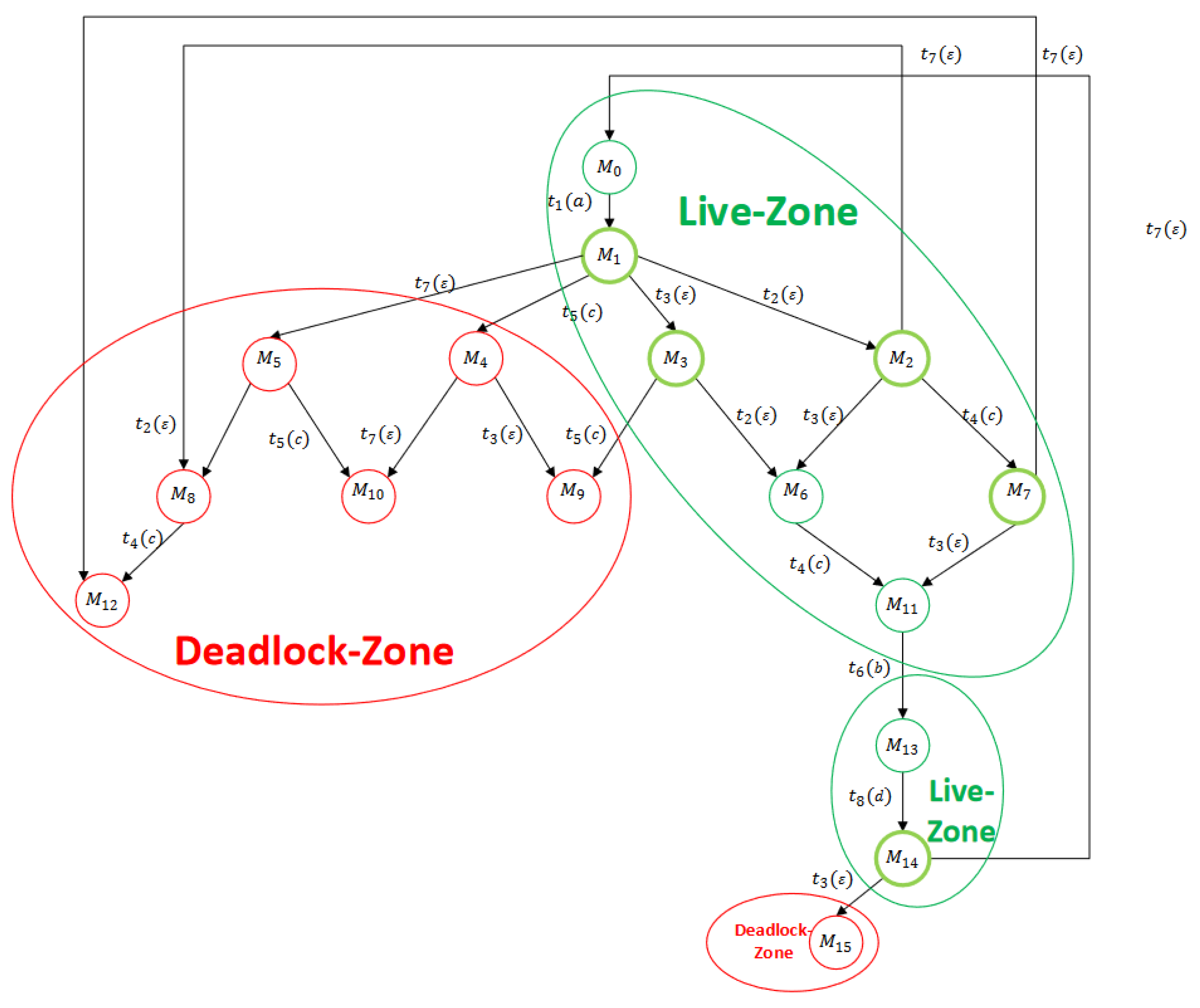
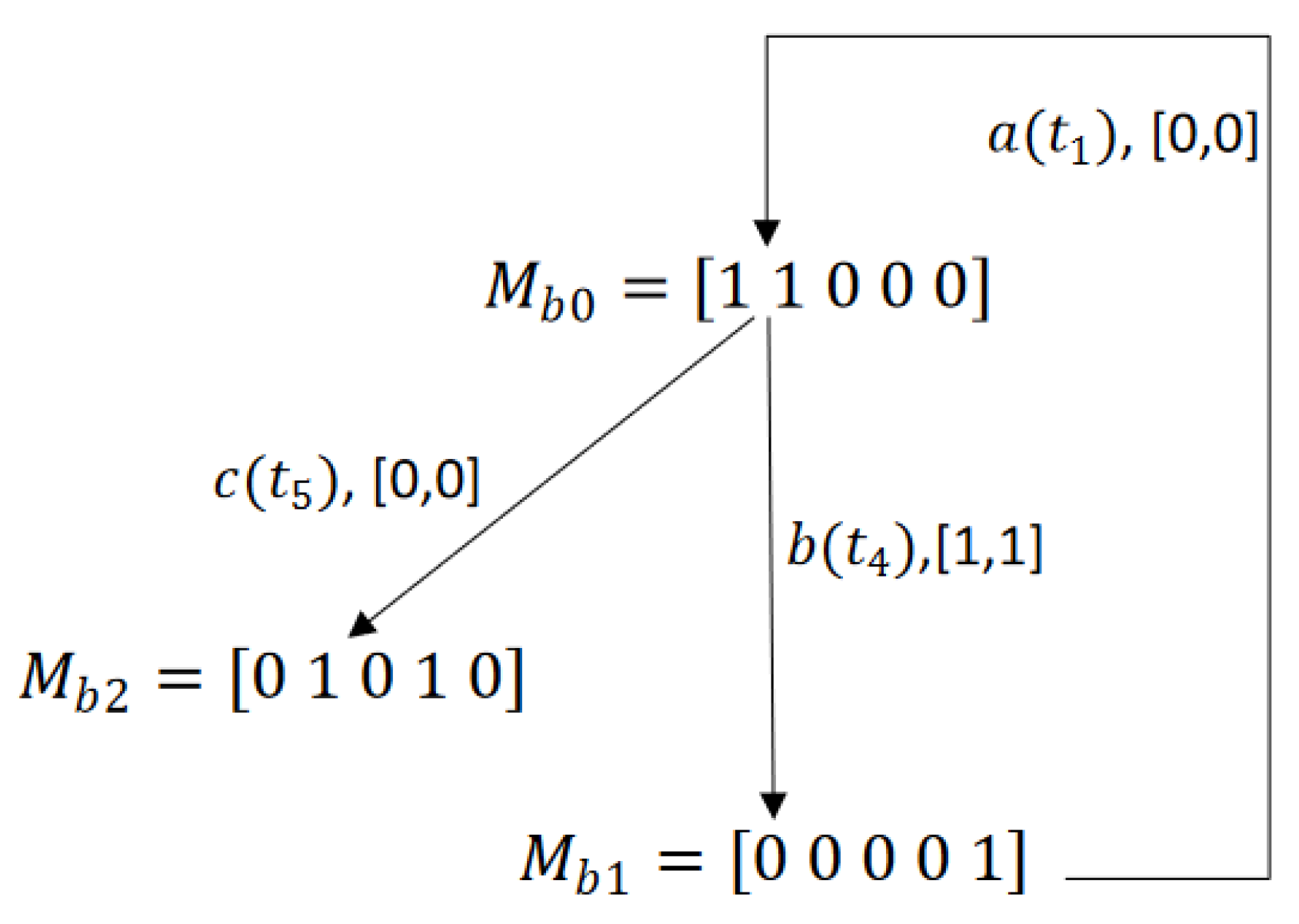
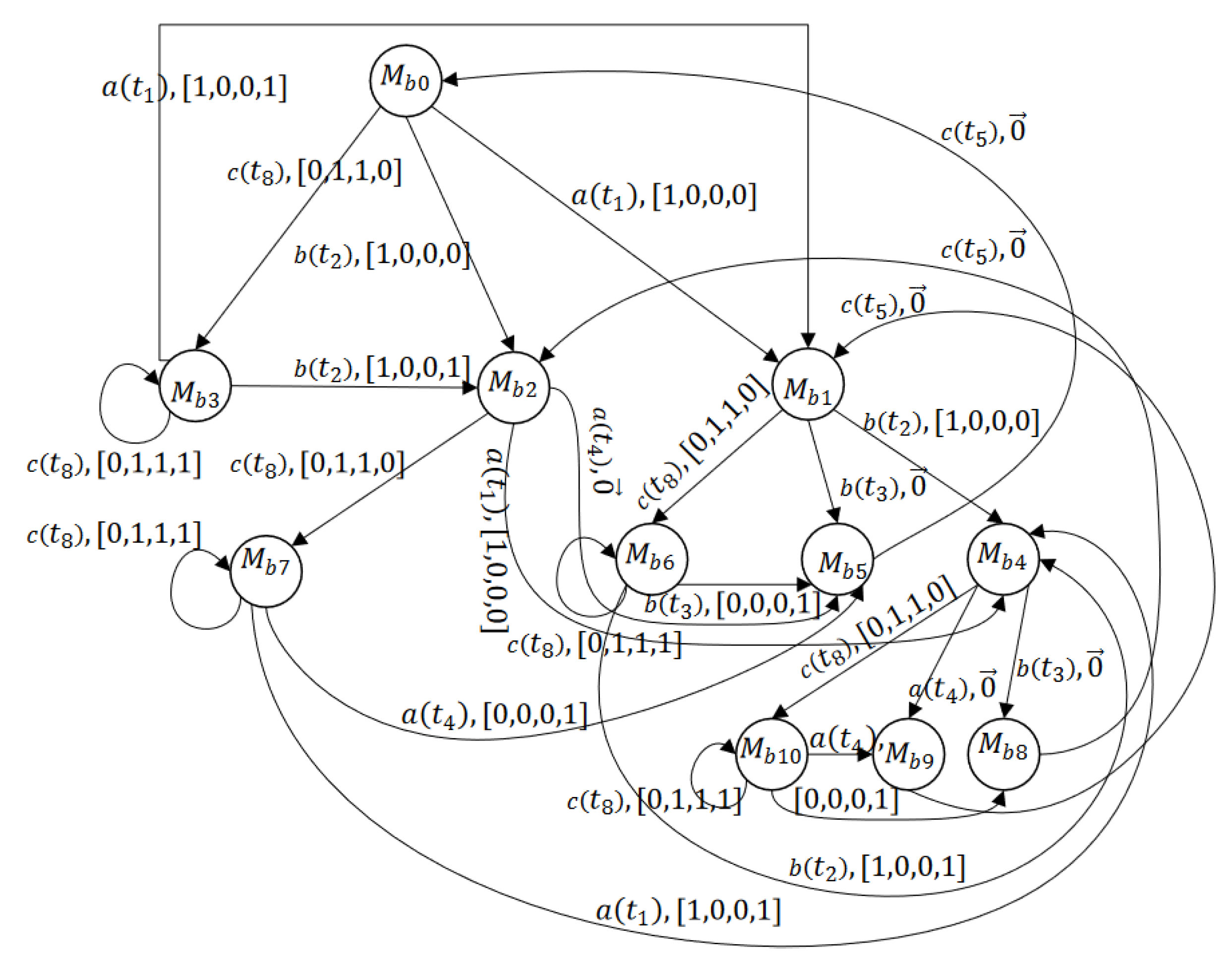
5. Deadlock Analysis
5.1. Analysis of Reachability Graph
5.2. Analysis of Basis Reachability Graph
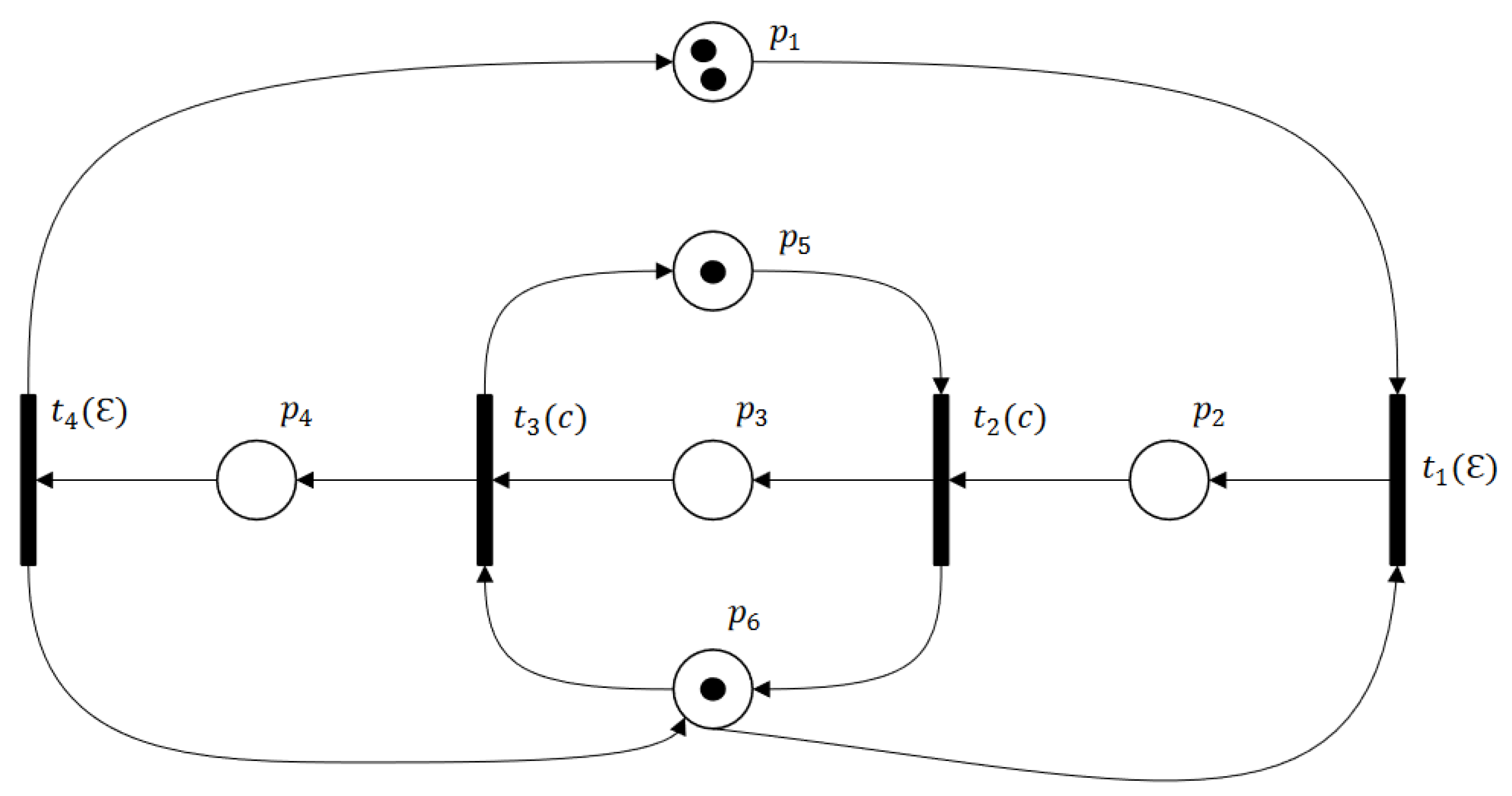
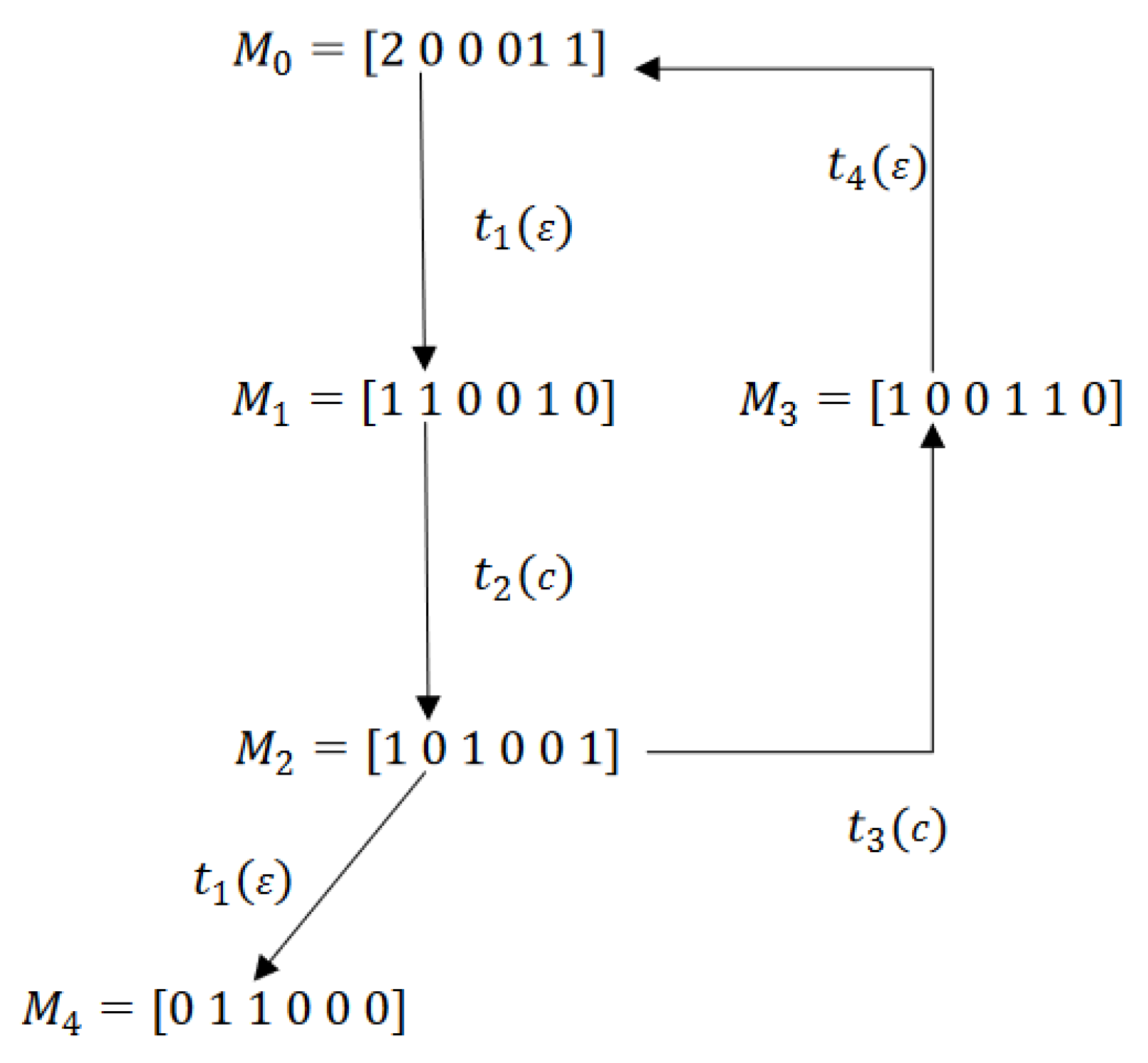
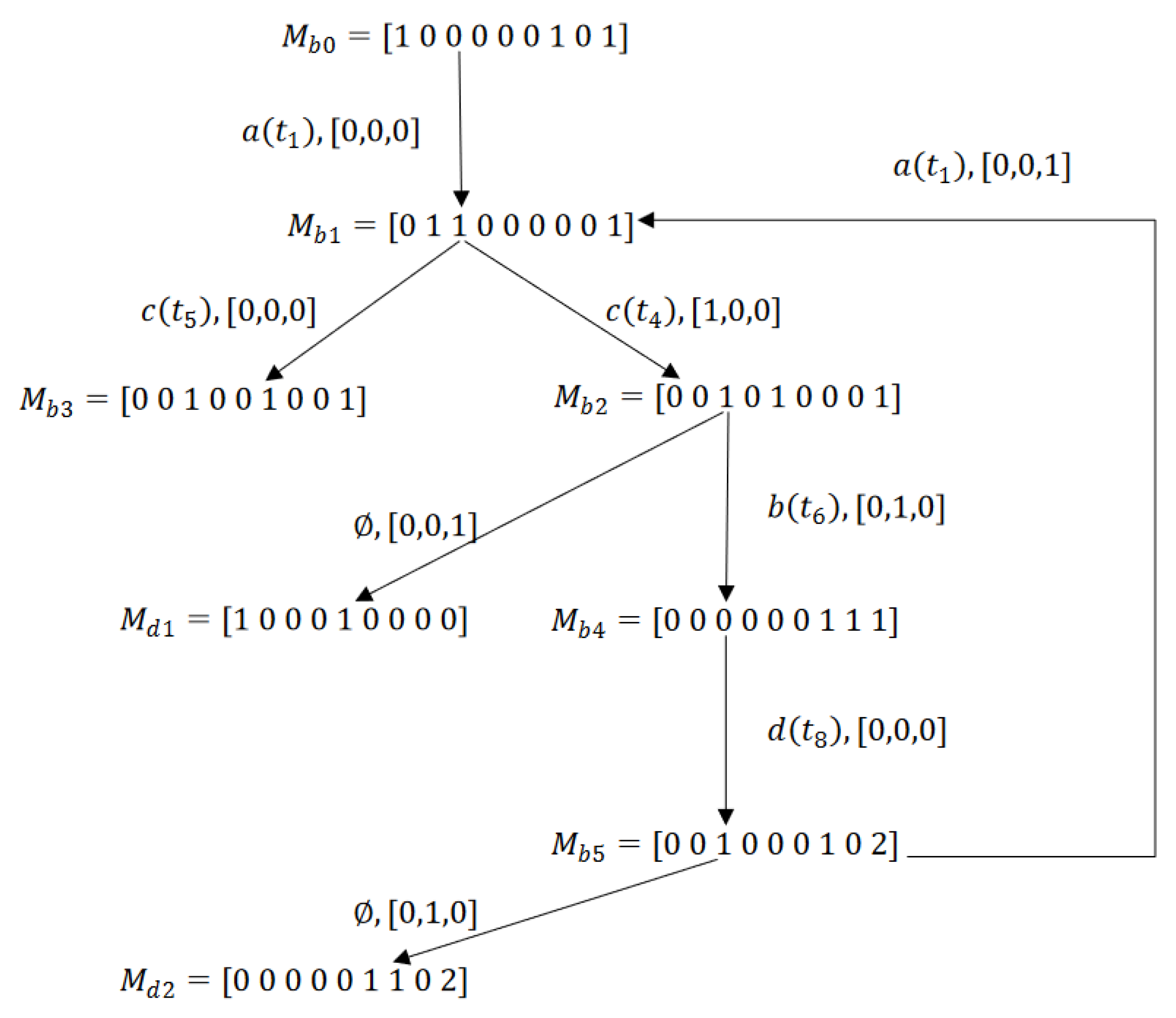
6. Dangerous Implicit Reaches
6.1. Dangerous Implicit Markings (DIMs) and Dangerous Implicit Vectors (DIVs)
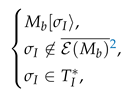
- (a)
- By , . Moreover, there does not exist such that due to .
- (b)
- As known, the -induced subnet is acyclic, implying that the predicate holds: : . That is to say, from the marking , we cannot co-reach by firing only implicit transitions.

6.2. Non Minimal Explanations
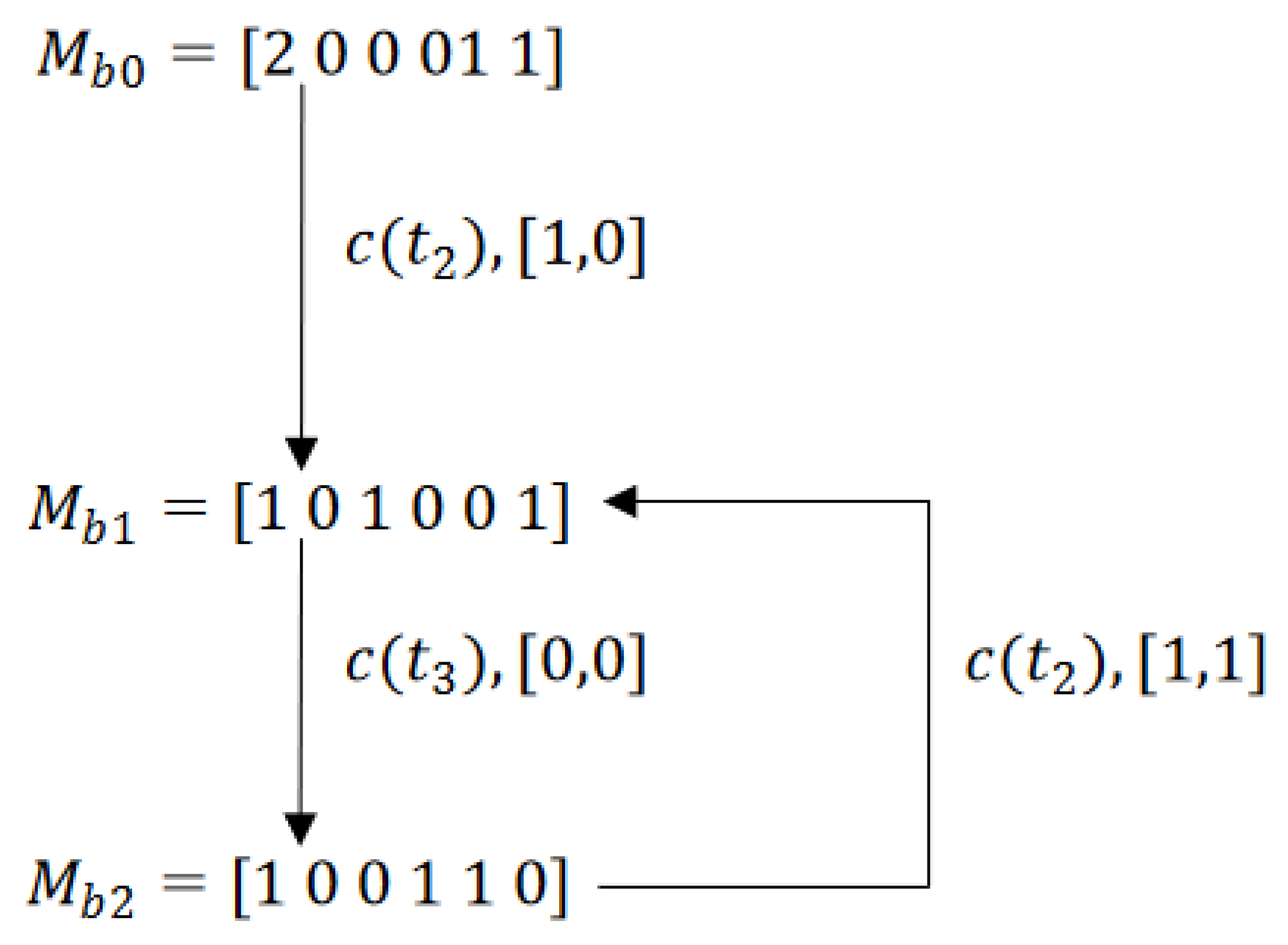
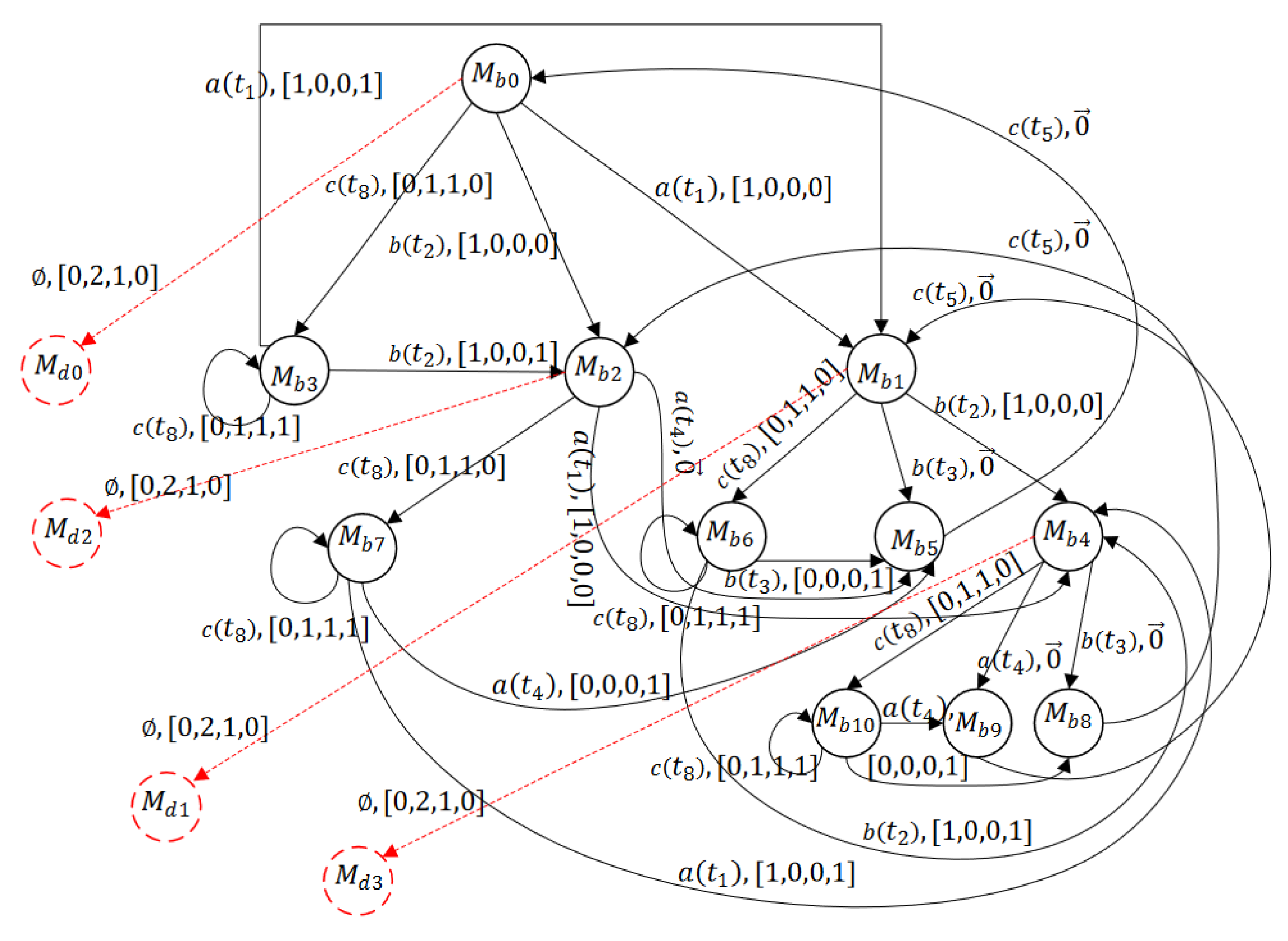
7. Observed Graph: A Deadlock Characterization for Labeled Petri Nets
-
the state set is the set of observed markings with:
- -
- the state set being the set of observed basis markings;
- -
- the state set being the set of observed dead markings;
- the event set is the set of pairs ;
-
the transition relation is with:
- -
- -
- the initial state is the initial marking .

8. Experimental Results
9. Conclusion and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| DES | Discrete-event system |
| LPN | Labeled Petri net |
| BRG | Basis reachability graph |
| DIM | Dangerous implicit marking |
| DIV | Dangerous implicit vector |
References
- Liang, Y.; Liu, G.Y.; El-Sherbeeny, A. M. Polynomial-time verification of decentralized fault pattern diagnosability for discrete-event systems. Mathematics 2023, 11, 3398. [Google Scholar] [CrossRef]
- Li, Y.Y.; Chen, Y.F.; Zhou, R. A set covering approach to design maximally permissive supervisors for flexible manufacturing systems. Mathematics 2024, 12, 1687. [Google Scholar] [CrossRef]
- Dou, H.; You, D.; Wang, S. G.; Zhou, M.C. Designing liveness-enforcing supervisors for manufacturing systems by using maximally good step graphs of Petri nets. IEEE Transactions on Automation Science and Engineering 2024. [Google Scholar] [CrossRef]
- Zhang, R.P.; Feng, Y.X.; Yang, Y.K.; Li, X.L.; Li, H.N. Polynomial-complexity deadlock avoidance policy for tasks offloading in satellite edge computing with data-dependent constraints and limited buffers. IEEE Transactions on Aerospace and Electronic Systems 2024. [Google Scholar] [CrossRef]
- Qi, H.D.; Wang, J.L.; Yan, C.G.; Jiang, C.J. The probabilistic liveness decision method of unbounded Petri nets based on machine learning. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2024, 54, 1070–1081. [Google Scholar] [CrossRef]
- Zhang, L.; Holloway, L.E. Forbidden state avoidance in controlled Petri nets under partial observation. In Proceedings of the 33rd Allerton Conference on Communication, Control, and Computing, Monticello, Illinois, USA, 27-29 September 1995; pp. 146–155. [Google Scholar]
- Li, Y.; Wonham, W.M. Controllability and observability in the state-feedback control of discrete-event systems. In Proceedings of the 27th IEEE Conference on Decision and Control, Austin, Texas, USA, December 1989; pp. 203–208. [Google Scholar]
- Zhou, Y.; Hu, H. S.; Deng, G. L.; Cheng, K.; Lin, S. W.; Liu, Y.; Ding, Z. H. Distributed motion control for multiple mobile robots using discrete-event systems and model predictive control. IEEE Trans. Syst., Man, Cybern.: Syst. 2024, 54, 997–1010. [Google Scholar] [CrossRef]
- Giua, A.; Seatzu, C.; Basile, F. Observer-based state-feedback control of timed Petri nets with deadlock recovery. IEEE Trans. Autom. Control 2004, 49, 17–29. [Google Scholar] [CrossRef]
- Giua, A.; Seatzu, C. Deadlock characterization for Petri nets controlled using GMECs and observers. In Proceedings of the 2003 American Control Conference, Denver, Colorado, USA; 2003; pp. 320–325. [Google Scholar]
- Chen, F.; Barkaoui, K. Maximally permissive Petri net supervisors for flexible manufacturing systems with uncontrollable and unobservable transitions. Asian J. Control 2014, 16, 1646–1658. [Google Scholar] [CrossRef]
- Corona, D.; Giua, A.; Seatzu, C. Marking estimation of Petri nets with silent transitions. In Proceedings of the 43rd IEEE Conference on Decision and Control, Paradise Island, Bahamas; 2004; pp. 966–971. [Google Scholar]
- Basile, F.; Chiacchio, P.; Giua, A.; Seatzu, C. Deadlock recovery of Petri net models controlled using observers. In Proceedings of the 8th IEEE Conference on Emerging Technologies and Factory Automation, Antibes, France; 2001; pp. 441–449. [Google Scholar]
- Ren, K.X.; Zhang, Z.P.; Xia, C.Y. Event-based fault diagnosis of networked discrete event systems. IEEE Transactions on Circuits and Systems II: Express Briefs 2022, 69, 1787–1791. [Google Scholar] [CrossRef]
- Murata, T. Petri nets: Properties, analysis, and applications. Proc. IEEE 1989, 77, 541–580. [Google Scholar] [CrossRef]
- Peterson, J.L. Petri Net Theory and the Modelling of Systems; Prentice-Hall: New Jersey, USA, 1981. [Google Scholar]
- Cassandras, C.G.; Lafortune, S. Introduction to Discrete Event Systems, 2nd ed.; Springer: New York, USA, 2008. [Google Scholar]
- Li, Z.; Zhao, M. On controllability of dependent siphons for deadlock prevention in generalized Petri nets. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2008, 38, 369–384. [Google Scholar]
- Chen, Y.F.; Li, Z.W. On structural minimality of optimal supervisors for flexible manufacturing systems. Automatica 2012, 48, 2647–2656. [Google Scholar] [CrossRef]
- Chen, Y.F.; Li, Z.W.; Al-Ahmari, A. Nonpure Petri net supervisors for optimal deadlock control of flexible manufacturing systems. IEEE Trans. Syst., Man, Cybern., Syst. 2013, 43, 252–265. [Google Scholar] [CrossRef]
- Ezpeleta, J.; Colom, J.M.; Martinez, J.A. A Petri net based deadlock prevention policy for flexible manufacturing systems. IEEE Trans. Robot. Autom. 1995, 11, 173–142. [Google Scholar] [CrossRef]
- Fanti, M.P.; Zhou, M.C. Deadlock control methods in automated manufacturing systems. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2004, 34, 5–22. [Google Scholar] [CrossRef]
- Lautenbach, K.; Ridder, H. The linear algebra of deadlock avoidance–A Petri net approach. Institute of Software Technology, University of Koblenz-Landau, Koblenz, Germany, Tech. Rep. No. 25–96, 1996.
- Wang, S.G.; You, D.; Wang, C.Y. Optimal supervisor synthesis for Petri nets with uncontrollable transitions: A bottom-Up algorithm. J. Inf. Sci. 2016, 363, 261–273. [Google Scholar] [CrossRef]
- Xing, K.Y.; Zhou, M.C.; Wang, F.; Liu, H.X.; Tian, F. Resource-transition circuits and siphons for deadlock control of automated manufacturing systems. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2011, 41, 74–84. [Google Scholar] [CrossRef]
- Ezpeleta, J.; Rcalde, L. A deadlock avoidance approach for non-sequential resource allocation systems. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2004, 34, 93–101. [Google Scholar] [CrossRef]
- Hsieh, F.S. Fault-tolerant deadlock avoidance algorithm for assembly processes. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2004, 34, 65–79. [Google Scholar] [CrossRef]
- Wu, N.Q.; Zhou, M.; Li, Z.W. Resource oriented Petri net for deadlock avoidance in flexible assembly systems. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2008, 38, 56–69. [Google Scholar]
- Wu, N.Q.; Zhou, M.C. Modeling, analysis and control of dual-arm cluster tools with residency rime constraint and activity time variation based on Petri nets. IEEE Trans. Autom. Sci. Eng. 2012, 9, 446–454. [Google Scholar]
- Wu, N.Q.; Zhou, M.C. Schedulability analysis and optimal scheduling of dual-arm cluster tools with residency time constraint and activity time Variation. IEEE Trans. Autom. Sci. Eng. 2012, 9, 203–209. [Google Scholar]
- Xing, K.Y.; Zhou, M.C.; Liu, H.X.; Tian, F. Optimal Petri-net-based polynomial-complexity deadlock-avoidance policies for automated manufacturing systems. IEEE Trans. Syst., Man, Cybern. A, Syst., Humans 2009, 39, 188–199. [Google Scholar] [CrossRef]
- Dotoli, M.; Fanti, M.P. Deadlock detection and avoidance strategies for automated storage and retrieval systems. IEEE Trans. Syst., Man, Cybern. C, Appl., Rev. 2007, 37, 541–552. [Google Scholar] [CrossRef]
- Huang, Y.S.; Pan, Y.L.; Su, P.J. Transition-based deadlock detection and recovery policy for FMSs using graph technique. ACM Trans. Embed. Comput. Syst. 2013, 12, 11:1–11:13. [Google Scholar] [CrossRef]
- Kumaran, T.K.; Chang, W.; Cho, H.; Wysk, R.A. A structured approach to deadlock detection, avoidance and resolution in flexible manufacturing systems. Int. J. Prod. Res. 1994, 32, 2361–2379. [Google Scholar] [CrossRef]
- Wysk, R.A.; Yang, N.S.; Joshi, S. Resolution of deadlocks in flexible manufacturing systems: Avoidance and recovery approaches. J. Manuf. Syst. 1994, 13, 128–138. [Google Scholar] [CrossRef]
- Chen, Y.; Li, Z.W.; Al-Ahmari, A.; Wu, N.Q.; Qu, T. Deadlock recovery for flexible manufacturing systems modeled with Petri nets. J. Inf. Sci. 2017, 381, 290–303. [Google Scholar] [CrossRef]
- Chen, Y.; Li, Z.W.; Barkaoui, K. Maximally permissive Petri net supervisors with a novel structure. In Proceedings of the 12th IFAC/IEEE International Workshop on Discrete Event Systems, Cachan, France; 2014; pp. 80–85. [Google Scholar]
- Ma, Z.Y.; Tong, Y.; Li, Z.W.; Giua, A. Basis marking representation of Petri net reachability spaces and its application to the reachability problem. IEEE Trans. Autom. Control 2017, 62, 1078–1093. [Google Scholar] [CrossRef]
- Cabasino, M.; Giua, A.; Seatzu, C. Fault detection for discrete event systems using Petri nets with unobservable transitions. Automatica 2010, 46, 1531–1539. [Google Scholar] [CrossRef]
- Cabasino, M.; Giua, A.; Pocci, M.; Seatzu, C. Discrete event diagnosis using labeled Petri nets: An application to manufacturing systems. Control Eng. Pract. 2011, 19, 989–1001. [Google Scholar] [CrossRef]
- Tong, Y.; Li, Z.W.; Seatzu, C.; Giua, A. Verification of state-Based opacity using Petri nets. IEEE Trans. Autom. Control 2017, 62, 2823–2837. [Google Scholar] [CrossRef]
- Giua, A.; Seatzu, C. Fault detection for discrete event systems using Petri nets with unobservable transitions. In Proceedings of the 44th IEEE International Conference on Decision and Control, Seville, Spain; 2005; pp. 6323–6328. [Google Scholar]
- Uzam, M.; Zhou, M.C. An improved iterative synthesis method for liveness enforcing supervisors of flexible manufacturing systems. Int. J. Prod. Res. 2006, 44, 1987–2030. [Google Scholar] [CrossRef]
- Zhang, X.; Uzam, M. Transition-based deadlock control policy using reachability graph for flexible manufacturing systems. Advances Mech. Eng. 2016, 8, 1–9. [Google Scholar] [CrossRef]
- Wonham, W.; Cai, K. Supervisory Control of Discrete-Event Systems; Springer: Cham, 2018. [Google Scholar]
| 1 | In this work, we use to denote the set of non-negative integers. |
| 2 |
denotes the prefix-closure of . |
| 3 |
denotes the prefix set of . |

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



