Submitted:
01 October 2024
Posted:
02 October 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Dmany Quest Engine and Dmany Nexus Protocol
1.2. Challenges in Trust and Reputation in Web3
1.2.1. Anonymity Leading to Information Asymmetry and Collusion Risks
1.2.2. Absence of Universal Reputation Mechanisms and Potential for Manipulation
1.2.3. Economic Implications: Market Inefficiencies and Vulnerability to Shocks
Over-Collateralization in Decentralized Finance (DeFi)
Vulnerability to Sybil Attacks and Collusion
Adverse Selection, Moral Hazard, and External Economic Shocks
1.3. Limitations of Existing Solutions
1.3.1. Decentralized Identity Protocols
1.3.2. Basic Reputation Systems and Their Vulnerabilities
1.3.3. Insufficient Protection Against Collusion and External Shocks
1.4. Problem Statement and Objectives
1.4.1. Research Questions
- How can a decentralized reputation protocol be designed to mitigate information asymmetry and collusion among pseudonymous participants in decentralized networks?
- What incentive mechanisms can align individual behavior with the overall health of the network, preventing moral hazard and adverse selection?
- How can privacy-preserving techniques be integrated to ensure user anonymity while enabling reliable reputation verification?
- In what ways can the protocol enhance economic efficiency, reduce over-collateralization in DeFi, and maintain stability in the face of economic fluctuations?
- How can the protocol support interoperability and reputation portability across different platforms in the Web3 ecosystem?
1.4.2. Objectives
- Develop a Quantitative Reputation Metric: Create the Social Capital Score (SCS) that reflects user actions, with mechanisms to detect and prevent manipulation and collusion, leveraging empirical data from the Quest Engine.
- Design Incentive Mechanisms Based on Game Theory: Employ game-theoretical models, such as repeated games and mechanism design, to promote honest behavior and deter malicious actions, accounting for potential irrational behavior observed in practice.
- Implement Privacy-Preserving Cryptographic Techniques: Utilize advanced cryptographic methods, such as zero-knowledge proofs (ZKPs) and zk-SNARKs, to maintain user privacy without compromising trust and verifiability.
- Ensure Interoperability and Standardization: Integrate seamlessly with existing decentralized identity solutions, adhering to established standards like W3C’s DID [36] and VC [37] specifications to enable reputation portability across platforms.
- Provide Integration Tools for Broad Adoption: Offer APIs, SDKs, and developer tools for seamless integration across platforms, facilitating standardization within the Web3 ecosystem.
- Incorporate Adaptive Mechanisms for Stability: Implement safeguards against external economic shocks, maintaining system stability by monitoring macroeconomic indicators and user activity patterns, employing techniques from financial risk management.
1.5. The Dmany Nexus Protocol: A Comprehensive Solution
Key Features
- Quantifiable Reputation with Anti-Collusion Measures: Utilizing mechanism design and information economics, the protocol reduces information asymmetry by quantifying user behavior across platforms. It employs sophisticated algorithms, including machine learning and anomaly detection, to detect patterns indicative of collusion, thereby ensuring the reliability of the reputation metric. For instance, the protocol uses clustering algorithms to identify anomalous clusters of interactions that may signify collusion.
- Privacy Preservation through Cryptography: Integrates advanced cryptographic techniques, such as zero-knowledge proofs (ZKPs) and zk-SNARKs [2], to verify reputation scores without revealing underlying personal data, aligning with the principles of self-sovereign identity and maintaining user anonymity. Users can prove that their SCS exceeds a threshold without disclosing the actual score.
- Interoperability and Standardization: Adheres to established protocols for decentralized identifiers (DIDs) and verifiable credentials (VCs), enabling reputation portability and interoperability across different platforms within the Web3 ecosystem. This standardization facilitates seamless integration and broad adoption.
- Incentive Alignment and Behavioral Considerations: Incorporates game-theoretical models, such as repeated games and the Extended Folk Theorem [12], to design incentive mechanisms that encourage cooperative behavior and deter malicious actions. The protocol accounts for behavioral economics principles, such as bounded rationality and loss aversion [28], to address potential irrational actions observed in the Quest Engine.
- Resilience to Economic Shocks: Implements adaptive mechanisms based on macroeconomic monitoring and stress testing, drawing from theories in financial economics to maintain system stability amid external economic fluctuations. For example, the protocol adjusts parameters in response to volatility indicators to prevent systemic risks.
Addressing Core Challenges
- Mitigate Information Asymmetry and Collusion: By providing a reliable and verifiable reputation metric, the protocol reduces information asymmetry, facilitating informed decision-making among participants. The anti-collusion measures, grounded in mechanism design and statistical anomaly detection, deter coordinated manipulation and enhance the integrity of the network.
- Enhance Economic Efficiency and Reduce Over-Collateralization: By enabling accurate assessment of participant trustworthiness, the protocol facilitates under-collateralized lending in DeFi, improving capital allocation efficiency. This addresses the current inefficiencies where excessive collateral is required due to the inability to assess borrower risk.
- Prevent Sybil Attacks and Malicious Activities: The protocol increases the economic and computational cost of creating multiple reputable identities, leveraging cryptographic identity verification and reputation systems, thus deterring Sybil attacks and enhancing network security. The cost function ensures that establishing high-reputation identities is economically burdensome.
- Foster Cooperation and Account for Behavioral Variability: By aligning individual incentives with network health through carefully designed reward structures and penalties, the protocol encourages ethical behavior and cooperation, even accounting for potential irrational behavior as described in behavioral economics. The utility function is structured to incentivize higher effort levels.
- Maintain Stability Amid Economic Fluctuations: The protocol incorporates adaptive mechanisms that monitor and respond to external economic indicators, utilizing models from macroeconomics and financial risk management to ensure resilience and stability of the network. For instance, it employs dynamic adjustment of parameters based on observed volatility to mitigate risks.
2. Economic and Game-Theoretical Foundations
2.1. Mitigating Information Asymmetry and Collusion
2.1.1. Akerlof’s “Market for Lemons” and Information Asymmetry
Mathematical Modeling
- and are the mean values of and .
- is the correlation coefficient between and .
2.1.2. Collusion Risks and Detection
Mathematical Representation
Protocol Application
2.2. Preventing Moral Hazard Through Incentive Alignment
2.2.1. Principal-Agent Model with Moral Hazard
Mathematical Modeling
Protocol Implementation
2.2.2. Contract Design and Optimal Effort
2.2.3. Empirical Evidence from the Quest Engine
2.3. Encouraging Cooperation in Repeated Games
2.3.1. Application of the Extended Folk Theorem
Mathematical Modeling
- Cooperate as long as all have cooperated in the past.
- Defect permanently if any participant deviates.
Sustainability of Cooperation
- : Payoff from cooperating.
- : Immediate payoff from deviating.
- : Payoff during punishment phase (e.g., Nash equilibrium payoff).
2.3.2. Empirical Evidence from the Quest Engine
2.4. Deterring Sybil Attacks and Collusion Economically
2.4.1. Economic Cost of Identity Creation
Mathematical Modeling
2.4.2. Collusion Detection Through Econometric Models
Statistical Techniques
Empirical Results
2.5. Incorporating Behavioral Economics and Irrational Behavior
2.5.1. Addressing Loss Aversion and Bounded Rationality
Mathematical Modeling
- is the change in wealth.
- reflects diminishing sensitivity.
- represents loss aversion.
Protocol Application
2.5.2. Empirical Evidence from the Quest Engine
2.6. Mitigating Impact of External Economic Shocks
2.6.1. Adaptive Mechanisms and Stress Testing
Mathematical Modeling
- represents a system variable (e.g., aggregate SCS).
- is the drift term.
- is the volatility.
- is the Wiener process increment.
Protocol Implementation
2.6.2. Empirical Validation
2.7. Conclusion
3. Dmany Nexus Protocol Overview
3.1. Objectives and Vision
- Quantify Trustworthiness: Provide a reliable and verifiable reputation metric (SCS) that reflects user actions across platforms.
- Enhance Trust in Decentralized Networks: Reduce information asymmetry and foster cooperation among pseudonymous participants.
- Ensure Privacy Preservation: Implement zero-knowledge proofs and other cryptographic techniques to protect user data.
- Facilitate Interoperability: Enable reputation portability across different platforms using the Social Reputation Token (SRT).
- Integrate Diverse Reputation Sources: Aggregate on-chain and off-chain data, including trusted Web2 reputation metrics like GitHub contributions and Reddit karma.
3.2. Key Features
- Social Capital Score (SCS): A quantitative metric aggregating various aspects of user behavior to reflect trustworthiness.
- Social Reputation Token (SRT): An interoperable, soulbound token representing a user’s reputation, enabling seamless reputation portability.
- Multi-Layered Architecture: A structured design comprising blockchain, token, integration, and application layers for efficient functionality.
- Advanced Anti-Collusion Mechanisms: Algorithms and economic incentives to detect and prevent manipulative behaviors.
- Privacy-Preserving Technologies: Utilization of zero-knowledge proofs and secure data handling to maintain user privacy.
3.3. Building Upon the Dmany Quest Engine
- Empirical Data: Real-world user interactions, task completions, and feedback that inform the SCS calculations.
- Testing Ground: A live environment to test and refine the protocol’s mechanisms, algorithms, and models.
- User Base: An existing community of over 70,000 users whose participation aids in scaling and validating the protocol.
4. Dmany Nexus Protocol Overview
4.1. Objectives and Vision
- Quantify Trustworthiness: Develop a reliable and verifiable reputation metric (SCS) that reflects user actions across platforms.
- Enhance Trust in Decentralized Networks: Reduce information asymmetry and foster cooperation among pseudonymous participants.
- Ensure Privacy Preservation: Plan to implement zero-knowledge proofs and other cryptographic techniques to protect user data.
- Facilitate Interoperability: Enable reputation portability across different platforms using the Social Reputation Token (SRT).
- Integrate Diverse Reputation Sources: Aggregate on-chain and off-chain data, including potential integrations with trusted Web2 reputation metrics like GitHub contributions and Reddit karma.
4.2. Key Features
- Social Capital Score (SCS): A quantitative metric aggregating various aspects of user behavior to reflect trustworthiness.
- Social Reputation Token (SRT): An interoperable, soulbound token representing a user’s reputation, enabling seamless reputation portability.
- Multi-Layered Architecture: A proposed design comprising blockchain, token, integration, and application layers for efficient functionality.
- Advanced Anti-Collusion Mechanisms: Planned algorithms and economic incentives to detect and prevent manipulative behaviors.
- Privacy-Preserving Technologies: Intending to utilize zero-knowledge proofs and secure data handling to maintain user privacy.
4.3. Building Upon the Dmany Quest Platform
- Empirical Data: Real-world user interactions, task completions, and feedback that will inform the SCS calculations.
- Testing Ground: A live environment to test and refine the protocol’s proposed mechanisms, algorithms, and models.
- User Base: An existing community of users whose participation aids in scaling and validating the protocol during development.
5. Protocol Architecture and Key Components
5.1. Proposed Overall Architecture
- Blockchain Layer: A Cosmos-based sidechain dedicated to storing and processing reputation data.
- Token Layer: The Social Reputation Token (SRT), a soulbound token representing user reputation.
- Integration Layer: Aggregates reputation data from various on-chain and off-chain sources.
- Application Layer: Provides tools and interfaces for users and developers to interact with the protocol.
5.2. Blockchain Layer: Cosmos Sidechain for Reputation Data
5.2.1. Rationale and Benefits
- Scalability: High throughput to handle extensive reputation transactions efficiently.
- Interoperability: The Inter-Blockchain Communication (IBC) protocol enables seamless interaction with other blockchains.
- Customization: Tailored governance and consensus mechanisms optimized for reputation management.
5.2.2. Planned Functions of the Sidechain
- Recording Transactions: Securely logging all actions affecting the SCS.
- Data Integrity: Ensuring immutability and consistency of reputation data.
- Consensus Mechanism: Employing proof-of-stake or other suitable algorithms for efficient validation.
5.3. Token Layer: Social Reputation Token (SRT)
5.3.1. Concept and Purpose
- Represent Reputation: Act as a tangible measure of a user’s SCS.
- Enable Portability: Allow users to carry their reputation across different platforms and services.
- Prevent Transferability: Being soulbound, it cannot be transferred or sold, maintaining the integrity of reputation.
5.3.2. Planned Mechanics and Implementation
- Issuance and Adjustment: SRT tokens would be minted as user connects his wallet and the Score will be adjusted on the change of SCS.
- Verification: Platforms could verify SRT holdings through standard interfaces to assess user reputation.
- Compliance: Adherence to ERC-1238 or similar standards for non-transferable tokens is planned.
5.4. Integration Layer: Aggregating Reputation Data
5.4.1. Incorporating Diverse Data Sources
- On-Chain Data: Activities from various blockchain networks.
- Off-Chain Data: Reputation metrics from trusted Web2 platforms like GitHub and Reddit.
5.4.2. Data Integration Mechanisms
- Verifiable Credentials (VCs): Utilizing standards from W3C to securely attest off-chain data.
- Decentralized Identifiers (DIDs): Ensuring user identities are verifiable and privacy-preserving.
- Oracles and APIs: Securely fetching and validating data from external sources.
5.5. Application Layer: Interfaces and Tools
5.5.1. Developer Resources
- SDKs: Available in multiple languages for ease of development.
- APIs: Access to protocol functionalities and data.
- Documentation: Comprehensive guides and support materials.
5.5.2. User Applications
- Reputation Dashboard: Visual representation of a user’s SCS and SRT.
- Privacy Controls: Allowing users to manage data sharing preferences.
- Engagement Platforms: Facilitating participation in tasks and community activities.
5.6. Key Components Detailed
5.6.1. Social Capital Score (SCS)
Mathematical Formulation
- : Normalized value of component j for user i.
- : Empirically determined weights for each component.
- n: Total number of components integrated into the SCS.
Components and Data Sources
- Reputation Points (RP): From the Quest Platform.
- On-Chain Experience: Activities across blockchain networks.
- Off-Chain Contributions: Data from GitHub, Reddit, etc.
- Referral Score: Impact of user referrals.
5.6.2. Anti-Collusion Mechanisms
Detection Algorithms
- Network Analysis: Identifying suspicious interaction patterns.
- Machine Learning: Anomaly detection to spot irregular behaviors.
Economic Deterrents
- Cost Functions: Making reputation manipulation economically unviable.
- Penalties: Reducing SCS for detected collusion.
5.6.3. Privacy-Preserving Techniques
Zero-Knowledge Proofs
- Protect Data: Allow users to prove statements about their reputation without revealing underlying data.
- Enhance Security: Prevent data leaks and unauthorized access.
Selective Disclosure
- Attribute-Based Credentials: Share specific attributes without exposing full identity.
- Consent Mechanisms: Users grant permissions for data access.
6. Development Roadmap and Future Implementations
6.1. Future Developments and Roadmap
6.1.1. Expansion of Reputation Sources
- Integrate Additional Platforms: Enhance SCS accuracy and relevance by incorporating data from more sources.
- Refine Weighting Mechanisms: Continuously improve the SCS model based on new data and user feedback.
6.1.2. Scaling and Optimization
- Performance Enhancements: Optimize the sidechain and data processing methods.
- Layer 2 Solutions: Explore technologies like zk-Rollups for scalability, pending further research and development.
6.1.3. Community and Governance
- Establish Decentralized Governance: Involve the community in protocol decisions through planned governance mechanisms.
- Encourage Open Source Contributions: Foster collaboration and innovation by making the protocol open-source.
6.2. Technical Implementations and Security Considerations
6.2.1. Planned Cryptographic Implementations
Zero-Knowledge Proofs (ZKPs)
- Security Level: Targeting 128-bit security, resistant to quantum and classical attacks.
- Elliptic Curve: Considering BLS12-381 for efficient pairing operations.
- Trusted Setup: A multi-party computation (MPC) ceremony is intended to ensure trustlessness.
6.2.2. Security Measures
Future Audits and Testing
- Third-Party Audits: Plan to engage leading firms for comprehensive security audits.
- Penetration Testing: Simulations using test data to identify vulnerabilities.
6.2.3. Scalability Solutions
Layer 2 Technologies
- zk-Rollups Integration: Potentially handling thousands of transactions per second.
- Reduced Costs: Lowering transaction fees through batched processing.
6.2.4. Optimization Strategies
- Efficient Algorithms: Optimizing data structures and processing methods.
- Parallel Processing: Leveraging multi-threading where possible.
6.3. Development Status and Milestones
- Phase 1: Conceptual design by lessons from Dmany Quest Platfrom.
- Phase 2: Development of core components and initial testing.
- Phase 3: Integration of cryptographic mechanisms and security features.
- Phase 4: Extensive testing, audits, and preparation for deployment.
- Phase 5: Launch of the mainnet with full functionality.
6.4. Conclusion
7. Tokenomics and Incentive Structures
7.1. Overview of the Proposed DMNY Token
7.1.1. Token Utility and Functions
- Access to Social Capital Score (SCS) Data: DApps and third-party platforms use DMNY tokens to access users’ SCS data, integrating reputation metrics into their services.
- Incentivizing Participation: Users earn DMNY tokens as rewards for contributing positively to the network, such as completing tasks, providing high-quality work, and engaging in community activities.
- Staking for Enhanced Services: Users and DApps can stake DMNY tokens to access premium features or higher levels of service within the protocol.
- Governance Participation: Token holders can participate in protocol governance by voting on proposals and protocol upgrades.
7.1.2. Token Distribution and Minting Plan
- Initial Token Offering: A public token sale with caps on individual purchases to ensure wide distribution and prevent concentration of tokens.
- Vesting Schedules: Implementing vesting periods for team members, advisors, and early investors to align long-term incentives.
- Community Rewards: Allocating a portion of tokens for community engagement, early adopters, and contributors to the protocol development.
7.2. Economic Models and Sensitivity Analysis
7.2.1. Access to SCS Data
Fee Structure Model
- : Base fee rate (in DMNY tokens).
- : Exponent controlling sensitivity to SCS levels.
- : User’s Social Capital Score (ranging from 0 to 1000).
Parameter Justification and Sensitivity Analysis
- Simulation Findings: A value around 1.0 balances the incentives for DApps to access high-SCS users without imposing prohibitive costs.
- Case Study Reference: Similar fee structures are employed in platforms like Brave Browser’s Basic Attention Token (BAT) [19], where advertisers pay users based on attention scores.
7.2.2. Incentivizing Participation and Rewards
Reward Model
- : Reward for user i.
- : Base reward amount.
- : Exponent reflecting reward sensitivity to SCS.
- : Effort level or quality score of user i (normalized between 0 and 1).
Parameter Justification and Sensitivity Analysis
- Simulation Results: Setting between 0.8 and 1.2 encourages users to improve their SCS without creating excessive disparities.
- Economic Theory Alignment: This approach aligns with the concept of diminishing marginal returns [20], preventing disproportionate accumulation by top users.
- Case Study Reference: Steemit’s reward system [21] faced issues with wealth concentration; lessons learned influenced our parameter choices.
7.2.3. Staking for Enhanced Services
Staking Model
- S: Amount of tokens to stake.
- : Base stake amount.
- : Incremental factor per service level.
- L: Service level (integer value).
Parameter Justification
- User Accessibility: A linear increase in staking amounts avoids steep barriers for higher service levels.
- Market Adaptability: Parameters can be adjusted based on user demand and market conditions.
7.3. Analysis of Potential Adverse Effects
7.3.1. Market Manipulation Risks
Risk Assessment
- Token Hoarding: Large holders may attempt to influence governance or manipulate prices.
- Pump-and-Dump Schemes: Coordinated buying and selling to inflate prices artificially.
Mitigation Strategies
- Distribution Caps: Limiting the maximum number of tokens any single entity can acquire during initial offerings.
- Transparency Measures: Publishing regular reports on token distribution and large transactions.
- Regulatory Compliance: Adhering to securities regulations to prevent fraudulent activities.
7.3.2. Volatility and Economic Exploits
Risk Assessment
Mitigation Strategies
- Stabilization Mechanisms: Exploring token buy-back programs or linking rewards to stable assets.
- Adaptive Reward Systems: Adjusting reward amounts based on token market value to maintain consistent real-world incentives.
- Case Study Reference: MakerDAO’s Dai stablecoin [22] demonstrates mechanisms for maintaining price stability.
7.4. Agent-Based Modeling and Simulations
Simulation Setup
- Agents: Simulated users with varying SCS, behavior patterns, and risk preferences.
- Market Conditions: Scenarios included bull markets, bear markets, and periods of high volatility.
- Metrics Analyzed: Token distribution, user engagement levels, governance participation, and market liquidity.
Key Findings
- Resilience to Market Shocks: The incentive structures maintained user engagement even during adverse market conditions.
- Governance Participation: Adjusting voting mechanisms improved participation rates, mitigating voter apathy.
- Wealth Distribution: Implementing progressive reward models prevented excessive wealth concentration.
7.5. Lessons Learned from Similar Token Economies
- Steemit: Faced issues with vote-buying and wealth concentration; highlighting the need for anti-collusion measures.
- BAT: Successfully incentivized user engagement through a well-designed token model, emphasizing the importance of utility.
- MakerDAO: Demonstrated effective mechanisms for maintaining stability, informing our approach to volatility mitigation.
7.6. Conclusion
8. Governance Framework and Protocol Development
8.1. Governance Framework
8.1.1. Governance Structure and Bodies
Key Governance Entities
-
Token Holders Assembly (THA):
- Composition: All DMNY token holders who choose to participate in governance.
- Role: Propose, discuss, and vote on protocol changes.
-
Core Development Team (CDT):
- Composition: Developers and technical experts responsible for implementing protocol upgrades.
- Role: Execute approved proposals and maintain the protocol’s technical integrity.
-
Dispute Resolution Council (DRC):
- Composition: Elected members with expertise in law, ethics, and community management.
- Role: Resolve conflicts, handle appeals, and oversee compliance with governance procedures.
8.1.2. Voting Mechanisms and Participation Strategies
Voting Power Calculation
- , ensuring a balance between token stake and reputation.
- Setting and to equally weigh financial stake and social reputation.
Practical Considerations
- Voter Apathy: Implementing incentive mechanisms, such as small rewards for participation, to increase voter turnout.
- Centralization Risks: Capping maximum voting power to prevent any single entity from having excessive influence.
8.1.3. Conflict Resolution Mechanisms
Dispute Resolution Process
- Filing a Dispute: Stakeholders can submit disputes to the DRC with relevant evidence.
- Mediation: The DRC facilitates mediation between parties to reach a voluntary agreement.
- Arbitration: If mediation fails, the DRC renders a binding decision based on protocol rules and community guidelines.
Adaptability to Challenges
- Rapid Response Protocols: Enabling swift action in case of security breaches or critical failures.
- Amendment Procedures: Allowing for the modification of governance rules through supermajority votes.
8.1.4. Legal and Regulatory Compliance
Compliance Measures
- Legal Counsel: Engaging with legal experts to ensure adherence to relevant laws and regulations.
- KYC/AML Procedures: Implementing Know Your Customer (KYC) and Anti-Money Laundering (AML) measures where required.
- Data Protection: Ensuring compliance with data privacy laws such as GDPR.
Token Issuance Considerations
- Securities Regulations: Assessing whether the DMNY token falls under securities law and taking appropriate steps.
- Jurisdictional Analysis: Understanding the legal implications in different countries and regions.
8.2. Development Roadmap and Feasibility Assessment
8.2.1. Phase 1: Protocol Design and Community Consultation (Months 1–2)
Objectives
- Finalize the protocol’s technical design with input from community and experts.
- Conduct feasibility studies and risk assessments.
Feasibility Considerations
- Allocating sufficient time for thorough analysis and feedback incorporation.
- Adjusting timelines based on consultation outcomes.
8.2.2. Phase 2: Development and Testing (Months 2–4)
Objectives
- Develop core smart contracts and infrastructure.
- Perform extensive testing, including unit tests, integration tests, and security audits.
Feasibility Considerations
- Acknowledging potential delays due to technical challenges.
- Incorporating buffer periods in the timeline.
8.2.3. Phase 3: Pilot Launch and Iteration (Months 4–8)
Objectives
- Launch a pilot version of the protocol with a limited user base.
- Collect data and feedback to refine the system.
Feasibility Considerations
- Ensuring scalability to handle initial user load.
- Preparing contingency plans for technical issues during the pilot.
8.2.4. Phase 4: Full Launch and Ongoing Development (Post-Month 12)
Objectives
- Officially launch the protocol to the public.
- Continue development with regular updates and improvements.
Feasibility Considerations
- Maintaining flexibility to adapt to changing market conditions.
- Allocating resources for long-term support and development.
8.3. Risk Mitigation Strategies and Contingency Plans
Regulatory Changes
- Monitoring Legislation: Staying informed about regulatory developments.
- Legal Flexibility: Designing the protocol to adapt to new laws with minimal disruption.
Major Security Breaches
- Emergency Protocols: Establishing procedures for immediate response to security incidents.
- Insurance Measures: Exploring options for cyber insurance to mitigate financial losses.
Adoption Challenges
- User Education: Investing in educational initiatives to lower the barrier to entry.
- Partnerships: Collaborating with existing platforms to integrate the protocol and expand the user base.
8.4. Conclusion
9. Real-World Applications and Use Cases
9.1. Decentralized Finance (DeFi)
9.1.1. Reputation-Based Lending and Credit Scoring
Overview
Insights from the Dmany Quest Platform
- User Engagement Patterns: Users with higher engagement levels tend to have better task completion rates and receive positive feedback.
- Reputation Correlation: A positive correlation exists between a user’s SCS and their reliability in completing assigned tasks.
Potential Application
- Improve Risk Assessment: Lenders could use SCS to evaluate borrower trustworthiness.
- Adjust Collateral Requirements: Users with higher SCS might benefit from lower collateralization ratios.
Barriers to Adoption
- Lack of Pilot Implementations: Without real-world testing, the effectiveness of SCS in lending remains hypothetical.
- Integration Challenges: Existing DeFi platforms may require significant modifications to incorporate SCS.
Strategies to Overcome Barriers
- Initiate Pilot Programs: Collaborate with DeFi platforms to test the integration of SCS.
- Develop Integration Tools: Create APIs and SDKs to facilitate the adoption of SCS in external platforms.
9.2. Gig Economy and Freelancing Platforms
9.2.1. Trustworthy Talent Matching
Overview
Insights from the Dmany Quest Platform
- Task Performance Data: Users who consistently complete tasks effectively tend to have higher SCS.
- User Feedback: Positive feedback from task creators correlates with higher reputation scores.
Potential Application
- Improve Matching Algorithms: Utilize SCS to match freelancers with appropriate projects.
- Enhance Client Trust: Provide clients with a reliable metric to assess freelancer reliability.
Barriers to Adoption
- No Existing Implementations: The protocol has not been tested in a freelancing context.
- Freelancer Acceptance: Freelancers may be hesitant to adopt a new reputation system.
Strategies to Overcome Barriers
- User Education: Inform freelancers about the benefits of the SCS for building trust with clients.
- Collaborations: Partner with freelancing platforms to pilot the integration of the SCS.
9.3. Social Media and Content Platforms
9.3.1. Enhancing Content Quality and Community Trust
Overview
Insights from the Dmany Quest Platform
- Content Contribution: Users with higher SCS are more likely to contribute valuable content.
- Community Engagement: Active participation is linked to reputation growth.
Potential Application
- Improve Content Quality: Encourage users to produce high-quality content.
- Strengthen Community Trust: Users can identify and trust reputable contributors.
Barriers to Adoption
- User Privacy Concerns: Users may be wary of reputation tracking affecting their privacy.
- Implementation Complexity: Integrating a new reputation system into existing platforms may be challenging.
Strategies to Overcome Barriers
- Privacy Controls: Allow users to manage how their reputation data is shared.
- Technical Support: Provide resources to assist platforms in integrating the protocol.
9.4. Supply Chain Management
9.4.1. Verifiable Vendor Reputation
Overview
Current Status
Potential Application
- Enhance Transparency: Provide an immutable record of vendor performance.
- Reduce Risks: Enable better decision-making by assessing vendor reliability.
Barriers to Adoption
- Data Integration: Difficulty in collecting and standardizing performance data.
- Vendor Participation: Vendors may be reluctant to adopt a system that increases transparency.
Strategies to Overcome Barriers
- Industry Partnerships: Collaborate with supply chain organizations to pilot the protocol.
- Incentivization: Offer benefits to vendors who participate, such as access to new markets.
9.5. Education and Credential Verification
9.5.1. Trusted Verification of Qualifications
Overview
Insights from the Dmany Quest Platform
Potential Application
- Simplify Verification: Allow instant verification of credentials.
- Enhance Trust: Provide employers with confidence in the authenticity of qualifications.
Barriers to Adoption
- Institutional Resistance: Educational institutions may be hesitant to adopt new systems.
- Standardization Issues: Lack of common standards for digital credentials.
Strategies to Overcome Barriers
- Standards Compliance: Align with existing frameworks like W3C Verifiable Credentials [37].
- Pilot Collaborations: Partner with progressive institutions to pilot the system.
9.6. Addressing Adoption Barriers
9.6.1. Critical Analysis of Challenges
Integration Challenges
- Developing comprehensive APIs and SDKs to simplify integration.
- Offering technical support and documentation to assist developers.
Stakeholder Resistance
- Demonstrating clear value propositions through case studies and educational materials.
- Engaging in open dialogues to address concerns and gather feedback.
Scalability Concerns
- Planning for scalability from the outset, including infrastructure optimization.
- Conducting stress tests and performance benchmarking to identify and address bottlenecks.
9.6.2. Collaborative Approach for Validation
- Initiate Pilot Programs: Identify willing partners in various industries to conduct pilot implementations.
- Gather Feedback: Collect input from users and stakeholders to improve the protocol.
- Adjust Strategies: Adapt our approach based on real-world experiences and challenges.
9.7. Conclusion of Applications
10. Conclusion
Conclusion
11. Materials and Methods
11.1. Data Collection and Preprocessing
11.1.1. Data Sources
- Reputation Points (RP): Reflecting the quality of user contributions based on task creator feedback.
- Experience Points (XP): Tracking overall user engagement, including both on-chain (OIS) and off-chain activities.
- Referral Score (RS): Measuring the success and activity level of users referred by others.
- On-Chain Interaction Score (OIS): Capturing blockchain-based activities within the Dmany Nexus system.
- Organization Data: Information on task creators used to calculate the OSCS.
11.1.2. Data Cleaning and Normalization
11.2. Mathematical Modeling
11.2.1. Social Capital Score (SCS) Calculation
- : Normalized RP.
- : Normalized On-chain XP.
- : Normalized Off-chain XP.
- : Normalized RS.
- : Empirically derived weights with .
11.2.2. Organization Social Capital Score (OSCS) Calculation
- : Normalized quality of tasks provided by organization k.
- : Normalized measure of timely payments and communications.
- : Normalized feedback from users.
- : Weights determined through empirical analysis.
11.3. Algorithm Design
11.3.1. Anti-Collusion Mechanisms
- Interaction Networks: Examining relationships between users.
- Behavioral Patterns: Detecting irregularities in task completion times, feedback loops, and referral activities.
11.3.2. Zero-Knowledge Proofs (ZKP) Implementation
- Circuit Design: Creating efficient arithmetic circuits representing the SCS calculation.
- Trusted Setup: Conducting a multi-party computation to generate common reference strings securely.
- Verification Contracts: Deploying smart contracts that verify proofs on-chain.
List of Abbreviations
| DeFi | Decentralized Finance, blockchain-based finance. 4, 6, 7, 23, 24 |
| DID | Decentralized Identifier, a unique identifier for digital identity. 27 |
| DMNY | Dmany Nexus Protocol Token, the native utility token for transactions and governance. 17–22 |
| OIS | On-Chain Interaction Score, tracking blockchain-based activities within the Dmany Nexus system. |
| 27, 28 | |
| OSCS | Organization Social Capital Score, a comprehensive metric in the Dmany Nexus protocol |
| that quantifies the reliability, quality, and trustworthiness of organizations or task creators. 27, 28 | |
| RP | Reputation Points, reflecting the quality of a user’s contributions in the Dmany Nexus ecosystem. |
| 15, 27, 28 | |
| RS | Referral Score, measuring the success of users referred by others. 27, 28 |
| SCS | Social Capital Score, a metric for user trustworthiness in the Dmany Nexus ecosystem. |
| 1, 3, 6–16, 18–21, 23–30 | |
| SRT | Social Reputation Token, a soulbound NFT reflecting a user’s reputation in the Dmany |
| Nexus protocol. 12–15, 17 | |
| VC | Verifiable Credential, a cryptographically secure credential. 27 |
| XP | Experience Points, tracking overall user engagement in Dmany Nexus. 27, 28 |
| zk-SNARK | Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, a type of ZKP for |
| private verification. 29 | |
| ZKP | Zero-Knowledge Proof, a cryptographic method for proving knowledge without revealing it. 27, 29 |
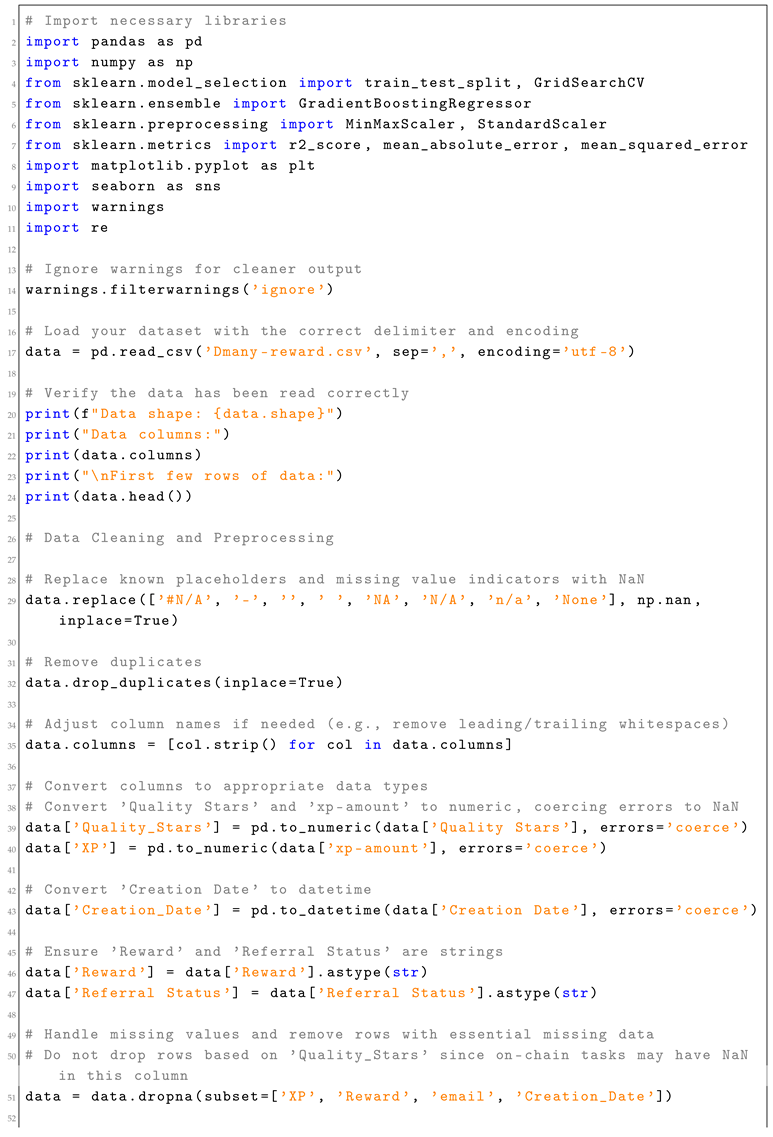
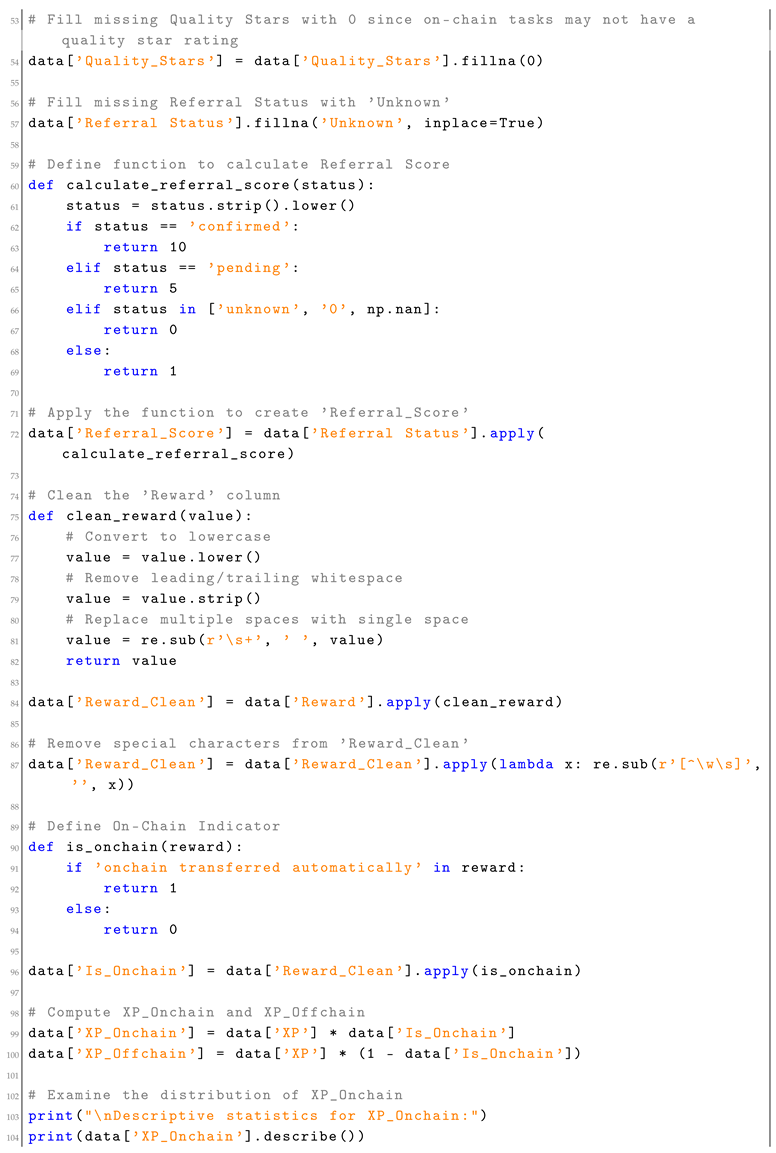
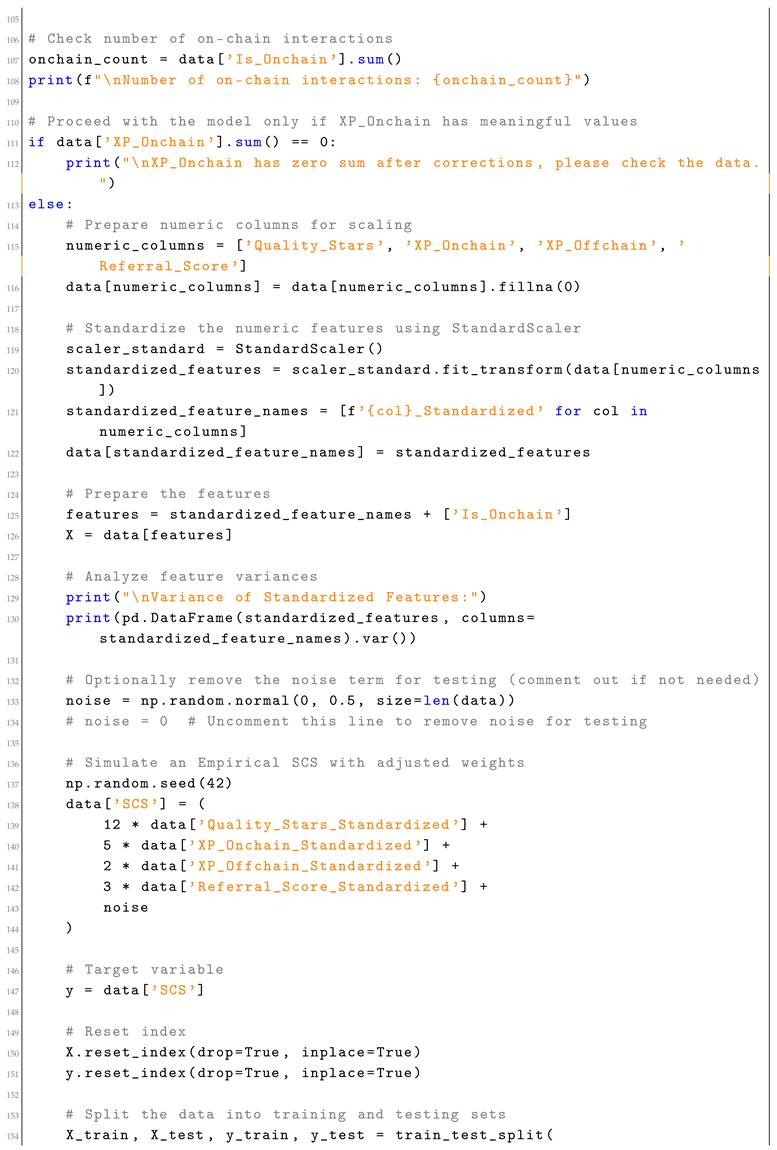
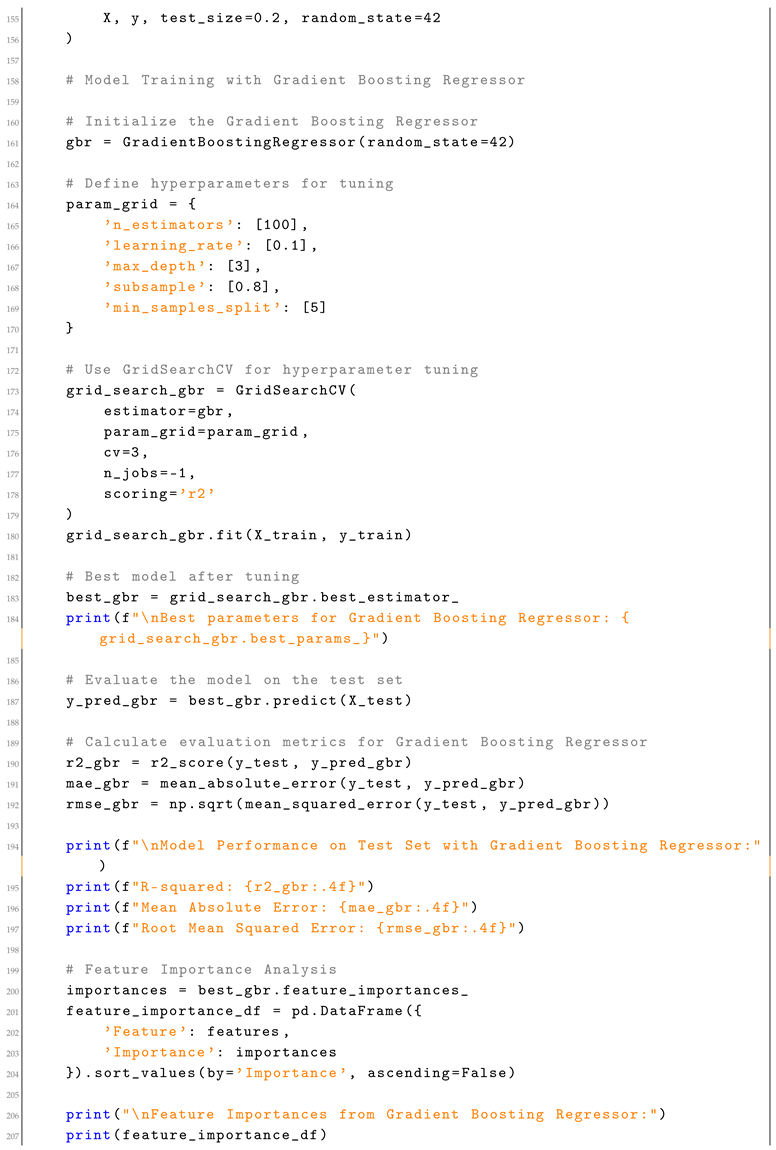
Appendix A. SCS Calculation Script
| Listing A1. Social Capital Score (SCS) Calculation Script. |
 |
 |
 |
 |
 |
References
- Akerlof, G. A. (1970). The market for “lemons”: Quality uncertainty and the market mechanism. Quarterly Journal of Economics, 84(3), 488–500.
- Ben-Sasson, E., Chiesa, A., Genkin, D., Tromer, E., & Virza, M. (2014). Succinct non-interactive zero knowledge for a von Neumann architecture. In 23rd USENIX Security Symposium (pp. 781–796). USENIX Association.
- Ben-Sasson, E., Chiesa, A., Garman, C., Green, M., Miers, I., Tromer, E., & Virza, M. (2014). Zerocash: Decentralized anonymous payments from bitcoin. In 2014 IEEE Symposium on Security and Privacy (pp. 459-474). IEEE.
- BrightID. (n.d.). BrightID: A Unique Identity Verification System. Available online: https://brightid.org.
- Buterin, V. (2014). A next-generation smart contract and decentralized application platform. Ethereum Whitepaper. Available online: https://ethereum.org/en/whitepaper/.
- Buterin, V. (2019). An incomplete guide to rollups. Available online: https://vitalik.ca/general/2019/12/23/rollup.html.
- Christidis, K., & Devetsikiotis, M. (2016). Blockchains and smart contracts for the internet of things. IEEE Access, 4, 2292-2303.
- Circom. (n.d.). Circom: A Circuit Compiler. Available online: https://docs.circom.io/.
- Douceur, J. R. (2002). The Sybil attack. In Proceedings of the First International Workshop on Peer-to-Peer Systems (pp. 251–260). Springer.
- DeFi Pulse. (2021). Total value locked (USD) in DeFi. Available online: https://defipulse.com.
- European Union. (2016). General Data Protection Regulation (GDPR). Available online: https://gdpr.eu.
- Fudenberg, D., & Tirole, J. (1991). Game Theory. MIT Press.
- Gao, Z., Li, Z., & Hou, Y. (2021). Trust management in decentralized IoT: A blockchain and smart contract based approach. IEEE Access, 9, 102774-102785.
- Arrow, K. J. (1972). Gifts and exchanges. Philosophy and Public Affairs, 1(4), 343–362.
- Nigrini, M. J. (2012). Benford’s Law: Applications for forensic accounting, auditing, and fraud detection. John Wiley & Sons.
- Jain, A. K., Murty, M. N., & Flynn, P. J. (1999). Data clustering: A review. ACM Computing Surveys (CSUR), 31(3), 264–323.
- Wooldridge, J. M. (2010). Econometric analysis of cross section and panel data (2nd ed.). MIT Press.
- Box, G. E. P., Jenkins, G. M., Reinsel, G. C., & Ljung, G. M. (2015). Time series analysis: Forecasting and control (5th ed.). John Wiley & Sons.
- Brave Software Inc. (2017). Basic Attention Token (BAT) white paper. Available online: https://basicattentiontoken.org/whitepaper/.
- Varian, H. R. (2014). Intermediate microeconomics: A modern approach (9th ed.).
- Steemit Inc. (2016). Steemit: A blockchain-based social media platform. Available online: https://steemit.com/whitepaper.
- MakerDAO. (2017). MakerDAO: Stablecoin system whitepaper. Available online: https://makerdao.com/en/whitepaper/.
- Goldreich, O., Micali, S., & Wigderson, A. (1991). Proofs that yield nothing but their validity or all languages in NP have zero-knowledge proof systems. Journal of the ACM (JACM), 38(3), 691–729.
- Ben-Sasson, E., Chiesa, A., Genkin, D., Tromer, E., & Virza, M. (2018). Scalable, transparent, and post-quantum secure computational integrity. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (pp. 254–271).
- Holmström, B. (1979). Moral hazard and observability. Bell Journal of Economics, 10(1), 74–91.
- Hoffman, D. L., Novak, T. P., & Peralta, M. (1999). Building consumer trust online. Communications of the ACM, 42(4), 80-85.
- Inter-Blockchain Communication Protocol (IBC). (n.d.). Available online: https://ibcprotocol.org.
- Kahneman, D., & Tversky, A. (2013). Prospect theory: An analysis of decision under risk. In Handbook of the fundamentals of financial decision making: Part I (pp. 99-127). World Scientific.
- Katz, M. L., & Shapiro, C. (1985). Network externalities, competition, and compatibility. American Economic Review, 75(3), 424–440.
- Mankiw, N. G. (2014). Principles of Economics. Cengage Learning.
- Mas-Colell, A., Whinston, M. D., & Green, J. R. (1995). Microeconomic Theory. Oxford University Press.
- Resnick, P., Zeckhauser, R., Friedman, E., & Kuwabara, K. (2000). Reputation systems. Communications of the ACM, 43(12), 45-48.
- Shapiro, C., & Stiglitz, J. E. (1984). Equilibrium unemployment as a worker discipline device. American Economic Review, 74(3), 433–444.
- Stiglitz, J. E., & Weiss, A. (1981). Credit rationing in markets with imperfect information. American Economic Review, 71(3), 393–410.
- Stiglitz, J. E. (1984). Theories of economic regulation. The Bell Journal of Economics, 5(2), 3-21.
- W3C. (2020). Decentralized identifiers (DIDs) v1.0. Available online: https://www.w3.org/TR/did-core/.
- W3C. (2019). Verifiable credentials data model 1.0. Available online: https://www.w3.org/TR/vc-data-model/.
- Xu, X., Weber, I., & Staples, M. (2019). Blockchain platforms: A systems perspective. Springer.
- Reed, D., Sporny, M., & Sabadello, M. (2016). Sovrin: A protocol and token for self-sovereign identity and decentralized trust. White Paper.
- Bowe, A., Grubbs, R., & Hasson, M. (2017). Zk-SNARKs for C: Verifying program executions succinctly and in zero knowledge. In Advances in Cryptology - CRYPTO 2017 (pp. 90–108). Springer.
- Benet, J. (2014). IPFS - Content Addressed, Versioned, P2P File System. Available online: https://ipfs.io.
- Friedman, J. H. (2001). Greedy function approximation: A gradient boosting machine. Annals of Statistics, 29(5), 1189–1232.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).




