Submitted:
01 October 2024
Posted:
02 October 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Literature Review
3. Methodology
3.1. Analyzing the Emerging Trends in Cybercrime
4. Results
4.1. Threats & Trends
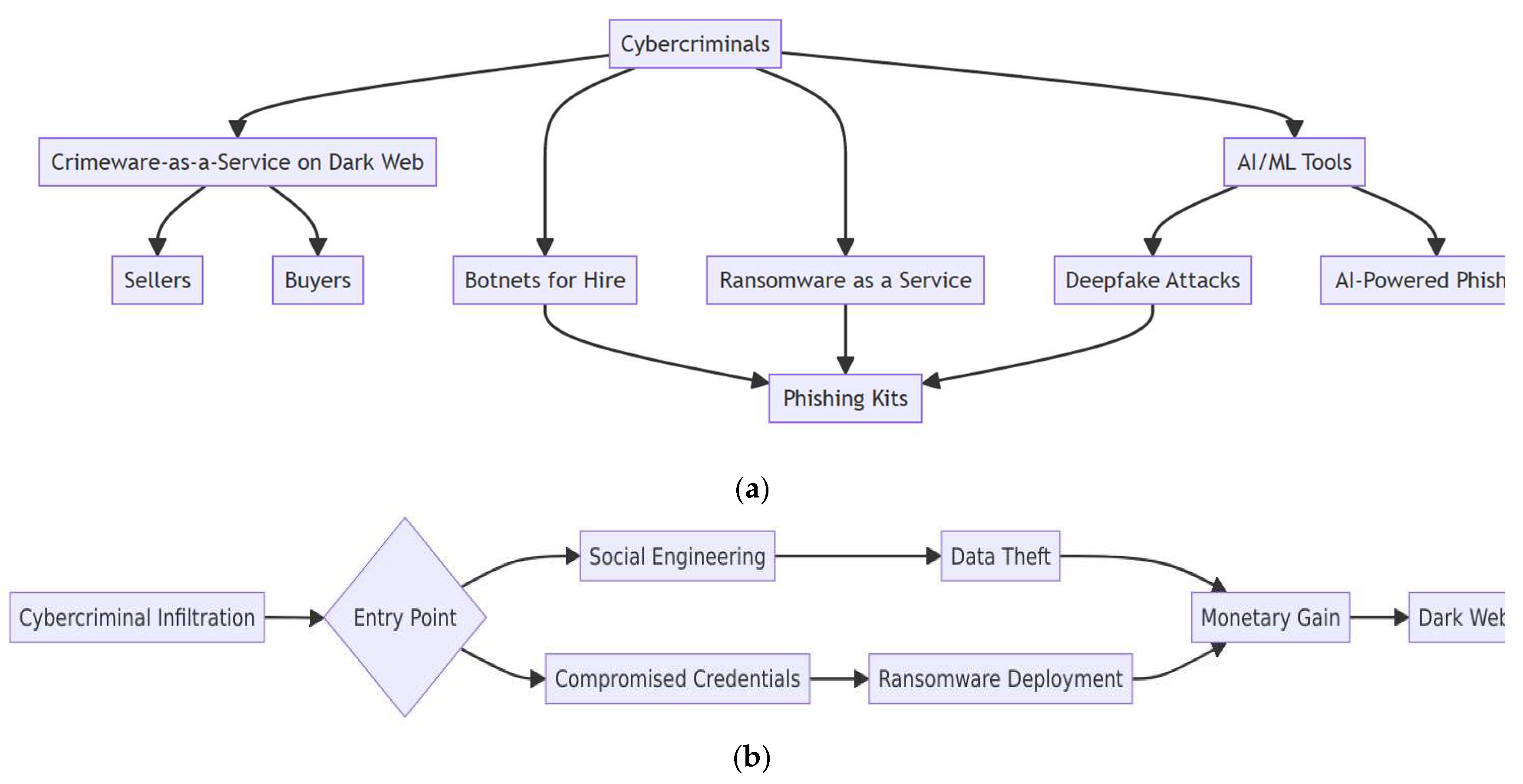
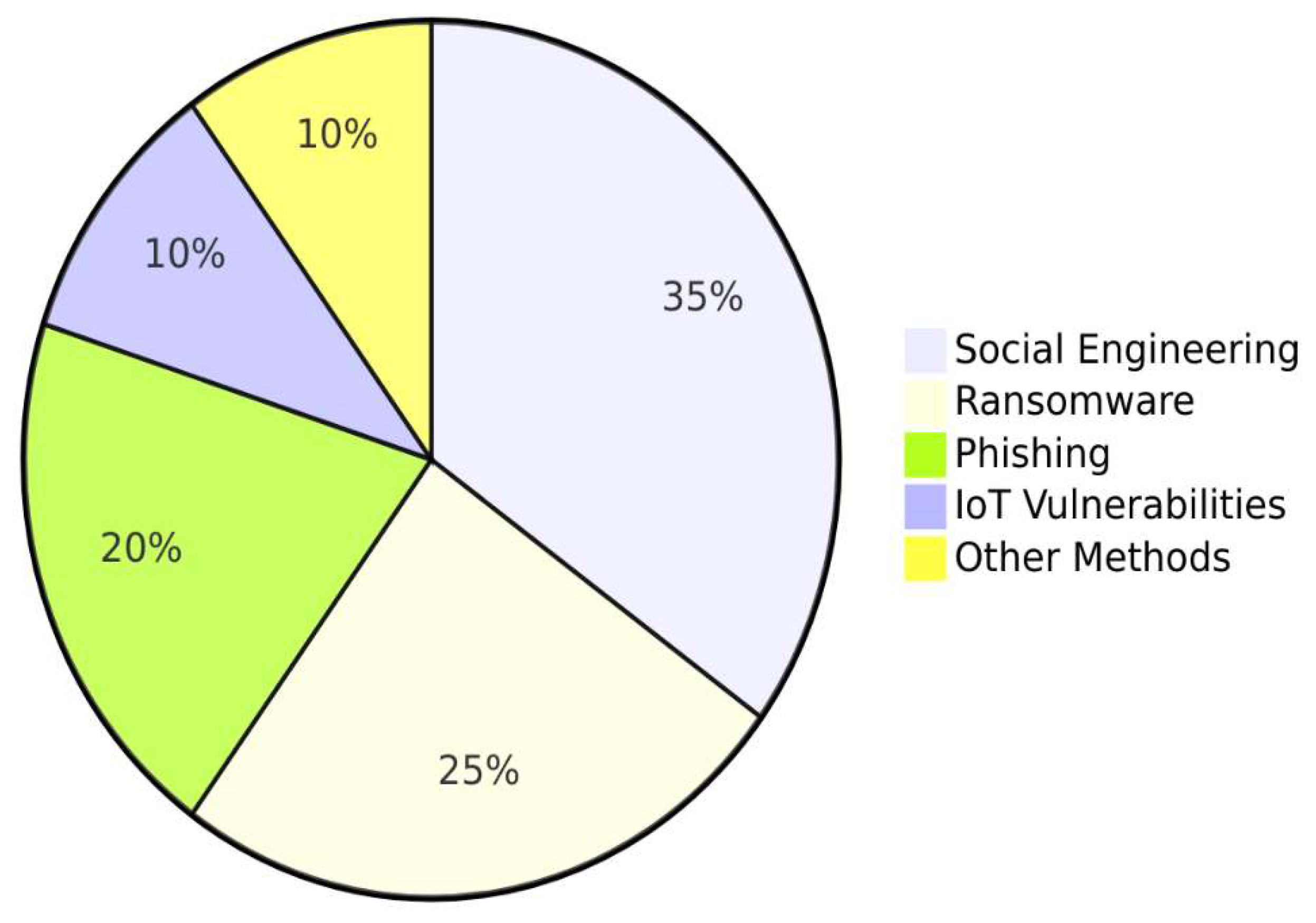
- Novel technology usage by cybercriminals will continue to increase. For instance, criminals will adapt to using artificial intelligence as part of their attack regime. Cybercriminals are currently using AI to evolve their attacks such that they will be more successful. AI is currently being used for the credential deduction, bypassing CAPTCHA controls, as well as for the emulation of voices, and evading other security controls. This trend is expected to continue to evolve with significant advances in malicious innovations to intensify future cybercriminal activities. Some innovations are expected to include social engineering to trick users into navigating to malicious sites or revealing data that is confidential. Another use of AI is through the development of videos called deepfakes which will superimpose a targeted individual’s face in a video performing activities that they actually did not participate in [1]. Other cybercriminal activities that could be augmented by AI include writing technique impersonation, the deployment of chatbots to perplex victims, software development performed directly by AI, and the inclusion of AI directly into malware and ransomware to amplify results. AI and ransomware will increase vulnerabilities identified and locate victims while also assisting with detection evasion. It is expected that the scale of cyber-attacks will continue to increase because of the efficiencies that AI provides for cybercriminal operations [40].
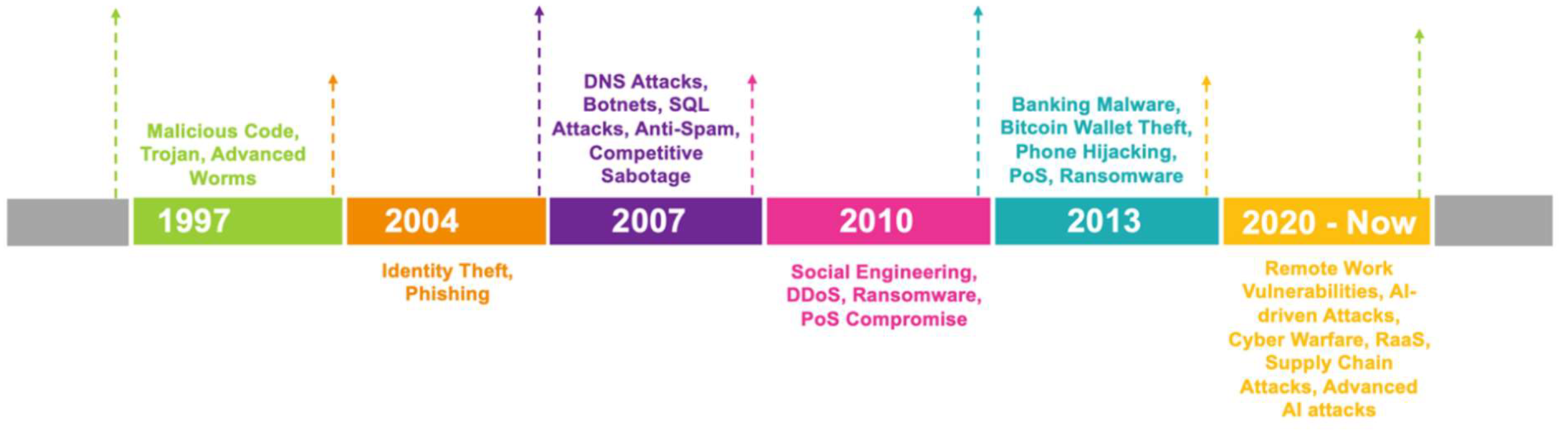
- As organizations have transformed into a business model that facilitates employees working from home on a more regular basis, trends in cybercrime are expected to continue to adapt to this model. The perimeter will be extended to include home networks as work equipment will continually relocate between different security zones represented by the home network and the secured network of the organization. Cybercriminals will attempt to take advantage of this with lateral movement between home networks and the organizations’ networks [3]. One such cyber threat is related to phishing attacks that is centered around COVID-19 related topics. The cybercriminals act as if they are healthcare or governmental organizations to engage victims to respond regarding federal aid or healthcare related benefits using alarmist rhetoric.
- Malware has become a mounting threat as it has transformed into a more efficient cybercriminal business model through the development of malware-as-a-service (MaaS). Enhanced malware is expected to lead to a large number of attacks targeting the theft of credentials as well as money and confidential data [4]. As more individuals work remotely, exposure is continued to increase for malware exploitation. Cybercriminals desire to target home networks as they are usually less secure than organizational infrastructure and have firewalls, routers, and other network devices that are not configured securely. Remote working distorts the boundaries of personal and work cultures which raises the possibility that confidential data could be compromised. This enables a larger number of cybercriminals to conduct operations using malware given that only a minute group of individuals possess the ability to create malware development capabilities.
- Ransomware is also presenting as a rising threat and has grown to include over 120 distinct families as cybercriminals have grown more skilled in concealing malicious instructions inside of seemingly legitimate business applications. As with malware, targets have been created due to the new remote work paradigm created during the COVID-19 pandemic [6]. In turn, the number of attacks and amount of ransom has ballooned as a consequence. The trend is for ransomware to become increasingly advanced through distribution within the Dark Web as well as the deployment of ML and AI into the code. Ransomware has evolved to begin making use of malware referred to as “wiper” which is more devastating and advanced than previous strains. Payloads will be enhanced to enable data extortion as well as to be cloud aware and the addition of the wiper malware is a sign that these attacks will likely be combined with other cybercrime tactics in the future. This represents a new pattern for coercing payment from the intended target.
- Damaging data denial incidents will transform to be even more devastating and are expected to begin targeting time-sensitive information generated by real-time sensors such as those found in Internet-of-Things (IoT) devices.
- Manufacturing and related industries will be the victims of more targeted attacks using Advanced Persistent Threats (APT) techniques conducted by nation states.
- Another trend due to technological advancement is the proliferation of IoT into an attack surface that has greatly expanded. Given the increase in IoT devices, there has been a related 300 percent rise in the number of attacks on IoT endpoints from 2018 to 2019. It is more challenging to enable security controls for IoT devices such as antivirus and firewalls because they have lower storage capacity and less processing power [8]. Attacks on IoT devices can be used to steal data, perform DoS attacks, lock access to critical devices for direct monetary benefit, and inflict environmental or personal harm.
- Another expanding trend is crypto jacking which is a specific malware attack type designed to compromise a computer and use the computer’s resources to perform cryptocurrency mining. This attack method is considered by cybercriminals to be lower risk and easy to conduct resulting in a continuous flow of revenue. Crypto mining related malware has become highly available which is making this threat something that will continue to increase in popularity among cybercriminals [19]. There are a large number of possible targets with minimal effort for payout and any foothold achieved with cryptojacking could also potentially be used for exfiltrating data.
- Another technological trend that continues to spread is the deployment of corporate resources using cloud services which have caused security concerns for institutions. Cloud environments have been implicated in a variety of exploits resulting in information leakage and unauthorized access, interfaces that have not been configured securely, and the hijacking of user accounts [10]. Security controls are expected to be inconsistently applied to cloud deployments since many security organizations do not have the experience or bandwidth to manage cloud environments. This will lead to misconfigurations as well as the delay of implemented security controls as the development of the cloud environment occurs.
- Social engineering is expected to also adapt to the increased use of remote work culture as personnel working from home are less complicated victims. These social engineering attacks would include phishing, SMS phishing (smishing), and voice phishing (vishing). New phishing attacks are expected to adopt ML to streamline the creation and dissemination of persuasive fraudulent messages to trick victims into providing unauthorized access to their organization’s infrastructure [12]. The number of smishing attacks are increasing because of the elevated use of mobile applications such as Skype, Teams, Zoom, WhatsApp, WeChat, and Signal. These applications are targeted to deceive users into the installation of malware onto their mobile devices [37]. With vishing, employees are deceived by cybercriminals impersonating IT helpdesk employees and tricked into authorizing access to critical systems.
- Another trend that is emerging is the increased concentration of malicious actors on techniques to bypass multi-factor authentication (MFA). Cybercriminals are concentrating on efforts to dissect MFA carried out through SMS and phone calls.
- Recent developments in automobile-related technology have exposed them to direct exploitation allowing the theft of sensitive information, the actual theft of the automobile, and can directly instigate harm upon the drivers.
- Many new concerns regarding mobile technology are being identified including spyware, vulnerability exploitation, and mobile malware. With spyware, cybercriminals can interact with applications responsible for encrypted messaging [14]. Mobile malware has introduced a number of security situations including data theft, spam over SMS, DDoS attacks using mobile devices, and compromising inadequate password security.
- As satellite-based internet networks have become mainstream with additional size and dimension, they have also presented themselves as a new attack vector for cybercriminals. The largest targets for satellite-based attacks are organizations with low latency requirements delivered through the connectivity provided by satellite-based internet networks [17]. These organizations are within the transportation, shipping, and energy business sectors. Also, cybercriminals have targeted satellite communications in Ukraine due to the ongoing conflict. Cybercriminals seek to compromise these satellite networks to conceal their activities so that they can remain anonymous.
- An increasing amount of new attack vectors are being enabled through the Dark Web as CaaS business offerings. As an extension to RaaS and other MaaS capabilities, the trend of new illicit services is expected to surge with a continued sale of the subscription-paid crime services in the future. The subscription-based offerings enable cybercriminals with rudimentary skills to launch advanced attacks with minimal investment of time and finances, and resources to develop a distinct tailored strategy [21]. This service offering enables experienced cybercriminals to sell attacks based on their skills quickly while providing a reliable income stream. As there is demand from unskilled cybercriminals and supply from experienced cybercriminals, the trend is expected to see CaaS continue to expand offerings in 2023 and the future. New emerging attack vectors are expected to be offered by cybercriminals such as deepfakes creation technology for sale [24]. Reconnaissance-as-a-service is expected to improve in demand with cybercriminals employing researchers to obtain intelligence on selected targets prior to executing an attack.
- Another anticipated direction for the future of money laundering is that cybercriminals will make use of ML to improve the recruitment of money mules by identifying better targets as well as making the location of the mule recruits more efficient [12]. Operational improvements are expected to be made for manual mule campaigns to transform them into automated services to transport money through a variety of crypto markets to expedite the movement procedure as well as to conceal the money transfer process while lowering the probability of fund recovery in the end [16]. Money Laundering-as-a-service is anticipated to be an integral part of the CaaS portfolio in the near future which will decrease the manual recruiting of mules and possibly remove it entirely.
- The development of business email compromise (BEC) swindles will continue to flourish with progressively directed attacks. BEC selected as targets of cyber-attacks generally had relationships with overseas suppliers and performed online money transfers [19]. During these attacks, the cybercriminals will mimic the merchants or clients to compromise monetary transfers and send the money to attacker owned accounts.
- As alluded to in some of the other predictions, cooperation and specialization are occurring in the world of cybercrime. Cybercrime has evolved to be performed by coordinated units of hackers. Specialization in different forms of cybercrime is also occurring including the publishing of viruses, the theft of confidential information, the performance of DDoS attacks, and the compromise of networks owned by organizations [26]. Collaboration and specialization enable the execution of extremely complex and destructive operations that an individual hacker may not be able to perform alone.
- Cooperation between nation-state threat actors and cybercriminals is an expanding threat with broad repercussions. Nation states can offer cybercriminals a large number of resources and skills to execute advanced attacks, while cybercriminals seek monetary gain and are inclined to work for larger compensation [31]. Together, these considerations make it predictable that increasingly advanced cybercrime will occur.
- Small-medium businesses (SMBs) are expected to become increasingly targeted due to the fact that they lack strong threat detection and prevention controls.
- Cyberactivism is a trending type of cybercrime in which protesters are struggling for a specific political cause. One main focus is to interfere with the operations of an organization’s website to send a message to management or to communicate knowledge regarding harmful activities performed by an organization.
- Supply chains will continue to be targeted by cybercriminals through selected vulnerabilities concentrating on third-party provided components within an organization’s environment.
- The proliferation of encrypted communication by cybercriminals is continuing to increase. This is important for cybercriminals because encrypted communications retain anonymity and are challenging to track [22]. Law enforcement agencies are severely hampered by encrypted communications as this makes it extremely tricky to decrypt the communications with details of the criminal activities.
- Cryptocurrency specifically Bitcoin has developed into the utmost prevalent ransom payout mechanism due to its anonymity, decentralization, and value.
- Unpatched vulnerabilities remain a preferred path of compromise by cybercriminals who continuously search the internet for instances of these vulnerabilities. Upon discovery of an instance of the vulnerability, the cybercriminals will exploit the vulnerability to compromise the system.
- Remote Desktop Protocol (RDP) has evolved into a primary entry point for cybercriminals to obtain a foothold in an organization with targets with SMBs typically being targeted [23]. Credentials for RDP grant remote access into an organization’s ecosystem which can be used to exfiltrate data or to lock access to critical systems.
- 5G cellular has the capacity to relay information 300 percent quicker than 4G cellular along with the capability to integrate more individuals and computing equipment due to IoT technology. In turn, 5G has manifested into a target for cybercriminals to make their malicious operations more expedient and efficient.
- As organizations integrate big data architecture into their operations, they have begun to gather large amounts of behavioral data regarding clients, vendors, and partners ranging from energy usage to financial information as well as usage of social networking platforms. With this expansion of data collection, cybercriminals continue to target and exploit big data infrastructure components.
- The latest online applications make use of a number of contemporary technologies including virtual reality, augmented reality, and mixed reality which provide end users with an extremely innovative interface. These technologies have virtual resources associated with the accounts related to the users making them ongoing targets for cybercriminals and attacks targeting these resources are expected to rise [10].
5. Discussion
Understanding Cybercriminal Behavior
The Role of Economic Instability
The Impact of Anonymity and Deterrence
Challenges in Cyber Law
6. Conclusion
7. Directions of Future Study
Author Contributions
Funding
Availability of Data and Materials
Acknowledgements
Conflict of Interest
Authors’ Information
References
- Zhang, H., & Zou, F. (2020). A Survey of the Dark Web and Dark Market Research. In 2020 IEEE 6th International Conference on Computer and Communications (ICCC). [CrossRef]
- Schäfer, M., Fuchs, M., Strohmeier, M., Engel, M., Liechti, M., & Lenders, V. (2019). BlackWidow: Monitoring the Dark Web for Cyber Security Information. 2019 11th International Conference on Cyber Conflict (CyCon), 1-21. [CrossRef]
- Cascavilla, G., Tamburri, D. A., & Van Den Heuvel W. J. (2021). Cybercrime threat intelligence: A systematic multi-vocal literature review. Computers & Security, 105. doi: . [CrossRef]
- Adewopo, V., Gonen, B., & Adewopo, F. (2020). Exploring Open Source Information for Cyber Threat Intelligence. In 2020 IEEE International Conference on Big Data (Big Data). [CrossRef]
- Samtani, S., Zhu, H., & Chen, H. (2020). Proactively Identifying Emerging Hacker Threats from the Dark Web: A Diachronic Graph Embedding Framework (D-GEF). ACM Transactions on Privacy and Security, 23(4), 1–33. [CrossRef]
- Holt, T. J. (2012). Examining the Forces Shaping Cybercrime Markets Online. Social Science Computer Review, 31(2), 165–177. [CrossRef]
- Rawat, R., Ajagbe, S. A., & Oki O. A. (2022). Techniques for Predicting Dark Web Events Focused on the Delivery of Illicit Products and Ordered Crime. [CrossRef]
- Rudesill, D. S., Caverlee, J., & Sui, D. (2015). The Deep Web and the Darknet: A Look Inside the Internet’s Massive Black Box. SSRN Electronic Journal. [CrossRef]
- Basheer, R. & Alkhatib, B (2021). Threats from the Dark: A Review over Dark Web Investigation Research for Cyber Threat Intelligence. Journal of Computer Networks and Communications, 2021, . [CrossRef]
- Świątkowska, J. (2020). Tackling cybercrime to unleash developing countries’ digital potential. https://pathwayscommission.bsg.ox.ac.uk/sites/default/files/2020-01/tackling_cybercrime_to_unleash_developing_countries_digital_potential.pdf/.
- Townsend, K. (2022). Understanding the Evolution of Cybercrime to Predict its Future. SecurityWeek, https://www.securityweek.com/understanding-evolution-cybercrime-predict-its-future/.
- Security, H. W. (2022). The Evolution of Cybercrime: Why the Dark Web is Supercharging the Threat Landscape and How to Fight Back. HP Wolf Security, https://threatresearch.ext.hp.com/evolution-of-cybercrime-report/.
- Enterprise, B. (2022). What Are The Biggest Cyber Threats of The Future? BitDefender. https://businessinsights.bitdefender.com/what-are-the-biggest-cyber-threats-of-the-future/.
- Kelly, P. (2023). Trends in Cybercrime in 2022 and Beyond. https://blog.govnet.co.uk/technology/trends-in-cybercrime-in-and-beyond/.
- Kaspersky. (2019). 4 Cyber Security Trends to Keep an Eye On. https://www.kaspersky.com/resource-center/preemptive-safety/cyber-security-trends/.
- Top Cybersecurity Threats. (2023). University of San Diego Online Degrees. https://onlinedegrees.sandiego.edu/top-cyber-security-threats/#threats-and-trends/.
- Fortinet. (2022). Cyber Threat Predictions for 2023 An Annual Perspective by FortiGuard Labs. https://www.fortinet.com/content/dam/maindam/PUBLIC/02_MARKETING/02_Collateral/WhitePaper/WP-threat-prediction-2023.pdf/.
- Micro, T. (2022). Future/Tense: Trend Micro Security Predictions 2023 - Security Predictions. https://www.trendmicro.com/vinfo/us/security/research-and-analysis/predictions/2023/.
- Eira, A. (2019). 16 Latest Cybercrime Trends & Predictions for 2021/2022 and Beyond. Financesonline.com. https://financesonline.com/cybercrime-trends/.
- Sindelar, E. & Ferguson, R. (2021). Cybercrime: Today and the Future. Trend Micro, https://www.trendmicro.com/en_us/ciso/21/h/cybercrime-today-and-the-future.html/.
- Weigand, S. (2023). 2023 threat predictions: Beware ‘economic uncertainty’ for the cybersecurity community. SC Media. https://www.scmagazine.com/feature/third-party-risk/2023-threat-predictions-beware-economic-uncertainty-for-the-cybersecurity-community/.
- Carmiel, D. (2022). Council Post: 5 Trends Shaping The Future Of Cybercrime Threat Intelligence. Forbes. https://www.forbes.com/sites/forbestechcouncil/2022/12/19/5-trends-shaping-the-future-of-cybercrime-threat-intelligence/.
- Glas, K. (2021). What Will the Future of Cybercrime Look Like? TFOT. https://thefutureofthings.com/15904-what-will-the-future-of-cybercrime-look-like/.
- Boehm, J., Lewis, C., Li, K., Wallance, D., & Dias, D. (2022). Cybersecurity trends: Looking over the horizon. McKinsey, https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/cybersecurity/cybersecurity-trends-looking-over-the-horizon/.
- Ryan, P. (2023). How the future of cyber crime could involve fake voice messages from loved ones? The National News. https://www.thenationalnews.com/uae/2023/03/17/how-the-future-of-cybercrime-could-involve-fake-voice-messages-from-loved-ones/.
- Morgan, S. (2020). Global Cybercrime Damages Predicted To Reach $6 Trillion Annually By 2021. Cybercrime Magazine. https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/.
- Labs, F. (2022). Threat Predictions for 2023: New Attack Surfaces and Threats Emerge as Cybercrime Expands. Fortinet Blog. https://www.fortinet.com/blog/threat-research/2023-threat-predictions-new-attack-surfaces-threats-emerge-cybercrime-expands/.
- Mador, Z. (2022). Infiltrating the Dark Web for Threat Intelligence Collaboration. CPO Magazine. https://www.cpomagazine.com/cyber-security/infiltrating-the-dark-web-for-threat-intelligence-collaboration/.
- Bowers, K. (2018). Dark Web Chatter Helpful in Predicting Real World Hacks, Firm Says. SecurityWeek. https://www.securityweek.com/dark-web-chatter-helpful-predicting-real-world-hacks-firm-says/.
- Paganini, P. (2020). The Crimeware-as-a-Service model is sweeping over the cybercrime world. Here’s why. CyberNews. https://cybernews.com/security/crimeware-as-a-service-model-is-sweeping-over-the-cybercrime-world/.
- Cerulus, L. (2021). One group that’s embraced AI: Criminals. POLITICO. https://www.politico.eu/article/artificial-intelligence-criminals/.
- Consulting, P., A. (2023). Why the ‘dark web’ is becoming a cyber security nightmare for businesses. PA Consulting. https://www.paconsulting.com/insights/why-the-dark-web-is-becoming-a-cyber-security-nightmare-for-businesses/.
- Singh, T. (2024). Dark Web Dynamics: Investigating Cybercrime Trends And Regulatory Responses In The Digital Age. Revista Electronica de Veterinaria, 25(1S), 612-618. [CrossRef]
- Montasari, R., & Hopcraft, B. (2024). Securing Cyberspace: Addressing the Dark Web and Cybercrime Underreporting. In Space Law Principles and Sustainable Measures, 185-198. Cham: Springer Nature Switzerland. [CrossRef]
- Kaur, G., Mukherjee, D., Moza, B., Pahwa, V., Kaur, K., & Kaur, K. (2024). The dark web: A hidden menace or a tool for privacy protection. IP International Journal of Forensic Medicine and Toxicological Sciences, 8(4), 160-167. [CrossRef]
- Sahu, S., Verma, P., & Kashyap, P. (2023). Surveying the Dark Web: An overview of its Structure, Content, and Challenges. International Journal of Gender, Science and Technology, 12(2), 46-54. https://ijgst.com/admin/uploadss/Paper8-IJGST-DECEMBER-2023.pdf.
- Anzaruddin, M., Shoaib, S. I., Dangwal, I., Nand, P., Agarwal, I., & Astya, R. (2024). The Enigma of the Dark Web: A Duality of Unrestricted Liberty and Unlawfulness. In 2024 Sixth International Conference on Computational Intelligence and Communication Technologies (CCICT), IEEE, 273-278. [CrossRef]
- Biedron, S. R. (2024). Cybercrime in the Digital Age (Doctoral dissertation, University of Oxford).
- Malik, S., Rana, A., & Chauhan, M. (2024). The Dark Web: An Analysis of its Structure, Activities and Implications. Journal of Network & Information Security, 12(1), 39-46.
- Holmes, L. (2024). Cybercrime. In Rethinking Organised Crime. Edward Elgar Publishing, 26-42. [CrossRef]
- Özaşçılar, M., Çalıcı, C., & Vakhitova, Z. (2024). Examining cybercrime victimisation among Turkish women using routine activity theory. Crime Prevention and Community Safety, 26(1), 112-128.
- Steinmetz, K. F., & Pratt, T. C. (2024). Revisiting the tautology problem in rational choice theory: What it is and how to move forward theoretically and empirically. European Journal of Criminology.
- Meehan, T., Forrester, L., & Haaja, J. A. (2024). Sociological Theories of Crime: Strain Theories. Introduction to Criminology and Criminal Justice, Open Educational Resources Collective.
- Kłusek, M. (2024). How acceptable is optimal deterrence?. International Review of Law and Economics, 78, 106194.
- Martin Coesel, A., Biancardi, B., & Buisine, S. (2024). A theoretical review of the Proteus effect: understanding the underlying processes. Frontiers in Psychology, 15, 1379599.
- Ruddin, I., & SGN, S. Z. (2024). Evolution of Cybercrime Law in Legal Development in the Digital World. Jurnal Multidisiplin Madani, 4(1), 168-173.
- Li, Z. (2024). The Evolution of Internet Law in The Digital Age. International Journal of Education and Humanities, 13(2), 124-126.
- Buçaj, E., & Idrizaj, K. (2025). The need for cybercrime regulation on a global scale by the international law and cyber convention. Multidisciplinary Reviews, 8(1), 2025024-2025024.
- Joshi, A. (2024). Study of Cybersecurity Laws and Regulations. Indian Journal of Law, 2(3), 7-14.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




