1. Introduction
Wireless networks have transformed the way people and organizations communicate, offering flexibility and mobility that were previously unattainable with wired systems. As society becomes increasingly dependent on wireless communication technologies such as Wi-Fi, 4G, 5G, and the Internet of Things (IoT), securing these networks against emerging cyber threats has become a critical priority. The widespread adoption of wireless networks across various sectors, including healthcare, finance, government, and smart cities, has made them an attractive target for malicious actors, who continually develop new methods to exploit vulnerabilities.
In recent years, the scope of potential attacks on wireless networks has expanded significantly. Traditional threats, such as eavesdropping and man-in-the-middle (MitM) attacks, have evolved into more sophisticated forms, leveraging artificial intelligence (AI) and machine learning (ML) techniques to automate and optimize attack vectors. Furthermore, the integration of emerging technologies such as 5G and IoT has introduced new vulnerabilities, particularly as these devices often lack the robust security mechanisms found in traditional computing systems.
The adoption of IoT, in particular, has drastically increased the number of devices connected to wireless networks, many of which are designed with minimal security measures. These devices, ranging from household appliances to industrial control systems, often have limited processing power and storage, making it challenging to implement strong encryption and authentication protocols. As a result, wireless networks supporting IoT are becoming more vulnerable to attacks such as distributed denial of service (DDoS), unauthorized access, and data interception.
To address these emerging threats, a range of security protocols has been developed over the years. Standards such as WPA3 (Wi-Fi Protected Access 3), the 802.11i standard, and various forms of Extensible Authentication Protocol (EAP) have introduced advanced encryption methods, improved authentication processes, and stronger protection against known attacks. However, as threats continue to evolve, so must the protocols designed to defend against them. This has led to the exploration of innovative security solutions, such as blockchain-based security frameworks and AI-driven anomaly detection systems, which offer promising ways to secure wireless networks in the face of increasingly sophisticated cyberattacks.
This paper aims to provide an in-depth analysis of the emerging threats targeting wireless networks and to evaluate the effectiveness of current security protocols in mitigating these risks. The study also examines the potential of advanced solutions like blockchain technology, quantum cryptography, and AI in addressing future challenges. Through a combination of case studies, empirical data, and theoretical frameworks, this article seeks to offer practical recommendations for enhancing the security of wireless networks in both current and future contexts.
In the following sections, the article will explore the evolution of wireless technologies, discuss the nature of the threats these technologies face, and analyze the protocols currently used to secure them. It will also present emerging solutions and consider the challenges and future directions in wireless network security. As wireless technologies continue to evolve, it is crucial to develop a holistic understanding of both the threats they face and the solutions available to mitigate them.
2. Emerging Threats in Wireless Networks
Wireless networks are increasingly being adopted across various sectors due to their convenience and cost-efficiency. However, their open and dynamic nature exposes them to a wide array of threats. As new technologies such as 5G, the Internet of Things (IoT), and AI become more integrated into wireless communication, the complexity and number of vulnerabilities increase, allowing for more sophisticated attacks. This section explores the evolution of wireless technologies, identifies common threats, and examines the future threat landscape.
2.1. Evolution of Wireless Technologies (5G, IoT, AI)
With the rapid growth of wireless networks, significant advancements have occurred, particularly in 5G, IoT, and AI technologies. While these innovations enhance connectivity and create new opportunities for users, they simultaneously introduce new attack vectors.
5G Networks: 5G offers higher speeds, lower latency, and broader bandwidth, making it ideal for mission-critical applications. However, these features make 5G networks a target for cybercriminals. The network’s increased reliance on software-defined networking (SDN) and network function virtualization (NFV) creates a larger attack surface, with more points of entry for potential attackers.
Internet of Things (IoT): IoT devices, ranging from smart home gadgets to industrial sensors, often operate with minimal security due to resource constraints. Their widespread adoption in critical industries (e.g., healthcare, manufacturing) amplifies the risk. Many IoT devices lack proper encryption and authentication mechanisms, leaving them vulnerable to hijacking and data breaches.
Artificial Intelligence (AI): While AI can bolster network defenses through machine learning-based threat detection, it can also be weaponized by attackers. AI-driven attacks can learn from network defenses, adapt to security protocols, and automate the execution of highly targeted, sophisticated intrusions.
2.2. Common Threats
Wireless networks face several well-known threats, many of which are exacerbated by the introduction of newer technologies. These include, but are not limited to:
Eavesdropping: The interception of wireless communication by unauthorized parties is one of the most prevalent threats. Attackers can exploit unencrypted or weakly encrypted connections to capture sensitive data in transit, including passwords, personal information, and proprietary business data. This risk is heightened in public Wi-Fi networks that lack adequate protection.
Man-in-the-Middle (MitM) Attacks: In MitM attacks, an attacker intercepts communication between two parties without their knowledge, enabling the attacker to alter or steal information. Such attacks are particularly dangerous in financial and corporate environments where real-time, secure communication is critical. Public Wi-Fi networks are especially vulnerable to MitM attacks due to their open access nature.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks: These attacks overwhelm a wireless network or device with traffic, rendering it inaccessible to legitimate users. DDoS attacks often target specific services within wireless networks, such as IoT devices or access points, effectively crippling the network’s functionality.
Spoofing: Attackers impersonate legitimate devices or users within a network to gain unauthorized access. In wireless networks, spoofing attacks often involve exploiting weak authentication protocols, tricking the network into granting access to the attacker as a trusted entity.
Replay Attacks: This involves intercepting and retransmitting valid data at a later time, often to gain unauthorized access or perform malicious activities. Even when encryption is used, if session keys are not frequently updated, attackers can capture and reuse valid credentials.
2.3. Future Threat Landscape
The future of wireless networks brings both opportunities and challenges. As technologies such as AI, quantum computing, and edge computing advance, the sophistication of attacks will likely increase.
AI-Driven Attacks: AI presents both a defensive and offensive tool in cybersecurity. On the offensive side, attackers are increasingly using AI to conduct reconnaissance, automate phishing, and deploy adaptive malware. AI-powered attacks can dynamically change their patterns based on how a target responds, making them difficult to detect and counter using traditional methods.
Quantum Computing: As quantum computing becomes a reality, it threatens to undermine current encryption standards. Quantum computers have the potential to break widely used encryption algorithms, such as RSA and ECC, by rapidly solving complex mathematical problems. Although quantum computing is still in its early stages, it represents a long-term threat that will require the development of quantum-resistant encryption algorithms.
IoT Device Proliferation: With the projected growth of IoT devices reaching billions in the coming years, securing these devices will become increasingly difficult. Many IoT devices, especially those in consumer environments, are designed with cost-efficiency in mind, often at the expense of robust security features. These devices will continue to be weak points in wireless networks, providing attackers with easy entry points.
5G Vulnerabilities: As 5G becomes widely deployed, attackers will target the more complex infrastructure and new architectural components it introduces, such as SDN and NFV. Multi-access edge computing (MEC), a key feature of 5G, will also present new vulnerabilities by moving computing resources closer to the network edge, potentially exposing them to tampering.
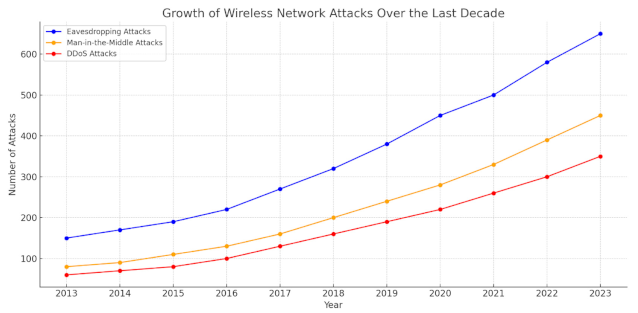
Graph Idea: A graph could depict the growth of various types of wireless network attacks (e.g., eavesdropping, MitM, DDoS) over the last decade, showing how the number and severity of attacks have increased as new technologies have emerged.
While wireless networks offer significant advantages, they are vulnerable to a variety of emerging threats. As these threats continue to evolve, it is critical to develop and adopt more advanced security measures that can mitigate the risks posed by new technologies such as 5G, IoT, and AI. The following sections of this paper will examine the existing protocols designed to protect wireless networks and explore emerging solutions that aim to address the challenges posed by these evolving threats.
3. Key Protocols for Wireless Network Security
Wireless networks, despite their convenience and widespread adoption, are particularly vulnerable to security breaches due to their open and shared nature. To mitigate these risks, various security protocols have been developed over time to protect the integrity, confidentiality, and availability of wireless communications. In this section, we will explore the most significant protocols that are currently employed to secure wireless networks, focusing on their features, strengths, and limitations. The primary protocols discussed are WPA3 (Wi-Fi Protected Access 3), the 802.11i Standard, and the Extensible Authentication Protocol (EAP).
3.1. WPA3 (Wi-Fi Protected Access 3)
WPA3 is the latest security protocol developed by the Wi-Fi Alliance, introduced in 2018 as the successor to WPA2. It addresses many of the vulnerabilities discovered in previous generations of wireless security protocols and brings robust new features designed to enhance the security of wireless communications.
Key Features:
Stronger Encryption: WPA3 uses AES-GCMP (Galois/Counter Mode Protocol), which is considered much more secure than the previous CCMP (Cipher Block Chaining Message Authentication Code Protocol) used in WPA2.
Simultaneous Authentication of Equals (SAE): This replaces the Pre-Shared Key (PSK) method, making it harder for attackers to exploit weak passwords through offline dictionary attacks. SAE provides forward secrecy, ensuring that if the encryption key is compromised, past communications cannot be decrypted.
Enhanced Protection in Public Networks: WPA3 introduces Opportunistic Wireless Encryption (OWE), which encrypts data even in open Wi-Fi networks without requiring authentication.
Simplified IoT Security: WPA3 includes Easy Connect, a feature aimed at improving the security of IoT devices, which are often targeted due to their weak security configurations.
Strengths:
Stronger defense against brute-force and dictionary attacks.
Improved security for public networks, which are often left unsecured.
Ensures higher levels of encryption even for devices using weak passwords.
Suitable for IoT devices, where traditional security measures are difficult to implement.
Limitations:
WPA3 is not universally supported by all devices, particularly older hardware, creating compatibility issues.
The transition from WPA2 to WPA3 has been slow, leaving many networks still vulnerable to WPA2’s weaknesses.
It does not provide full protection against physical attacks on devices, such as key extraction from compromised endpoints.
3.2. 802.11i Standard
The 802.11i standard, also known as WPA2, was ratified by the IEEE (Institute of Electrical and Electronics Engineers) in 2004. It is the most widely adopted wireless security protocol to date and introduced a significant enhancement over its predecessor, WPA, by employing stronger encryption methods and improved authentication mechanisms.
Key Features:
AES Encryption: The Advanced Encryption Standard (AES) replaced the weak WEP (Wired Equivalent Privacy) encryption and the transitional TKIP (Temporal Key Integrity Protocol), providing a much stronger encryption framework.
Robust Security Network (RSN): The RSN framework ensures that devices use the strongest possible encryption available, preventing older or weaker encryption protocols from being used in a handshake process.
Key Management: 802.11i uses the 802.1X authentication framework for key management, enabling dynamic key allocation based on user authentication rather than pre-shared keys (PSK), which are more vulnerable to attacks.
Strengths:
AES encryption is virtually unbreakable, ensuring a high level of data protection.
Dynamic key management minimizes the risk of key reuse and reduces vulnerability to certain types of attacks, such as the KRACK (Key Reinstallation Attack).
RSN ensures that networks always use the strongest possible encryption, offering strong protection against many common wireless threats.
Limitations:
While WPA2 (802.11i) significantly improves upon WPA, it is still vulnerable to KRACK, an exploit that targets the four-way handshake process during key exchange.
As technology has evolved, attackers have found new ways to target WPA2, making it necessary to adopt even stronger protocols like WPA3.
Table Idea.
A comparison of WPA2 (802.11i) and WPA3 security features and vulnerabilities.
Table Idea.
A comparison of WPA2 (802.11i) and WPA3 security features and vulnerabilities.
| Feature |
WPA2 (802.11i) |
WPA3 |
| Encryption Method |
AES + TKIP |
AES-GCMP |
| Key Management |
PSK / 802.1X |
SAE (Simultaneous Authentication of Equals) |
| Public Network Protection |
None |
Opportunistic Wireless Encryption (OWE) |
| IoT Device Compatibility |
Limited |
Enhanced (Easy Connect) |
| Vulnerability to KRACK Attack |
Yes |
No |
3.3. Extensible Authentication Protocol (EAP)
EAP is a flexible authentication framework used extensively in wireless networks, especially in enterprise settings. It is not a standalone protocol but a framework that supports multiple authentication mechanisms, allowing different types of credentials (e.g., passwords, certificates, tokens) to be used for authenticating users.
Key Features:
Flexible Authentication: EAP supports multiple methods of authentication, such as EAP-TLS (Transport Layer Security), EAP-TTLS (Tunneled Transport Layer Security), and PEAP (Protected Extensible Authentication Protocol), offering versatility based on security requirements.
Strong Mutual Authentication: Methods such as EAP-TLS provide strong mutual authentication between the client and server, ensuring that both parties can verify each other’s identities.
Support for Smart Cards and Biometrics: EAP can be configured to support advanced authentication methods like smart cards or biometric verification, providing robust security for high-risk environments.
Strengths:
Provides highly secure mutual authentication, particularly when using certificate-based methods like EAP-TLS.
Flexibility to choose the appropriate authentication method based on the network’s security needs.
Widely used in enterprise environments for secure Wi-Fi access.
Limitations:
Implementation can be complex and costly, particularly in smaller networks that lack the necessary infrastructure to manage certificate-based authentication.
Vulnerabilities can arise if weaker EAP methods, such as EAP-MD5, are used, which are susceptible to password-based attacks.
EAP does not encrypt data directly; it relies on protocols like WPA or WPA2 for data encryption, making it a critical but complementary security framework.
While wireless networks offer unparalleled flexibility and convenience, they also pose significant security challenges. Protocols such as WPA3, 802.11i, and EAP provide robust security mechanisms to mitigate common vulnerabilities, but they must continually evolve to stay ahead of emerging threats. Understanding the strengths and limitations of each protocol is essential for implementing secure wireless networks, particularly in an age where the adoption of technologies like IoT and 5G continues to expand.
4. Emerging Solutions for Wireless Network Security
As wireless networks continue to grow in scale and importance, traditional security protocols such as WPA3, though effective, may not be sufficient to tackle the increasing sophistication of cyber threats. Emerging technologies, driven by advancements in fields like blockchain, artificial intelligence (AI), and quantum computing, are offering novel approaches to securing wireless communications. This section explores some of the most promising solutions currently being developed to mitigate these threats.
4.1. Blockchain-Based Security for Wireless Networks
Blockchain technology, originally developed for secure financial transactions in decentralized systems, has emerged as a promising solution for wireless network security. Its decentralized nature and cryptographic foundation make it ideal for preventing various types of attacks, particularly in environments with numerous interconnected devices, such as the Internet of Things (IoT).
Decentralized Security Frameworks: Blockchain eliminates the need for a central authority by creating a distributed ledger where each node in the network verifies and records transactions or data exchanges. This makes it extremely difficult for attackers to compromise an entire network since the breach of a single node does not affect the entire system.
Key Use Cases: One of the key applications of blockchain in wireless networks is for securing IoT devices. With IoT, thousands of devices are interconnected, each representing a potential entry point for attackers. Blockchain can help authenticate devices, secure data exchanges, and maintain an immutable log of activity to detect anomalies or breaches.
Smart Contracts: Another significant application of blockchain is in automating security policies using smart contracts. These contracts execute predefined rules automatically when certain conditions are met. For instance, smart contracts can be used to revoke access to a device if it exhibits suspicious behavior, ensuring real-time responses to threats.
Example: A blockchain-based network framework can secure device-to-device communication in a smart city, where thousands of sensors and devices interact in real-time. If a malicious entity tries to breach the network, the immutable blockchain ledger can quickly identify and isolate compromised nodes, preventing lateral movement across the network.
4.2. AI-Driven Threat Detection and Response
Artificial intelligence (AI) has become a pivotal tool in enhancing the security of wireless networks by offering dynamic and adaptive protection measures. Traditional security protocols often rely on predefined rules, which can struggle to keep up with sophisticated, rapidly evolving threats. AI-based systems, however, can learn from past behaviors and adapt to emerging threats in real-time.
Machine Learning for Anomaly Detection: One of the primary applications of AI in wireless network security is machine learning (ML)-based anomaly detection. By analyzing vast amounts of data from network traffic, machine learning models can identify patterns that indicate potential threats, such as unusual login attempts, suspicious data flows, or abnormal network activity. These systems become smarter over time, improving their ability to detect both known and unknown threats.
Predictive Analytics: AI can also leverage predictive analytics to forecast potential attacks. By analyzing historical data and identifying trends, AI systems can predict vulnerabilities before they are exploited. This is particularly useful in wireless environments where threats can emerge rapidly due to device mobility and ever-changing network topologies.
Automated Response Mechanisms: AI-driven systems can not only detect threats but also initiate automated responses. For example, if a man-in-the-middle (MitM) attack is detected, AI systems can immediately sever the connection, notify administrators, and initiate protocols to secure sensitive data, all without human intervention.
Example: In an enterprise wireless network, an AI-powered intrusion detection system can detect unusual traffic spikes or unauthorized access attempts, flagging them for investigation or automatically blocking the source of the potential attack. Over time, the system will become more efficient at identifying subtle indicators of malicious activity.
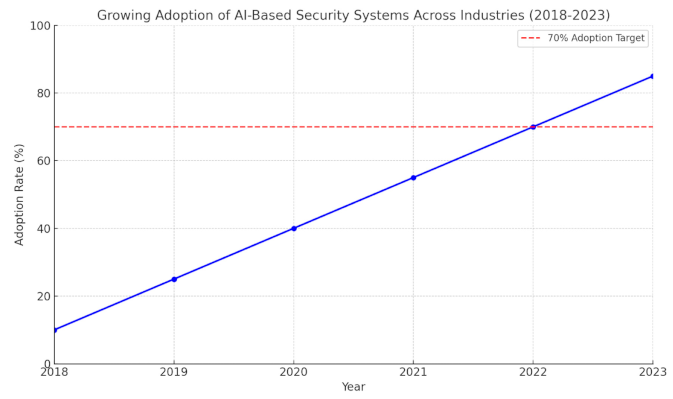
Graph Idea: A graph can be used here to show the growing adoption of AI-based security systems across industries, highlighting how many enterprises are integrating AI-driven solutions into their wireless network infrastructure.
4.3. Quantum Cryptography
Quantum cryptography represents the future of secure wireless communications, offering a level of security theoretically impervious to classical cyberattacks. As quantum computing advances, traditional encryption methods could eventually become obsolete, as quantum computers will be able to break current cryptographic codes with relative ease. Quantum cryptography, particularly Quantum Key Distribution (QKD), is designed to provide secure communication channels that even quantum computers cannot compromise.
Quantum Key Distribution (QKD): The primary application of quantum cryptography is QKD, which enables the secure sharing of encryption keys over a network. In QKD, keys are transmitted as quantum bits (qubits) over a quantum channel. The unique property of quantum particles is that they cannot be observed without altering their state. This means that any attempt to intercept or eavesdrop on the key exchange will be immediately detected, rendering the key invalid and alerting the network to the presence of an attacker.
Use in Wireless Networks: In wireless networks, QKD can be particularly useful for securing high-value communications that require absolute security, such as government or military communications. As wireless networks expand to support critical infrastructure, the need for quantum-resistant security solutions becomes paramount.
Challenges: While quantum cryptography is promising, it is still in its infancy and faces several challenges, including the need for specialized hardware and difficulties in transmitting quantum signals over long distances. Nevertheless, researchers are actively working on overcoming these limitations to make quantum cryptography more widely accessible for wireless networks.
Example: In a secure military communication network, quantum cryptography can ensure that all transmitted data remains confidential and tamper-proof. Any attempt by an adversary to intercept the communication would be immediately detected, triggering defensive countermeasures.
4.4. Integration of Blockchain, AI, and Quantum Cryptography
In many advanced security systems, the integration of multiple emerging technologies offers the best defense. By combining blockchain’s decentralized authentication, AI’s adaptive threat detection, and quantum cryptography’s future-proof encryption, a multi-layered approach to wireless network security can be created.
Synergy Between Technologies: Blockchain can secure device identities and interactions, AI can continuously monitor network traffic for signs of intrusion, and quantum cryptography can protect sensitive data transmissions. Together, these technologies form a cohesive security framework that addresses both present and future threats.
Future Trends: As wireless networks continue to evolve with the growth of 5G and IoT, the convergence of these emerging technologies will be critical in defending against increasingly sophisticated cyberattacks.
Emerging technologies such as blockchain, artificial intelligence, and quantum cryptography are transforming wireless network security, offering advanced solutions to counteract the growing complexity of threats. While each technology provides unique benefits, their integration offers the most robust protection. As threats to wireless networks continue to evolve, leveraging these cutting-edge technologies will be essential for securing communications in a rapidly advancing digital landscape.
5. Case Studies
To illustrate the practical challenges and solutions in securing wireless networks against emerging threats, this section presents two detailed case studies. These real-world examples highlight vulnerabilities in IoT security and the successful application of blockchain technology in securing wireless communication systems.
5.1. IoT Security Vulnerabilities: The Mirai Botnet Attack
Background:
In October 2016, the Mirai Botnet Attack exploited vulnerabilities in IoT devices to launch one of the largest Distributed Denial of Service (DDoS) attacks in history. The attack targeted the domain name system (DNS) provider Dyn, disrupting major websites like Twitter, Netflix, and PayPal. The root cause of this attack was the lack of robust security measures in millions of IoT devices, such as cameras and DVRs, which were compromised and used to form the Mirai botnet.
Details of the Attack:
Mirai took advantage of weak default passwords and open Telnet ports on IoT devices, allowing attackers to gain unauthorized access. The widespread use of default credentials across IoT devices, combined with the lack of firmware updates, made it easy for attackers to commandeer these devices into a botnet.
Once infected, the compromised devices communicated with a command-and-control server, coordinating a massive DDoS attack. The volume of traffic generated by these devices overwhelmed Dyn’s servers, causing a significant disruption in internet services across the United States and Europe.
Lessons Learned:
The Mirai attack underscored the need for stricter security protocols for IoT devices, particularly in terms of enforcing secure credential management, automatic firmware updates, and encryption of wireless communications.
Future IoT devices should implement more secure wireless communication protocols, such as WPA3, and utilize blockchain-based frameworks for better management of device identities and secure data transmissions.
5.2. Blockchain Implementation in Secure Wireless Networks: The Case of Xage Security
Background:
Xage Security, a blockchain-based security company, has successfully implemented blockchain technology to secure wireless networks in industrial IoT environments. The decentralized nature of blockchain makes it ideal for ensuring the integrity, confidentiality, and availability of wireless communication, particularly in sectors like energy, manufacturing, and transportation, where IoT networks play a critical role.
Details of the Implementation:
Xage’s solution integrates blockchain into wireless networks to create a distributed ledger that records device identities and network access control. Each device in the network is registered and authenticated via blockchain, ensuring that only authorized devices can communicate over the wireless network.
Blockchain ensures that all transactions and communications across the wireless network are cryptographically secured. If an attacker attempts to tamper with data or gain unauthorized access, the blockchain ledger identifies discrepancies, immediately alerting the system to the potential breach.
Unlike traditional centralized security models, blockchain eliminates the risk of a single point of failure. In Xage’s case, if one node or device in the wireless network is compromised, the blockchain system continues to function securely, as all other nodes maintain a verifiable, immutable copy of the transaction history.
Impact on Wireless Networks:
Blockchain provides a robust solution to the issue of identity management and access control, particularly in large wireless IoT networks where devices frequently communicate over unsecured wireless protocols.
By decentralizing security management, blockchain reduces the risk of attacks like MitM (Man-in-the-Middle) and DDoS. Xage’s case study shows how this decentralized approach enhances the overall resilience of wireless networks.
Lessons Learned:
While blockchain can significantly enhance wireless network security, it requires optimization to handle the high transaction throughput required in large-scale IoT environments.
Industries that rely heavily on wireless IoT networks should explore blockchain-based solutions for secure communication and data integrity. Future research should focus on improving the scalability of blockchain systems to meet the demands of global wireless communication networks.
Summary of Case Studies
These case studies illustrate two critical dimensions of securing wireless networks:
The Mirai botnet attack highlights the dangers posed by unsecured IoT devices and weak wireless protocols. The lessons learned emphasize the need for stronger security standards and innovative solutions like blockchain-based identity management.
Xage Security’s blockchain implementation showcases how decentralized security frameworks can address wireless communication vulnerabilities, particularly in industrial IoT environments. Blockchain offers promising solutions for mitigating common threats such as unauthorized access and data tampering.
Together, these cases underscore the need for continuous adaptation and innovation in wireless network security protocols. The integration of new technologies such as blockchain and AI is critical for staying ahead of emerging threats in wireless communication systems.
6. Challenges and Future Directions
Securing wireless networks in the face of emerging threats is a dynamic and multifaceted challenge. As technological advancements in areas such as 5G, IoT, and artificial intelligence (AI) continue to evolve, they bring not only new opportunities but also significant security risks. This section explores the key challenges currently faced in wireless network security, discusses the limitations of existing solutions, and outlines future directions for enhancing wireless security to combat increasingly sophisticated threats.
6.1. Integration of New Technologies
One of the most pressing challenges is the integration of cutting-edge technologies such as 5G and IoT devices into existing wireless infrastructures. These technologies offer unprecedented speed, connectivity, and data exchange capabilities but also increase the attack surface.
5G Networks: With its high data throughput and reduced latency, 5G opens up vulnerabilities in its more complex network architecture. The introduction of network slicing, for example, enables the creation of multiple virtual networks on the same physical infrastructure. While beneficial, this also presents opportunities for attackers to exploit poorly secured network slices.
IoT Devices: IoT devices, particularly in smart homes, healthcare, and industrial settings, have been prone to security lapses due to weak authentication and lack of encryption. Many IoT devices operate on limited resources, making it difficult to implement strong security protocols. The exponential growth of IoT devices increases the probability of vulnerabilities within the system, and their interconnectivity could allow breaches to spread across networks quickly.
Future research and development should focus on creating security frameworks that can handle the complexity and high-connectivity nature of these systems. Solutions like blockchain for decentralized device authentication or edge computing for localized security management hold promise but need further refinement.
6.2. Regulatory and Compliance Issues
The global nature of wireless networks means that different regions may have varying security standards and regulations, which poses a challenge for companies that operate across borders. Regulatory bodies have yet to fully standardize the rules governing the security of 5G and IoT networks, leading to fragmented security practices.
Lack of Unified Standards: While frameworks such as the NIST Cybersecurity Framework provide guidance on securing networks, their adoption is not globally consistent. Countries that lag behind in updating their security regulations may inadvertently become gateways for cyberattacks.
Compliance Costs: Adhering to ever-evolving security standards often requires companies to continuously upgrade their systems, which can be costly. Smaller organizations may struggle to keep up with regulatory compliance, leaving their networks vulnerable.
To address these issues, international regulatory bodies need to collaborate more effectively to establish universal security protocols. There is also a need for security automation tools that can help organizations of all sizes maintain compliance without extensive manual oversight.
6.3. Scalability of Security Solutions
Another significant challenge is ensuring that security solutions can scale effectively as the size and complexity of wireless networks grow. With the proliferation of billions of IoT devices and the expansion of 5G networks, traditional security solutions often fail to meet the demands of high-speed, high-volume data transfer.
Current Limitations: Existing protocols like WPA3 provide foundational security, but they are not designed to handle the massive scale of future wireless ecosystems. Additionally, as more devices join the network, the likelihood of attack points increases, overwhelming the current security infrastructure.
Future directions in scalability include the use of AI-powered threat detection systems that can dynamically identify and mitigate security risks in real-time. Quantum cryptography, though still in its infancy, could also revolutionize wireless security by providing virtually unbreakable encryption for large-scale networks.
6.4. Adaptability to Emerging Threats
The threat landscape is constantly evolving, with new attack vectors being discovered as rapidly as countermeasures are developed. Adaptive threats, such as AI-driven malware, have the ability to learn and modify their attack patterns in real-time, making it difficult for static security solutions to provide adequate defense.
AI in Cybersecurity: While AI can be used to enhance security, it also poses a threat. Malicious actors are increasingly leveraging AI to develop more sophisticated and adaptive malware that can evade traditional security protocols. For example, AI-based attacks can simulate normal network behavior, making detection exceedingly difficult for rule-based security systems.
Future solutions will need to be adaptive and autonomous, capable of evolving in tandem with the threat landscape. This could include AI systems that actively learn from network behavior and continuously update their defense mechanisms. Collaborative threat intelligence, where data on cyber threats is shared across organizations, will also play a key role in predicting and preempting attacks.
6.5. Lack of Skilled Workforce
The rapid advancement of wireless technologies has outpaced the development of a skilled workforce capable of managing and securing these systems. The shortage of cybersecurity professionals who understand the nuances of wireless communication systems is a major barrier to effective security management.
To mitigate this, there is a need for more specialized educational programs focused on wireless security. Companies may also need to invest in automation tools to compensate for the shortage of skilled labor in this field.
Table Idea.
Table summarizing current challenges and potential future directions in wireless network security.
Table Idea.
Table summarizing current challenges and potential future directions in wireless network security.
| Challenge |
Current Solutions |
Future Directions |
| 5G Security |
Enhanced encryption |
AI-driven adaptive protocols |
| IoT Device Vulnerabilities |
Blockchain frameworks |
Secure hardware development |
| Regulatory Compliance |
WPA3 adoption |
Global security standards |
7. Future Directions
Given these challenges, it is clear that the future of wireless network security will require both technological innovation and regulatory evolution. Key areas of future research and development include:
AI-Driven Security: AI and machine learning will play a critical role in the future of wireless security by enabling real-time threat detection and automated responses. Continuous improvement of these systems is essential for handling adaptive threats.
Blockchain for IoT Security: Blockchain technology can provide a decentralized, tamper-proof method of authentication and communication for IoT devices. Its use in wireless security frameworks should be explored further.
Quantum Cryptography: As quantum computing becomes more feasible, quantum cryptography will provide a breakthrough in secure communications. Research into how quantum cryptography can be applied to wireless networks is still in its early stages, but it has the potential to offer unparalleled security.
Standardization of Security Protocols: Global regulatory bodies must collaborate to develop and enforce universal security standards for wireless networks, particularly as 5G and IoT become more ubiquitous. Standardized, globally accepted security protocols will be key to preventing large-scale breaches.
Continuous Skill Development: Addressing the cybersecurity skills gap will be crucial. Investments in education, professional development, and automation will help bridge this gap.
The challenges of securing wireless networks are significant, but by focusing on innovation and adaptability, the future of wireless security looks promising. Overcoming the hurdles of scalability, regulation, and skilled workforce shortages will be critical in the continued fight against emerging threats. With proactive measures, organizations can stay ahead of potential vulnerabilities and protect their wireless infrastructure in an increasingly connected world.
8. Conclusions
The security of wireless networks has become paramount in an age where connectivity is essential to personal, commercial, and governmental operations. This article has provided an in-depth overview of the emerging threats faced by wireless networks, elucidating the vulnerabilities introduced by advancements in technology such as 5G, the Internet of Things (IoT), and artificial intelligence (AI). These advancements, while facilitating enhanced connectivity and functionality, also create an expanded attack surface that malicious actors can exploit.
The analysis of current wireless security protocols, particularly WPA3 and the 802.11i standard, reveals a mixed picture. Although these protocols have made strides in improving encryption and authentication mechanisms, they still fall short in addressing the complexities of modern cybersecurity threats. Moreover, as demonstrated in case studies, existing protocols often struggle to keep pace with the innovative tactics employed by cybercriminals, leading to significant security breaches and data loss.
To counter these emerging threats, this paper has explored various innovative solutions that offer promising advancements in wireless security. Blockchain technology presents a decentralized approach to enhance security, ensuring integrity and transparency in communications. Similarly, the application of AI for real-time threat detection offers the potential for adaptive security measures capable of responding to evolving threats as they occur. The exploration of quantum cryptography suggests that future developments in wireless security could harness cutting-edge technology to provide unprecedented levels of protection against sophisticated attacks.
Nevertheless, several challenges remain. The integration of new technologies into existing frameworks poses substantial hurdles, particularly concerning regulatory compliance and the standardization of security measures across diverse platforms and devices. As wireless networks continue to evolve, ongoing research and collaboration among stakeholders in technology, security, and regulatory fields are essential to develop comprehensive strategies that can effectively address the challenges posed by emerging threats.
In light of the findings presented in this study, it is clear that a proactive approach to wireless network security is necessary. Organizations must not only adopt the latest protocols and technologies but also foster a culture of security awareness among users. Continuous education and training on the importance of security measures can significantly reduce the risks associated with human error, one of the most common vulnerabilities in network security.
As we move into an increasingly interconnected future, the importance of securing wireless networks cannot be overstated. This research highlights the urgent need for ongoing innovation in security protocols and the integration of advanced technologies to safeguard against the ever-evolving threat landscape. Future research should focus on exploring new methodologies for threat detection and response, as well as the implications of emerging technologies on wireless network security.
In summary, while significant progress has been made in securing wireless networks, the journey is far from over. Continuous adaptation and evolution of security measures will be crucial to protect sensitive information and maintain the integrity of wireless communications in an increasingly complex digital world.
The challenges of securing wireless networks are significant, but by focusing on innovation and adaptability, the future of wireless security looks promising. Overcoming the hurdles of scalability, regulation, and skilled workforce shortages will be critical in the continued fight against emerging threats. With proactive measures, organizations can stay ahead of potential vulnerabilities and protect their wireless infrastructure in an increasingly connected world.
References
- Tomić, I., & McCann, J. A. (2017). A survey of potential security issues in existing wireless sensor network protocols. IEEE Internet of Things Journal, 4(6), 1910-1923. [CrossRef]
- Zou, Y., Zhu, J., Wang, X., & Hanzo, L. (2016). A survey on wireless security: Technical challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), 1727-1765.
- Jatav, V. K., & Singh, V. (2014, September). Mobile WiMAX network security threats and solutions: A survey. In 2014 International Conference on Computer and Communication Technology (ICCCT) (pp. 135-140). IEEE.
- Boubiche, D. E., Athmani, S., Boubiche, S., & Toral-Cruz, H. (2021). Cybersecurity issues in wireless sensor networks: current challenges and solutions. Wireless Personal Communications, 117, 177-213.
- Chopra, G., Jha, R. K., & Jain, S. (2017). A survey on ultra-dense network and emerging technologies: Security challenges and possible solutions. Journal of Network and Computer Applications, 95, 54-78.
- Karygiannis, T., & Owens, L. (2002). Wireless Network Security:. US Department of Commerce, Technology Administration, National Institute of Standards and Technology.
- Mavoungou, S., Kaddoum, G., Taha, M., & Matar, G. (2016). Survey on threats and attacks on mobile networks. IEEE Access, 4, 4543-4572. [CrossRef]
- Grammatikis, P. I. R., Sarigiannidis, P. G., & Moscholios, I. D. (2019). Securing the Internet of Things: Challenges, threats and solutions. Internet of Things, 5, 41-70.
- Chen, Y., Xu, W., Trappe, W., & Zhang, Y. (2008). Securing emerging wireless systems: lower-layer approaches. Springer Science & Business Media.
- Yang, H., Luo, H., Ye, F., Lu, S., & Zhang, L. (2004). Security in mobile ad hoc networks: challenges and solutions. IEEE wireless communications, 11(1), 38-47. [CrossRef]
- Swessi, D., & Idoudi, H. (2022). A survey on internet-of-things security: threats and emerging countermeasures. Wireless Personal Communications, 124(2), 1557-1592.
- Aslan, Ö., Aktuğ, S. S., Ozkan-Okay, M., Yilmaz, A. A., & Akin, E. (2023). A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics, 12(6), 1333.
- Adefemi Alimi, K. O., Ouahada, K., Abu-Mahfouz, A. M., & Rimer, S. (2020). A survey on the security of low power wide area networks: Threats, challenges, and potential solutions. Sensors, 20(20), 5800.
- Marksteiner, S., Jiménez, V. J. E., Valiant, H., & Zeiner, H. (2017). An overview of wireless IoT protocol security in the smart home domain. 2017 Internet of Things Business Models, Users, and Networks, 1-8.
- Di Pietro, R., Guarino, S., Verde, N. V., & Domingo-Ferrer, J. (2014). Security in wireless ad-hoc networks–a survey. Computer Communications, 51, 1-20.
- Ichaba, M. (2018). Security threats and solutions in mobile ad hoc networks; a review. Universal J. Commun. Netw, 6(2), 7-17.
- Mahmoud, C., & Aouag, S. (2019, March). Security for internet of things: A state of the art on existing protocols and open research issues. In Proceedings of the 9th international conference on information systems and technologies (pp. 1-6).
- Tan, J., Wen, H. J., & Gyires, T. (2003). M-commerce security: the impact of wireless application protocol (WAP) security services on e-business and e-health solutions. International Journal of Mobile Communications, 1(4), 409-424.
- Savithri, G., Mohanta, B. K., & Dehury, M. K. (2022, June). A brief overview on security challenges and protocols in internet of things application. In 2022 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS) (pp. 1-7). IEEE.
- Tabrizchi, H., & Kuchaki Rafsanjani, M. (2020). A survey on security challenges in cloud computing: issues, threats, and solutions. The journal of supercomputing, 76(12), 9493-9532.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).