1. Introduction
As machine learning (ML) technologies continue to advance and find applications across a wide range of industries, ensuring the security of ML systems has become a critical concern. From healthcare to finance, transportation to cybersecurity, ML systems are increasingly used to automate decision-making processes, Analyze vast amounts of data, and optimize business operations. However, the rapid adoption of ML has brought with it new security challenges, as malicious actors seek to exploit vulnerabilities in these systems for their own gain. One of the primary threats to ML systems is the emergence of adversarial attacks. In these attacks, adversaries create specially crafted inputs that can fool ML models into making incorrect predictions or classifications. These attacks pose significant risks, particularly in safety-critical applications such as autonomous vehicles, where erroneous decisions could lead to catastrophic consequences. Similarly, adversarial attacks in financial applications could result in significant monetary losses or fraud. Another key threat to ML systems is data poisoning, where attackers manipulate the training data used to create ML models. This type of attack can undermine the integrity of ML systems and erode trust in their outputs. Model inversion is another form of attack where adversaries attempt to reverse-engineer a model to extract sensitive information, such as personally identifiable information (PII) or proprietary business data. This type of attack can have
Machine learning in cybersecurity offers innovative approaches to detecting and preventing cyber threats. It can identify patterns in large datasets to detect anomalies, classify different types of malware, and even predict potential attacks before they happen. This technology powers applications like intrusion detection systems, malware analysis tools, and user behavior analytics. Many modern challenges are facing malware investigators that make inactive investigation more troublesome and unreasonable. By leveraging ML, organizations can respond more quickly and accurately to security incidents. Implementing machine learning in cybersecurity is not without its challenges. Issues like data quality, privacy concerns, and adversarial attacks can complicate ML applications. Additionally, the evolving nature of cyber threats demands constant adaptation and updates to ML models. Despite these hurdles, the potential for ML to revolutionize cybersecurity remains significant. A prepared ML demonstrate may moreover be powerless to adversarial attacks such as enrollment, property, or property induction assaults and demonstrate reversal attacks.
This paper explores these various aspects of applying cybersecurity principles to machine learning, providing an overview of key challenges and solutions. By examining real-world case studies and presenting best practices, the paper aims to guide researchers and practitioners in creating more secure, resilient, and trustworthy ML applications. In doing so, it contributes to the broader goal of fostering safer and more reliable technology in an increasingly data-driven world.
2. Machine Learning
Machine learning: One of the basically utilized progressed strategies for cybercrime discovery is machine learning procedures. Machine learning (ML) is a subfield of artificial intelligence (AI) that allows computers to learn from data and make predictions or decisions without explicit programming. Artificial intelligence (AI) had for numerous a long times for the most part been a field centered intensely on hypothesis, without numerous applications of real-world affect. This has profoundly changed over the past decade as a combination of more capable machines, made strides learning calculations, as well as less demanding get to tremendous sums of information empowered progresses in Machine Learning. It relies on algorithms that identify patterns in data and improve over time as they process more information.
2.1. The Definition of Machine Learning
Machine learning (ML) is a branch of artificial intelligence (AI) that focuses on the development of algorithms and systems enabling computers to learn from data, identify patterns, and improve their performance over time without being explicitly programmed. ML encompasses a range of statistical methods that allow systems to analyze vast datasets, make predictions, and make data-driven decisions. The learning process can be supervised, where models are trained on labeled datasets; unsupervised, where the system identifies patterns without explicit guidance; or reinforcement-based, where an agent learns through interaction with an environment and feedback. This adaptability has made ML a core technology in many industries, including healthcare, finance, e-commerce, cybersecurity, and autonomous vehicles. It has also raised challenges related to data quality, interpretability, and ethical considerations, prompting ongoing research into ensuring fairness, transparency, and robustness in ML systems.
Machine Learning (ML) methods are being utilized over the range of security. Most of these innovations have their own future prospects and are giving the security to the community by decreasing the fakes in advanced exchanges etc.
2.2. The Basic Model of Machine Learning
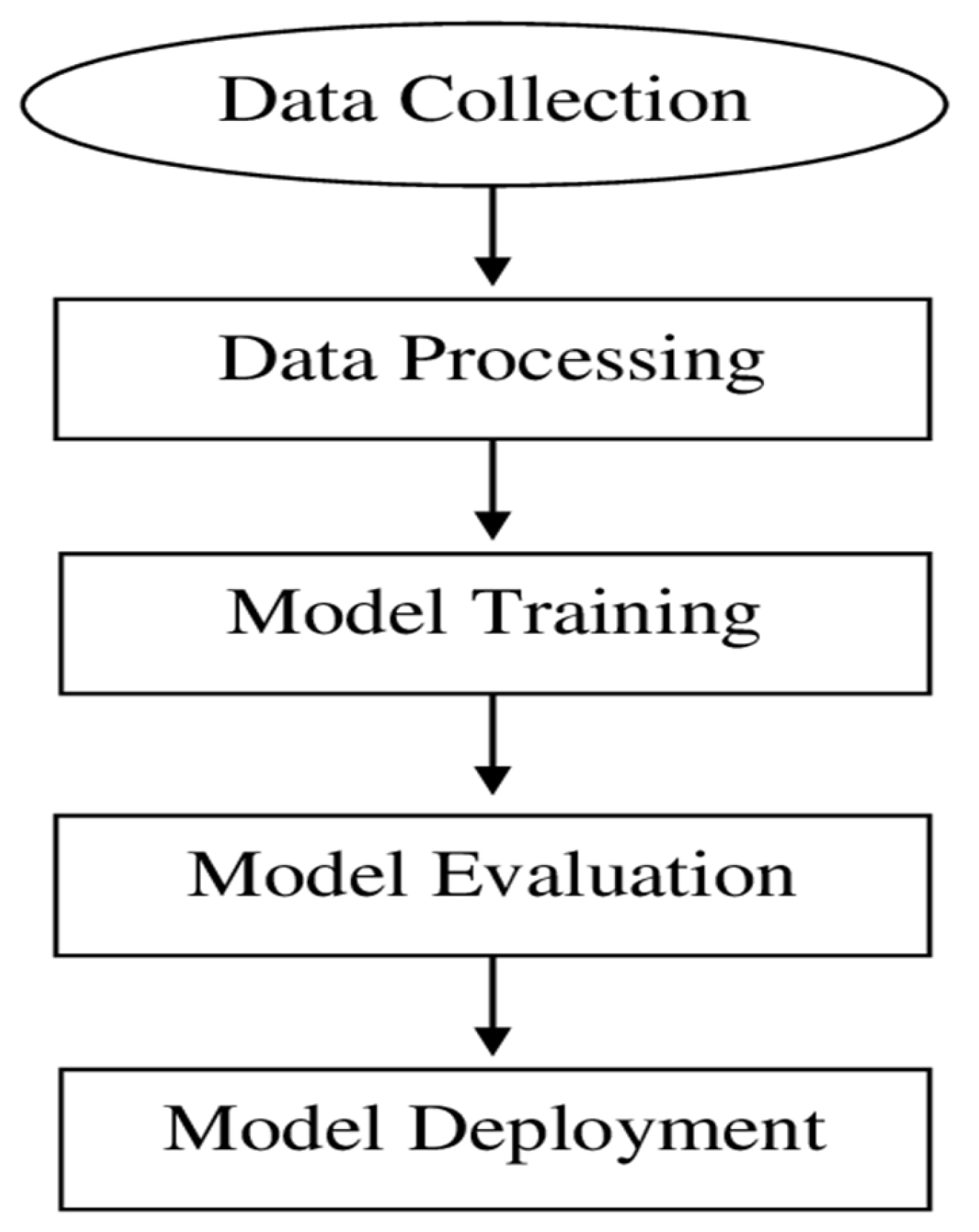
Machine learning (ML) involves training a model to perform a specific task by learning from data. The basic model of machine learning can be divided into several key stages: data collection, data preprocessing, model training, model evaluation, and model deployment.
Figure 1.
The basic model of machine learning.
Figure 1.
The basic model of machine learning.
Data Collection
This is often regularly the initial organize, where data is collected from distinctive sources. The quality and amount of the information play a significant part in deciding the victory of the ML model.
Data Preprocessing
Before the data can be used to train a model, it needs to be cleaned and transformed. This stage includes handling missing values, normalizing or scaling data, encoding categorical variables, and splitting the data into training and testing sets.
Model Trainings
After preparing, the demonstrate is tried employing a isolated dataset to assess its execution. Common measurements for assessment incorporate exactness, exactness, review, F1-score, and cruel squared mistake, depending on the errand.
Model Evaluation
After training, the model is tested using a separate dataset to evaluate its performance. Common metrics for evaluation include accuracy, precision, recall, F1-score, and mean squared error, depending on the task.
Model Deployment
Once the model has been evaluated and fine-tuned, it is deployed for use in real-world applications. This stage involves integrating the model into existing systems or software, ensuring it functions as expected, and monitoring its performance over time.
3. Machine Learning Techniques for Cybersecurity
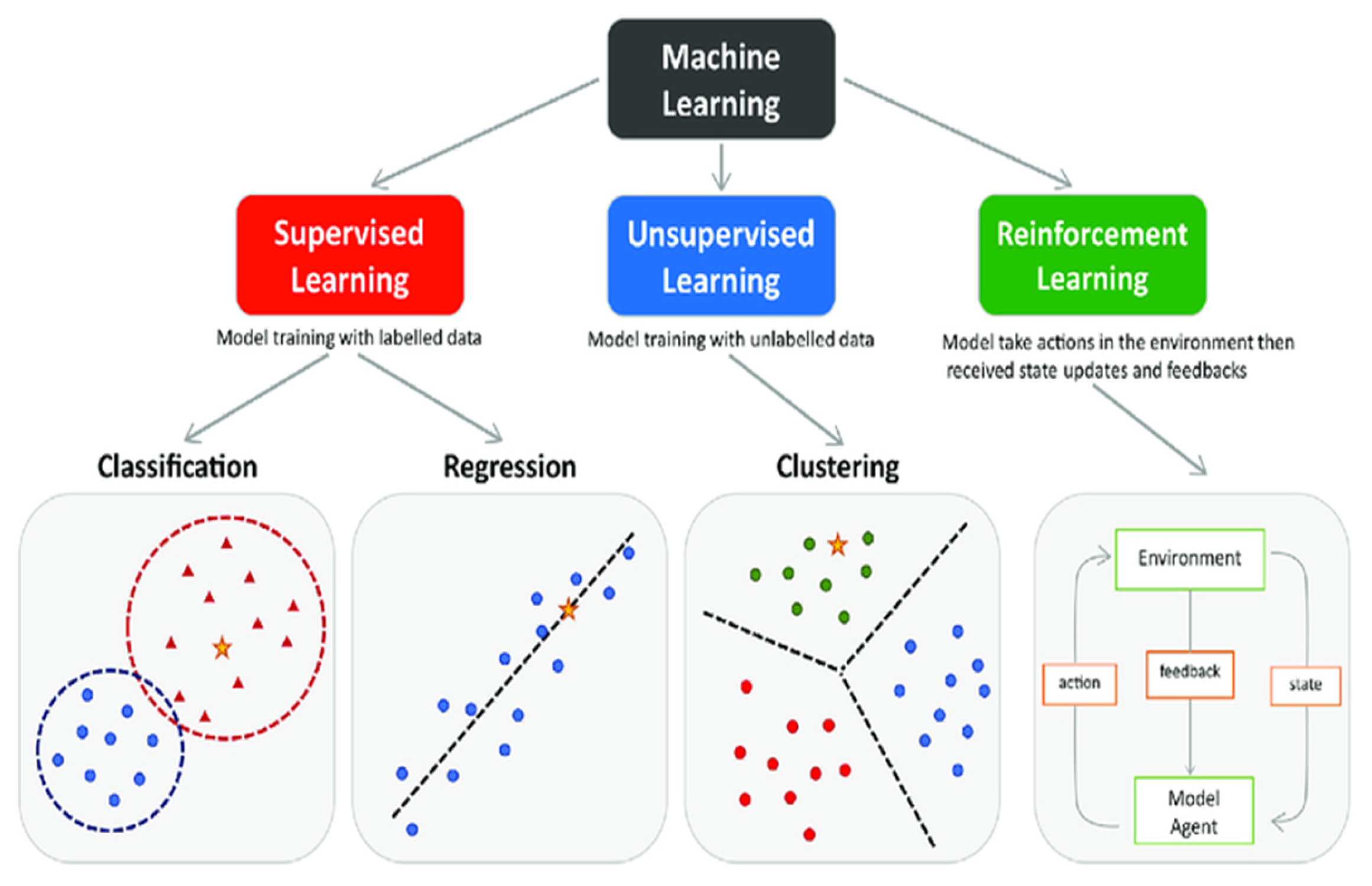
Supervised Learning
Overview: Supervised learning involves training a model on labeled data, where each input instance is associated with a corresponding output label. The model learns to map input features to the correct output based on the provided labels.
Applications: Supervised learning is widely used in cybersecurity for tasks such as malware detection, intrusion detection, and phishing detection. Common algorithms include decision trees, random forests, support vector machines (SVM), and logistic regression.
Overview: Unsupervised learning involves training a model on unlabeled data to identify patterns, clusters, or anomalies without explicit guidance from labeled examples.
Applications: Unsupervised learning techniques are used for anomaly detection, network traffic analysis, and identifying unusual behaviors indicative of security threats. Clustering algorithms like k-means and hierarchical clustering are commonly employed, along with techniques such as principal component analysis (PCA) for dimensionality reduction.
Overview: Deep learning techniques utilize neural networks with multiple layers to automatically learn hierarchical representations of data. These models excel at capturing complex patterns and relationships in large datasets.
Applications: Deep learning has been applied to various cybersecurity tasks, including malware detection, intrusion detection, and network traffic analysis. Convolutional neural networks (CNNs) are often used for image-based tasks like malware classification, while recurrent neural networks (RNNs) and long short-term memory (LSTM) networks are suitable for sequential data analysis, such as detecting network intrusions.
Overview: Reinforcement learning involves training an agent to interact with an environment to maximize cumulative rewards. The agent learns through trial and error, receiving feedback in the form of rewards or penalties based on its actions.
Applications: Reinforcement learning can be applied to cybersecurity tasks such as adaptive intrusion response and automated vulnerability patching. Agents learn optimal strategies for defending against cyber threats by dynamically adapting to evolving attack scenarios.
Overview: Ensemble learning combines multiple base learners to improve predictive performance, robustness, and generalization ability. It leverages diverse models to mitigate the weaknesses of individual classifiers.
Applications: Ensemble learning techniques such as bagging, boosting, and stacking are widely used in cybersecurity for building robust detection systems. Ensemble methods can enhance the accuracy and reliability of intrusion detection systems, malware classifiers, and spam filters by aggregating predictions from multiple models.
Overview: Transfer learning involves transferring knowledge from a source domain to a target domain, typically by fine-tuning pre-trained models on new data or tasks.
Applications: Transfer learning is valuable in cybersecurity when labeled data is scarce or when adapting models to new security domains. Pre-trained deep learning models, such as those trained on general image datasets like ImageNet, can be fine-tuned for specific cybersecurity tasks, reducing the need for extensive labeled data and accelerating model training.
Figure 2.
Machine learning techniques for cybersecurity.
Figure 2.
Machine learning techniques for cybersecurity.
4. Classification of Machine Learning Tasks in Cybersecurity
In cybersecurity, machine learning plays an essential part in improving location, avoidance, and reaction to different dangers and assaults. Cyber Risk Insights (CTI) can be utilized by organizations to help their security groups in shielding their networks against cyber-attacks. This will be accomplished by counting risk information nourishes into their systems or frameworks. The expanding number of phishing assaults is one of the major concerns of security analysts nowadays. The customary rebellious for recognizing phishing websites utilize signature-based approaches which are not able to recognize as of late made phishing web pages.
5. Challenges and Limitations
The application of machine learning in cybersecurity gives a diagram of the benefits and headways that ML brings to the field. In any case, it too faces different challenges and confinements that got to be tended to guarantee the effective execution and supportability of these applications. Here are a few of the key challenges and restrictions:
5.1. Disposed Vulnerabilities
Machine learning models, especially those utilized in cybersecurity, are helpless to adversarial attacks. Artificial Insights (AI) and Machine Learning (ML) could be a cybersecurity field. As cyber dangers ended up more complex and versatile, the application of AI and ML advances within the development of successful, energetic protective frameworks for advanced resources has gotten to be vital.
5.2. Information Quality and Keenness
Machine learning depends intensely on huge volumes of high-quality information. In any case, cybersecurity information can often be noisy, fragmented, or sullied, driving to potential issues with demonstrate precision and generalization. Guaranteeing information keenness and unwavering quality may be a basic impediment that requires strong information preprocessing and cleaning forms.
5.3. Security Concerns
Cybersecurity information regularly includes touchy data, raising concerns almost information protection and compliance with controls like GDPR and CCPA. The use of ML in cybersecurity must adjust the requirement for information to prepare models with the prerequisite to secure client protection. This impediment requires the execution of privacy-preserving procedures, such as differential protection.
6. Future Trends and Emerging Technology
Long-term patterns and rising advances within the field of machine learning for cybersecurity offers a see into how this energetic scene will advance. Conventional security arrangements are deficiently to address modern security issues due to the fast multiplication of numerous sorts of cyber-attacks and dangers. These patterns are driven by the got to address progressively modern cyber dangers whereas improving the proficiency and adequacy of cybersecurity operations.
6.1. Advanced Adversarial Defense Mechanisms
As adversarial attacks become more sophisticated, there’s a growing need for advanced defense mechanisms. Future trends point toward more robust adversarial training techniques, including gradient-based methods and generative adversarial networks (GANs) used to simulate attacks for training purposes. This development will strengthen the resilience of ML models against tampering and manipulation.
6.2. AI-Augmented Security Operations
Future trends in cybersecurity indicate a move toward AI-augmented security operations, where machine learning assists security teams in threat detection, incident response, and automation. Technologies such as Security Orchestration, Automation, and Response (SOAR) platforms will incorporate ML to streamline and automate routine security tasks, allowing human analysts to focus on higher-level decision-making.
6.3. Zero Trust Security and ML
The concept of Zero Trust Security, where access controls are based on a “never trust, always verify” approach, is expected to integrate more machine learning elements. Emerging technologies will focus on using ML to continuously monitor user behavior, device activity, and network traffic to identify potential security risks within Zero Trust frameworks.
6.4. Edge Computing and IoT Security
As edge computing and the Internet of Things (IoT) grow, machine learning will play a critical role in securing these distributed environments. Future trends include deploying ML models on edge devices for real-time threat detection and anomaly analysis. This development will be crucial for securing connected devices and networks in industrial and consumer IoT settings.
6.5. Quantum Computing and Post-Quantum Cryptography
Quantum computing presents both openings and dangers to cybersecurity. Whereas quantum computing can possibly break conventional cryptographic strategies, it too offers modern roads for progressing ML calculations. Future patterns will look at how ML can be utilized to create post-quantum cryptography and investigate ways to secure frameworks against quantum-based assaults.Top of Form
7. Conclusions
Machine learning plays a pivotal role in enhancing detection, prevention, and response to various threats and attacks. The intersection of machine learning and cybersecurity offers a compelling landscape for innovation and progress. The paper’s exploration of various ML applications in cybersecurity reveals the significant impact of these technologies in enhancing security measures. From anomaly detection and intrusion prevention to spam and phishing detection, machine learning has proven its value in combating an array of cyber threats. The paper’s comprehensive review underscores the need for robust defense strategies against emerging threats targeting ML models. Adversarial attacks, data poisoning, and model inversion pose unique risks, requiring advanced techniques like adversarial training and differential privacy to ensure the security and resilience of ML systems. As the field of cybersecurity continues to evolve, it is essential to prioritize the ethical implications of machine learning, emphasizing fairness, transparency, and accountability.
Machine learning is a viable device that can be utilized in numerous ranges of data security. There exist a few strong anti-phishing calculations and organize interruption discovery frameworks. Machine learning can be effectively utilized for creating confirmation frameworks, assessing the convention usage, surveying the security of human interaction proofs, savvy meter information profiling, etc. Looking ahead, the paper identifies key research directions that can further advance the use of machine learning in cybersecurity. These include developing more robust models, improving explainability, and addressing biases in data and algorithms.
Evaluate the effectiveness of various cybersecurity techniques, such as adversarial training, data encryption, and runtime monitoring, in enhancing the security and resilience of machine learning models against specific threats, including adversarial attacks and data breaches.
References
- Handa, A., Sharma, A., & Shukla, S. K. (2019). Machine learning in cybersecurity: A review. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 9(4), e1306. [CrossRef]
- Martínez Torres, J., Iglesias Comesaña, C., & García-Nieto, P. J. (2019). Machine learning techniques applied to cybersecurity. International Journal of Machine Learning and Cybernetics, 10(10), 2823-2836. [CrossRef]
- Ford, V., & Siraj, A. (2014, October). Applications of machine learning in cyber security. In Proceedings of the 27th international conference on computer applications in industry and engineering (Vol. 118). Kota Kinabalu, Malaysia: IEEE Xplore.
- Shaukat, K., Luo, S., Varadharajan, V., Hameed, I. A., Chen, S., Liu, D., & Li, J. (2020). Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies, 13(10), 2509. [CrossRef]
- Kaushik, D., Garg, M., Gupta, A., & Pramanik, S. (2022). Application of machine learning and deep learning in cybersecurity: An innovative approach. In An Interdisciplinary Approach to Modern Network Security (pp. 89-109). CRC Press.
- Bharadiya, J. (2023). Machine learning in cybersecurity: Techniques and challenges. European Journal of Technology, 7(2), 1-14. [CrossRef]
- Iyer, S. S., & Rajagopal, S. (2020). Applications of machine learning in cybersecurity domain. In Handbook of research on machine and deep learning applications for cybersecurity (pp. 64-82). IGI Global.
- Apruzzese, G., Laskov, P., Montes de Oca, E., Mallouli, W., Brdalo Rapa, L., Grammatopoulos, A. V., & Di Franco, F. (2023). The role of machine learning in cybersecurity. Digital Threats: Research and Practice, 4(1), 1-38. [CrossRef]
- Apruzzese, G., Laskov, P., Montes de Oca, E., Mallouli, W., Brdalo Rapa, L., Grammatopoulos, A. V., & Di Franco, F. (2023). The role of machine learning in cybersecurity. Digital Threats: Research and Practice, 4(1), 1-38. https://doi.org/10.1145/3545574. [CrossRef]
- Ten, C. W., Hong, J., & Liu, C. C. (2011). Anomaly detection for cybersecurity of the substations. IEEE Transactions on Smart Grid, 2(4), 865-873. [CrossRef]
- Dasgupta, D., Akhtar, Z., & Sen, S. (2022). Machine learning in cybersecurity: a comprehensive survey. The Journal of Defense Modeling and Simulation, 19(1), 57-106. [CrossRef]
- Kumar, K., & Pande, B. P. (2022). Applications of machine learning techniques in the realm of cybersecurity. Cyber Security and Digital Forensics, 295-315. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).