Submitted:
18 November 2024
Posted:
19 November 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Steganography
- undetectability: this metric quantifies a steganographic technique's capacity to conceal information within a steganogram such that its presence remains imperceptible to both human perception and statistical detection methods [8]. High undetectability indicates that the alterations introduced into the cover medium by the steganographic process are minimally discernible and resistant to detection [9],
- capacity: this metric measures the volume of information that can be embedded within a digital cover medium without inducing perceptible degradation in its quality. The capacity is contingent upon both the properties of the cover medium and the specific steganographic technique employed. While high capacity allows for greater information concealment, it may inversely affect undetectability by increasing the risk of detection [10],
- robustness: this metric assesses a steganographic technique's ability to preserve the embedded information within a steganogram when subjected to various disruptions or transformations, including but not limited to compression, format conversion, filtering, rotation, or scaling. Enhanced robustness implies that the embedded message is more likely to remain intact and undistorted after such modifications, or that a larger proportion of the original information will be retained [11].
- encoding function - maps a given cover object and a message to a steganogram. The encoding process embeds the message within the cover medium while minimizing perceptible alterations,
- decoding function - extracts the embedded message from a given steganogram. The decoding function is designed to accurately retrieve the message without requiring access to the original cover object. It is noteworthy that the decoding function can also be conceptualized as an integral component of the steganalysis process, serving as a means to verify the presence and content of hidden information [12].
1.2. Iterative Steganography
- information increment: resulting from decoding the data encoded in the steganogram,
- information degradation: due to transformations or interference with the steganogram.
2. A Model for Iterative Steganography
2.1. Iterative Cover
2.2. Message
2.3. Iterative Steganogram
2.4. Coding Indices
2.5. Encoding and Decoding Iterations
2.6. Encoding Function
2.7. Decoding Function
3. The Proposed Method
3.1. IIF (Incremental Information Function)
3.2. Properties of the IIF function
- Value range: The values of the IIF function lie within the closed interval from 0 to 1, with values in the range of approximately 0.5 to 1 being particularly significant. The interpretation of these values is analogous to the Bit Error Rate (BER) indicator; however, in the case of the IIF function, lower values indicate a higher presence of noise, while higher values reflect a greater amount of encoded information.
- Monotonicity: In the case of a properly functioning steganographic technique, including a well-defined encoding and decoding algorithm, the IIF function should not be decreasing, except for possible singular, isolated instances where the iterative steganogram might exhibit non-uniformity, leading to periodic disturbances in monotonicity. Successive iterations of the RAI decoding algorithm should lead to an increase in the amount of information contained in the decoded message, or at worst, not lead to its decrease.
- Asymptotic behavior: The IIF function exhibits an asymptotic nature, tending to reach the maximum possible value of information that can be decoded from a given steganogram under specified noise conditions and given parameter values of the basic RAI encoding algorithm. In most cases, this value will not be equal to 1, which would correspond to the decoding of the full information encoded in the original steganogram. Nevertheless, it should constitute a sufficiently significant portion of the information to enable the recipient to correctly decode the message content.
3.3. Characteristic Values
3.4. IIF Value Matrix
4. Results
4.1. Research Experiments
- The covers are video files treated as sequences of consecutive frames, each being an image.
- The successive iterations in which the message is encoded occur every third frame of the video files.
- The message is encoded using a steganographic method that operates in the spatial domain, altering the color values of the pixels in the video frames.
- The decoding function assumes that from the first iteration, all bits of the message are initialized to zero. Subsequent iterations incrementally build information by setting one bits and clearing zero bits of the message.
- The message is encoded in the form of a version 1 QR code with error correction level H. This allows encoding up to 72 bits of the message in a 21×21 module matrix with error correction up to 30% [18] enabling the use of automatic tools for reading the decoded message.
4.4. Example 1
4.3. Example 2
4.2. Discussion
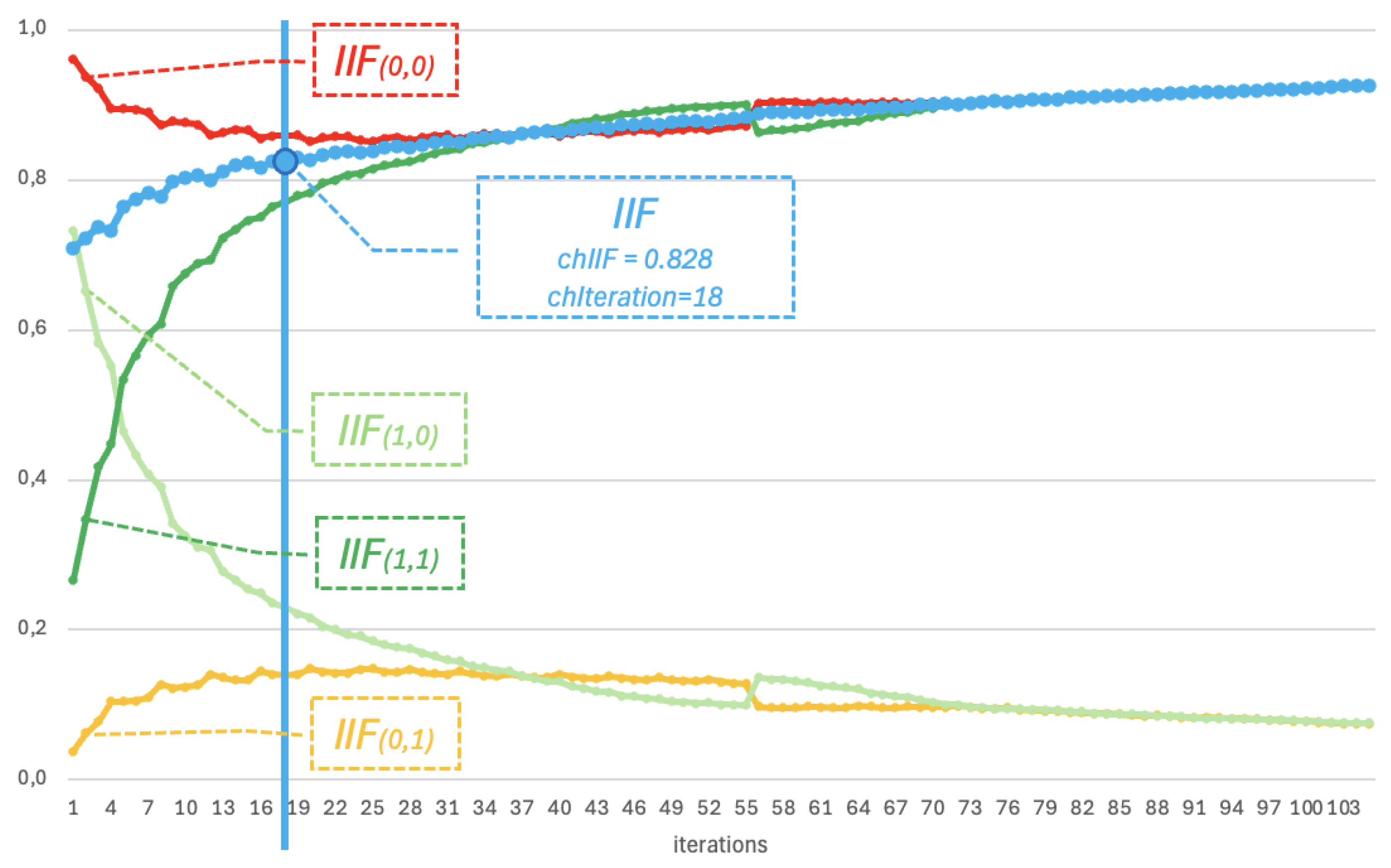
- for the example of video steganogram No. 1, the message was successfully decoded at the 18th iteration ( = 18) with an value of =0.828,
- the functions , and the overall function asymptotically converge to a maximum value close to 1.0,
- the values of and in this example do not carry any significant information, as they are complementary to the values of and ,
- the initial value of is very high, which is due to a specific property of the RAI decoding function, which assumes that all information bits are zeroed at the start of the algorithm,
- in general, the behavior of the functions align with the theoretical assumptions of the model.
5. Conclusions
5.1. Theoretical Contributions
- a formal mathematical model for characterizing a class of iterative steganographic methods,
- a novel quantitative method for evaluating the efficacy of iterative steganographic techniques, based on the proposed Incremental Information Function (IIF),
- the application of characteristic IIF values to quantify robustness and capacity metrics in iterative steganographic systems.
5.2. Practical Implications
5.3. Future Research
- extension of IIF application: explore the utilization of the Incremental Information Function (IIF) in diverse iterative steganography methods beyond video steganography, such as network steganography protocols,
- universal IIF characteristics: examine the potential existence of universal characteristic values (chIIF) of the IIF that may describe and differentiate various iterative steganography techniques, including multiple video steganography methods,
- IIF in steganalysis: investigate the potential applications of IIF properties in steganalysis processes for the detection and analysis of steganographic content, potentially enhancing the efficacy of current steganalysis techniques.
Author Contributions
Funding
Conflicts of Interest
References
- Kahn, D. The Codebreakers: The Story of Secret Writing. NYC, USA : Macmillan, 1967, ISBN 978-0025604605.
- Shannon, C. A Mathematical Theory of Communication. NYC, USA : Bell System Technical Journal 1948, 27, 379–423, ISSN 0005. [Google Scholar]
- Johnson, N. and Jajodia, S. Exploring Steganography: Seeing the Unseen. Los Alamitos, USA : IEEE Computer 1998, 31, 26–34, ISSN 0018. [Google Scholar]
- Johnson, N. , Duric, Z. and Jajodia, S. Information Hiding: Steganography and Watermarking - Attacks and Countermeasures. Boston, USA : Springer, 2001, ISBN 978-0-7923-7204-2, DOI 10.1007/978-1-4615-4375-6, 2001.
- Petitcolas, F. , Anderson, R. and Kuhn, M. Information hiding - a survey. NYC, USA : Proceedings of the IEEE 1999, 87, 1062–1078, ISSN 0018. [Google Scholar]
- Fridrich, J. Steganography in Digital Media: Principles, Algorithms, and Applications. Cambridge, UK : Cambridge University Press, 2009, DOI 10.1017/CBO9781139192903.014.
- Sencar, H. , Ramkumar, M. and Akansu, A. Data Hiding Fundamentals and Applications. Burlington, USA : Elsevier Academic Press, 2004, ISBN 9780120471447, DOI 10.1016/B978-0-12-047144-7.X5000-5.
- Huynh-Thu, Q. and Ghanbari, M. Scope of validity of PSNR in image/video quality assessment. London, UK : Electronics Letters 2008, 44, 800–801, ISSN 0013. [Google Scholar]
- Wang, Z. , et al. Image Quality Assessment: From Error Visibility to Structural Similarity. NYC, USA : IEEE Transactions on Image Processing 2004, 13, 600–612, ISSN 1057. [Google Scholar]
- Cox, I. , Miller, M. and Kalker, T. Digital Watermarking and Steganography. Burlington, USA : Morgan Kaufmann Publishers, 2007, ISBN 0123725852.
- Anderson, R. and Petitcolas, F. On the limits of steganography. NYC, USA : IEEE Journal on Selected Areas in Communications 1998, 16, 474–481, ISSN 0733. [Google Scholar]
- Kadhim, I. , et al. Comprehensive survey of image steganography: Techniques, Evaluations, and trends in future research. Amsterdam, Netherlands : Neurocomputing 2019, 335, 299–326, ISSN 0925. [Google Scholar]
- Chan, C. and Cheng, L. Hiding data in images by simple LSB substitution. Amsterdam, Netherlands : Elsevier, Pattern Recognition 2004, 37, 469–474, ISSN 0031. [Google Scholar]
- Bennett, K. Linguistic Steganography: Survey, Analysis, and Robustness Concerns for Hiding Information in Text. West Lafayette, USA : CERIAS Tech Report 2004-13, Purdue University, Available online:. Available online: https://www.cerias.purdue.edu/assets/pdf/bibtex_archive/2004-13.pdf (accessed on 16 November 2024).
- Kunhoth, J. , et al. Video steganography: recent advances and challenges. Berlin, Germany : Springer - Multimedia Tools and Applications 2023, 82, 11817–11868, ISSN 1380. [Google Scholar]
- Lubacz, J. , Mazurczyk, W. and Szczypiorski, K. Principles and Overview of Network Steganography. NYC, USA : IEEE Communications Magazine. 2012; 52. [Google Scholar] [CrossRef]
- Katzenbeisser, S. and Petitcolas, F. Information Hiding Techniques for Steganography and Digital Watermarking. Norwood, USA : Artech House, 2000, ISBN 978-1-58053-035-4.
- DensoWave. QR code. Denso Wave, Available online:. Available online: https://www.qrcode.com (accessed on 16 November 2024).
| original bit values in | |||
| 0 | 1 | ||
| decoded bit values in | 0 | ||
| 1 | |||
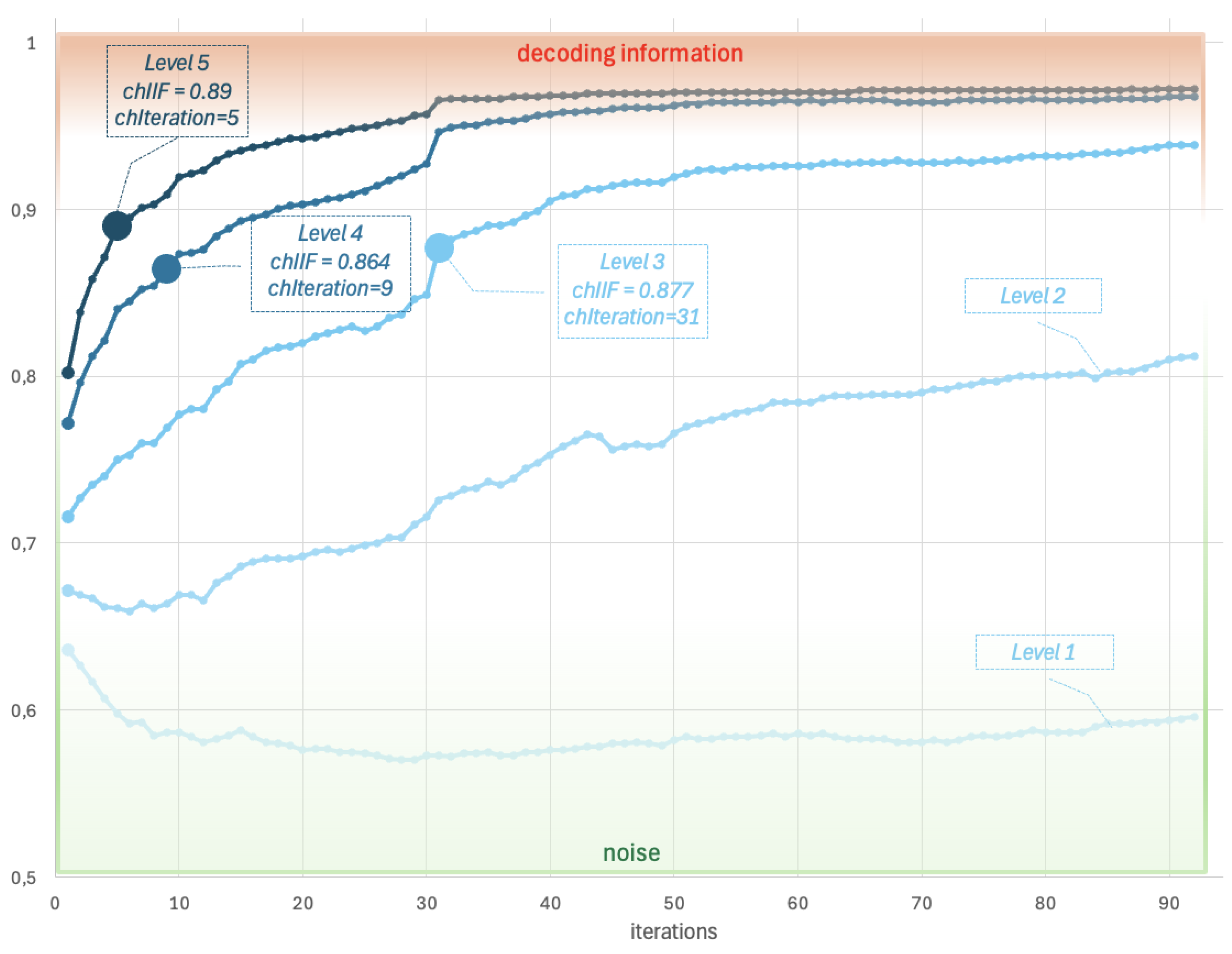
| iteration | Level 1 | Level 2 | Level 3 | Level 4 | Level 5 |
| 1 |  |
 |
 |
 |
 |
| IIF=0.636 | IIF=0.672 | IIF=0.716 | IIF=0.772 | IIF=0.802 | |
| 2 |  |
 |
 |
 |
 |
| IIF=0.627 | IIF=0.669 | IIF=0.727 | IIF=0.796 | IIF=0.838 | |
| 3 |  |
 |
 |
 |
 |
| IIF=0.617 | IIF=0.667 | IIF=0.735 | IIF=0.812 | IIF=0.858 | |
| 4 |  |
 |
 |
 |
 |
| IIF=0.607 | IIF=0.662 | IIF=0.740 | IIF=0.821 | IIF=0.871 | |
| 5 |  |
 |
 |
 |
 |
| IIF=0.598 | IIF=0.661 | IIF=0.750 | IIF=0.840 | IIF=0.890 | |
| 6 |  |
 |
 |
 |
 |
| IIF=0.592 | IIF=0.659 | IIF=0.753 | IIF=0.845 | IIF=0.895 | |
| 7 |  |
 |
 |
 |
 |
| IIF=0.593 | IIF=0.664 | IIF=0.760 | IIF=0.852 | IIF=0.901 | |
| 8 |  |
 |
 |
 |
 |
| IIF=0.585 | IIF=0.661 | IIF=0.760 | IIF=0.854 | IIF=0.903 | |
| 9 |  |
 |
 |
 |
 |
| IIF=0.587 | IIF=0.664 | IIF=0.769 | IIF=0.864 | IIF=0.909 | |
| 10 |  |
 |
 |
 |
 |
| IIF=0.587 | IIF=0.669 | IIF=0.777 | IIF=0.873 | IIF=0.919 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





